Attackers often clear event logs to cover their tracks. Though the act of clearing an event log itself generates an event, attackers who know ETW well may take advantage of tampering opportunities to cease the flow of logging temporarily or even permanently, without generating any event log entries in the process.
Blocking or even disabling host-based sensors, such as Event Tracing for Windows (ETW) will leave zero traces of attackers’ activities.
Event Tracing for Windows (ETW) is an efficient kernel-level tracing facility that lets you log kernel or application-defined events to a log file. You can consume the events in real time or from a log file and use them to debug an application or to determine where performance issues are occurring in the application.
Event Tracing Architecture
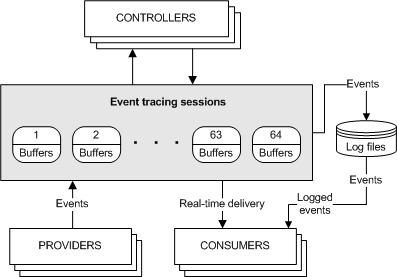
ETW works in three parts:
- Controllers start and stop Event Tracing Sessions. These sessions can subscribe to 1 or more providers, enabling the providers to start logging.
- Providers are where the events come from. Due to the sheer number of events some of these providers can generate, they’re disabled unless a Tracing Session is actively using it.
- Consumers take the generated events and handle them. The default method of handling events is outputting them to an .ETL file, but another example of a consumer is using the Windows API.
Logman
Logman.exe is a native Windows command-line utility, which is considered to be a Controllerto interact with the log kernel.We can use Logman to query, create, start and stop tracing sessions.
List all running trace sessions
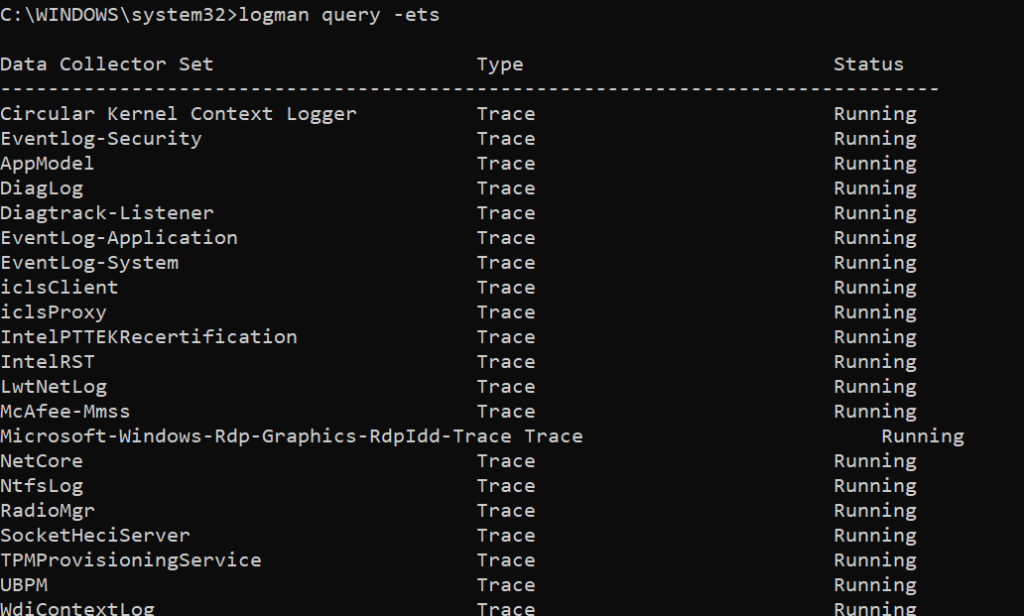
List all providers that a trace session is subscribed to
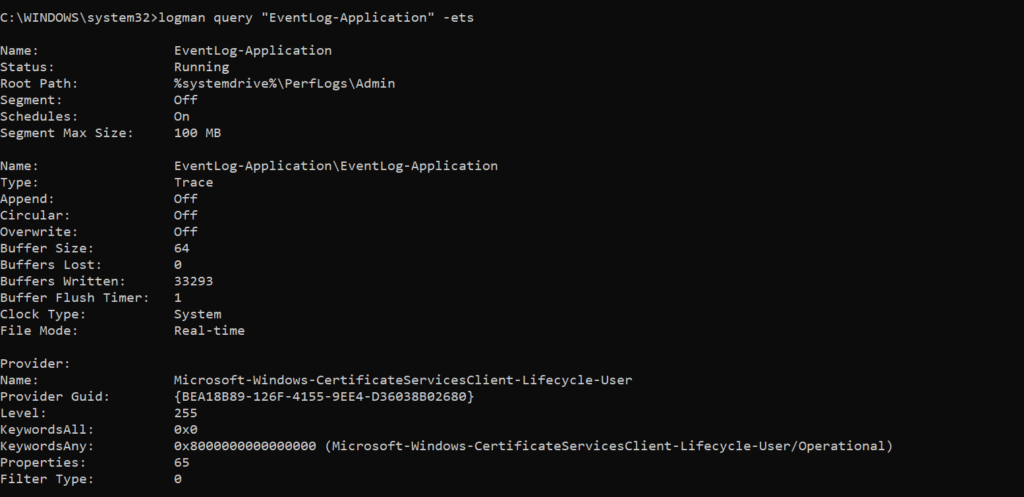
Each provider that the session is subscribed to, including the following parameters:
- Name: The name of the provider. A provider only has a name if it has a registered manifest, but it always has a unique GUID.
- Provider GUID: The unique GUID for the provider. The GUID and/or name of a provider is useful when performing research or operations on a specific provider.
