NetworkMiner is an open source Network Forensic Analysis Tool (NFAT) for Windows (but also works in Linux / Mac OS X / FreeBSD). NetworkMiner can be used as a passive network sniffer/packet capturing tool in order to detect operating systems, sessions, hostnames, open ports, etc. without putting any traffic on the network. NetworkMiner can also parse PCAP files for off-line analysis and to regenerate/reassemble transmitted files and certificates from PCAP files.
NetworkMiner makes it easy to perform advanced Network Traffic Analysis (NTA) by providing extracted artifacts in an intuitive user interface. The way data is presented not only makes the analysis simpler but also saves valuable time for the malware analyst or forensic investigator.
Installation & Start Guide
- Download the tool here
- Disconnect Internet on sandbox machine and isolate your VM from other machines.
- Run Wireshark on sandboxed machine and record all PCAP files for later analysis.
Getting Started
- Export the PCAP file from wireshark and import it on networkminer.
- Here we have an sample for BazarLoader-Malware.
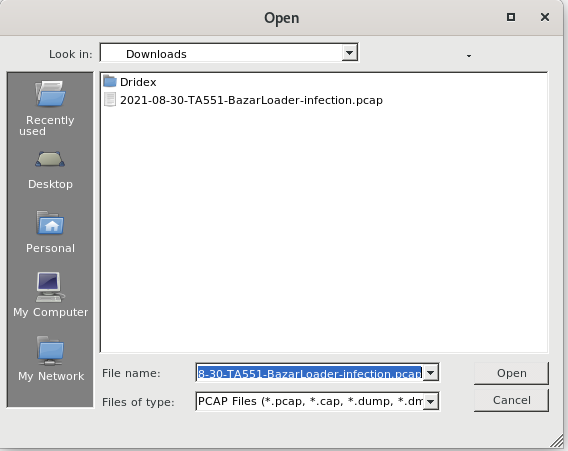
Malware Hosts
- Post implementing the .PCAP file .Navigate to Host Tab, Here we have a quick overview of malware commuicating IP addresses and its domains.
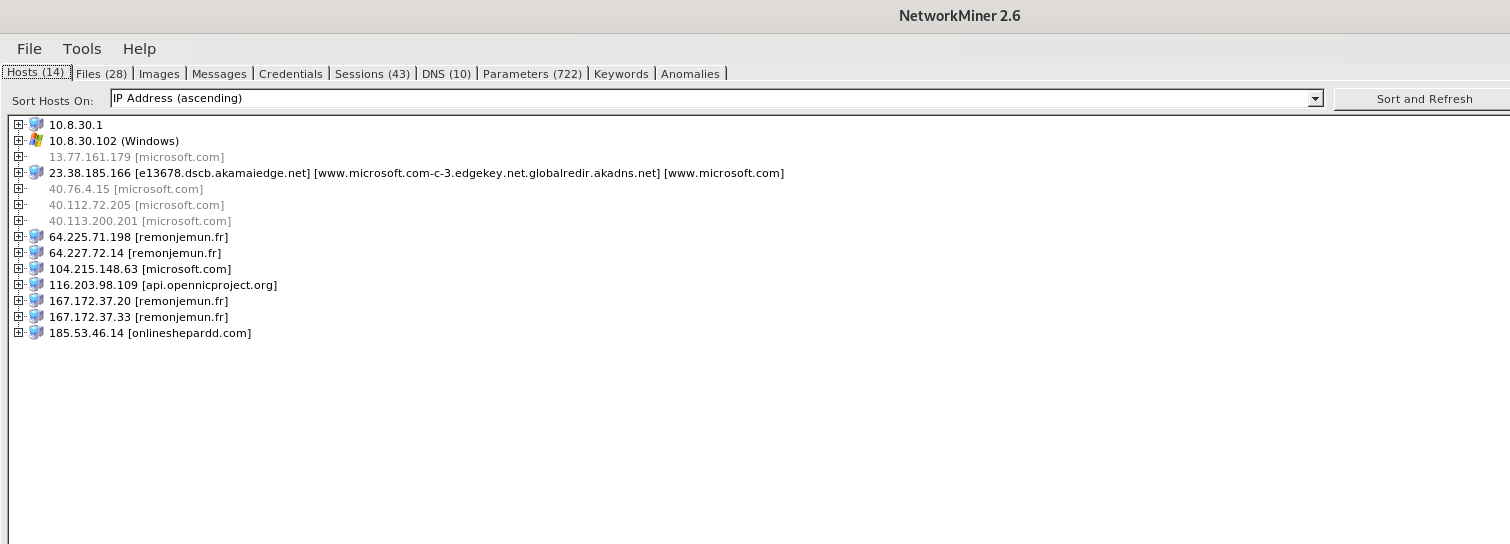
- Expanding the Tree gets you more information such as infected machine , MAC address, NIC Vendor Name ,IP Address , Operating system information, Incoming & Outgoing sesssion bytes, DNS queries and JA3 Hashes for SSL/TLS finger printing.
