If your website has been compromised with malware, it’s likely that your database has been infected as well. If this is the case, you may take efforts to remove all malware from your site’s code and files but still notice malware behavior.
This could be due to the malware infecting the database as well. This is extremely common, but there is a solution to recover the WordPress database that has been corrupted. Users must immediately scan and clear the database in order to achieve this.
This article explains how to manually scan a WordPress database.
Scan & Clean WordPress Database Manually
Scanning and cleaning the database via manually will take a long time. Furthermore, there’s a considerable risk you’ll overlook malware that’s been hidden. Furthermore, if you make any mistakes while cleaning the database, such as deleting the wrong table or eliminating non-malicious code, may result in a broken website.
As a result, we suggest using a manual method to scan and clean your database. If you have some technical skills and prefer to proceed, we’ll guide you through the steps to clean your database of malware. But first, make sure you have a complete backup of your WordPress site.
Export Your DB SQL
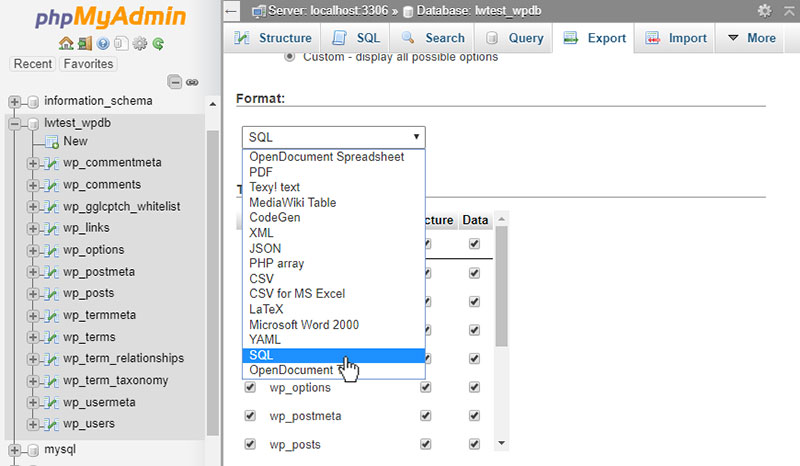
To search your DB, you would need to export it as text. Using the database tool provided by your web host, you can perform this export.
Finally, open the downloaded database file in notepad and search for malicious code.
There are two common malware signs in your database. – Unknown Links or iFrames, as well as malicious PHP functions. We’ll show you how to manually look for these.
1. Malicious PHP Functions: One very common way of identifying infection in the database is the presence of potentially malicious codes like base64_decode, gzinflate, error_reporting(0), and shell_exec. That said, there is a drawback to this method. The codes are not always malicious. Sometimes programmers are known to use such code to execute certain functions.
base64_decode: This function is used to decode data encoded with base64. Since WordPress is open-source, it is very unlikely to contain encoded information. This function in your DB would usually indicate that a hacker is trying to hide or mask their malicious code.
search for string – “base64_decode( ” or “base64_decode (”
gzinflate: This function is used to decode (inflate) data that is encoded (deflated). Same as above, an open-source platform should not contain encoded sections. The presence of this function thus points to a hacker trying to hide their activity.
search for string – “gzinflate(” or “gzinflate (”
eval: This language construct tries to process any string as valid PHP code. Because this construct is very dangerous, php.net discourages its usage, and most programmers avoid it. If you find this construct in your DB, it is very likely infected.
search for string – “eval(” or “eval (”
error_reporting(0): When the zero parameters is used for this function, code errors will neither be displayed nor logged. This usage is very unlikely in any web application. If found, this may indicate a hacker testing out various codes but hiding the error reports so the site owner does not find out.
search for string – “error_reporting(0)” or “error_reporting (0)
shell_exec: The shell is the layer in a Unix operating system that processes commands. Using the shell_exec function, hackers can execute commands at the operating system (server level). Since this enables them to take over an entire server, it is a prime target for hackers.
search for string – “shell_exec(” or “shell_exec (”
GLOBALS: Disabled by default in versions of PHP since 2002 (v. 4.2.0), “GLOBALS” can pose a security risk when not implemented thoughtfully and carefully. If used in conjunction with user input, there is a much higher risk of unintended variable manipulation, which can lead to a compromised site. As a result, most applications and sites these days do not use global variables.
search for string – “Globals”
Also Read: Web Malware Removal | How to Remove Malware From Your Website?
2. Unknown Links or iFrames: Hackers insert unknown links and iFrames into the website and disguise them so that the site owner can’t identify the link. A good way of fishing out these links are by examining your website code. You can use a tool named Online cURL to display and review the codes on your website.

You must clean your database once you’ve found evidence of infection. To clean the database, you will have to restore a copy of the clean database. This is only possible if you’ve been backing up your WordPress database.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
The malware scanning and database cleaning for your WordPress database are now complete.
Conclusion
Getting your database hacked could be a wake call that you needed to take security more seriously. While your website is no longer in danger, there is no guarantee that it will not be hacked in the future. If you wish to prevent future attacks, you should implement some WordPress security measures, such as installing a security plugin and scanning your WordPress database for malware on a regular basis. A plugin will identify malware, clean it up, and provide security steps to safeguard your website from future hacking attempts.
Contact Us for Malware removal – [email protected]