- Level: The logging level specified. Standard logging levels are: 0 — Log Always; 1 — Critical; 2 — Error; 3 — Warning; 4 — Informational; 5 — Verbose. Custom logging levels can also be defined, but levels 6–15 are reserved. More than one logging level can be captured by ORing respective levels; supplying 255 (0xFF) is the standard method of capturing all supported logging levels.
- KeywordsAll: Keywords are used to filter specific categories of events. While the logging level is used to filter by event verbosity/importance, keywords allow filtering by event category. A keyword corresponds to a specific bit value. All indicates that, for a given keyword matched by, further filtering should be performed based on the specific bitmask in
KeywordsAll. This field is often set to zero. More information on All vs. Any can be found here. - KeywordsAny: Enables filtering based on any combination of the keywords specified. This can be thought of as a logical OR where KeywordsAll is a subsequent application of a logical AND.This corresponds to one or more event channels where the following channels are defined:
0x01 - Admin channel
0x02 - Debug channel
0x04 - Analytic channel
0x08 - Operational channel
- Properties: This refers to optional ETW properties that can be specified when writing the event. The following values are currently supported (more information here):
0x001 - EVENT_ENABLE_PROPERTY_SID
0x002 - EVENT_ENABLE_PROPERTY_TS_ID
0x004 - EVENT_ENABLE_PROPERTY_STACK_TRACE
0x008 - EVENT_ENABLE_PROPERTY_PSM_KEY
0x010 - EVENT_ENABLE_PROPERTY_IGNORE_KEYWORD_0
0x020 - EVENT_ENABLE_PROPERTY_PROVIDER_GROUP
0x040 - EVENT_ENABLE_PROPERTY_ENABLE_KEYWORD_0
0x080 - EVENT_ENABLE_PROPERTY_PROCESS_START_KEY
0x100 - EVENT_ENABLE_PROPERTY_EVENT_KEY
0x200 - EVENT_ENABLE_PROPERTY_EXCLUDE_INPRIVATE
From a detection perspective, EVENT_ENABLE_PROPERTY_SID, EVENT_ENABLE_PROPERTY_TS_ID, EVENT_ENABLE_PROPERTY_PROCESS_START_KEY are valuable fields to collect. For example, EVENT_ENABLE_PROPERTY_PROCESS_START_KEY generates a value that uniquely identifies a process. Note that Process IDs are not unique identifiers for a process instance.
