Overview
APT-Hunter is the threat hunting tool for windows event logs which will detect APT movements and uncover suspicious activities. It was written by ahmedkhlief. Also, Ahmed would like to thank Joe Maccry for his amazing contribution to Sysmon use cases ( more than 100 use cases added by Joe ), This tool will be useful for Threat Hunter, Incident Responder, or forensic investigators. A list of default rules within this tool will detect the indicator of attack which includes the apt techniques and map the tactics and techniques of the Mitre ATT&CK framework to Windows event log event IDs.
APT-Hunter New Features
- Apt-Hunter now support more than 200 use cases.
- Introducing Log hunting feature which can take string or regex and search all the logs and provide you a parsed report for all findings.
- New Process Execution frequency analysis : this will help you identify suspicious and rare processes run in the environment .
- New Login Events report : the new CSV Login events report include parsed (Date, User , Source IP , Logon Process , Workstation Name , Logon Type , Device Name , Original Log ) column fields so you can easily filter , investigate suspicious logins and if you analyze multiple machines you can have time line analysis for the logins .
- Specify the timezone you want : before APT-Hunter was using UTC timezone for all reports but now you can specify the timezone or use ( local ) to auto detect your timezone.
- No need to specify the type of logs : APT-Hunter will analyze folders for logs and detect the type of logs then analyze it .
- Analyze Multiple devices logs and get unified timeline : You can provide a directory with all machine logs you want to analyze and APT-Hunter will provide a single report for all machines which will easy the timeline analysis .
- Terminal Service Events now include columns for ( user , source IP ) to make it easier to filter and check for suspicious activity .
- Many bug fixes since last release.
Also Read: APT-Hunter – Threat Hunting Tool For Windows Event Logs
APT-Hunter new use cases
- Suspicious Command or process found in the log
- User Added using Net Command
- Process running in suspicious location
- Process running in Unusual location
- Suspicious Process Found
- Suspicious Powershell commands Process Found
- Suspected privielge Escalation attempt using NAMED PIPE
- non-interactive powershell being executed by another application in the background
- User Created through management interface
- User Created through management interface
- Dcsync Attack detected
- dcshadow Attack detected
- network share object was added
- network share object was added
- Windows is shutting down
- User added to local group
- User added to local group
- User added to global group
- User added to global group
- User added to Universal group
- User added to Universal group
- User Removed from Global Group
- User Removed from Global Group
- User Removed from Universal Group
- User Removed from Universal Group
- User Removed from Local Group
- User Removed from Local Group
- User Removed Group
- User Removed Group
- User Account Removed
- User Account Removed
- High number of Pass the hash attempt Detected . detection will be paused for this user to not flood the detection list
- Pass the hash attempt Detected
- Pass the hash attempt Detected
- Audit log cleared
- Suspicious Attempt to enumerate groups
- Suspicious Attempt to enumerate groups
- System audit policy was changed
- schedule task created
- schedule task deleted
- schedule task updated
- schedule task enabled
- schedule task disabled
- System Logs Cleared
- Service Installed with executable in TEMP Folder
- Service installed in the system
- psexec service detected installed in the system
- Service start type changed
- Service State Changed
- Zerologon Exploitation Using Well-known Tools
- non-system accounts getting a handle to and accessing lsass
- non-system accounts getting a handle to and accessing lsass
