Intrusion Analysis Overview
The success of any security team depends on how quickly they respond to threats, how efficiently they stop them, and also how well they prevent the same in the future. But to even engage with these stages, one must first identify a threat. Organizations take the help of tools like SIEM, EDR, IDS, Firewall, etc to help identify threats and alert them as they occur. These tools are like great weapons in our arsenal but only if we use them strategically against our enemies.
Threat analysts/Intelligence analysts use a few frameworks to aid their process of intrusion analysis. Everyone related to cyber security must have come across the term KILL CHAIN. A lot of analysts talk in terms of the kill chain phases, use it to map an intrusion, and develop defenses for these stages. Taking it another step further, a lot of us have heard of the MITRE ATT&CK framework to map the TTP to an adversary or an attack.
Traditionally the who, what, when, where, why, and how questions were asked by the Incident responders to mitigate the ongoing attacker activity in hand- Tactical mitigation.
The defenders did not have models or frameworks to answer questions like
- what if the attacker is not a single entity ?
- what if the attack is part of a bigger campaign ?
- what if there were more than one attack at the given time?
The Diamond Model for Intrusion analysis answers these questions providing Intel and moves defenders towards the bigger picture of Strategic mitigation. A significant amount of limelight must be given to this delicate, simple but powerful model for intrusion analysis that fits right in between the Kill chain and Att&ck. This model is peculiar because it scrutinizes victimology and links the capabilities of the attacker to the infrastructure of the attack as well. It makes mitigation effective and the adversary’s cost to operate more.
The Diamond Model for intrusion analysis
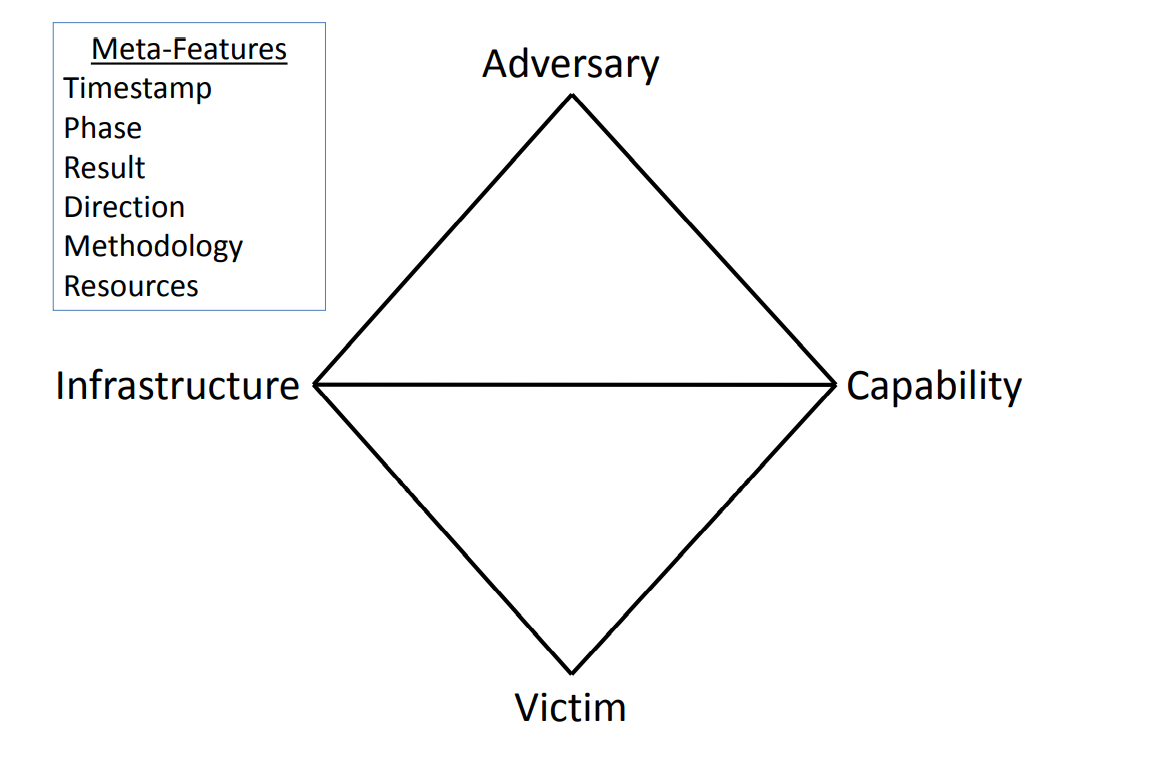
Sergio Caltagirone, Andrew Pendergrast, and Christopher Betz felt that linear cybersecurity intrusion models had flaws. They wanted to focus on specific hacker behaviors and create a model that allowed cybersecurity professionals to map the relationships between attackers, the victim, and the technology used to execute an attack. The first articulated the diamond model in 2006 and later published it in 2013. The model has 4 main vertices Adversary, Infrastructure, Capability, and Victim forming 4 quadrants like a Diamond(thus the name).
