Attackers use tools to scan networks for vulnerabilities and sometimes these tools can be used to our advantage. Here we describe one of the more popular vulnerability scanning tools and techniques and demonstrate how net defenders and analysts can leverage them for threat intelligence purposes.
Out-of-band application security testing (OAST) is a method for finding exploitable vulnerabilities in a web application by forcing a target to call back to a piece of infrastructure controlled by the tester. This type of testing can be facilitated by OAST tools such as those provided by Project Discovery (interact.sh) and Port Swigger (Burp Collaborator). These tools have become increasingly popular in recent months and currently account for a large proportion of scanning activity in general.
How does OAST work?
OAST improves the results returned by DAST security testing ( Example: OWASP ZAP ). In many ways, it is itself a dynamic method, albeit one that can see “around corners”. This is because “dynamic application security testing” really just denotes a test that can’t see the inner workings of an application. This could also describe OAST.
Also Read: Race Condition Attack – How to Prevent Race condition vulnerabilities in your organization
Attacking from the outside
Conventional dynamic testing is elegant in its simplicity. In essence, it sends payloads to a target application and analyses the responses that come back – just like a real attacker might:
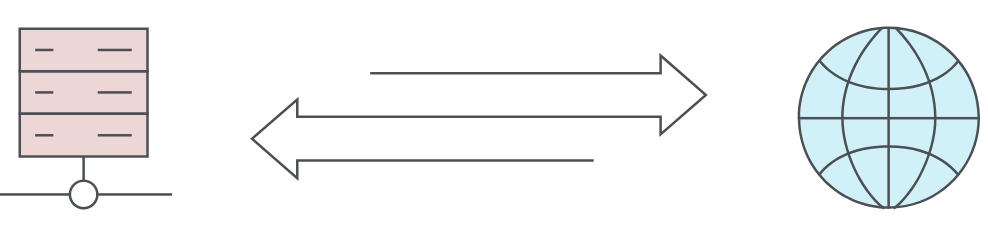
When you send a DAST payload and your target comes back to you with a response suggesting a vulnerability, you can be pretty sure it’s real. Dynamic testing has achieved the success it has because it works well in these situations.
But what if a target app doesn’t send back a response to a payload, even though the target is actually vulnerable? This is a particular problem when an app is working asynchronously. Traditional DAST techniques alone just won’t see it.
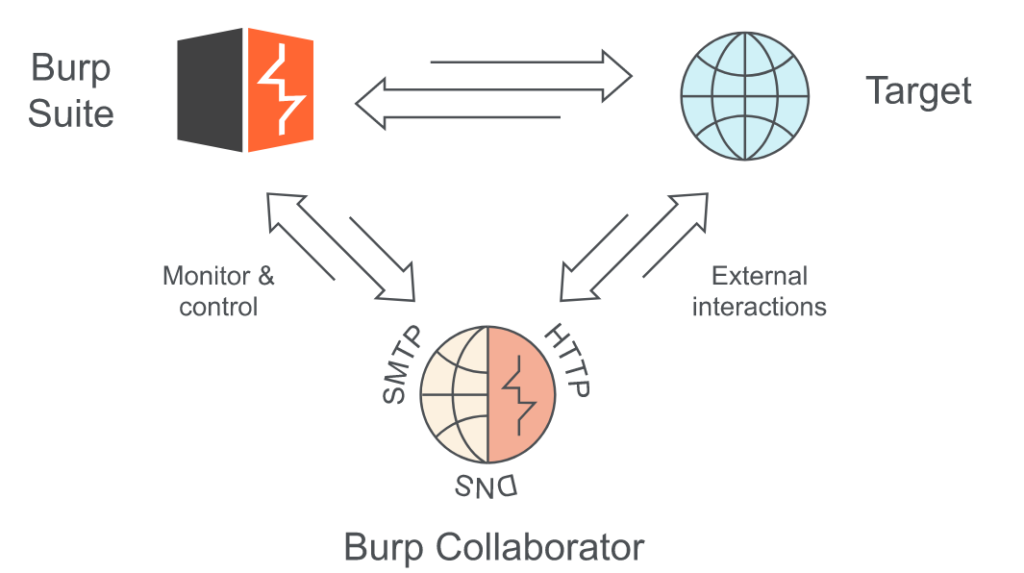
Burp Collaborator performs OAST by introducing a new channel of communication into the dynamic testing process. So, what’s actually happening here? Burp Collaborator can search for a huge range of vulnerabilities that were once invisible to DAST testing.
If a vulnerability is blind SQL injection, then it sends back no useful response to us when we send a test attack – even if that attack is successful. We need a way to bypass this. Out-of-band testing methods are that bypass. This is a silent way to perform attacks without any noise. It is done by sending an attack payload that causes an interaction with an external system we have control over, that sits outside the target domain.
Also Read: Credential Stuffing Attack Prevention and Detections
Why SOC Operations Should Care?