- Password Spray Detected
- Suspicious Command or process found in the log
- Windows Defender took action against Malware
- Windows Defender failed to take action against Malware
- Windows Defender Found Malware
- Windows Defender deleted history of malwares
- Windows Defender detected suspicious behavior Malware
- Windows Defender real-time protection disabled
- Windows Defender real-time protection configuration changed
- Windows Defender antimalware platform configuration changed
- Windows Defender scanning for malware is disabled
- Windows Defender scanning for viruses is disabled
- Suspicious Command or process found in the log
- schedule task registered
- schedule task updated
- schedule task deleted
- Service installed in the system
- psexec service detected installed in the system
- Service start type changed
- Service State Changed
- Zerologon Exploitation Using Well-known Tools
- Suspicious Command or process found in the log
- Powershell Module logging – Malicious Commands Detected
- powershell script block – Found Suspicious PowerShell commands
- PowerShell ISE Operation – Found Suspicious PowerShell commands
- Powershell Executing Pipeline – Suspicious Powershell Commands detected
- Powershell Executing Pipeline – User Powershell Commands
- Suspicious Command or process found in the log
- Powershell Executing Pipeline – Suspicious Powershell Commands detected
- Suspicious PowerShell commands Detected
- Suspicious PowerShell commands Detected
- User connected RDP from Local host – Possible Socks Proxy being used
- User Connecting RDP from Public IP
- User Loggedon to machine
- connection is initiated using WinRM from this machine – Powershell remoting
- connection is initiated using WinRM to this machine – Powershell remoting
- [ T1086 ] Powershell with Suspicious Argument
- [ T1543 ] Sc.exe manipulating windows services
- [ T1059 ] wscript or cscript runing script
- [ T1218.005 ] Mshta found running in the system
- Psexec Detected in the system
- [T1053] Scheduled Task manipulation
- Prohibited Process connecting to internet
- Command run remotely Using WMI
- Detect IIS/Exchange Exploitation
- [T1082] System Information Discovery
- [T1117] Bypassing Application Whitelisting with Regsvr32
- [T1055] Process Injection
- [T0000] Console History
- [ T0000 ] Remotely Query Login Sessions – Network
- [ T0000 ] Remotely Query Login Sessions – Process
- T0000 Suspicious process name detected
- T1002 Data Compressed
- T1003 Credential Dumping ImageLoad
- [T1003] Credential Dumping – Process
- [T1003] Credential Dumping – Process Access
- [T1003] Credential Dumping – Registry
- [T1003] Credential Dumping – Registry Save
- [T1004] Winlogon Helper DLL
- [T1004] Winlogon Helper DLL
- [ T1007 ] System Service Discovery
- [T1223] Compiled HTML File
- [T1218] Signed Binary Proxy Execution – Process
- [T1218] Signed Binary Proxy Execution – Process
- [T1218] Signed Binary Proxy Execution – Network
- [T1216] Signed Script Proxy Execution
- [T1214] Credentials in Registry
- [T1209] Boot or Logon Autostart Execution: Time Providers
- [T1202] Indirect Command Execution
- [T1201] Password Policy Discovery
- [T1197] BITS Jobs – Process
- [T1197] BITS Jobs – Network
- [T1196] Control Panel Items – Registry
- [T1196] Control Panel Items – Process
- [T1191] Signed Binary Proxy Execution: CMSTP
- [T1183] Image File Execution Options Injection
- [T1182] AppCert DLLs Registry Modification
- [T1180] Screensaver Hijack
- [T1179] Hooking detected
- [T1170] Detecting Mshta
- [T1170] Detecting Mshta
- [T1158] Hidden Files and Directories – VSS
- [T1158] Hidden Files and Directories
- [T1146] Clear Command History
- [T1140] Deobfuscate/Decode Files or Information
- [T1138] Application Shimming – Registry
- [T1138] Application Shimming – process
- [T1136] Create Account
- [T1135] Network Share Discovery – Process
- [T1131] Authentication Package
- [T1130] Install Root Certificate
