SystemBC is a proxy malware that has been used by various attackers for the last few years. While it is recently distributed through SmokeLoader or Emotet, this malware has steadily been used in various ransomware attacks in the past. The infected system utilizes SystemBC, which acts as a Proxy Bot. Because it can also act as a downloader to install additional malware externally, attackers can also use it to install additional payloads.
Recent Distribution Cases:
In March 2022, it was found that SystemBC was being installed as an additional payload by Emotet. Emotet is a banking malware that installs additional modules or malware strains to steal credentials from the infected system. Normally, the attackers install Cobalt Strike through Emotet to dominate the infected system, but recently, SystemBC is also being distributed.
According to AhnLab’s ASD infrastructure, most of the recent cases involving SystemBC have malware installed by SmokeLoader.
SmokeLoader operates by being injected into explorer.exe (Windows Explorer that is currently being run) and can install additional modules or malware. The figure below shows the log of the injected Explorer process installing SystemBC.
Also Read: Hunting for Suspicious Windows Services – Mind Map
Analysis of SystemBC:
SystemBC has a number of variants. But the variants are categorized based on their additional features. Unlike Type 1 which is an early version and can only update itself, Type 2 can run scripts such as Batch, VBS, and PowerShell after downloading them. It can also download malware in DLL and Shellcode forms to execute them in the memory.
In addition, the malware can communicate with the C&C server through the Tor network. This post will discuss the analysis of SystemBC type that can currently communicate with the C&C server. To be more precise, it is an analysis of Type 2.
Initial Routine:
When SystemBC is initially run. , It checks the windows current running processes. If there is a process with “Microsoft” as the window name and “win32app” as the class name, it will send the message “WM_COPYDATA” and goes inactive for a certain amount of time. Afterward, it deletes the file for the process.
Later , SystemBC register this window class and created a window. The name of the window and class is “Microsoft” and “win32app” respectively. As shown in the figure below, the following windows and classes can be seen when SystemBC is executed.
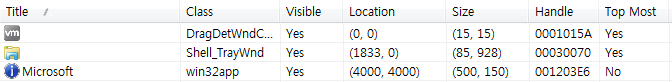
It then scans the process named “a2guard.exe” which is assumed to be a product of Emisoft. If the process is running, it terminates itself and will no longer perform malicious behaviours. Lastly, it copies the binary of the currently running SystemBC as a random name in %ALLUSERSPROFILE% (in the random folder of the ProgramData path). The process uses COM objects, TaskScheduler class, and methods of the Task class.
The task runs every 2 minutes. The target that is executed is SystemBC, and designates “start” as an argument. SystemBC can download payloads in exe form from the C&C server and run them. If the downloaded executable is SystemBC with the latest version, the process then becomes a binary update for SystemBC.
Also Read: Most Common Malware Obfuscation Techniques
C&C Communications:
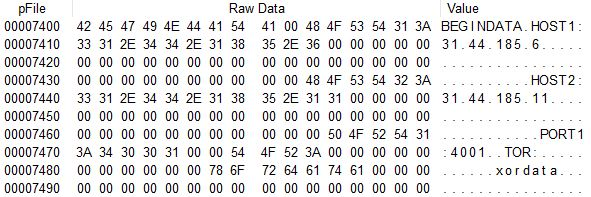
SystemBC executed with the “start” argument attempts to communicate with the C&C server. It has the URL of the C&C server in the data section in XOR-encrypted form.
The malware decrypts the C&C server address and port number before communicating with the C&C server. If it cannot access the first URL, it will attempt to communicate with the second one.
Since the current analysis target does not have its settings data encrypted, one can check it in its plain form. The 0x32 byte-sized data that has the string is the value for the RC4 key. If a normal RC4 key value exists, the XOR encoding will be processed.
The encrypted data is then sent to the C&C server. SystemBC uses the Raw TCP socket to communicate with the C&C server. When the server receives information from the malware, it uses the same RC4 key to send the encrypted command data. The following is encrypted data sent from the C&C server.
- C&C Server URL 1: 31.44.185[.]6:4001
- C&C Server URL 2: 31.44.185[.]11:4001
The encrypted data is then sent to the C&C server. SystemBC uses the Raw TCP socket to communicate with the C&C server. When the server receives information from the malware, it uses the same RC4 key to send the encrypted command data. The following is encrypted data sent from the C&C server.
Note that the exe malware downloaded currently is also SystemBC; this indicates that the command is for updating the binary.
- Download URL: hxxp://michaelstefensson[.]com/supd/s.exeSystemBC uses Raw TCP socket again for HTTP communications. The following is a User-Agent string used for downloading binaries from the URL that was sent.
