In my earlier blog post, I demonstrated the process of analyzing executable packers. In this current blog, we will explore additional static malware analysis tools. Prior to that, we will examine why it is crucial.
Now-a-days, the significance of malware analysis cannot be overstated. The detection and analysis of malicious samples necessitate the use of malware analysis tools, which are critical for security experts and researchers to comprehend the malware’s behavior, pinpoint its origin, and devise countermeasures to safeguard against it.
Here’s some specific reasons:
- Detect malware on a system or network by identifying suspicious files and behaviors.
- Identifying the type of malware, its source, and how it operates.
- Allow researchers to reverse engineer the code of malware to understand how it works and create solutions to counteract it.
- Mitigate the damage caused by malware by identifying its impact and taking appropriate steps to contain and remove it.
- Also helps in preventing future attacks by using the knowledge gained from analyzing existing malware to improve security systems and develop better defenses against malware.
Let’s begin..
PE-Studio
PEStudio is a software analysis tool used for examining executable files on Windows operating systems. It is designed to assist security professionals and researchers in identifying potentially malicious files by analyzing their structure, contents, import & export table, TLS-callbacks, and mainly any suspicious strings found in the sample.
Here’s the snap of the PE-Studio – Malware Initial Assessment window.
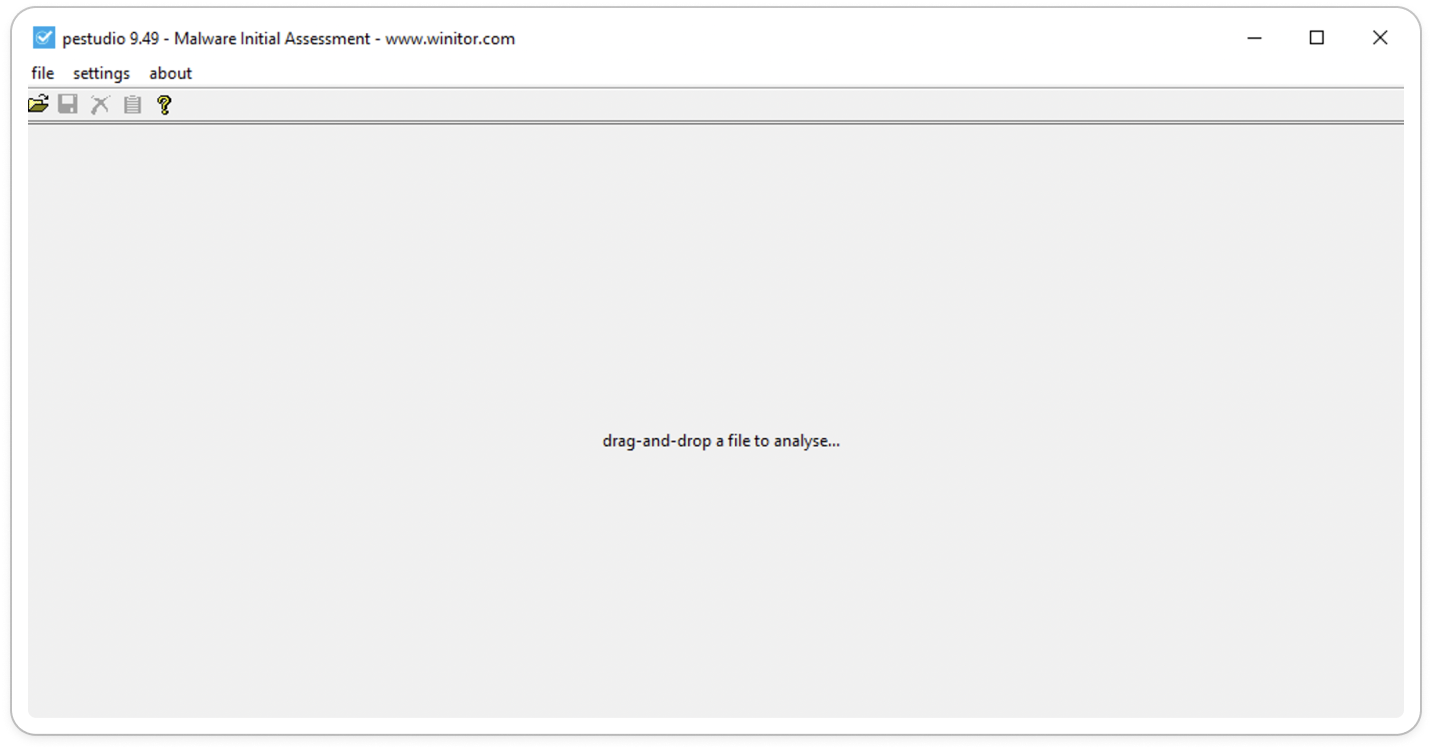
Fig 1: PE-Studio – Malware Initial Assessment window
How does it work?