- Filter Type: Providers can optionally choose to implement additional filtering; supported filters are defined in the provider manifest. In practice, none of the built-in providers implement filters as confirmed by running TdhEnumerateProviderFilters over all registered providers. There are some predefined filter types defined in
eventprov.h(in the Windows SDK):
0x00000000 - EVENT_FILTER_TYPE_NONE
0x80000000 - EVENT_FILTER_TYPE_SCHEMATIZED
0x80000001 - EVENT_FILTER_TYPE_SYSTEM_FLAGS
0x80000002 - EVENT_FILTER_TYPE_TRACEHANDLE
0x80000004 - EVENT_FILTER_TYPE_PID
0x80000008 - EVENT_FILTER_TYPE_EXECUTABLE_NAME
0x80000010 - EVENT_FILTER_TYPE_PACKAGE_ID
0x80000020 - EVENT_FILTER_TYPE_PACKAGE_APP_ID
0x80000100 - EVENT_FILTER_TYPE_PAYLOAD
0x80000200 - EVENT_FILTER_TYPE_EVENT_ID
0x80000400 - EVENT_FILTER_TYPE_EVENT_NAME
0x80001000 - EVENT_FILTER_TYPE_STACKWALK
0x80002000 - EVENT_FILTER_TYPE_STACKWALK_NAME
0x80004000 - EVENT_FILTER_TYPE_STACKWALK_LEVEL_KW
Enumerating all registered ETW providers
In the example Microsoft-Windows-PowerShell the provider has the following registry values set to default:
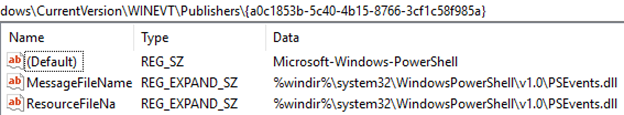
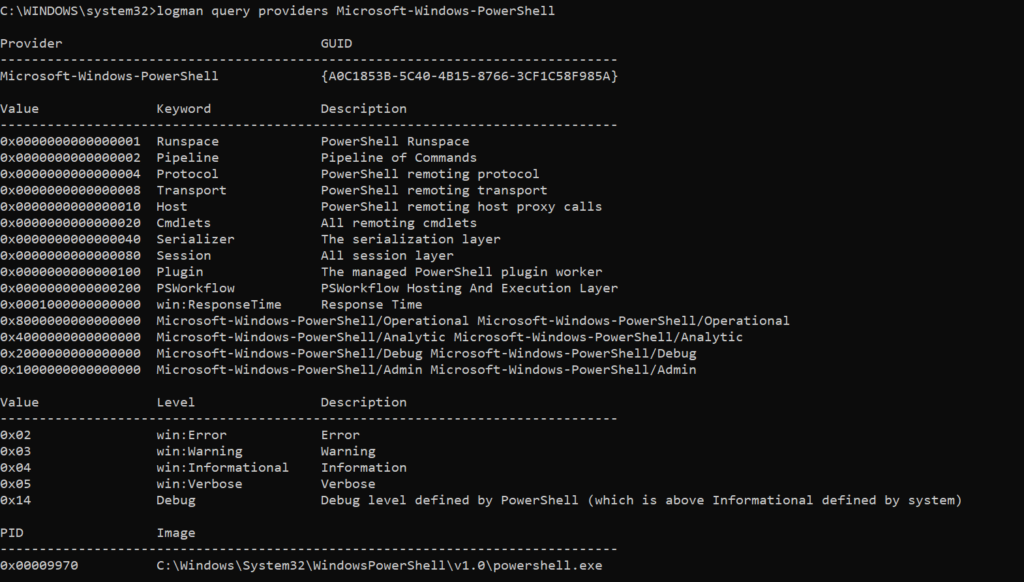
The listings show supported keywords and logging values, as well as all processes that are registered to emit events via this provider.