- [T1128] Netsh Helper DLL – Process
- [T1128] Netsh Helper DLL – Registry
- [T1127] Trusted Developer Utilities
- [T1126] Network Share Connection Removal
- [T1124] System Time Discovery
- [T1115] Audio Capture
- [T1122] Component Object Model Hijacking
- [T1121] Regsvcs/Regasm
- [T1118] InstallUtil
- [T1117] Regsvr32
- [T1117] Bypassing Application Whitelisting with Regsvr32,rundll32,certutil or scrobj
- [T1115] Clipboard Data Collection
- [T1107] Indicator Removal on Host
- [T1103] AppInit DLLs Usage
- [T1096] Hide Artifacts: NTFS File Attributes
- [T1088] Bypass User Account Control – Registry
- [T1088] Bypass User Account Control – Process
- [T1087] Account Discovery
- [T1086] PowerShell Downloads – Process
- [T1086] PowerShell Process found
- [T1085] Rundll32 Execution detected
- [T1082] System Information Discovery
- [T1081] Credentials in Files
- [T1077] Windows Admin Shares – Process – Created
- [T1077] Windows Admin Shares – Process
- [T1077] Windows Admin Shares – Network
- [T1076] Remote Desktop Protocol – Process
- [T1076] Remote Desktop Protocol – Registry
- [T1074] Data Staged – Process
- [T1070] Indicator removal on host
- [T1069] Permission Groups Discovery – Process
- [T1063] Security Software Discovery
- [T1060] Registry Run Keys or Start Folder
- [T1059] Command-Line Interface
- [1057] Running Process Discovery
- [T1054] Indicator Blocking – Sysmon registry edited from other source
- [T1054] Indicator Blocking – Driver unloaded
- [T1053] Scheduled Task – Process
- [T1050] New Service – Process
- [T1049] System Network Connections Discovery
- [T1047] Windows Management Instrumentation – Process
- [T1047] Windows Management Instrumentation – Network
- [T1047] Windows Management Instrumentation – Instances of an Active Script Event Consumer – Process
- [T1047] Windows Management Instrumentation – Instances of an Active Script Event Consumer – FileAccess
- [T1040] Network Sniffing Detected
- [T1037] Boot or Logon Initialization Scripts
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
- [T1036] Masquerading – Extension
- [T1031] Modify Existing Service
- [T1028] Windows Remote Management
- [T1027] Obfuscated Files or Information
- [T1018] Remote System Discovery – Process
- [T1018] Remote System Discovery – Network
- [T1015] Accessibility Features – Registry
- [T1015] Accessibility features
- [T1013] Local Port Monitor
- [T1012] Query Registry – Process
- [T1012] Query Registry – Network
- [T1012] Processes opening handles and accessing Lsass with potential dlls in memory
- [T1003] Processes opening handles and accessing Lsass with potential dlls in memory
- [T1112] process updating fDenyTSConnections or UserAuthentication registry key values
- [T1059] processes loading PowerShell DLL system.management.automation
- [T1059] PSHost* pipes found in PowerShell execution
- [T1112] process updating UseLogonCredential registry key value
- [T1055] Process Injection – Process
Also Read: Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
Working with APT-Hunter
- Download the tool here
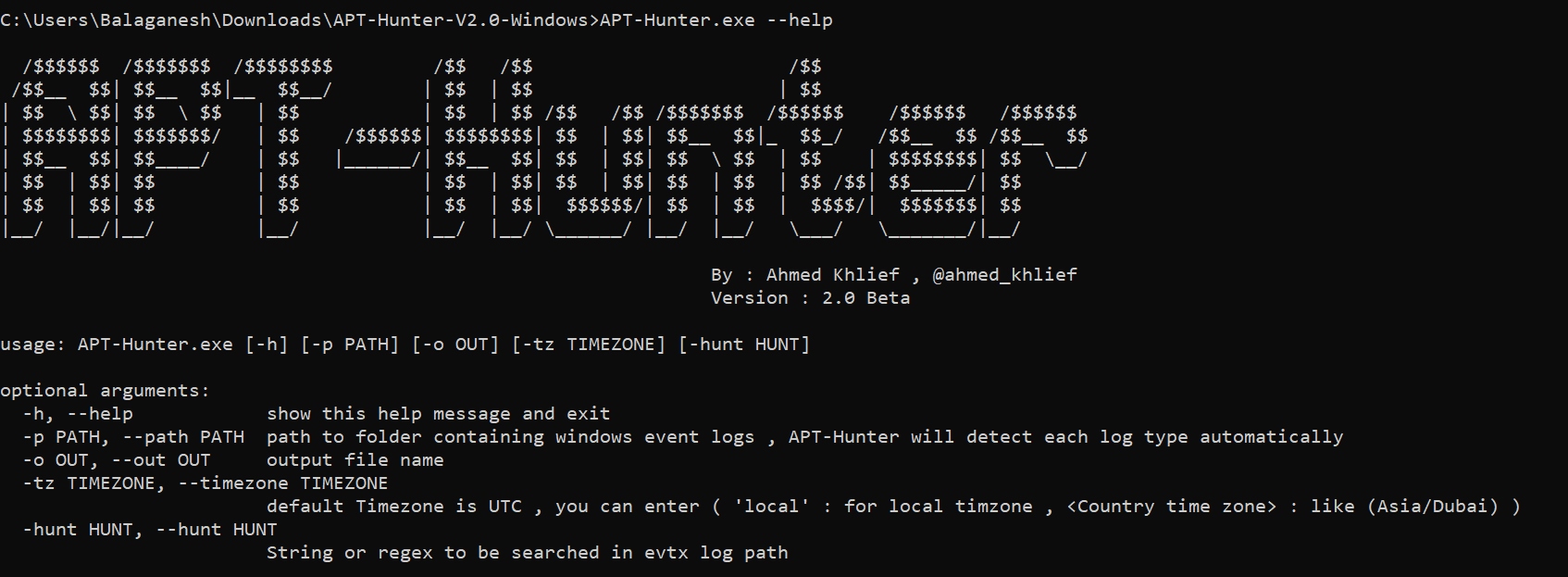
- Run the APT-Hunter tool with the collected log files directory and wait for some seconds.
-t = FileFormat ( We have collected logs in csv format )
-P = Log File Path ( Mapping the log file location )
- Tool with run and check the default rules and results will be populated on this console
- Results are Exported in the APT-Hunter Folder under the file name _Report.xlsx and _TimeSketch.xlsx , Analyst can use this file to quickly check the security risk level.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Report.xlsx : This excel sheet will have details of the events detected from every windows log provided to APT-Hunter.
- TimeSketch.csv : This excel sheet will have details of the time sketch in order to have timeline analysis that will help you see the full picture of the attack.
Happy Hunting!



































