FireEye’s launched an open-source tool ( CAPA ) for malware analysis for potentially PE files or shellcode. CAPA detects capabilities in executable files. You run it against a PE file or shellcode and it tells you what it thinks the program can do. For example, it might suggest that the file is a backdoor, is capable of installing services, or relies on HTTP to communicate.
Installation steps:
Features of CAPA:
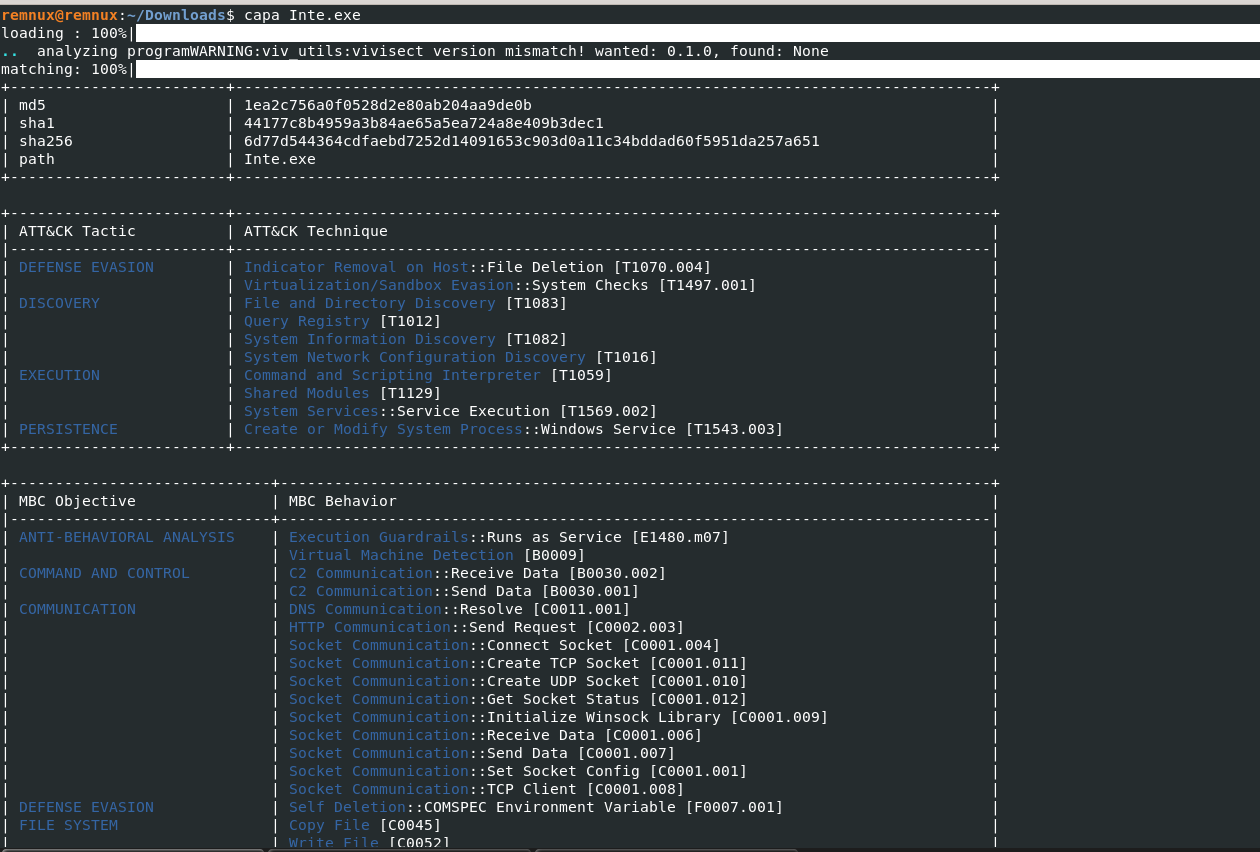
- Detecting with inbuild rules describing additional malware capabilities and mapping it with ATT&CK techniques.
- Static malware analysis with clear picture of malware instruction and execuction flow.
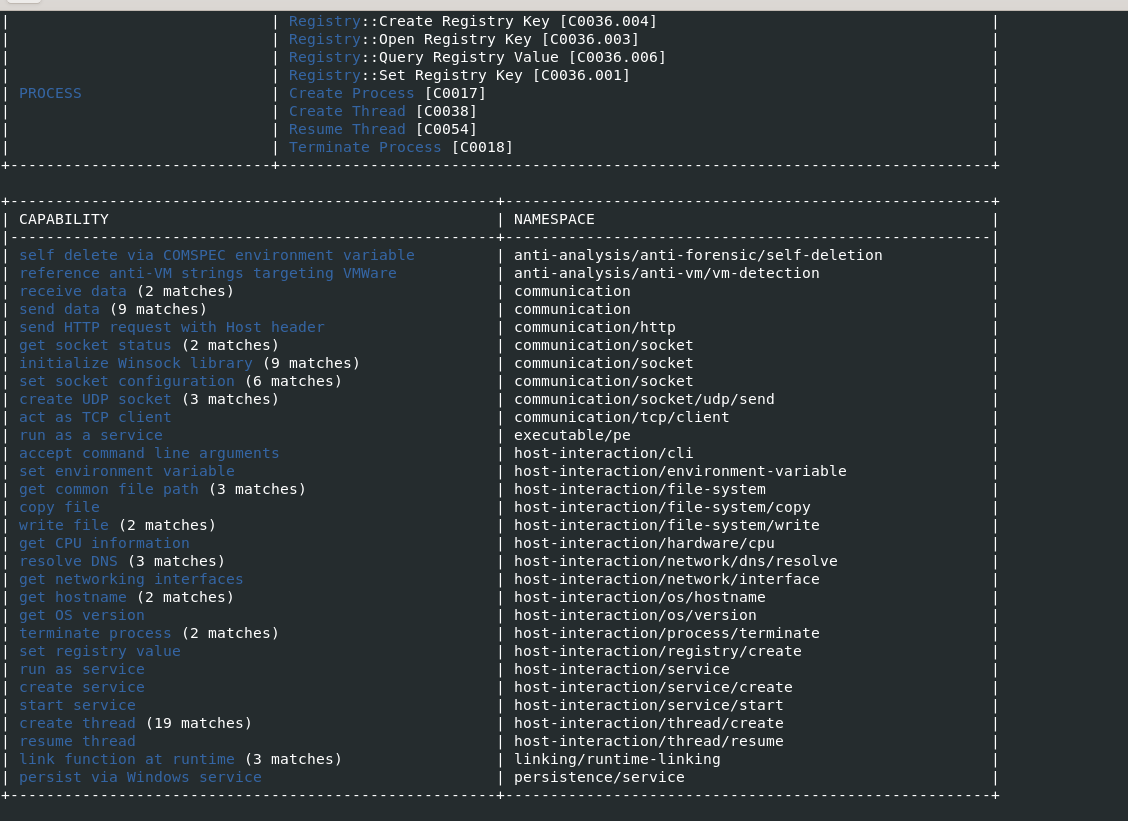
- Host Interactiondescribes program functionality to interact with the file system, processes, and the registry.