GET %s HTTP/1.0
Host: %s
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0
Connection: closeAfter the download is complete, the malware sends the result encrypted with RC4 to the C&C server.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
The download URLs that were sent are categorized depending on the file extension and format.
| Type | Extension | Format | Feature |
| exe | exe | – | Self-update for SystemBC |
| VBS script | .vbs | – | Run VBS script |
| Batch script | .bat | – | Run Batch script |
| Batch script | .cmd | – | Run Batch script |
| Powershell Script | .ps1 | – | Run Powershell script |
| DLL | – | DLL | Load DLL in the memory Run the function of DLL if the URL has # at the back |
| Shellcode | – | Encoded form | Run Shellcode in the memory |
The malware creates normal files in the Temp path and registers the files in the task scheduler to run them. For Powershell scripts, it additionally uses command lines such as “-WindowStyle Hidden -ep bypass -file”.
If the downloaded payload is DLL, it assigns memory and loads it to run as a new thread. If the “#” string is behind the URL sent from the C&C server, it calls the export function from the downloaded DLL. For Shellcode, the malware also runs it as a new thread going through the decoding routine. As a result, DLL and Shellcode are not created as files but run in the memory of SystemBC.
TOR Communications:
The malware in this case has the C&C server URLs encoded as shown below. If it cannot access both servers, it uses Tor to access another server.
- C&C Server URL 1: admex175x[.]xyz:4044
- C&C Server URL 2: servx278x[.]xyz:4044To do so, it accesses the following URLs to obtain a public IP address. The address is then encoded with the data that will be sent to the C&C server and sent.
https://api.ipify.org/
https://ip4.seeip.org/SystemBC is known to utilize the mini-tor library to use the Tor network It first goes through the reset process to access Tor.Tor C&C URL needs an additional decryption process, unlike normal C&C URLs that can be checked in text after Xor decryption.
- C&C URL (Tor): dfhg72lymw7s3d7b[.]onion:4044After normally accessing the Tor network, the malware will send the information of the infected system including the public IP address that was mentioned earlier. This method is identical to other methods of using Raw TCP socket communications, except that it sends data by using the Tor network. So the malware will send the data encrypted with RC4 algorithm and receive C&C commands encrypted with the same key as in previous cases. The case is also the same for the HTTP communications used for downloading additional payloads.
- Download URL: http://5.61.33[.]200/henos.exeSOCKS5 PROXY:
Besides downloader, the main features of SystemBC include being able to operate as Proxy Bot.If the attacker wants to use an infected system as Proxy Bot (using SystemBC of the infected system when accessing a certain address), a command to create proxies will be sent first. SystemBC creates a socket depending on the type when it receives a command to create proxies. The created socket will be managed by index.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Should the attacker send requests to a certain address later, they will send the created proxy socket with the assigned index. SystemBC will then send the data it received to the address. The data received will be sent to the C&C server through SystemBC. SystemBC thus acts as Proxy Bot, allowing the attacker to hide the IP when performing attacks. If the malware operates in the system that can access internal networks, the networks can be accessed by the external attacker through SystemBC.
Indicators of Compromise:
AhnLab’s anti-malware software, V3, detects and blocks the malware above using the aliases below.
[File Detection]
– Trojan/Win.MalPE.R480644 (2022.03.29.02)
– Trojan/Win.Generic.C5006057 (2022.03.11.03)
– Malware/Win32.RL_Generic.R358611 (2020.12.18.01)
– Trojan/Win32.Agent.C3511593 (2019.10.14.08)
[IOC]
Type 1 MD5
– beb92b763b426ad60e8fdf87ec156d50
Type 2 MD5
– 8e3a80163ebba090c69ecdeec8860c8b
– 28c2680f129eac906328f1af39995787
Type 3 MD5
– ae3f6af06a02781e995650761b3a82c6
Type 1 C&C
– db1.pushsecs[.]info:40690
– db2.pushsecs[.]info:40690
Type 2 C&C
– 31.44.185[.]6:4001
– 31.44.185[.]11:4001
– admex175x[.]xyz:4044
– servx278x[.]xyz:4044
– dfhg72lymw7s3d7b[.]onion:4044
Type 3 C&C
– 96.30.196[.]207:4177
– 45.32.132[.]182:4177
Download URLs
– hxxp://michaelstefensson[.]com/supd/s.exe
– hxxp://5.61.33[.]200/henos.exe
Ever since SystemBC was distributed through exploit kits in the past, the malware has been installed through other malware strains from malicious websites disguised as download pages for cracks and serials of commercial software until recently. While it was used for attacks targeting normal users, it was also employed by attackers in multiple ransomware attacks targeting companies to achieve their goals.
After it is installed, SystemBC stays in the infected system to download additional payloads. Moreover, it can also act as Proxy Bot, meaning that the system can become a passageway for other attackers. Users should apply the latest patch for OS and programs such as Internet browsers, and update V3 to the latest version to prevent malware infection in advance.
Source : Asec Ahnlab



