Hex Convert:
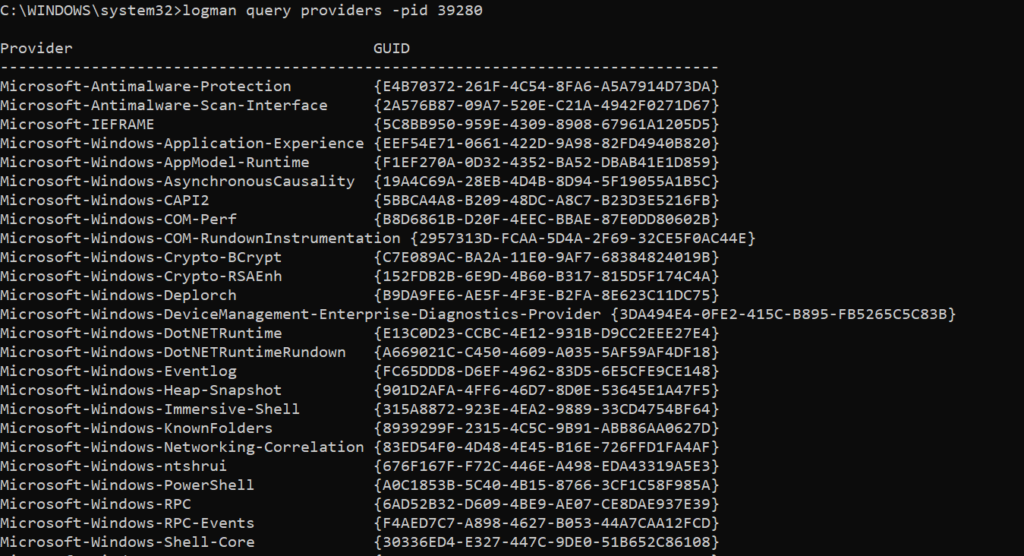
PID 39280 is tracked in logman which results in the Windows Defender service. The defender monitors the PowerShell providers for the anomalies.
ETW Tampering Techniques
Tampering techniques can generally be broken down into two categories:
- Persistent, requiring a reboot — i.e., a reboot must occur before the attack takes effect. Changes can be reverted but would require another reboot. These attacks involve altering autologger settings — persistent ETW trace sessions with settings in the registry. There are more types of persistent attacks than ephemeral attacks, and they are usually more straightforward to detect.
- Ephemeral — i.e., where the attack can take place without a reboot.
Autologger provider removal
Tampering category: Persistent, requiring reboot
Minimum permissions required: Administrator
Detection artifacts: Registry key deletion: HKLM\SYSTEM\CurrentControlSet\Control\WMI\Autologger\AUTOLOGGER_NAME\{PROVIDER_GUID}
Description: This technique involves the removal of a provider entry from a configured autologger. Removing a provider registration from an autologger will cause events to cease to flow to the respective trace session.
Example: The following PowerShell code disables Microsoft-Windows-PowerShell event logging:
Remove-EtwTraceProvider -AutologgerName EventLog-Application -Guid '{A0C1853B-5C40-4B15-8766-3CF1C58F985A}'
In the above example, A0C1853B-5C40-4B15-8766-3CF1C58F985A refers to the Microsoft-Windows-PowerShell ETW provider. This command will end up deleting the HKLM\System\CurrentControlSet\Control\WMI\Autologger\EventLog-Application\{a0c1853b-5c40-4b15-8766-3cf1c58f985a} registry key.
Provider “Enable” property modification
Tampering category: Persistent, requiring reboot
Minimum permissions required: Administrator
Detection artifacts: Registry value modification: HKLM\SYSTEM\CurrentControlSet\Control\WMI\Autologger\AUTOLOGGER_NAME\{PROVIDER_GUID} - EnableProperty (REG_DWORD)
Description: This technique involves alerting the Enable keyword of an autologger session. For example, by default, all ETW provider entries in the EventLog-Application autologger session are set to 0x41 which translates to EVENT_ENABLE_PROPERTY_SID and EVENT_ENABLE_PROPERTY_ENABLE_KEYWORD_0. EVENT_ENABLE_PROPERTY_ENABLE_KEYWORD_0 is not documented; it specifies that any events generated for a provider should be logged even if the keyword value is set to 0. An attacker could swap out EVENT_ENABLE_PROPERTY_ENABLE_KEYWORD_0 for EVENT_ENABLE_PROPERTY_IGNORE_KEYWORD_0, resulting in a value of 0x11, which would result in all events where the keyword is 0 to not be logged. For example, PowerShell eventing supplies a 0 keyword value with its events, resulting in no logging to the PowerShell event log.