The model is defined by a set of Axioms published by Sergio Caltagirone as a blog post in ‘active response’.
The axioms are :
Axiom 1
For every intrusion event, there exists an adversary taking a step towards an intended goal by using a capability over infrastructure against a victim to produce a result.
Axiom 2
There exists a set of adversaries (insiders, outsiders, individuals, groups, and organizations) which seek to compromise computer systems or networks to further their intent and satisfy their needs.
Axiom 3
Every system, and by extension every victim asset, has vulnerabilities and exposures.
Axiom 4
Every malicious activity contains two or more phases that must be successfully executed in succession to achieve the desired result.
Axiom 5
Every intrusion event requires one or more external resources to be satisfied prior to success.
Axiom 6
A relationship always exists between the Adversary and their Victim(s) even if distant, fleeting, or indirect.
Axiom 7
There exists a subset of the set of adversaries which have the motivation, resources, and capabilities to sustain malicious effects for a significant length of time against one or more victims while resisting mitigation efforts. Adversary-Victim relationships in this sub-set are called persistent adversary relationships.
The above axioms lay foundations for this Intrusion analysis model. As we explore the diamond model in detail, we will comprehend the axioms better.
The Extended Model
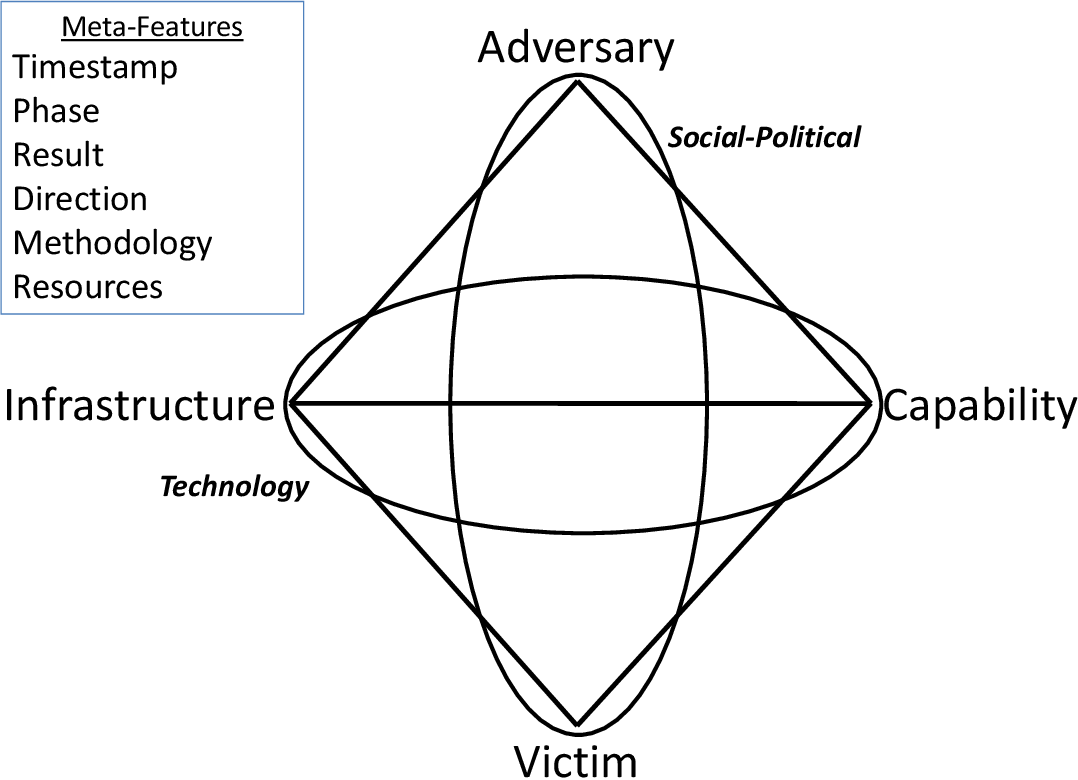
The Diamond Model comprises of core features that constitute an intrusion event:
- Adversary (mentioned in Axiom 2)
The actor/organization responsible for utilizing a capability against the victim to achieve their intent. Not just the attacker but also the ones hired the attacker.
