As part of its normal operations, the typical Windows PC runs dozens of common services. The essence of the malware game these days is hiding in the shadows, which means that everything may be exploited. Security Analysts may believe that they can distinguish the difference between benign and malicious Windows services; however, some of these services are hard to recognize.
The tougher it is for security administrators to identify malware that is hidden, especially if it appears to be genuine Windows activity. The newest attacks leverage the same or comparable Windows services capabilities that attackers have previously exploited, and they work on even the most recent versions of Windows.
We have a handful of mitigation strategies herein that we have probably never seen before, but malware authors are increasingly targeting them.
1-Remote Service:
- Remote Desktop Services (RDS), formerly known as Terminal Services in Windows Server 2008 and earlier versions, is a Microsoft Windows component that allows a user to control a remote computer or virtual machine over a network connection.
- We can open RDS via RUN prompt with the command “MSTSC” (Microsoft Terminal Services Client is the command line interface to run the Microsoft Remote Desktop (RDP) client).
- Zero-day vulnerabilities generally present the most wide-open vulnerabilities, because no patch has yet been created. RDS, though widely used, has some particularly dangerous published vulnerability.
- There are few use-cases based on static behavioral indicators and independently from the used utilities. Let have a look into it.
i) Rules based on the remote service using legit windows built-in utilities:
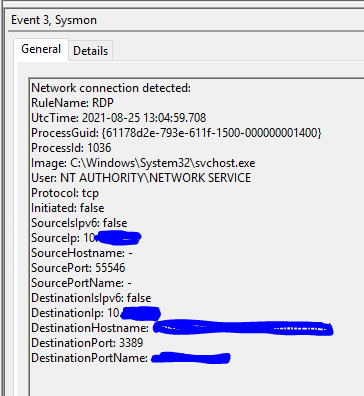
For example, an attacker is executing an “sc” command to create remotely a new service “remotesvc” on the destination host that persists system reboot and executes cmd.exe. From the source machine, we can observe logs for sc.exe connecting to a remote host, and source|destination ports are both dynamic RCP port numbers [TCP 49152-65535].
The following are the most noteworthy observed occurrences on the target machine:
A–Windows’s built-in observed key events:
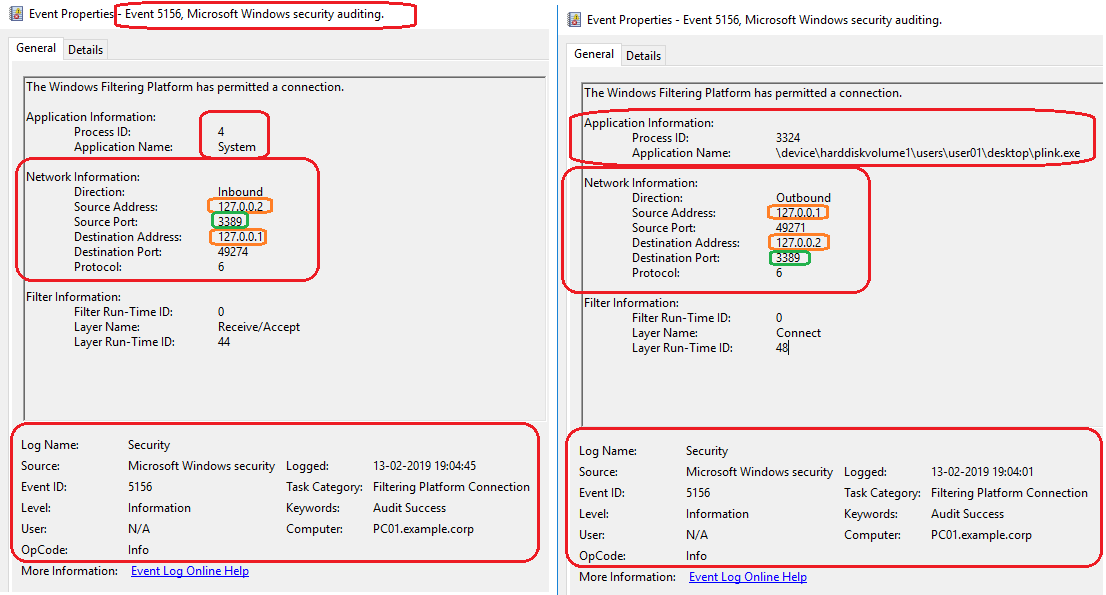
- The Event ID 5156 will be logged since the Windows Filtering Platform has allowed a connection. This event documents each time WFP allows a program to connect to another process (on the same or a remote computer) on a TCP or UDP port.