- Anti-Analysis describes packers, Anti-VM, Anti-Debugging, and other related techniques
- Collection describes functionality used to steal data such as credentials or credit card information
- Data Manipulation describes capabilities to encrypt, decrypt, and hash data
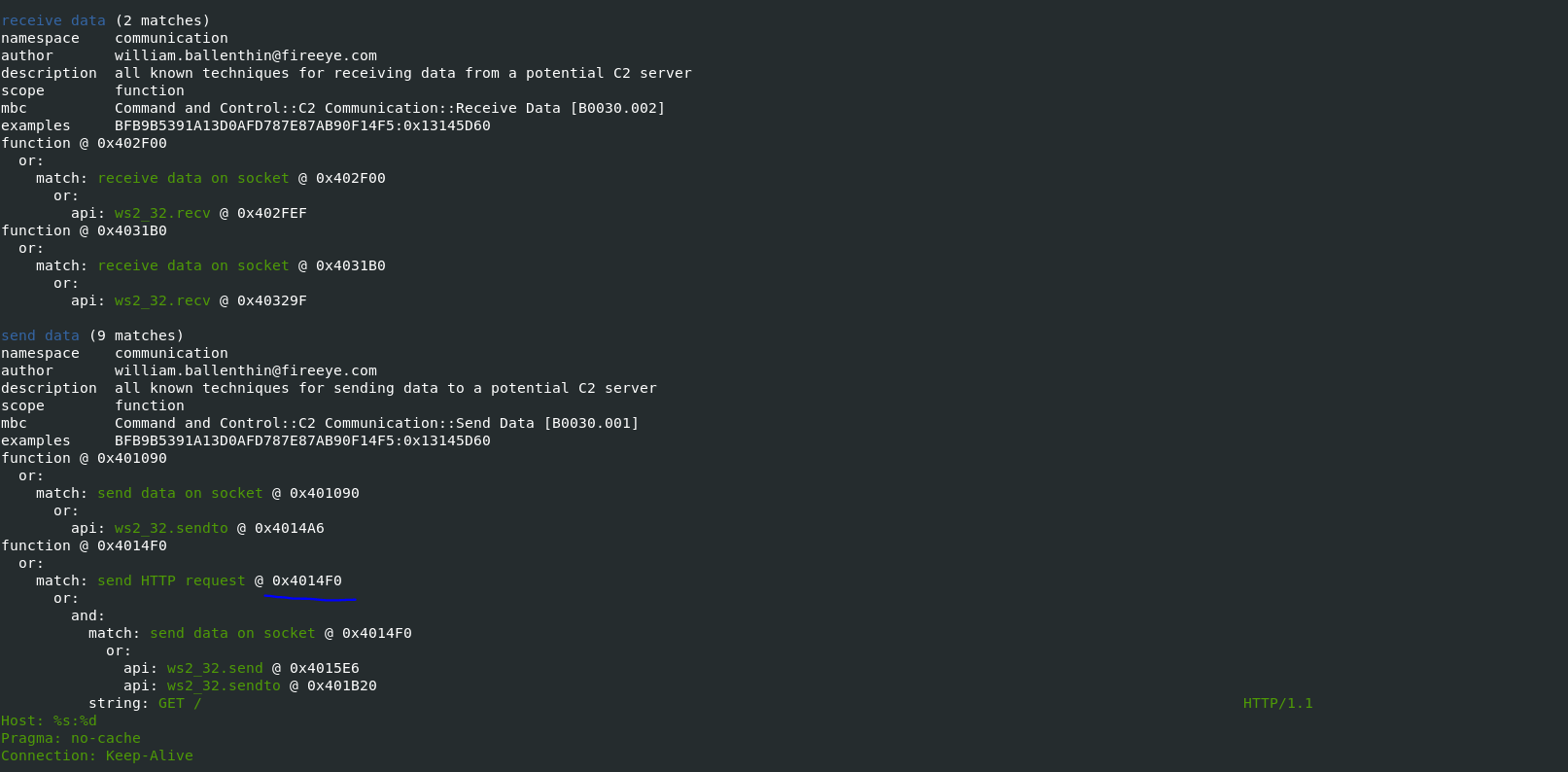
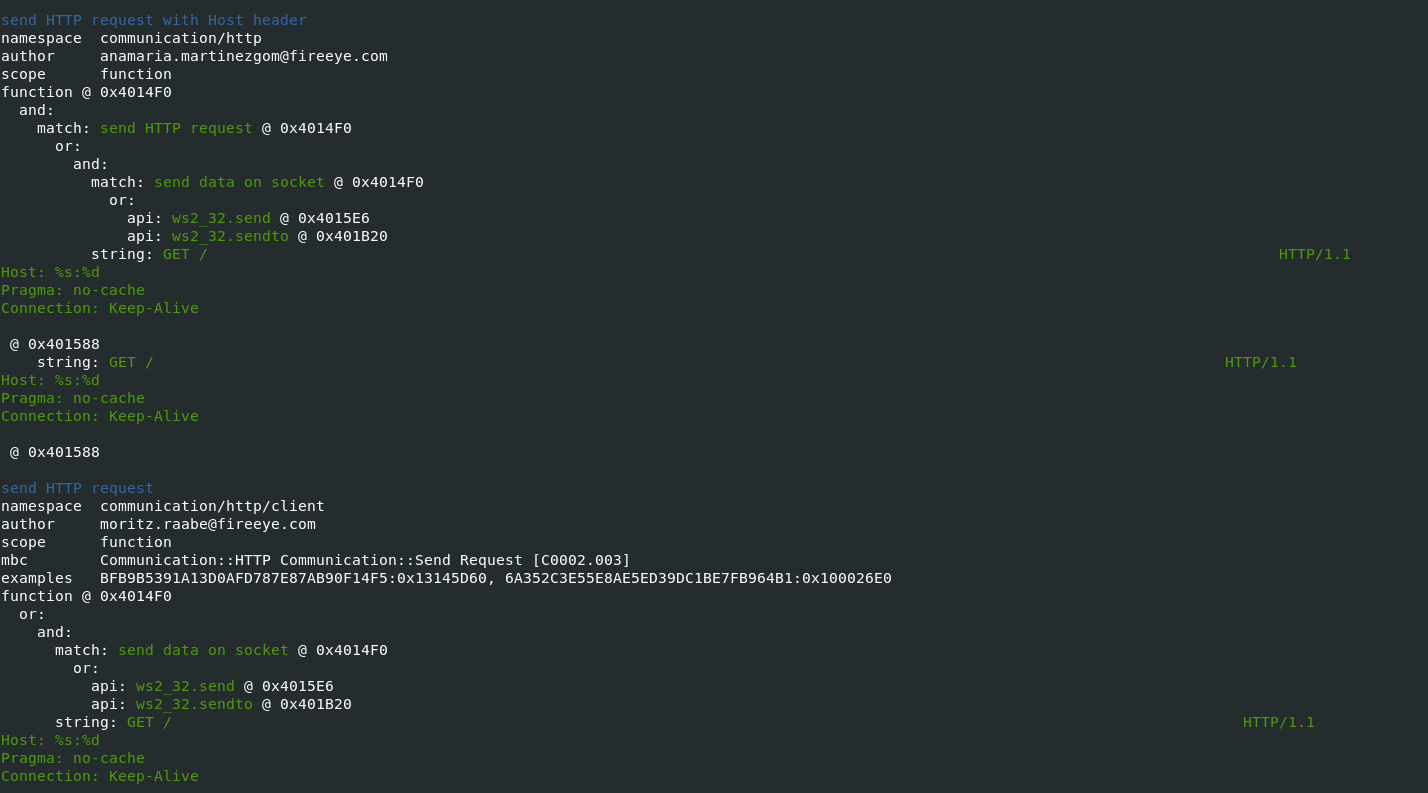
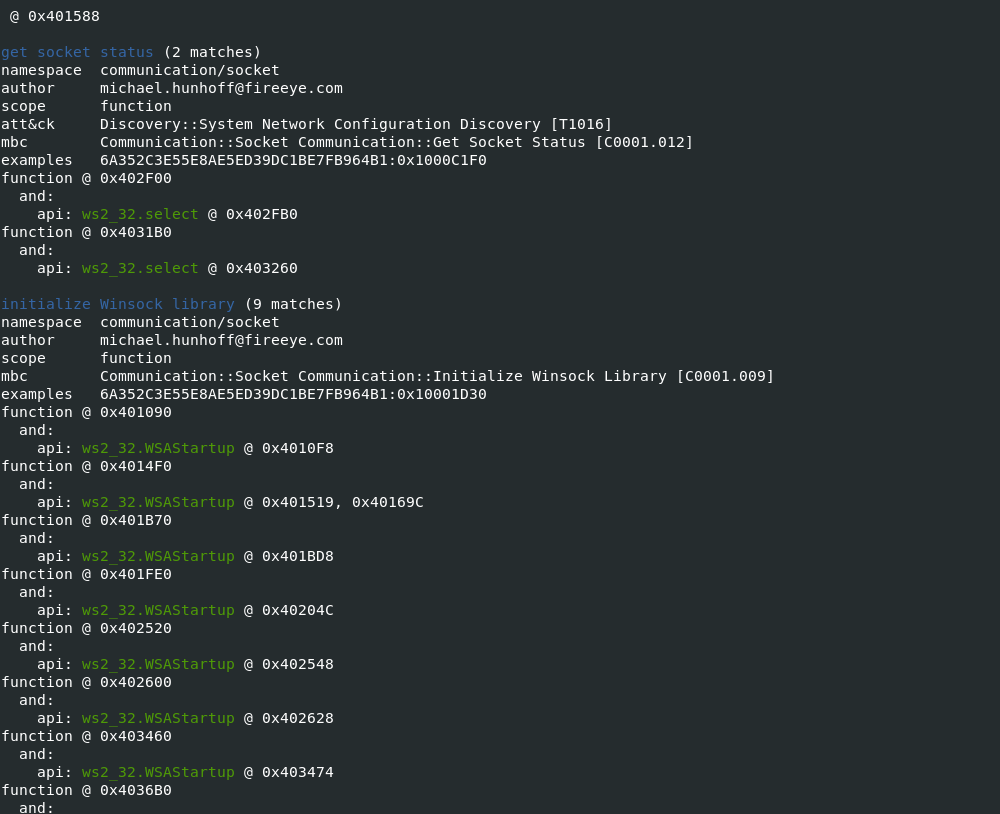
- Communication describes data transfer techniques such as HTTP, DNS, and TCP