Example: The following PowerShell code disables Microsoft-Windows-PowerShell event logging:
Set-EtwTraceProvider -Guid '{A0C1853B-5C40-4B15-8766-3CF1C58F985A}' -AutologgerName 'EventLog-Application' -Property 0x11
In the above example, A0C1853B-5C40-4B15-8766-3CF1C58F985A refers to the Microsoft-Windows-PowerShell ETW provider. This command will end up setting HKLM\System\CurrentControlSet\Control\WMI\Autologger\EventLog-Application\{a0c1853b-5c40-4b15-8766-3cf1c58f985a}\EnableProperty to 0x11. Upon rebooting, events will cease to be reported to the PowerShell event log.
An attacker is not constrained to using just the Set-EtwTraceProvider cmdlet to carry out this attack. An attacker could just modify the value directly in the registry. Set-EtwTraceProvider offers a convenient autologger configuration abstraction.
Alternative detection artifacts/ideas: If possible, it is advisable to monitor for modifications of values within the HKLM\SYSTEM\CurrentControlSet\Control\WMI\Autologger\AUTOLOGGER_NAME\{PROVIDER_GUID} registry key. Note that modifying EnableProperty is just one specific example and that an attacker can alter ETW providers in other ways, too.
ETW provider removal from a trace session
Tampering category: Ephemeral
Minimum permissions required: SYSTEM
Detection artifacts: Unfortunately, no file, registry, or event log artifacts are associated with this event. While the technique example below indicates that logman.exe was used to perform the attack, an attacker can obfuscate their techniques by using Win32 APIs directly, WMI, DCOM, PowerShell, etc.
Description: This technique involves removing an ETW provider from a trace session, cutting off its ability to supply a targeted event log with events until a reboot occurs, or until the attacker restores the provider. While an attacker must have SYSTEM privileges to perform this attack, it is unlikely that defenders will notice such an attack if they rely on event logs for threat detection.
Example: The following PowerShell code immediately disables Microsoft-Windows-PowerShell event logging until a reboot occurs or the attacker restores the ETW provider:
logman update trace EventLog-Application --p Microsoft-Windows-PowerShell -ets
Alternative Detection ideas:
- Event ID 12 within the Microsoft-Windows-Kernel-EventTracing/Analytic log indicates when a trace session is modified, but it doesn’t supply the provider name or GUID that was removed, so it would be difficult to confidently determine whether or not something suspicious occurred using this event.
- Providers can also be enumerated with wpr.exe utility too.
The frequency at which providers are removed from Application event logs in large environments is not currently known. As a fallback, it is still advised to log the execution of logman.exe, wpr.exe, and PowerShell in your environment.
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ((("Image" ilike '%\logman.exe') and ("Process CommandLine" ilike '%query%' or "Process CommandLine" ilike '%update%' or "Process CommandLine" ilike '%EventLog%')) or ("Image" ilike '%\powershell.exe' and ("Process CommandLine" ilike '%Remove-EtwTraceProvider%' or "Process CommandLine" ilike '%AutologgerName%' or "Process CommandLine" ilike '%EventLog%' or "Process CommandLine" ilike '%Set-EtwTraceProvider%' or "Process CommandLine" ilike '%Property%')) or "Image" ilike '%\wpr.exe')Splunk:
