Scheduled Tasks are also a great weapon for attackers to employ because they are available on all Windows operating systems and are simple to use and most users are unaware that they exist. Even people who are knowledgeable may have difficulty determining which tasks are legitimate aspects of the operating system or apps they have installed and which of those are malicious. A number of threat groups are presently employing Scheduled Tasks to gain persistence. They could also be used to check for new content for a trojan or dropper on a regular basis via command and control channels.
To help automate recurring tasks, Windows include a mechanism of scheduling the launch of programs or scripts based on specific time intervals. If configured incorrectly, this can become a flaw, allowing attackers to escalate privileges to root.
This post will go over the most common strategies for defending the exploitation using scheduled activities.
Event IDs covering scheduled tasks:
- Event ID 4698 – A scheduled task was created: This event generates every time a new scheduled task is created.
- Event ID 4699 – A scheduled task was deleted: This event generates every time a scheduled task was deleted.
- Event ID 4700 – A scheduled task was enabled: This event generates every time a scheduled task is enabled.
- Event ID 4701 – A scheduled task was disabled: This event generates every time a scheduled task is disabled.
- Event ID 4702 – A scheduled task was updated: This event generates every time scheduled task was updated/changed.
- Event ID 4688 – A new process has been created: This event generates every time a new process starts.
- Event ID 5145 – A network share object was checked to see whether client can be granted desired access: This event generates every time network share object (file or folder) was accessed.
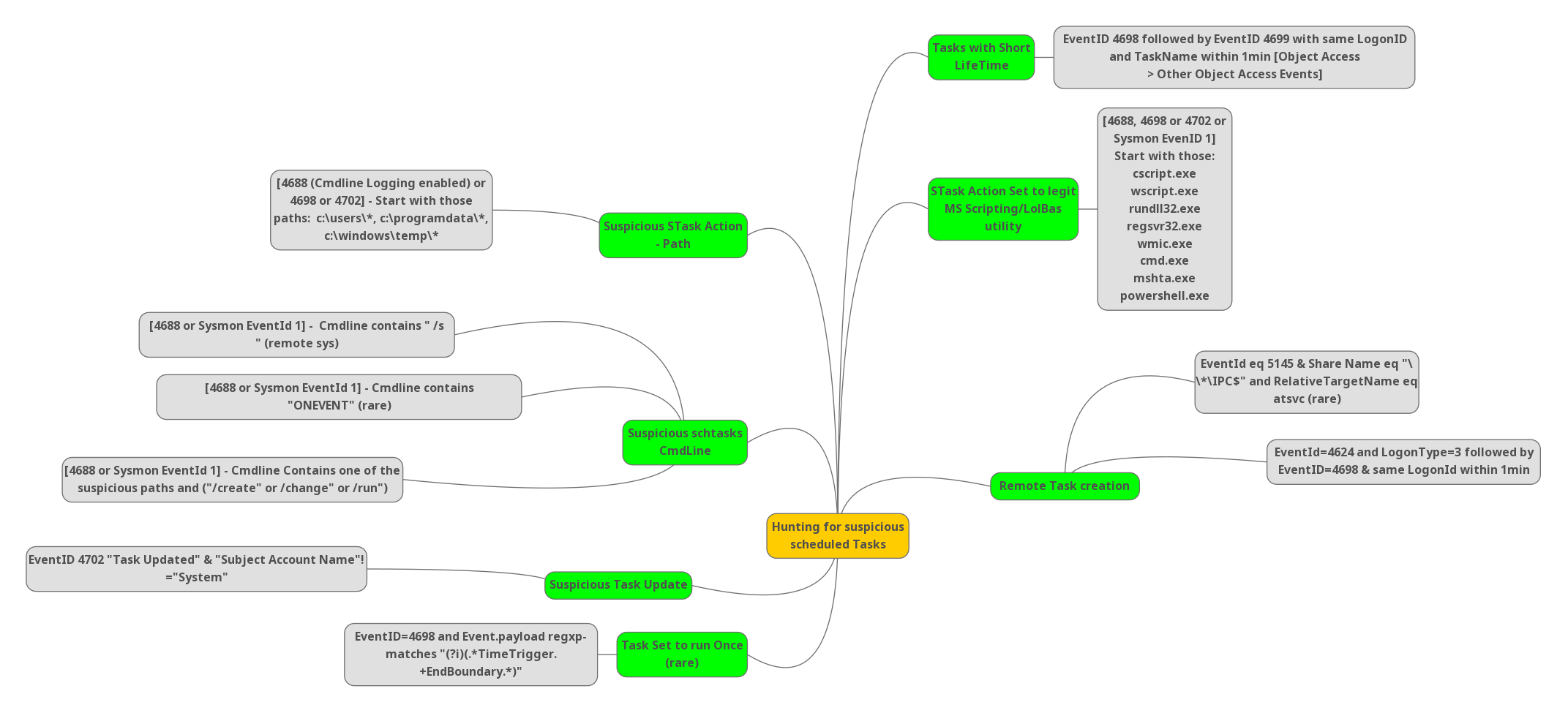
Hunting for suspicious scheduled task:
The task with Short Life Time:
Audit Object Access Events allows you to monitor operations with scheduled tasks. Hunt for Event ID 4698 followed by EventID 4699 with the same LogonID and TaskName within 1 minute.
STask action set to legit MS Scripting/LoLBas utility:
Create a rule with EventID 4688, 4698 or 4702 or Sysmon EventID 1, where the execution of the script is initiated by script.exe, wscript.exe, rundll32.exe, wmic.exe, cmd.exe, mshta.exe & powershell.exe. Hunt with this rule to stop unwanted entries of adversaries.
Also Read: Topmost Signs of Compromise Detected with Windows operating System
Remote task creation:
- Hunt for EventID = 5145 & Share Name = “\\*\IPC$” and RelativeTargetName = atsvc (alerts very rare event)
- Hunt for EventID = 4624 and LogonType=3 follwed by EventID=4698 & same LogonId within 1 minute.
Task Set to run Once (rare event):
Hunt for EventID = 4698 and Event.payload regular expression matches “(?i)(.*TimeTrigger.+EndBoundary.*)”
Suspicious Task Update:
Hunt for EventID 4702 “Task Updated” & “Subject Account Name”!=”System”.
Also Read : Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Suspicious schtasks cmdline:
- Hunt for the EventID 4688 or Sysmon EventID = 1 where the Cmdline contains one of the suspicious paths : “/create” or “/change” or “/run”.
- Hunt for the EventID 4688 or Sysmon EventID = 1 where the Cmdline contains “ONEVENT”. We usually don’t get any logs for it. It’s a very rare alert.
- Hunt for the EventID 4688 or Sysmon EventID = 1 where the Cmdline contains “/s”. This will work for remote system.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Suspicious STask Action = Path:
Hunt for the EventID 4688 (cmdline logging enabled) or 4698 or 4702 where the current path/directory i.e starting with the paths: “c:\users\*”, “c:\programdata\*” and “c:\windows\temp\*”.
Attackers mostly will exploit using two ways:
- Weak File Permissions used for the script being run by the scheduled tasks
- Creating or modifying scheduled tasks (only works in older versions of Windows)
Conclusion:
For persistence, adversaries may use task scheduling to execute scripts at system startups or on a regular basis. Scheduled tasks should be configured properly, particularly when executed as root, as they could compromise the entire system. This has been using as an exploitation vector for a long time, as there has always been a demand for automation, and today more than ever, there is a need for automation.



