For Example: In many ransomware-as-a-service models we get to see these collaborations. (Lockbit2.0 uses affiliates to perform intrusion and exfiltration by providing them the weaponized file. )
- Capability
The capability feature describes the tools and/or techniques of the adversary used in the event.
- Infrastructure
The infrastructure feature describes the physical and/or logical communication structures the adversary uses to deliver a capability, maintain control of capabilities (command-and-control), and effect results from the victim (exfiltration etc).
- Victim
A victim is the target of the adversary and against whom vulnerabilities and exposures are exploited and capabilities used.
On the whole a Diamond Event is when an adversary taking a step towards an intended goal by
using a capability over infrastructure against a victim producing a result. (Axiom 1)
Example: To understand a Diamond event better let us take FIN8 attack as a simple example.
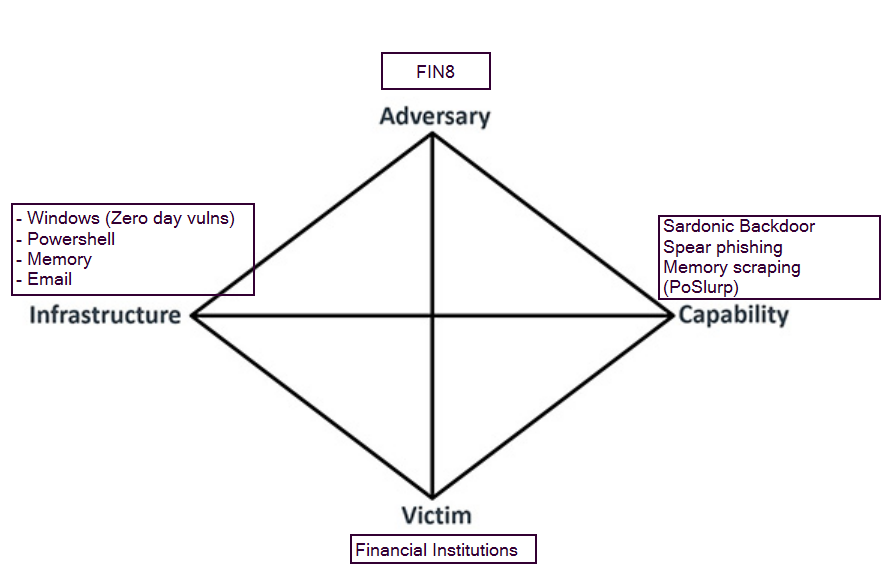
Recent attack investigations had revealed that (adversary) FIN8 uses PowerShell scripts (infrastructures) to deploy a backdoor “Sardonic Backdoor” (capability) while attacking Financial institutions(victim). This can map to the Execution/persistence phase of the kill chain. This is one diamond event.