PEStudio uses a combination of signature scanning, heuristics, and other methods, PEStudio is capable of identifying malevolent or dubious code within executable files. Additionally, it has the ability to recognize packers, libraries, and functions utilized by an executable, and offer insights into their security implications.
Features of PEStudio:
PEStudio offers several features such as detecting malware, conducting static analysis of files, identifying digital signatures, and inspecting for suspicious code or behavior. It is frequently utilized in malware analysis, forensic investigations, and software development as a means to safeguard the computer systems. Let’s take a brief look.
Sample Test:
Before starting our analysis, initially we can set our preference settings inside the tool. And then subsequently load the sample into the PE-Studio.
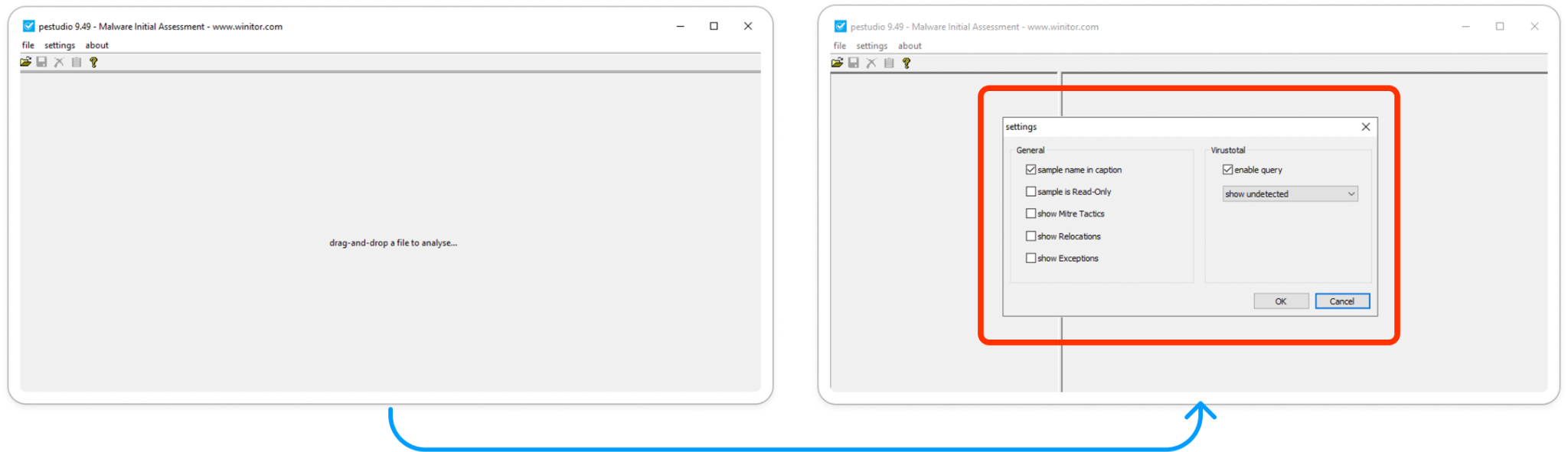
Fig 2: Setting Preferences
On successful loading, we can get the file meta-properties at the left-side of the windows. Where it consists of Indicators, VT Results, PE- DOS stub, Import & export sections and resources.