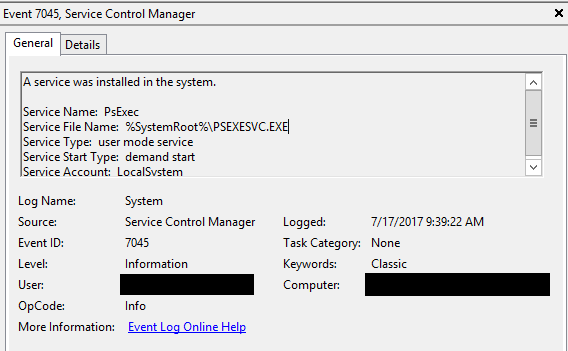
- The Event ID 7045 will be logged on the destination host since a service was installed on the system (As per the example, we have created a service on source host)
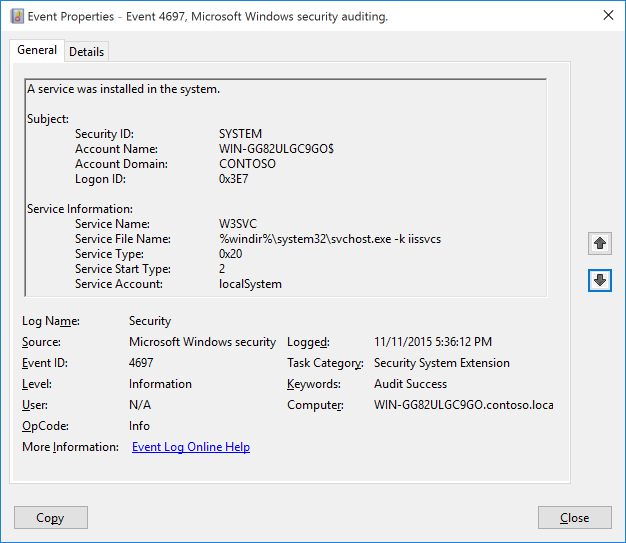
- If the organization has activated Security System Extension in the Advanced Audit Policy GPO, we will see Event ID 4697, which is equivalent to 7045, in the security events. The Event 4697 will be logged if OS version is Server 2016 or Windows 10. This event documents each time when a new service was installed by the user indicated in the subject. Subject often identifies the local system (SYSTEM) for services installed as part of native Windows components and therefore you can’t determine who actually initiated the installation.
Also Read: How to Detect Windows Sensitive Privilege Manipulation
Mitigation:
Create a rule based on standard remote service creation with windows built-in services event ID:
WinBuiltin – [EventID=5156 and ApplicationName like “*\services.exe” and SourceAddress!= DestinationAddress and SourcePort>=49152 and DestinationPort>=49152 and SourceAddress!-Null and DestinationAddress!=Null] followed by (EventID=7045 or EventID=4697) within 1 min and same ComputerName.
B–Sysmon’s observed key events:
- Registry value will be set to “HKLM\System\CurrentControlSet\services\<svcname>\*” on the destination host with the sysmon RegValueSet ID 13. (As per the example, we have created a service on source host)
- Network connection will be detected with the Sysmon Network Connect ID 3. The windows Event ID 5156 and the sysmon ID 3 are the same since they both carry the identical information about incoming and outgoing network connections from the services.exe process to the command’s source machine. This is a good sign of remote interaction with the target machine’s service control manager.