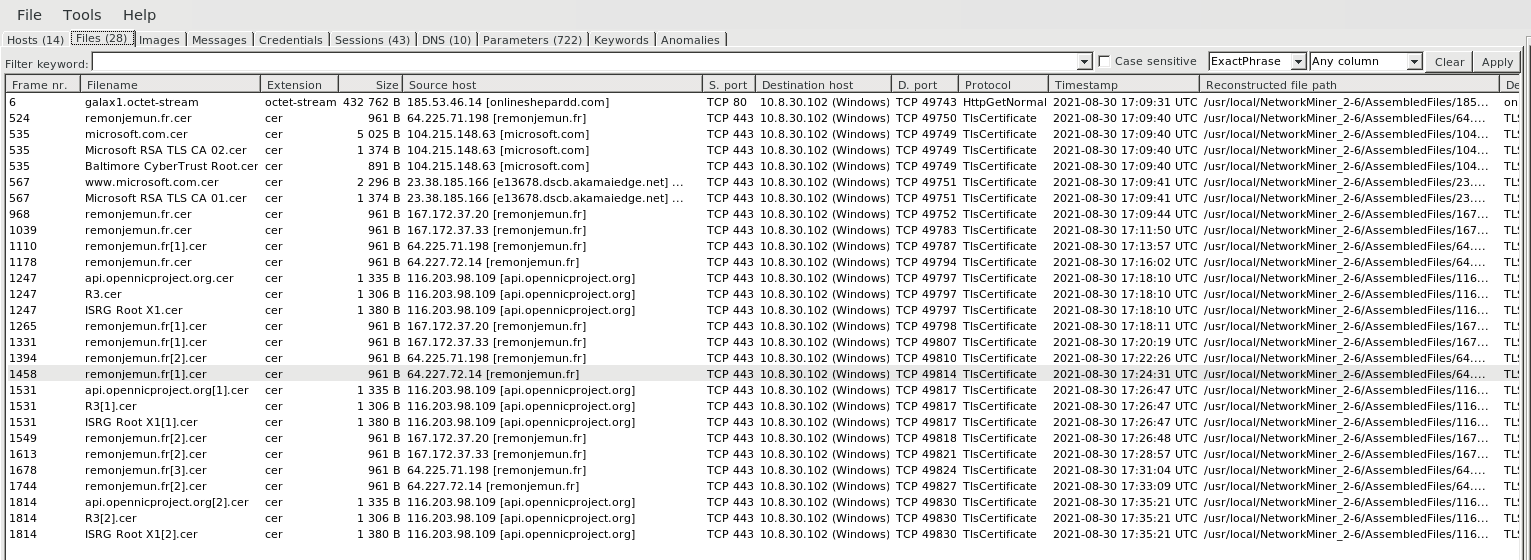
Malware Files
- File Tab , Provides information on malware files names that are exhanged between source IP address to Destination Machine , Protocol usage , File Size , Timestamp information.