Working with CAPA:
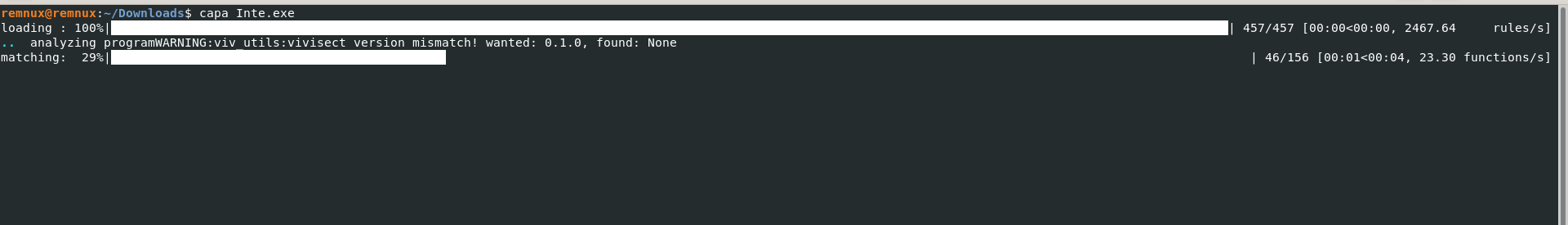
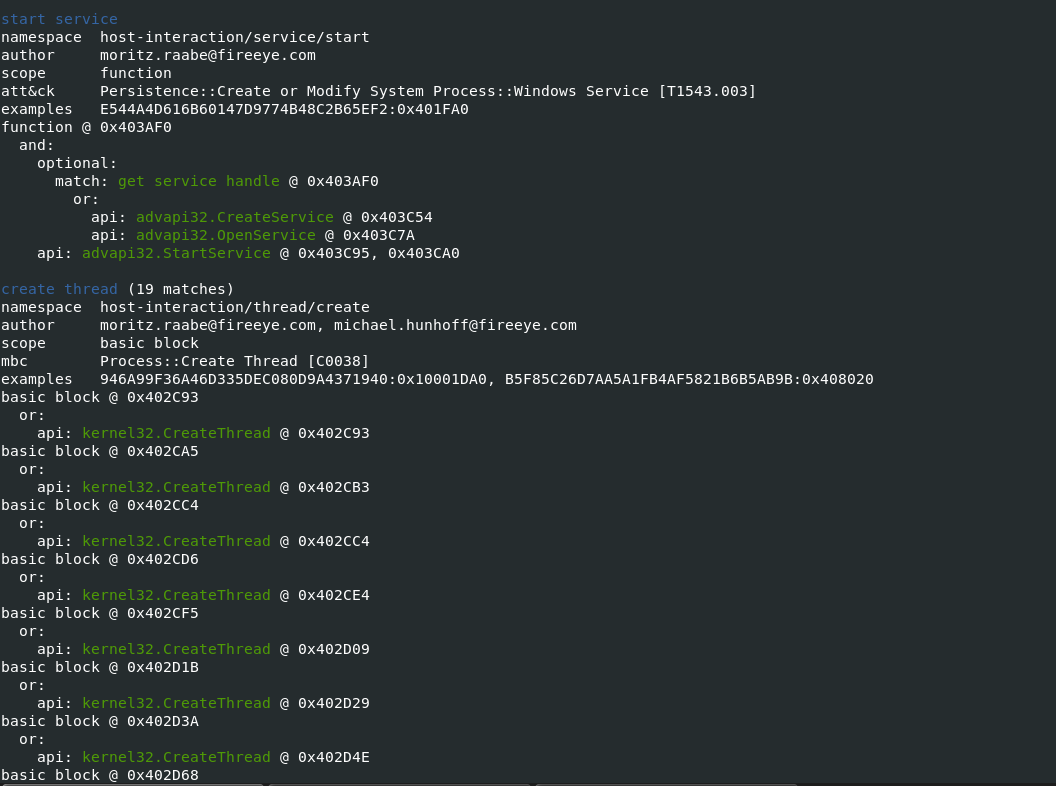
- Starting the tool to analyze malicious windows executable & check the malware Capabilities and its ATT&CK techniques.