Mitigation:
Create a rule based on standard remote service creation with sysmon event ID:
Sysmon -[EventID=13 and TargetObject like “HKLM\System\Current ControlSet\services \*”] followed by [EventID=3 and Source IP != Destination IP and SourcePort>=49152 and DestinationPort>=49152 and Image like “*\services.exe” and SourceIP!=Null and Destination IP!=Null] within 1 minute and Same ComputerName.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
ii) Rules based on the remote service using external utilities:
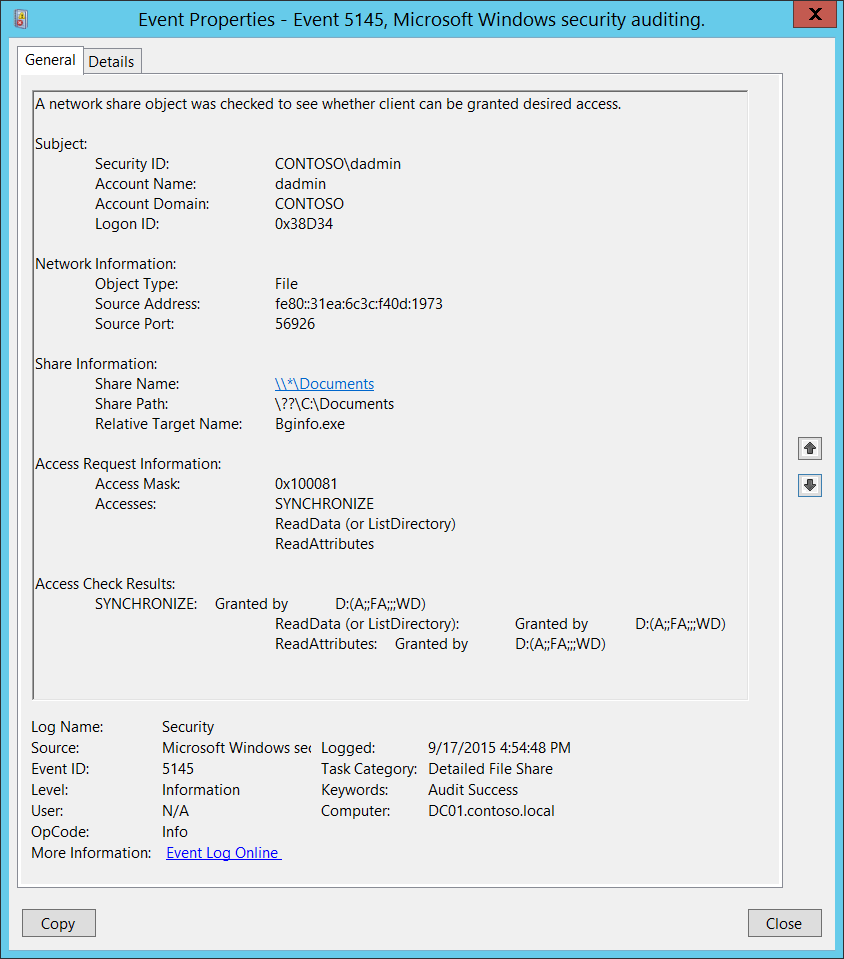
For an attacker to go laterally and broaden the compromise, third-party utilities like psexec, paexec, psexec_psh, remcom, etc., are highly beneficial. For example, if the psexec service is installed on the destination host. The remote session is started from source to destination. In this case, Event ID 5145 will be logged on to the destination host. The event will be logged since a network share object was checked to see whether the client can be granted desired access.
Mitigation:
Enable a rule based on the utility psexec service along with the Event ID and with the related event ID fields.
WinBuiltin – [EventID=5145 and ShareName-(\\*\ADMINS or \\*\C$) and event.payloads contains “WriteData”] followedby [EventID=5145 & ShareName=’\\*\IPC$’ and RelativeTargetName:’svcctl’)] within 1min and with Same (AccountName, SourceAddres, Port] and Same ComputerName
iii) Other Remote Service rules:
Rule 1:
Hunt for network interactive login followed by whenever a new service was installed in the system with the same logonid. Because, whenever a login is initiated, there will be a unique logonid which will be logged in every following winevent log until the session ends.