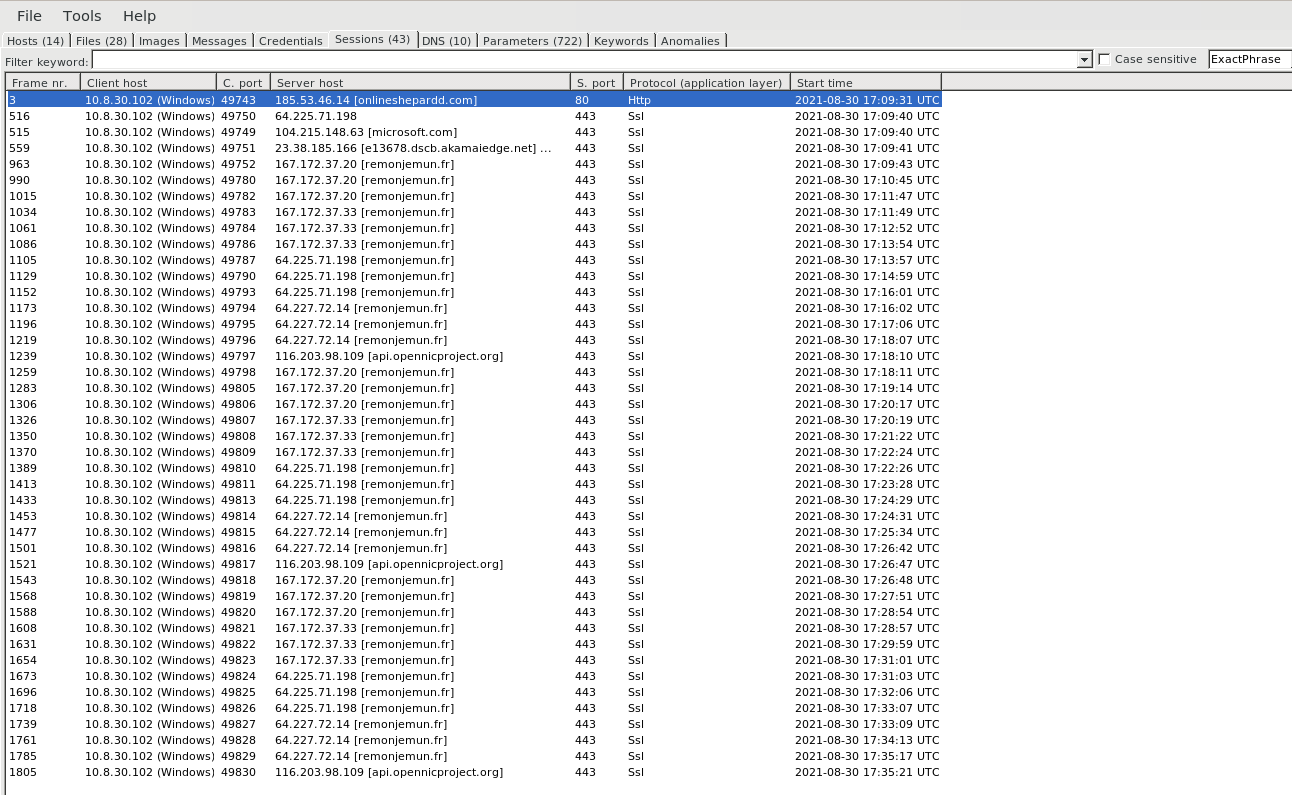
Malware Sessions
- Session Tab , Provides information on malware establishing session information such as source & Destination Port numbers , Protocol, Client Host and Server Host.
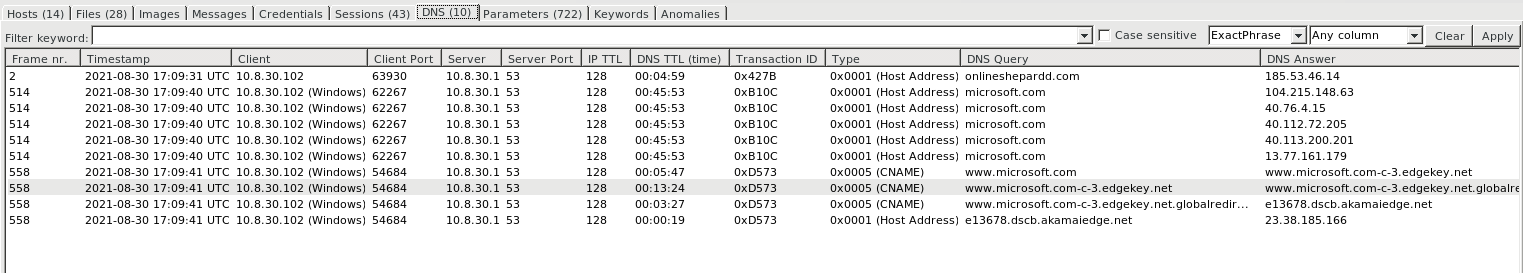
Malware DNS Communications
- Session Tab , Provides information on malicious DNS queries established by clinent and its DNS Record Types , DNS Query , DNS answers & TTL.