Also Read : APT-Hunter – Threat Hunting Tool For Windows Event Logs
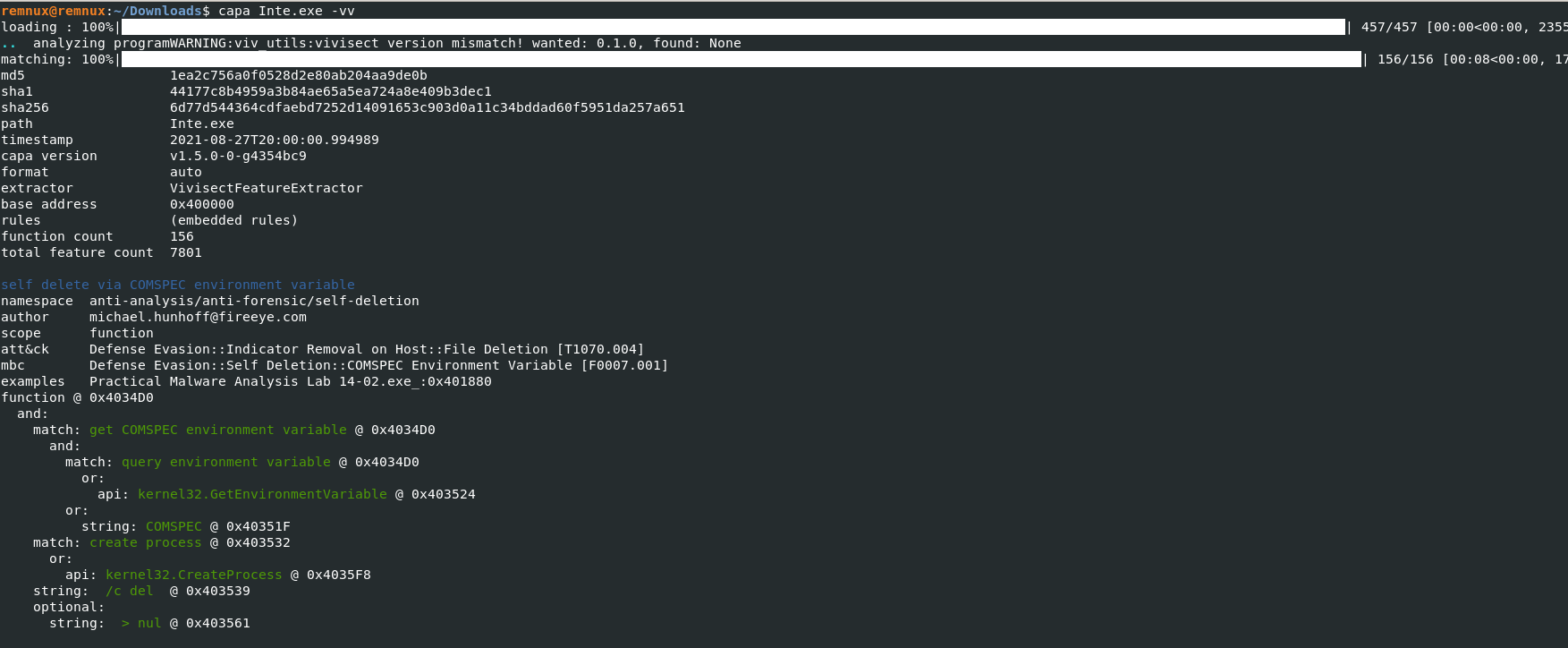
Passing the -vv flag
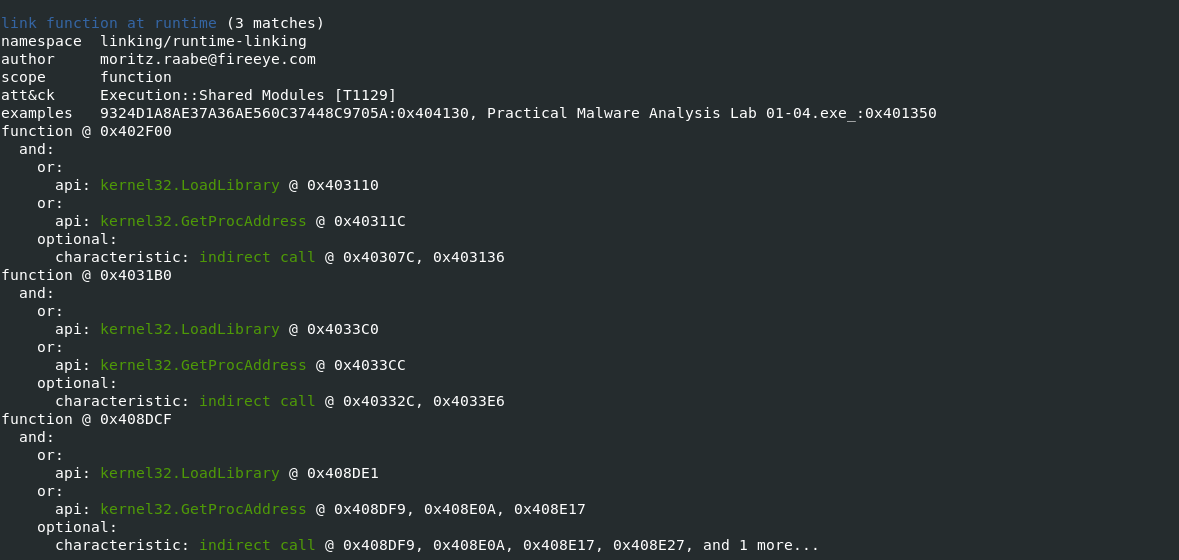
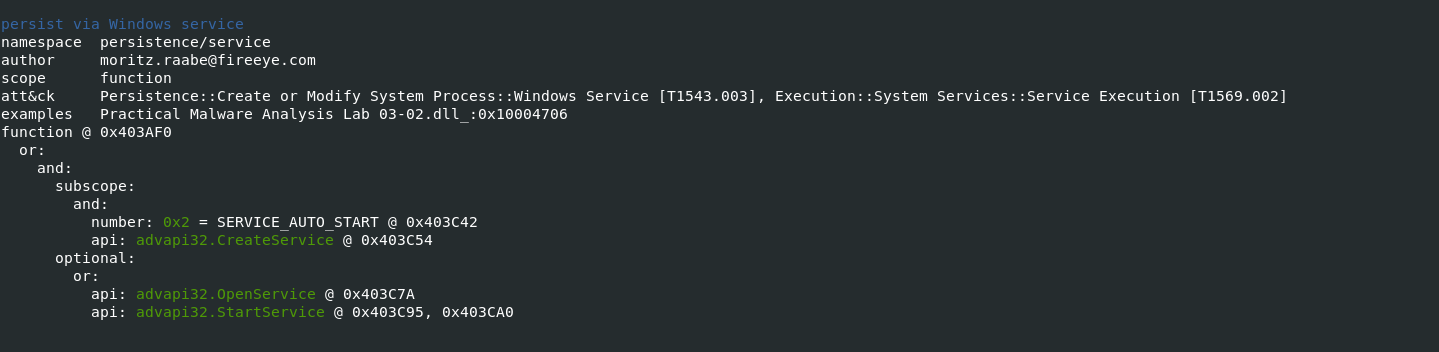
-vvflag (for very verbose), capa reports exactly where it found evidence of these capabilities.- it shows where within the binary an experienced analyst might study with IDA Pro or other malware disassembler tools.
