Silver Ticket is similar to Golden Ticket, wherein the golden ticket attack, attackers have full control to Domain itself. But Silver Ticket provides access only to the specific service account (e.g SharePoint, MSSQL), Adversaries who have the password hashes for any of the service accounts may forge Kerberos ticket-granting service (TGS) tickets, which is known as silver tickets. TGS Tickets will be created without communicating with the domain ( Key Distribution Center ) which is likely to be forged one and the level of detection will be time taking process.
Detecting Silver Ticket Attacks
- Hunt for the event id 4769 which has a new username in the domain.
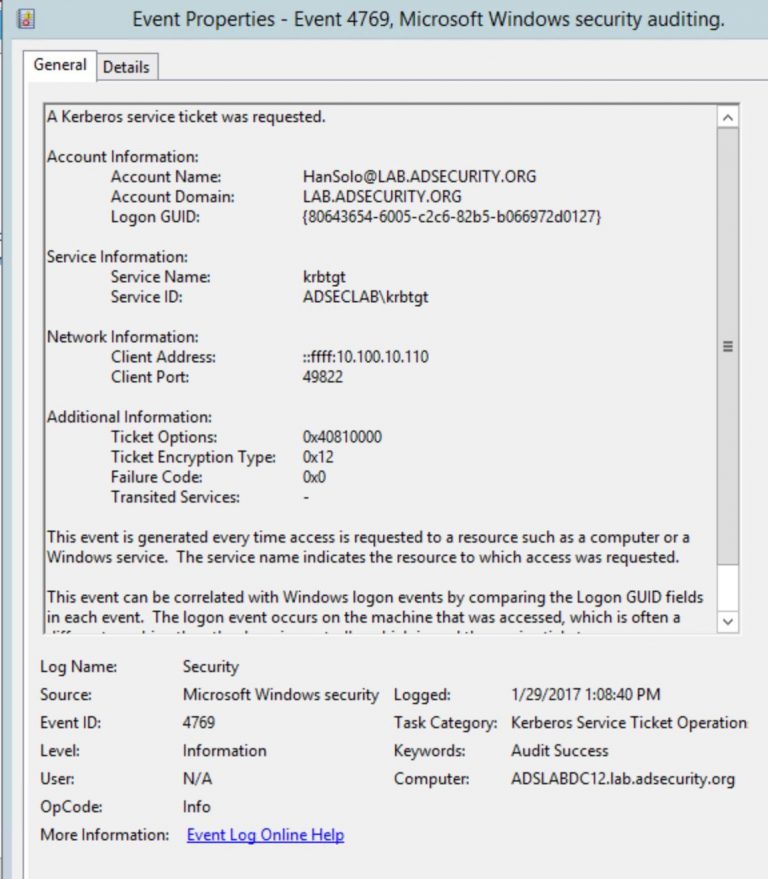
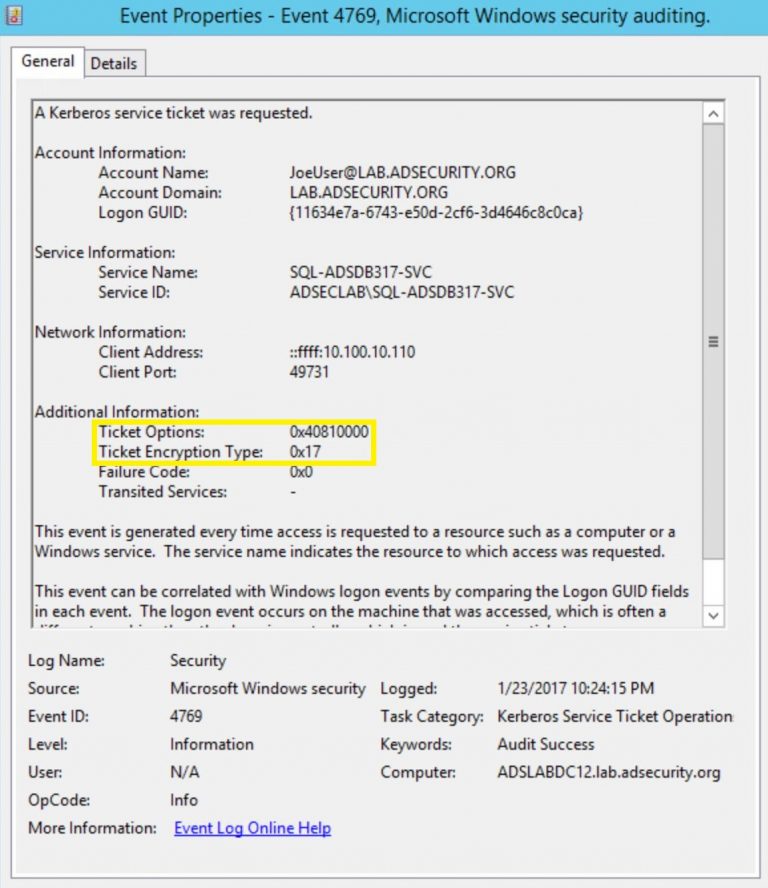
- Check for the suspicious service ticket requests with Kerberos RC4 encrypted and the ticket encryption type is 0x17.