EventId 4624 & LogonType=3 followed by EventId 4697 with same Logonid witin 1 min
Rule 2:
Hunt for the process which attempts an account logon by explicitly specifying that account’s credentials along with the process name “sc.exe”
EventId 4648- ProcessName: c:\windows\system32\sc.exe (or Syswow64) and Target Server!=localhost or ‘-’
2-Suspicious processes:
When attempting to gain access to a Remote Desktop Gateway, the attacker will almost certainly be encountered with such a restricted environment. As part of the connection establishment, an application is launched on the terminal server. It could be a Remote Desktop Protocol connection window for local resources, Office Packets in File Explorer, or any other software.
The attacker wants to get access to the command execution process in order to run CMD or PowerShell scripts. Several tried-and-true methods for escaping the Windows sandbox may be useful here.
Mitigation:
Hunt with the below-mentioned Windows/Sysmon Event IDs along with the mentioned process names.
[4688, Sysmon_1, Sysmon_13, 4697, 7045] and Service BinPath or Process Name is in [cmd.exe, powershell.exe, cscript.exe, rundll32.exe, regsvr32.exe, regsvcs.exe, regasm.exe, wmic.exe]
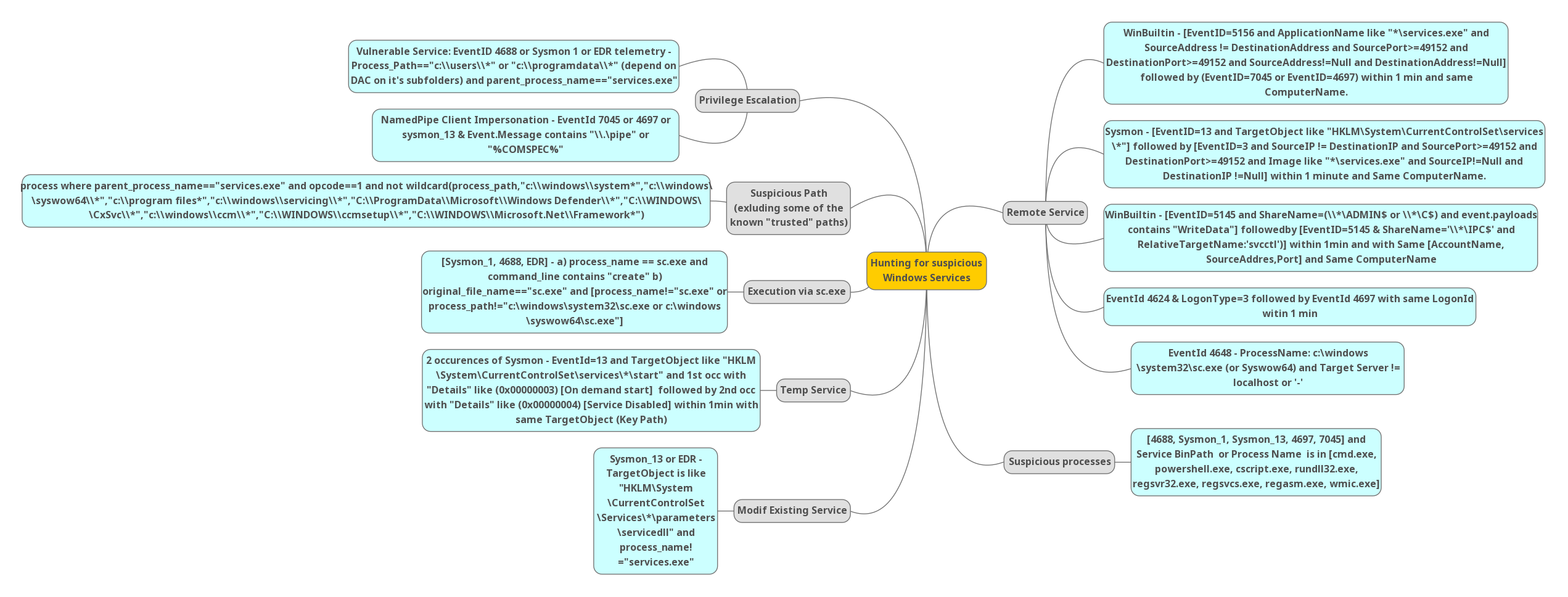
3-Privilege Escalation:
Now day’s attackers are mostly targeting to gain Privilege as a first step since after that they can execute more stuff.