source="WinEventLog:*" AND (((Image="*\\logman.exe") AND (CommandLine="*query*" OR CommandLine="*update*" OR CommandLine="*EventLog*")) OR (Image="*\\powershell.exe" AND (CommandLine="*Remove-EtwTraceProvider*" OR CommandLine="*AutologgerName*" OR CommandLine="*EventLog*" OR CommandLine="*Set-EtwTraceProvider*" OR CommandLine="*Property*")) OR Image="*\\wpr.exe")Elastic Query:
((process.executable.text:*\\logman.exe AND process.command_line.text:(*query* OR *update* OR *EventLog*)) OR (process.executable.text:*\\powershell.exe AND process.command_line.text:(*Remove\-EtwTraceProvider* OR *AutologgerName* OR *EventLog* OR *Set\-EtwTraceProvider* OR *Property*)) OR process.executable.text:*\\wpr.exe)Arcsight:
(((((((sourceProcessName ENDSWITH "\logman.exe" OR destinationProcessName ENDSWITH "\logman.exe" OR deviceProcessName ENDSWITH "\logman.exe")) AND ((destinationServiceName CONTAINS "query" OR destinationServiceName CONTAINS "update" OR destinationServiceName CONTAINS "EventLog" OR deviceCustomString1 CONTAINS "query" OR deviceCustomString1 CONTAINS "update" OR deviceCustomString1 CONTAINS "EventLog"))) OR ((sourceProcessName ENDSWITH "\logman.exe" OR destinationProcessName ENDSWITH "\logman.exe" OR deviceProcessName ENDSWITH "\logman.exe")))) OR (((sourceProcessName ENDSWITH "\powershell.exe" OR destinationProcessName ENDSWITH "\powershell.exe" OR deviceProcessName ENDSWITH "\powershell.exe")) AND ((destinationServiceName CONTAINS "Remove-EtwTraceProvider" OR destinationServiceName CONTAINS "AutologgerName" OR destinationServiceName CONTAINS "EventLog" OR destinationServiceName CONTAINS "Set-EtwTraceProvider" OR destinationServiceName CONTAINS "Property" OR deviceCustomString1 CONTAINS "Remove-EtwTraceProvider" OR deviceCustomString1 CONTAINS "AutologgerName" OR deviceCustomString1 CONTAINS "EventLog" OR deviceCustomString1 CONTAINS "Set-EtwTraceProvider" OR deviceCustomString1 CONTAINS "Property"))) OR sourceProcessName ENDSWITH "\wpr.exe" OR destinationProcessName ENDSWITH "\wpr.exe" OR deviceProcessName ENDSWITH "\wpr.exe")) AND type != 2 | rex field = flexString1 mode=sed "s//Sigma: aagh/g"CarbonBlack:
((process_name:*\\logman.exe AND process_cmdline:(*query* OR *update* OR *EventLog*)) OR (process_name:*\\powershell.exe AND process_cmdline:(*Remove\-EtwTraceProvider* OR *AutologgerName* OR *EventLog* OR *Set\-EtwTraceProvider* OR *Property*)) OR process_name:*\\wpr.exe)Crowdstike:
(((ImageFileName="*\\logman.exe") AND ((CommandLine="*query*" OR CommandLine="*update*" OR CommandLine="*EventLog*") OR (CommandHistory="*query*" OR CommandHistory="*update*" OR CommandHistory="*EventLog*"))) OR (ImageFileName="*\\powershell.exe" AND ((CommandLine="*Remove-EtwTraceProvider*" OR CommandLine="*AutologgerName*" OR CommandLine="*EventLog*" OR CommandLine="*Set-EtwTraceProvider*" OR CommandLine="*Property*") OR (CommandHistory="*Remove-EtwTraceProvider*" OR CommandHistory="*AutologgerName*" OR CommandHistory="*EventLog*" OR CommandHistory="*Set-EtwTraceProvider*" OR CommandHistory="*Property*"))) OR ImageFileName="*\\wpr.exe")Fireeye:
(metaclass:`windows` ((process:`*\logman.exe` args:[`query`,`update`,`EventLog`]) OR (process:`*\powershell.exe` args:[`Remove-EtwTraceProvider`,`AutologgerName`,`EventLog`,`Set-EtwTraceProvider`,`Property`]) OR process:`*\wpr.exe`))GrayLog:
((Image.keyword:*\\logman.exe AND CommandLine.keyword:(*query* *update* *EventLog*)) OR (Image.keyword:*\\powershell.exe AND CommandLine.keyword:(*Remove\-EtwTraceProvider* *AutologgerName* *EventLog* *Set\-EtwTraceProvider* *Property*)) OR Image.keyword:*\\wpr.exe)Logpoint:
