OVERVIEW
Automation in cyber security is still be more challenging for many researchers many process like SOAR is still under development in that case developing a automation tool for RED teaming is some what harder than all, but a researched team name RED CANARY has published a revolutionary automated Threat detection tool and attack technique tools which consist of many advantages and key features, in this documentation we are going to see implementation and working of ATH.
AtomicTestHarshness an open-source automated attack technique tool that executes specific Mitre attack techniques on a host machine and generates test output, which has been used to validate the Mitre attack technique execution and detection on the host system
AtomicTestHarnesses streamlines the execution of attack technique variations and validates that the expected telemetry surfaces in the process.
Getting Started
A custom-created PowerShell module contains a suite of tools for simulating attack techniques for attack execution and detection on the host machine, Foundation of detection is made up of our ability to observe a technique, its been of some three test process they are
3 major steps
- Run [Deploying or executing the tool on the host machine]
- Review [Reviewing the results of your tests, improving your understanding of the environment
- Repeat
Installation/Deployment
ATH can be installed using 2 ways
- Powershell gallery
- Manually import method
Powershell Gallery
User can directly get installs the ATH from the PowerShell Gallery
Install-Module -Name AtomicTestHarnesses -Scope CurrentUser
The above-given PowerShell script used to get directly download the ATH module on the PowerShell module directory.
Manually import method
For manual installation from GitHub, you can follow these steps
- The AtomicTestHarnesses folder must reside in a PowerShell module directory %ProgramFiles%\WindowsPowerShell\Modules
Or
It can be directly get imported to the root directory from the GIT, for the manual installation from GIT requires some sort of steps needs to be followed which are mentioned below
STEP: 1
Below mention GIT link repository allow you to download ATH
Link: ATH
STEP: 2
After downloading it from GIT just extract it, you can observe the list of following files
STEP: 3
Open the PowerShell and navigate to the ATH directory which you successfully downloaded and extracted

Import-Module \AtomicTestHarnesses-master\AtomicTestHarnesses.psd1
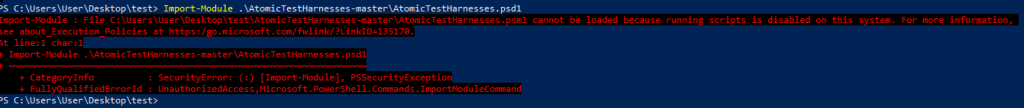
By default, Windows os will disable the script execution due to some sort of security reasons, in case of ATH need to enabled so remodify the script execution policy to enable state, the following PowerShell queries will be used to reassign the script execution policy.
Set-ExecutionPolicy Unrestricted
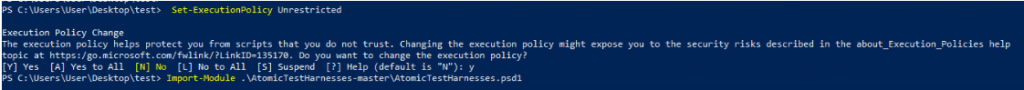
After importing and reset the execution state, import the ATH module

Import-Module .\AtomicTestHarnesses-master\AtomicTestHarnesses.psd1
This time it can be imported successfully without any sort of errors and the ATH has been successfully imported to the Host machine
Attack Techniques
Initially, the Red Canary Research team has included the three attack techniques of Mitre framework, but later they planned to gradually add new techniques over time
- Access Token Manipulation: Parent PID Spoofing
- Signed Binary Proxy Execution: Compiled HTML File
- Signed Binary Proxy Execution: Mshta
Access Token Manipulation: Parent PID Spoofing
Access token manipulation is a process of cloning or duplicating an existing parent process[ppid] of the target system
Adversaries usually create a new process with the stolen token of [PPID], hence this would make the new process more privileged this type of attack has been used to evade defence and get privileged access on the target system
| ID | T1134.004 |
| Sub-technique of: | T1134 |
| Tactics: | Defence Evasion, Privilege Escalation |
| Platforms: | Windows |
| Permissions Required: | Administrator, User |
Signed Binary Proxy Execution: Compiled HTML File
Signed Binary is a process of abusing binaries that are signed and trusted, generally many organizations trust everything that comes from some top companies like Microsoft. Signing means using a public-private encryption scheme, where you sign the binary with a public key, and the client uses the private key to verify that you really did sign the key.