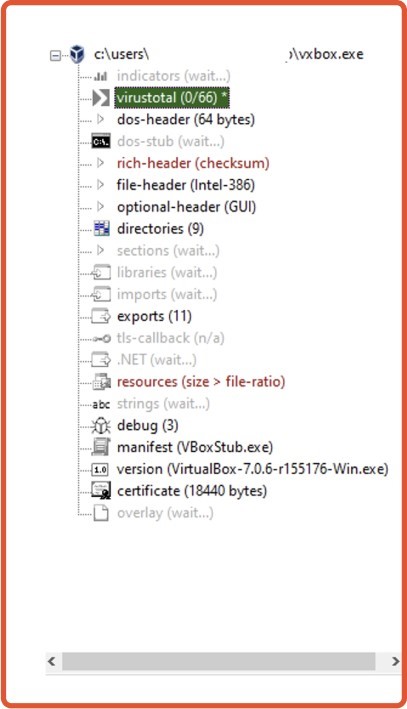
Fig 3: Main window
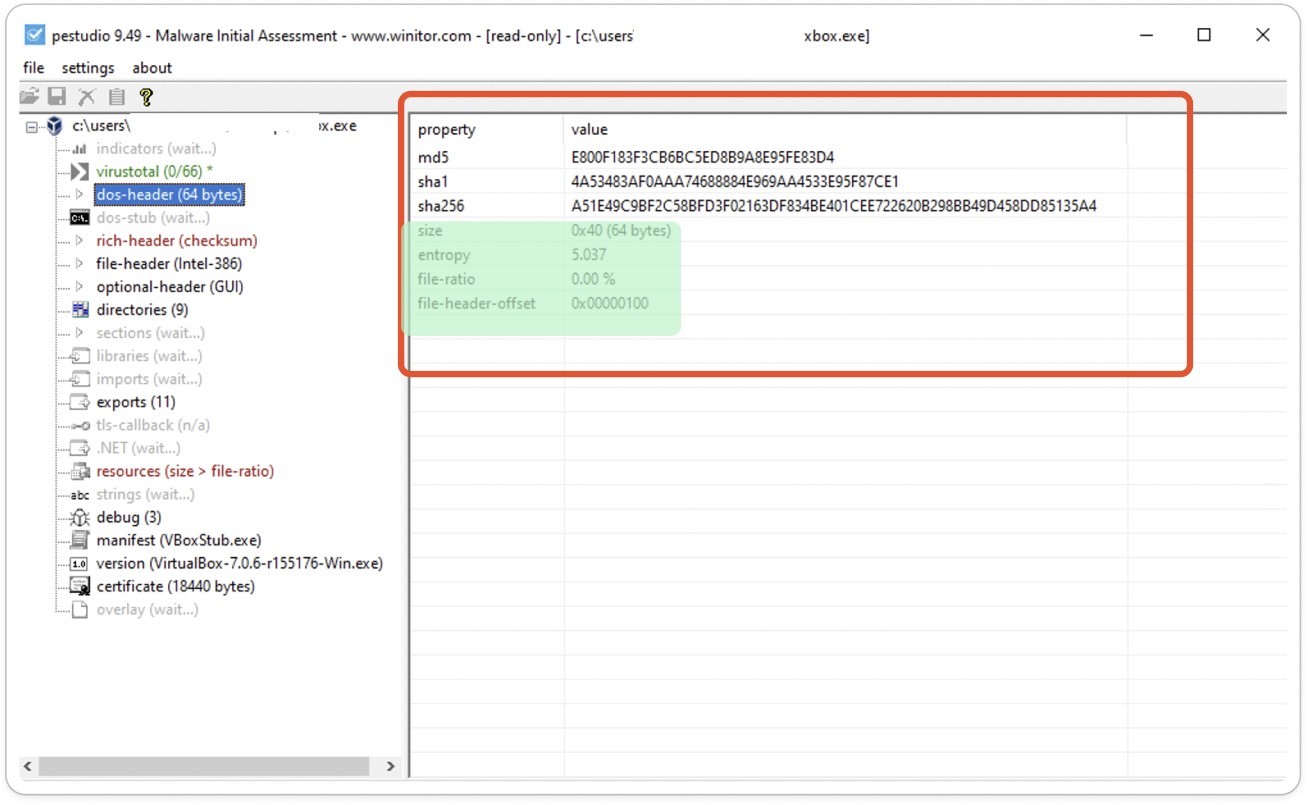
Fig 4: DOS- Header section
Here, we have to note the most important factor in the header section is Entropy.
Due to the increasing automation and complexity of malware and spam, security professionals must be more proactive in identifying and preventing the exfiltration of stolen data. To aid in static analysis, a useful tool for spotting hidden threats is the use of “entropy” with the assistance of machine learning.
Entropy is a powerful and critical indicator of packing, encryption, and compression – techniques often employed by malware. If a sample has an entropy of 7.2 or greater, it can be considered as malware and it will be highly obfuscated and possess significant randomness within the file.
Then Subsequently, we can view the VirusTotal (VT) results, which enable us to predict whether the sample is clean or malicious with 60+ AV vendors results.