- It provides the Instruction information and malware entry addresess which can be later verifed in disassembler tools to retrive indicators of Comproimise.
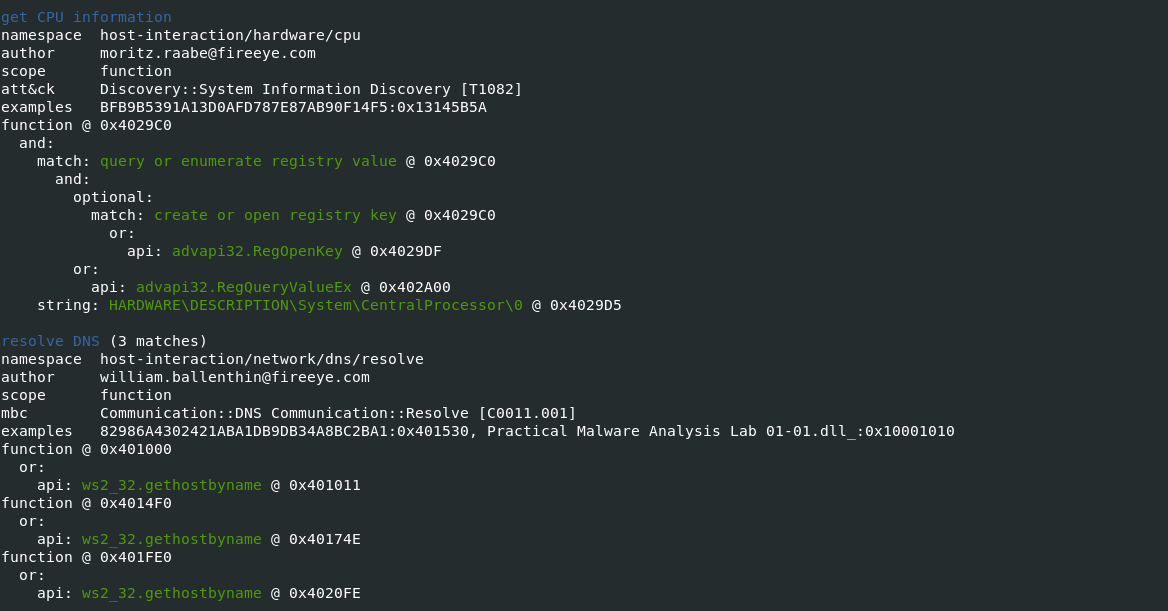
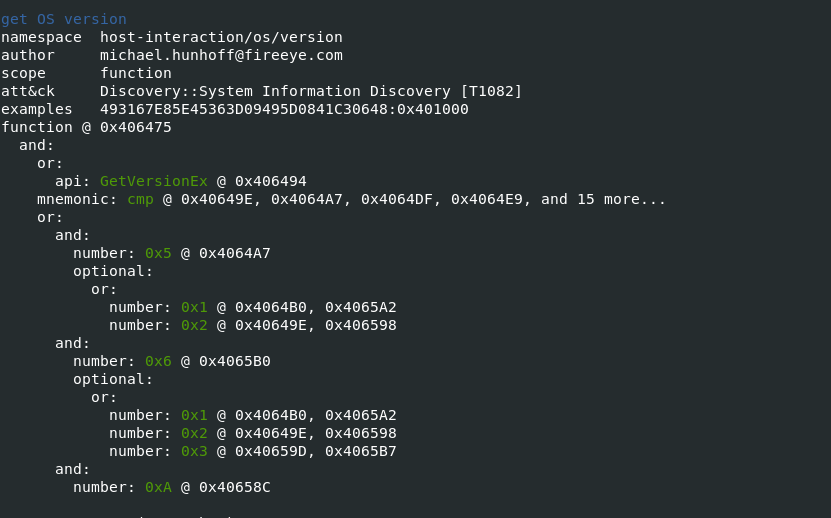
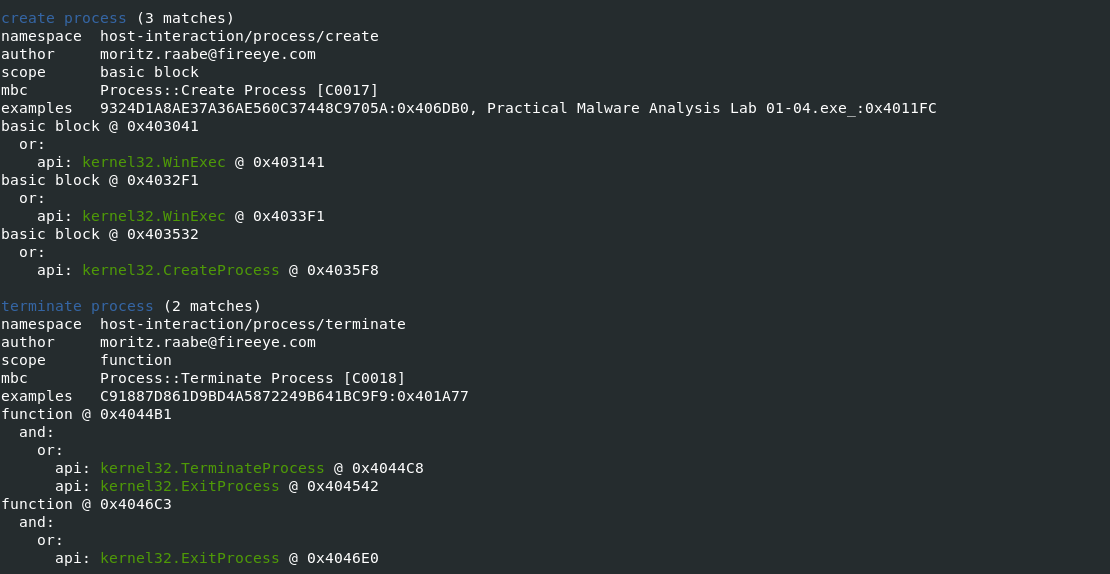