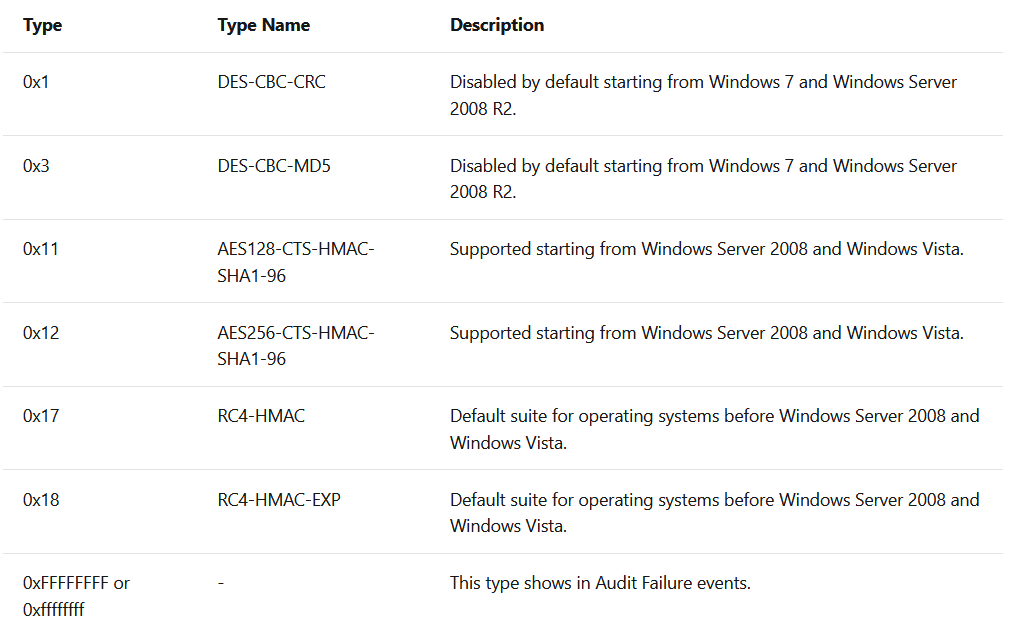
- Most of the Kerberos requests will be AES encrypted. If any Kerberos RC4 ticket request should be suspicious.
- Write a correlation rule to match ( RC4 encryption + Event ID 4769 + New User Names In domains + Login Frequency ) , Gather such attributes information to detect anomalous activity.
- In addition, Hunt for the malformed or blank fields in Windows logon/logoff events such as (Event ID 4624, 4634, 4672)
- Monitor for unexpected processes interacting with lsass.exe. Common credential dumpers such as Mimikatz access the LSA Subsystem Service (LSASS) process by opening the process, locating the LSA secrets key, and decrypting the sections in memory where credential details, including Kerberos tickets, are stored.
Also Read: DnsTwist Tool – Proactive Approach for Handling Phishing Cases
Preventive Measures
- Educate users about password reuse and phishing attacks.
- Manage a least-privilege model to restrict user and domain administrator access.
- Implement Kerberos with Privilege Attribute Certificate (PAC) and requiring the TGS to be signed by the KDC using the krbtgt encryption key.
- Offline cracking of credentials is a key component of Silver Ticket attacks, make sure that local user, administrator, and service accounts use strong, unique passwords.
- Implement tools to validate every ticket presented by a Kerberos principal (i.e. service client) has been issued by a legitimate key distribution center. This requires collecting and validating all Kerberos authentication messages for each SPN ( Service Principal Name ) being protected.
- Enable AES Kerberos encryption (or another stronger encryption algorithm), rather than RC4, where possible.



