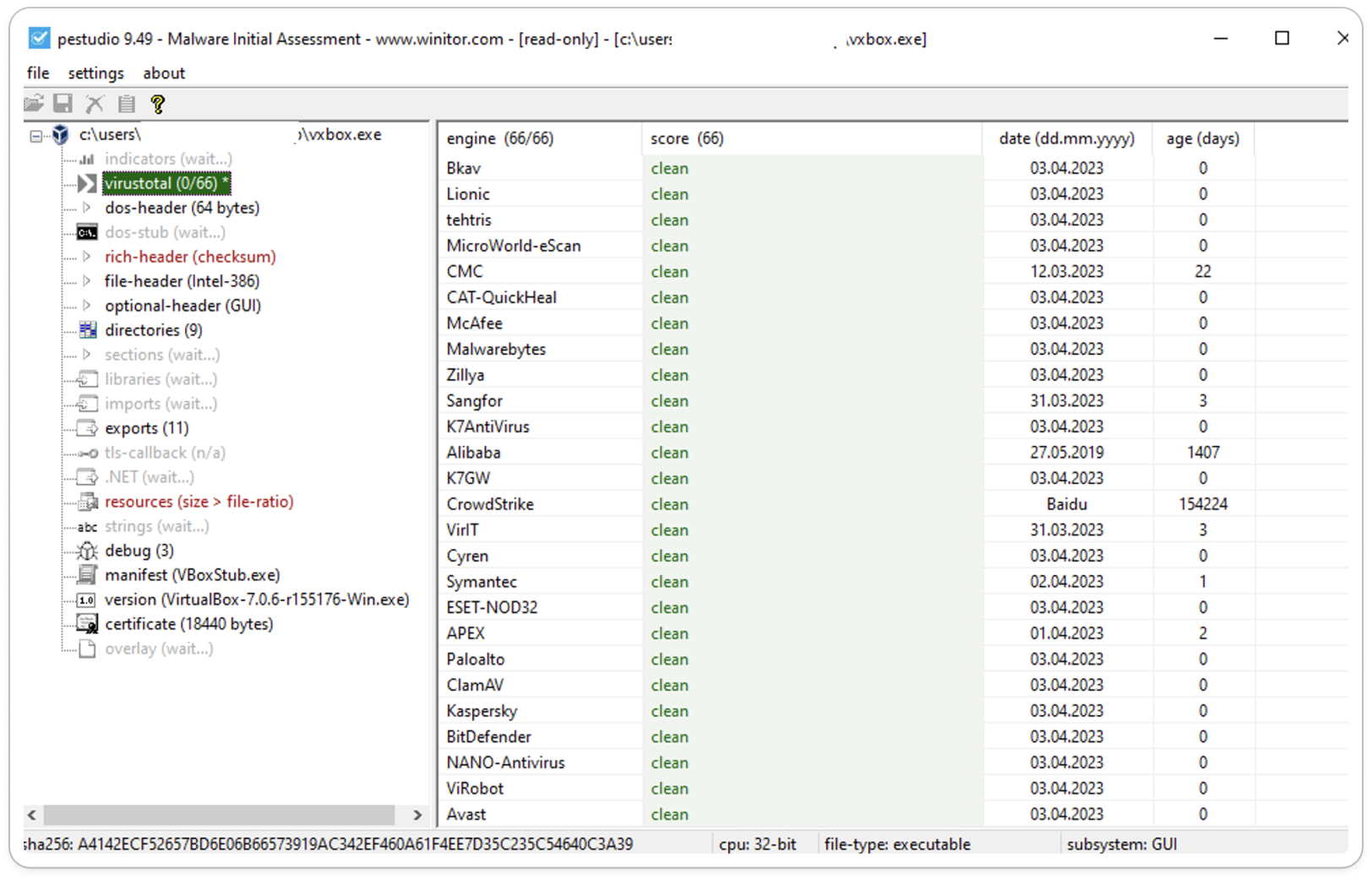
Fig 5: VT Integration
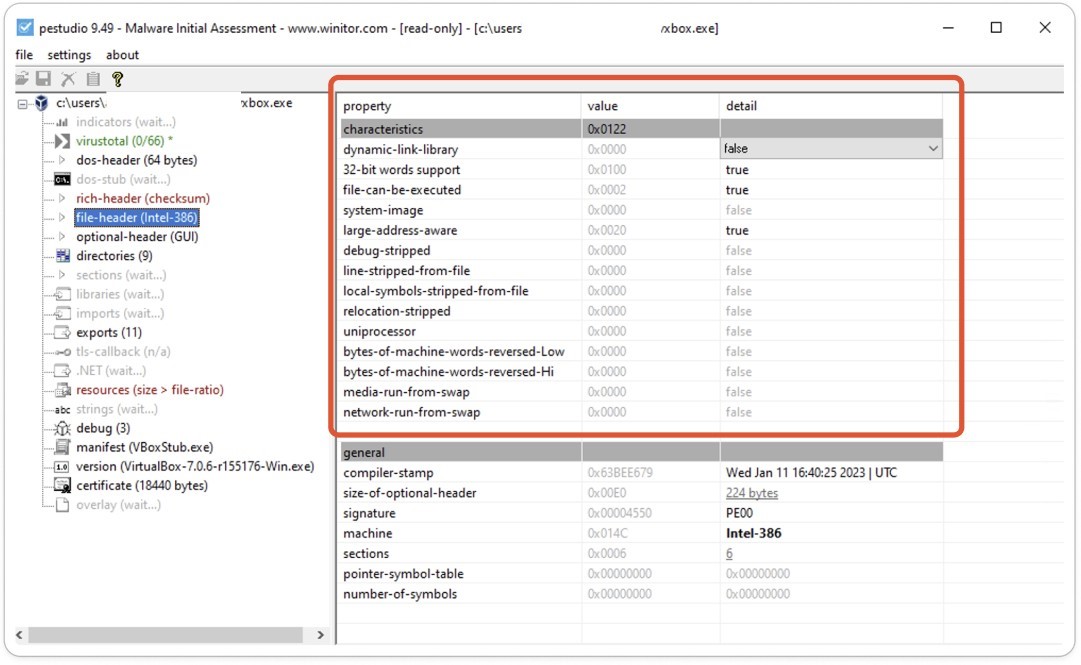
Fig 6: File header – Properties
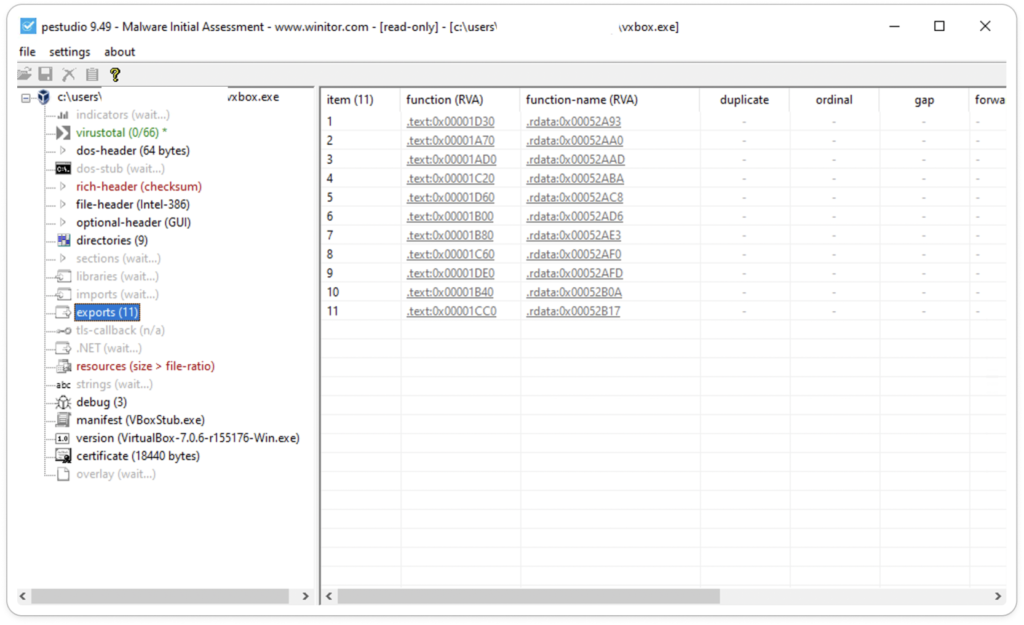
Fig 7: Export function (.text & .rdat)
Typically, the Windows loader loads any executable file into memory by first reading its PE structure and then loading the executable image. Next, it scans the Import Address Table (IAT) of the executable to identify the DLLs and functions utilized by the executable and maps these DLLs into the process address space.