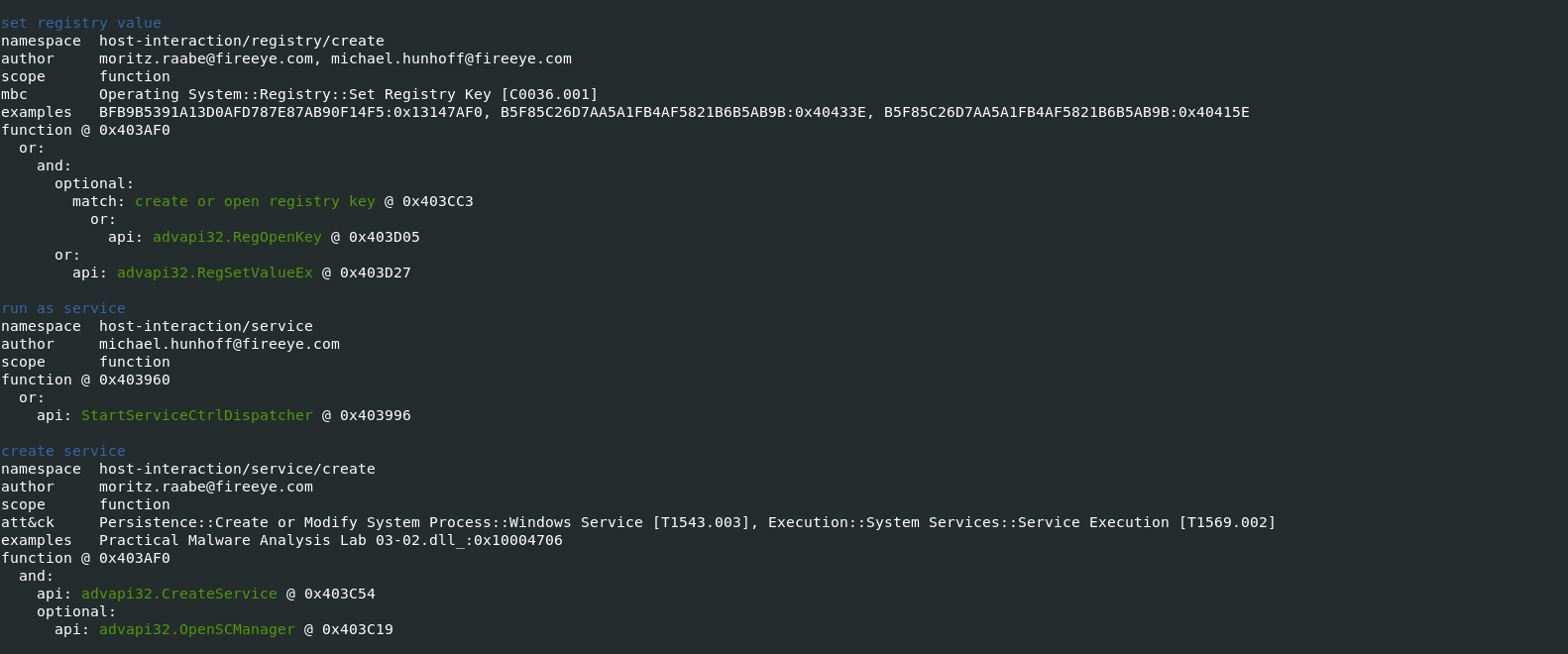
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Disassembler to Extract Indictors of Compromise
- Let us verify some of above malware actions with Disassembler to retrive suspicious files downloaded & malware domain.