Example:
PSExec is a command-line tool which allows users to execute processes on remote systems, probably the best-known executable that is signed by Microsoft that has been used maliciously by the attackers to execute code on a remote system using the SMB service
The above could be the best example for the signed binary execution
Microsoft HTML file ?
Microsoft Compiled HTML Help is commonly distributed as part of the Microsoft HTML Help system, which usually gets executed under Internet Explorer[IE]
Attackers usually custom creates the own malicious HTML files (.chm) payload which gets triggered when the user executes, which has been typically used to bypass application control
| ID | T1218.001 |
| Sub-technique of: | T1218 |
| Tactics: | Defence Evasion |
| Platforms: | Windows |
| Permissions Required: | User |
Signed Binary Proxy Execution: Mshta
Mshta.exe is a utility that executes Microsoft HTML Applications (HTA) files. Mshta is used to bypass application defence and execute outside of the browsers.
Adversaries usually target Mshta to proxy execution of malicious .hta files and Javascript or VBScript through a trusted Windows utility.
| ID | T1218.005 |
| Sub-technique of: | T1218 |
| Tactics: | Defence Evasion |
| Platforms: | Windows |
| Permissions Required: | User |
Let’s get started
After successful installation and deployment of ATH lets starts testing AtomicTestHarnesses module on the host system,
Lab
- List of all functions are available on ATH
- Invoke-ATH functions
- Help command and documentation
List of all functions are available on ATH
A Simple Powershell query which has been used to list all sort of function available on the module
Get-Command -Module AtomicTestHarnesses
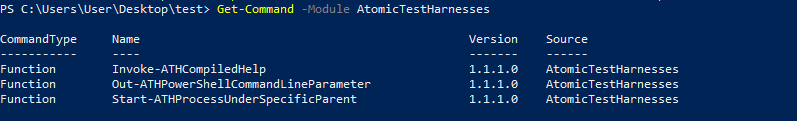
In this output, we can observe the list of Name and its relevant version of the attack technique, the main feature of ATH is the simple queries and its execution
Invoke-ATH functions
It’s time for action let’s start to execute the ATH module on the host and we can observe the automatic execution of ATH module on the host machine with the output, as same as implementation, executing ATH is been more simple than we expect the user can easily execute the ATH functions using the following command
Invoke-ATHHTMLApplication
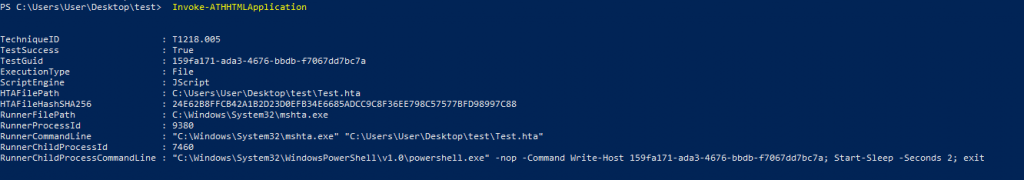
When the above-given command gets executed we can observe a detailed output of the specific attack with the relevant technique I’D and the Test result, in the test result you can generally observe [True/False] based result, A value of `true` will indicate that the specific technique executed without issue. Having such confidence can dramatically reduce root cause analysis time when diagnosing test versus detection failures.
In the case of HTA execution, HTA content can contain embedded Windows Script Host (WSH)—e.g. VBScript, JScript)—script code and execute it. on the host machine
.
Help command and documentation
The main goal of ATH is to “getting up and running as easy as possible” as they just created a well-defined help and documentation for ATH, the following command has been used to list the documentation.
Get-Help Invoke-ATHHTMLApplication -Full
This entire documentation includes the overall description and the parameters which are been used in ATH.
Conclusion
The documentation will help you to understand the working and implementation of ATH on the host machine for attack execution and threat-based detections, In part two of this blog series, we’ll explain in great depth of ATH like invoking the atomic scripts and methodology for identifying relevant variations on a given technique.
\



