There are other events observed in the attack of the same adversary, using backdoors such as BadHatch, Punchbaggy etc, deploying ShellTea malware and Poslurp to scrap essential memory. These can be other individual diamond events themselves and can map to Action on the objective phase of the kill chain. Each of these can be further associated with Techniques in the MITRE ATT&CK framework for the tactics such as Exfiltration/Execution/Credential access etc.
Also Read : Cyber Threat Hunting – Proactive Intrusion Detection
The meta-features of the diamond model are listed as well
- Timestamp
Each event is notated with a date and/or time that it occurred - Phase
Malicious activity does not happen in a single event but rather two or more events(Axiom 4).
- Result
While the results of an adversary’s operations will not always be known, it is particularly useful to look across an adversary’s operations to determine their success rate with particular capabilities or against sets of victims. - Direction
The direction of an event is important for planning mitigation.This is how the placement of detection mechanisms are planned. There are generally seven potential values for this feature:
Victim-to-Infrastructure, Infrastructure-to-Victim, Infrastructure-to-Infrastructure, Adversary-to-Infrastructure, Infrastructure-to-Adversary, Bidirectional, or Unknown.
By knowing this adversary’s activity direction over time, better decisions can be made on which mechanism of detection( external-facing or internal-facing) would work best to counter the adversary.
- Methodology
The methodology meta-feature allows an analyst to describe the general class of activity.
For example: DDOS, phishing email, etc.
- Resources
The resources meta-feature lists one or more external resources the event requires to be satisfied. Resources are to be broadly understood as all supporting elements on which the event(core- and meta-feature) depends.(Axiom 5)
The Model has an extension with two more meta-features :
- Technology
The technology meta-feature connects the infrastructure and capability and describes the
technology enabling the infrastructure and capabilities to interact effectively. For example, if installed malware resolves domains and communicates with C2, the technologies used can be IP, TCP, and DNS.
Socio-Political
A relationship always exists between the Adversary and their Victim. There is always an Intent (Axiom 6). The social-political meta-feature describes the always existing, and sometimes enduring, the relationship between adversary and victim. It describes that there are underlying needs, aspirations, and intent behind every malicious activity and that each victim has a unique relationship with the adversary.