((Image IN "*\\logman.exe" CommandLine IN ["*query*", "*update*", "*EventLog*"]) OR (Image="*\\powershell.exe" CommandLine IN ["*Remove-EtwTraceProvider*", "*AutologgerName*", "*EventLog*", "*Set-EtwTraceProvider*", "*Property*"]) OR Image="*\\wpr.exe")Microsoft Defender:
DeviceProcessEvents | where (((FolderPath endswith @"\logman.exe") and (ProcessCommandLine contains "query" or ProcessCommandLine contains "update" or ProcessCommandLine contains "EventLog")) or (FolderPath endswith @"\powershell.exe" and (ProcessCommandLine contains "Remove-EtwTraceProvider" or ProcessCommandLine contains "AutologgerName" or ProcessCommandLine contains "EventLog" or ProcessCommandLine contains "Set-EtwTraceProvider" or ProcessCommandLine contains "Property")) or FolderPath endswith @"\wpr.exe")Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where (((NewProcessName endswith @'\logman.exe') and (CommandLine contains 'query' or CommandLine contains 'update' or CommandLine contains 'EventLog')) or (NewProcessName endswith @'\powershell.exe' and (CommandLine contains 'Remove-EtwTraceProvider' or CommandLine contains 'AutologgerName' or CommandLine contains 'EventLog' or CommandLine contains 'Set-EtwTraceProvider' or CommandLine contains 'Property')) or NewProcessName endswith @'\wpr.exe')RSA Netwitness:
(((Image contains '\logman\.exe') && (CommandLine contains 'query', 'update', 'EventLog')) || ((Image contains 'powershell.exe') && (CommandLine contains 'Remove-EtwTraceProvider', 'AutologgerName', 'EventLog', 'Set-EtwTraceProvider', 'Property')) || (Image contains 'wpr.exe'))SumoLogic:
(_sourceCategory=*windows* AND ((((Image = "*\logman.exe") AND (CommandLine = "*query*" OR CommandLine = "*update*" OR CommandLine = "*EventLog*")) OR (Image="*\powershell.exe" AND (CommandLine = "*Remove-EtwTraceProvider*" OR CommandLine = "*AutologgerName*" OR CommandLine = "*EventLog*" OR CommandLine = "*Set-EtwTraceProvider*" OR CommandLine = "*Property*")) OR Image="*\wpr.exe")))Sentinel One:
((TgtProcImagePath endswith "\logman.exe" AND TgtProcCmdLine in contains anycase ("query", "update", "EventLog")) OR (TgtProcImagePath endswith "\powershell.exe" AND TgtProcCmdLine in contains anycase ("Remove-EtwTraceProvider", "AutologgerName", "EventLog", "Set-EtwTraceProvider", "Property")) OR TgtProcImagePath endswith "\wpr.exe")Securonix:
index = activity AND (rg_functionality = "Microsoft Windows" AND (((((@customstring54 ENDS WITH "\logman.exe") OR (@destinationprocessname ENDS WITH "\logman.exe")) AND (@resourcecustomfield3 CONTAINS "query" OR @resourcecustomfield3 CONTAINS "update" OR @resourcecustomfield3 CONTAINS "EventLog")) OR ((@customstring54 ENDS WITH "\logman.exe") OR (@destinationprocessname ENDS WITH "\logman.exe"))) OR ((@customstring54 ENDS WITH "\powershell.exe" OR @destinationprocessname ENDS WITH "\powershell.exe") AND (@resourcecustomfield3 CONTAINS "Remove-EtwTraceProvider" OR @resourcecustomfield3 CONTAINS "AutologgerName" OR @resourcecustomfield3 CONTAINS "EventLog" OR @resourcecustomfield3 CONTAINS "Set-EtwTraceProvider" OR @resourcecustomfield3 CONTAINS "Property")) OR @customstring54 ENDS WITH "\wpr.exe" OR @destinationprocessname ENDS WITH "\wpr.exe"))References:
bmcder.com/blog/a-begginers-all-inclusive-guide-to-etw
docs.microsoft.com/en-us/windows-hardware/drivers/devtest/wpp-software-tracing
blog.palantir.com/tampering-with-windows-event-tracing-background-offense-and-defense-4be7ac62ac63



































