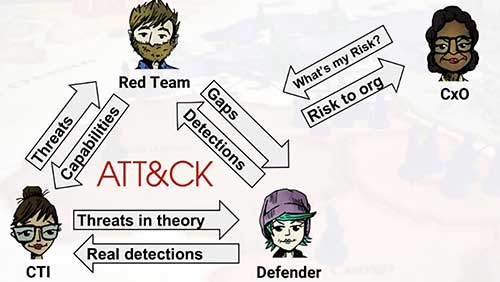
Introduction
MITRE | ATTACK is an open-source framework that mainly focuses to understand or familiarize yourself with adversary tactics and techniques based on real-world observations, In general, MITRE ATTACK is a collection of attack techniques used by an adversary during breaches or even for defensive engagement like [Threat modelling, Threat Hunting].
ATT&CK MATRIX
ATT&CK MATRIX is a collection of the attacker’s tactics and techniques based on real-world observations. Which are been generally used to understand the attacker models, methodologies, and mitigation. Hence it is combinations of TTP [Tactics, Technique, Procedure]
Tactics → Advisory end goal
Technique → How it can be archived
Procedure → Implementation of Techniques
ATT&CK MATRIX included 14 Tactics with 201 unique techniques which are been used by an attacker during breaches,
TACTICS & TECHNIQUES
ATTACK MAP
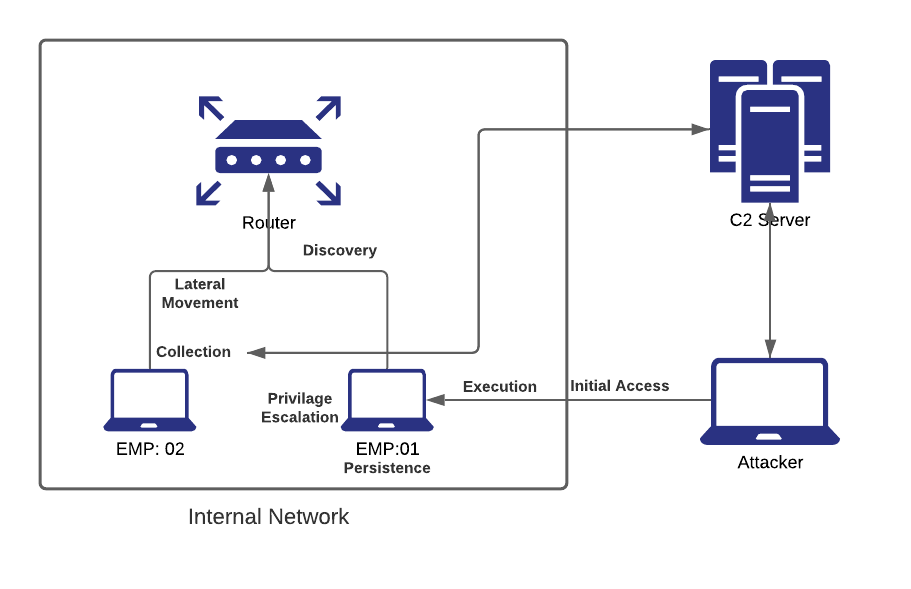
- Reconnaissance
A Process of gathering sensitive information about the target environment via Active and Passive scanning techniques.
Active Scanning –
Collecting information by interacting with the target system [IP scan, PORT scan, vulnerability scan, etc]
Passive Scanning –
Collecting information without iterating with the target system
This gathered information will be helpful in post-compromise objectives.
Resource Development
A Process of creating or establishing a resource that can be supported in further attack operations, this phase involves in purchasing of IP, Domains and C2c servers or BOTS for the execution of attacks
- Initial Access
A Process of gaining initial access to an internal environment by checking for various vulnerable entry points, The most challenging part for every adversary is to get an initial foothold with the target environment.
Also Read: Latest Cyber Security News – Hacker News !
- Execution
A process of executing a malicious code or script on the target environment via a local or remote method, After a successful foothold with the target environment the adversary needs some communication medium to execute or initiate their malicious code. This can be achieved by various tactics like IPC, DLL and even WMI scripts.
- Persistence
A Process of Maintaining a stable connection with the target environment, the initial access and persistence look similar but the major difference would be the connection state in initial access the connection state would be temporary [if a system gets shutdown or restart its gets disconnected] but in persistence phase, the connection state would be permanent [even if the system gets shut down or restart the adversary can establish a connection with the target environment].
- Privilege Escalation
A Process of Gaining higher-level access within the target environment can be done at both system and network level, this can be achieved by any bug or misconfigurations.
- Defensive Evasion
A process of evading from any antivirus or anti-malware programs which has been configured at the target environment,
- Credential Access
A process of gathering or stealing all the sensitive credentials which have been available in the target environment, this process makes them harder to detect and provides the opportunity to create more accounts to help achieve their goals.
- Discovery
A process of discovering the entire internal network, this process involves exploring the entire infrastructure and the working of the organization
- Lateral Movement
The process of gaining control of various systems in the internal environment involves the process of moving from one computer to another in the internal environment using the legitimate credential [credential which are been acquired in the credential access phase],
- Collection
The process of gathering sensitive information from various sources, sources include various drive types, browsers, audio, video, and email. Common collection methods include capturing screenshots and keyboard input.
- Command & Control
A process of communicating with the compromised system in the target environment involves transferring malicious commands or payloads to the target system.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Exfiltrate
A process of transferring data from the compromised system to the attacker PC, this process includes packing, encryption and compression; these steps are used to avoid getting detected.
- Impact
This includes the impact of the attacks, impact can include destroying or tampering with data. In some cases, business processes can look fine but may have been altered to benefit the adversaries’ goals.
Benefits of using the MITRE ATT&CK framework
- To understand the threat actors Behaviors and rely on TTP’s rather than Ioc’s ( Indicator of compromise ).
- Indicators of attack ( IOA ) leverages security operations to clarify threats and maps to an appropriate attack accordingly.
- Used to understand post-compromise detection and Helps to Identify, Detect, Monitor, and Respond against real-time cyber attacks
- Red teams can simulate adversaries TTP’s and Security operations can try to detect such behaviors with correlation rules, Threat hunting.
- Functioning a red team assessment provides soc teams to aware of real-world attacks and as the organization can find the missing gaps in the existing security controls.
- Improvement in the Meantime detection ( MTTD ) and mean time resolution ( MTTR ).
- The exchange of threat intelligence provides more insights for security analysts.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
APPLICATIONS OF MITRE ATT&CK

Conclusion
Implementing the Mitre Framework will ensure the organization stays top on attack behaviors, prioritizes the alert and incident response time faster and better way.