Mitigation:
Rule 1:
Hunt for the new process creation along with the below-mentioned process path and the parent process needs to be “services.exe”
Vulnerable Service: EventID 4688 or Sysmon 1 or EDR telemetry-Process Path=”c:\users\\*” or “c:\\programdata\\*” (depend on DAC on it’s subfolders) and parent process name=”services.exe”
Rule 2:
- Hunt for new service installation by the user which will be logged with the Event ID 7045 or 4697 or with the sysmon RegistryEvent value set 13 which will be logged if the Registry value modification was done, along with the message “pipe” OR “COMSPEC”.
- “COMSPEC” just points to cmd.exe, so both commands will do the same thing. The majority of security analysts were unaware of “COMSPEC,” and no rules will be written using it. So, it is incredibly easy for attackers to escape.
NamedPipe Client Impersonation-Eventld 7045 or 4697 or sysmon_13 & Event Message contains “\\.\pipe” or “%COMSPEC%”
4-Suspicious Path (excluding some of the known “trusted” paths):
Security engineers should be familiar with known process paths to exclude from the alert. Or else False positives will be creating noise and fill the pool.
Mitigation:
Hunt for the process where the parent process is “services.exe” by excluding the known process path.
process where parent_process name==”services.exe” and opcode==1 and not wildcard(process_path, “c:\\windows\\system*”, “c:\\windows\ \syswow64\\*”, “c:\\program files*”, “c:\\windows\\servicing\\*”, “C:\\ProgramData\\Microsoft\\Windows Defender\\*”, “C:\\WINDOWS\ \CxSvc\\”, “c:\\windows\\ccm\\*”, “C:\\WINDOWS\\ccmsetup\\*, “C:\\\WINDOWS\\Microsoft.Net\\framework*”)
Also Read: Windows Service Creation and Malware Detection Methods
5-Execution via sc.exe:
One technique to execute programs remotely and have them persist beyond system reboots is to interact with Windows services remotely. It can be done with a variety of tools such as sc.exe, WMI, etc.
Monitoring sc.exe process execution command line and network connections are good but not resilient enough and can be bypassed easily as detection because adversaries rename sc.exe to something else and run it from another folder.
Mitigation:
Enable rules based on below mentioned 2 queries to detect the attack effectively.
[Sysmon_1, 4688, EDR) –
a) process_name == sc.exe and command_line contains “create”
b) original_file_name=”sc.exe” and [process name!=”sc.exe” or process_path!=”c:\windows\ system32\sc.exe or c:\windows\syswow64\sc.exe”]
6-Temp Service:
Mitigation:
- Hunt for the below mentioned two occurrences with the sysmon Event ID 13 along with the service type parameter 0x00000003 & 0x00000004.
- 0x00000004 : SERVICE_DISABLED – A service that cannot be started. Attempts to start the service result in the error code ERROR_SERVICE_DISABLED.
- 0x00000003 : SERVICE_DEMAND_START – A service started by the service control manager when a process calls the “StartService” function.
2 occurrences of Sysmon-EventId=13 and TargetObject like “HKLM\System\CurrentControlSet\services\*\start” and 1st occurrence with “Details” like (0x00000003) [On demand start] followed by 2nd occurrence with “Details like (0x00000004) [Service Disabled] within 1min with same TargetObject (Key Path)
Also Read: Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
6-Modifying Existing Service:
Mitigation:
Hunt for the below-mentioned target object i.e “servicedll” where the process is not of ”services.exe”.
Sysmon 13 or EDR –
TargetObject is like “HKLM\System\CurrentControlSet\Services\*\parameters\Services\*\parameters\servicedll” and process_name!=”services.exe”
Conclusion:
Most of the security analysts will conclude the alert as False Positive if they are seeing the parent process as windows services. We need to make sure that the executed command line is a valid process and whether it can be executed from the parent process. The detection rules listed above will be effective for the blue team.