Out-of-band application security testing (OAST) uses standard external domains to share the organization’s information. These external domains are configured to explore vulnerabilities in the corporate environment. If below given external domains are observed in logs. Soc analyst is advised to reach the machine owner to understand whether is a legitimate business risk assessment or can be a reconnaissance activity to explore vulnerabilities.
Out of band interaction domains
| interact.sh |
| oast.pro |
| oast.live |
| oast.site |
| oast.online |
| oast.fun |
| oast.me |
| burpcollaborator.net |
| oastify.com |
| canarytokens.com |
| requestbin.net |
| dnslog.cn |
Matt Kelly says during the Confluence vulnerability, if you see DNS resolves to domains like http://interact.sh & http://oast.me – you likely have an exploitable web app that was just found. $hostname.interact.sh is a common way to look for RCE via out-of-band interaction. Also, he had added, Detecting resolution to these domains is a way to find vulnerable systems in your network that probably is about to be (or already were) exploited. A better practice would be to stop recursive DNS resolves on DMZ systems (including no Internet).
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Detection Rules
Qradar:
SELECT UTF8(payload) from events where "query" ilike '%.interact.sh%' or "query" ilike '%.oast.pro%' or "query" ilike '%.oast.live%' or "query" ilike '%.oast.site%' or "query" ilike '%.oast.online%' or "query" ilike '%.oast.fun%' or "query" ilike '%.oast.me%' or "query" ilike '%.burpcollaborator.net%' or "query" ilike '%.oastify.com%' or "query" ilike '%.canarytokens.com%' or "query" ilike '%.requestbin.net%' or "query" ilike '%.dnslog.cn%'Splunk:(query="*.interact.sh*" OR query="*.oast.pro*" OR query="*.oast.live*" OR query="*.oast.site*" OR query="*.oast.online*" OR query="*.oast.fun*" OR query="*.oast.me*" OR query="*.burpcollaborator.net*" OR query="*.oastify.com*" OR query="*.canarytokens.com*" OR query="*.requestbin.net*" OR query="*.dnslog.cn*")GrayLog:query.keyword:(*.interact.sh* *.oast.pro* *.oast.live* *.oast.site* *.oast.online* *.oast.fun* *.oast.me* *.burpcollaborator.net* *.oastify.com* *.canarytokens.com* *.requestbin.net* *.dnslog.cn*)RSA Netwitness:(query contains '.interact\.sh', '.oast\.pro', '.oast\.live', '.oast\.site', '.oast\.online', '.oast\.fun', '.oast\.me', '.burpcollaborator\.net', '.oastify\.com', '.canarytokens\.com', '.requestbin\.net', '.dnslog\.cn')Elastic Query:dns.question.name:(*.interact.sh* OR *.oast.pro* OR *.oast.live* OR *.oast.site* OR *.oast.online* OR *.oast.fun* OR *.oast.me* OR *.burpcollaborator.net* OR *.oastify.com* OR *.canarytokens.com* OR *.requestbin.net* OR *.dnslog.cn*)ArcSIGHT:(deviceCustomString1 CONTAINS "*.interact.sh*" OR deviceCustomString1 CONTAINS "*.oast.pro*" OR deviceCustomString1 CONTAINS "*.oast.live*" OR deviceCustomString1 CONTAINS "*.oast.site*" OR deviceCustomString1 CONTAINS "*.oast.online*" OR deviceCustomString1 CONTAINS "*.oast.fun*" OR deviceCustomString1 CONTAINS "*.oast.me*" OR deviceCustomString1 CONTAINS "*.burpcollaborator.net*" OR deviceCustomString1 CONTAINS "*.oastify.com*" OR deviceCustomString1 CONTAINS "*.canarytokens.com*" OR deviceCustomString1 CONTAINS "*.requestbin.net*" OR deviceCustomString1 CONTAINS "*.dnslog.cn*")SUMO LOGIC:(_sourceCategory=*dns* AND (".interact.sh" OR ".oast.pro" OR ".oast.live" OR ".oast.site" OR ".oast.online" OR ".oast.fun" OR ".oast.me" OR ".burpcollaborator.net" OR ".oastify.com" OR ".canarytokens.com" OR ".requestbin.net" OR ".dnslog.cn"))Microsoft Sentinel:Dns | where (query contains '.interact.sh' or query contains '.oast.pro' or query contains '.oast.live' or query contains '.oast.site' or query contains '.oast.online' or query contains '.oast.fun' or query contains '.oast.me' or query contains '.burpcollaborator.net' or query contains '.oastify.com' or query contains '.canarytokens.com' or query contains '.requestbin.net' or query contains '.dnslog.cn')References: https://portswigger.net/burp/application-security-testing/oast https://www.lacework.com/blog/the-oast-with-the-most/



