Analytically, the Diamond allows concepts from criminology and victimology to be applied to intrusion analysis allowing one to understand the reason a victim was chosen, the value the victim brings to the adversary, and ultimately how that relationship can be influenced to enhance mitigation.
For example, This feature enables to know and thereby help prevent attackers in spear-phishing campaigns, targeted espionage, or data leaks.
Also Read : DnsTwist Tool – Proactive Approach for Handling Phishing Cases
Analytical pivoting:
Analytical pivoting is one of the main aspects of this model. It’s about how from any point on the Diamond, an analyst can possibly reach the other connection points. It is Mapping other features of a diamond starting from one feature (The center). Pivots can happen between diamond events and phases as well. The analyst can take any feature of the model as the center based on individual scenarios and approach ahead to track or map the event. Centered approaches can be :
- Victim-Centred Approach
- Capability-centred Approach
- Infrastructure-centred Approach
- Adversary-centred Approach
- Social-Political-centred Approach
- Technology-centred Approach
For example: A following diagram is a victim-centric approach
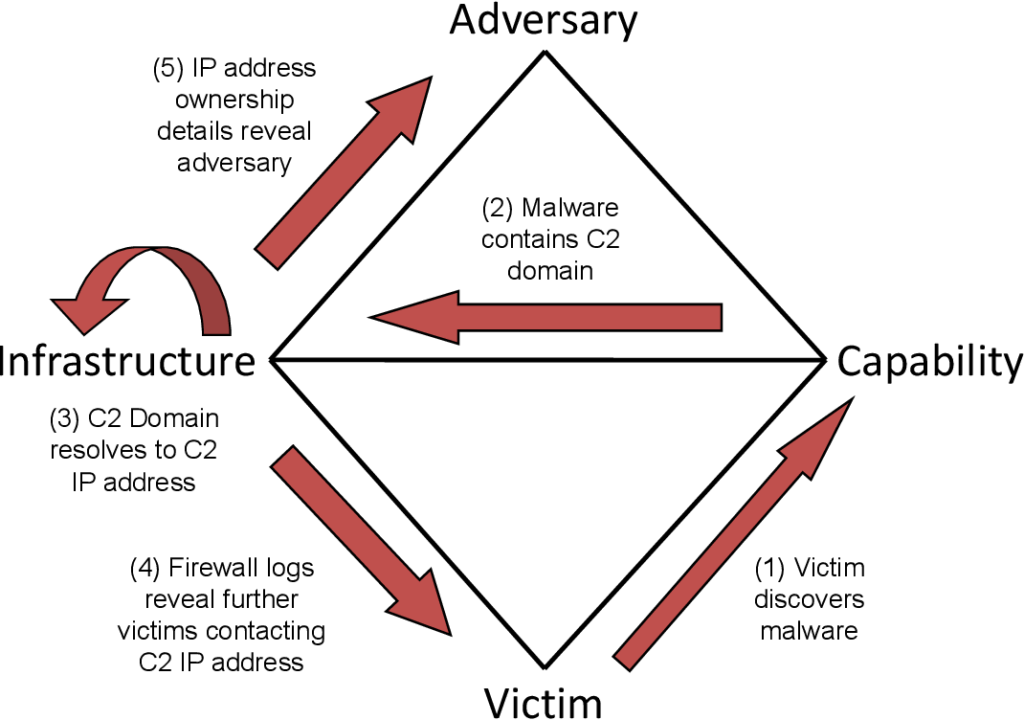
Activity threads:
An activity thread is a directed phase-ordered graph where each vertex is an event and the arcs identify causal relationships between the events.
Once activity is discovered and events have been characterized, they are
ordered by the phases of malicious activity(Kill chain) and linked by their causal relationship into
threads. These are called activity threads. Threads not only span vertically along a
single adversary-victim pair, but horizontally also as adversaries take advantage of knowledge
and access gained in one operation to enable other operations.
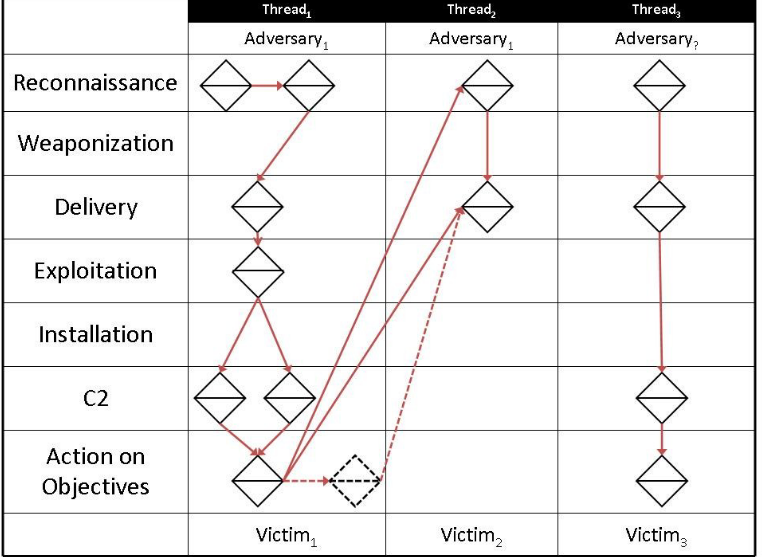
For Example:
Lateral movement by an adversary inside an organization by compromising different targets towards the goal. Activities on each target can be an activity thread.
To understand it better let us take a recent example where a threat group was found deploying LockFile ransomware exploiting Petitipotam bug in windows.
The attacker exploits NTLM relay attack vulnerability and gains control of domain controller- activity thread 1
The same attacker uses DC to push ransomware files to connected devices. Ransomware file activity in each of the devices can be activity thread 2,3,….n.