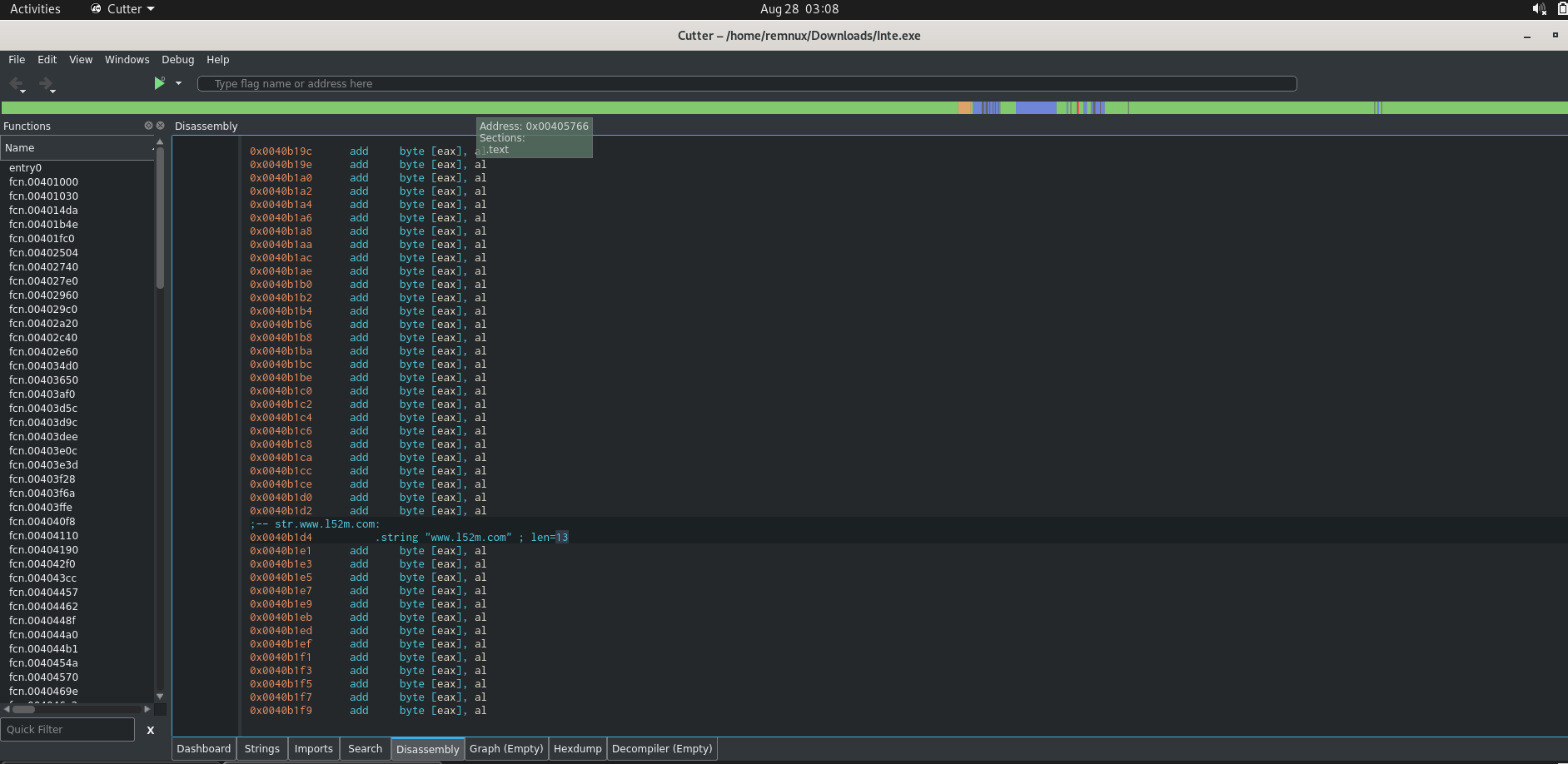
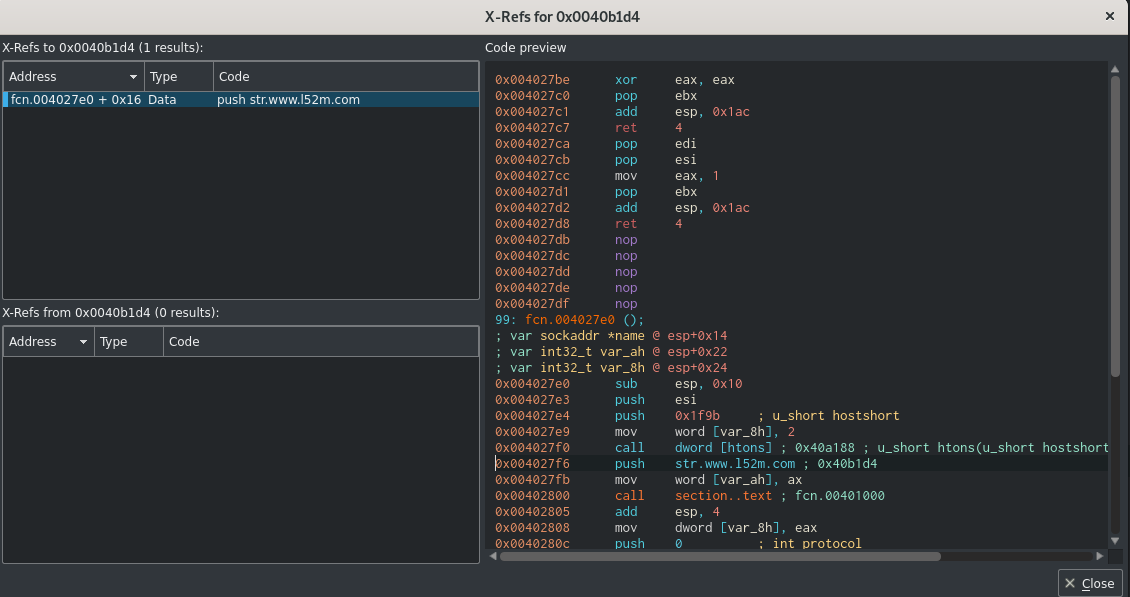
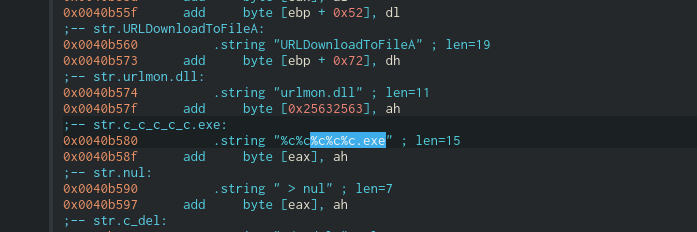
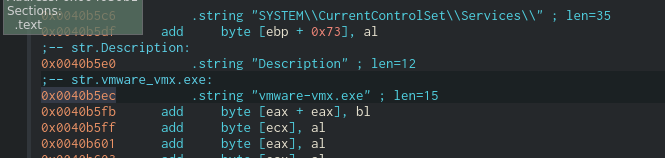
- Similar way we can reverse and extract other information such as ( Process name , Registry entry values ,etc ) as part of static analsysis.
- CAPA provides users with a unique tool to quickly analyse an executable sample , CAPA tool will recognize some features and patterns of malware that would help malware analysts for further investigations.
Happy Hunting !!!



