Within the section header, there exist multiple layers that can be examined individually.
- .text: Contains the executable code for the application to run.
- .data: Holds initialized data of an application, such as strings and constants.
- .bss: Holds Uninitialized data of an application
- .rdata: Represents the read-only data on the file system.
- .reloc: Hold the information about the address of the relocation table.
- .idata: Import descriptors.
- .edata: Export descriptors.
- .rsrc: This is the most common resource-container section, which contains things like images used for the application’s UI.
- .debug: contains debug information.
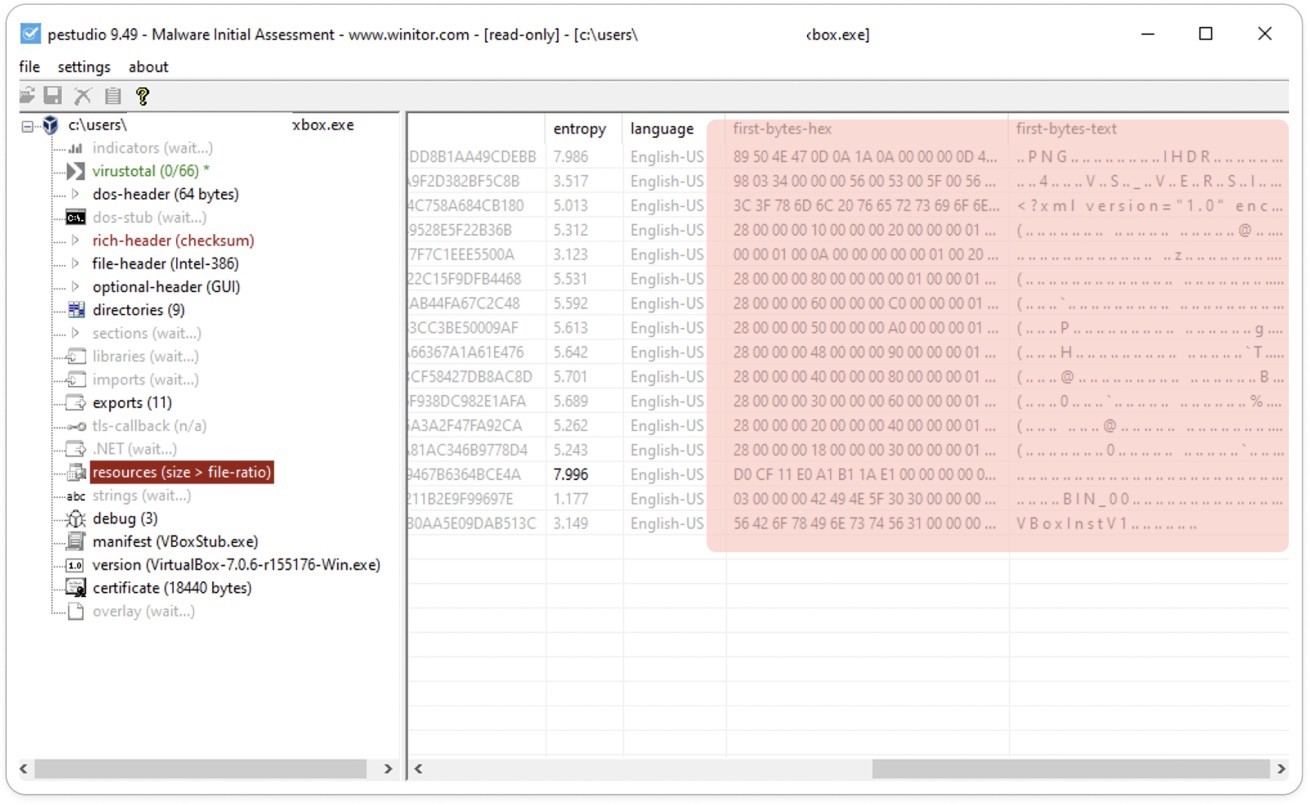
Fig 8: Resources
PEStudio examines a file’s resources, encompassing visual elements such as images and icons, and also provides access to hex-byte values.
Final Thoughts:
PEStudio is a robust tool that offers users an in-depth analysis of executable files, particularly those operating on the Windows platform. It supports security researchers in analyzing file structure and identifying key characteristics, and includes impressive features that allow for byte code analysis. For newcomers in this field, PEStudio is an excellent choice.
Keep learning and be on the lookout for my next blog!! PD