We can analytically pivot in each diamond event in an activity thread or between threads as well.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Activity Attack graphs
While activity graphs resolve adversary(s) actions, The model takes even a step further.Usually, the vulnerability management or risk assessment teams determine assets and their risk posture. A threat modeling is done and conclusions are drawn to know in how many ways a particular asset can be attacked and what are the risks for business if attacked in each way(Attack Graphs). Based on the business impacts aligned with cost incurred in protecting, strategies are picked only for the most probable attacks. The diamond model makes use of such attack graphs and merges it with activity threads
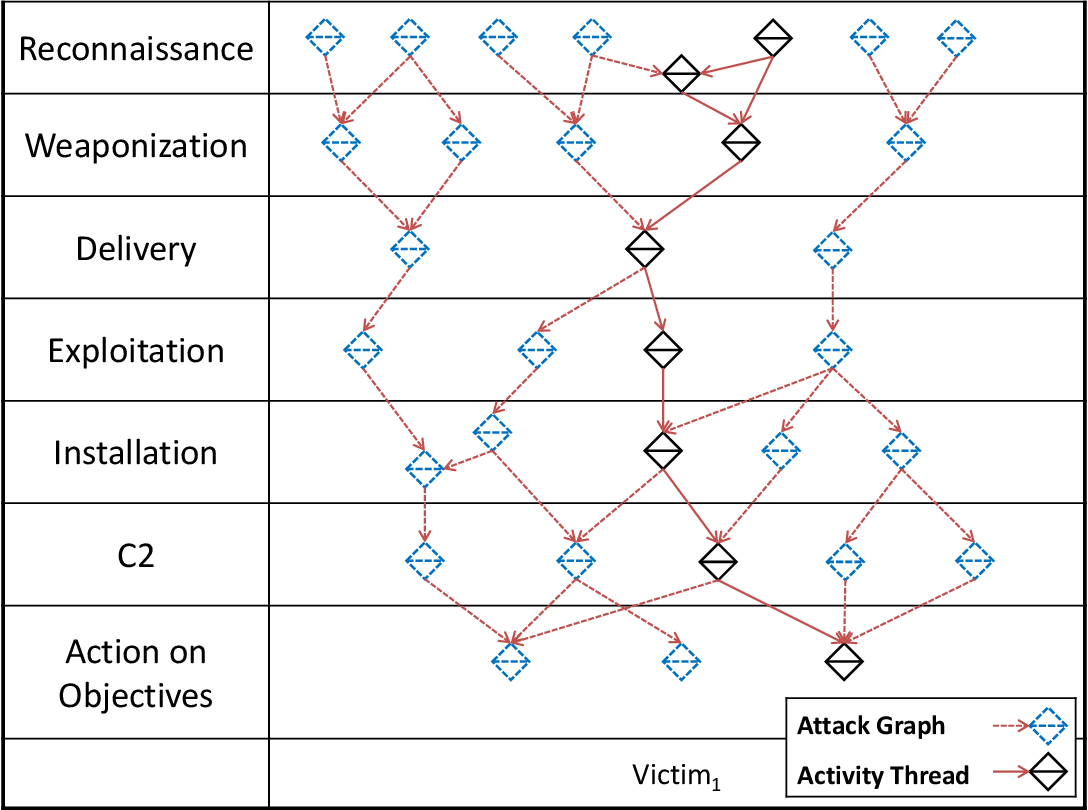
This not only presents us what we so far know of the attacker (Activity thread) but also predicts alternate attacker strategies that are possible, to achieve the same goal based on the attack surface of our environment(Attack graph). Together they make the activity-attack graph . Now we know much more before we decide a mitigation strategy.
Conclusion
The power of this model not alone ends here. It can be used to
- Map similar activities of attacker into activity groups.
- Help in gap analysis,
- used in Att&ck framework based threat modelling
- answer questions when there are more than one attacker or attackers follow a campaign and much more.
This is a model that clearly solves the pain points of the linear kill chain model and adds value to our approach by connecting Adversary to victim and Infrastructure to the capability of an attacker in phases which can also be further mapped to TTPs by MITRE framework. What a great way to go about it right, well Happy Intelligence to you!



