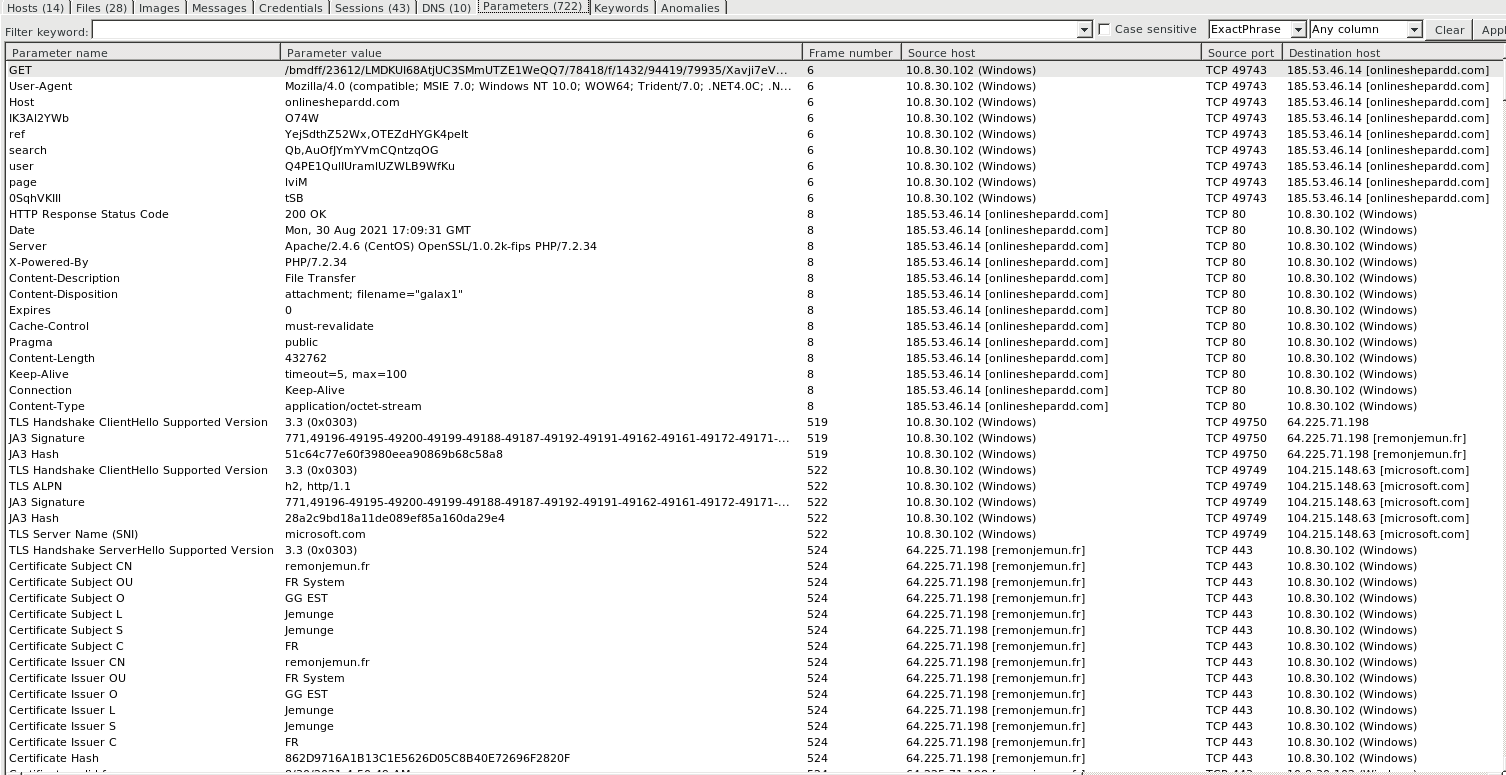
Parameters
- Parameters Tab , Provides information on HTTP Methods , HTTP Header Details , TLS certificate Details & JA3 Hashes are generated for all unique TLS connections.
JA3 Signature to Identify Malware
- TLS Fingerprinting are used with JA3 ,JA3S Hashs, JARM hashes. These are more effective way to detect malicious activity over SSL/TLS , other then depending on external threat feeds.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
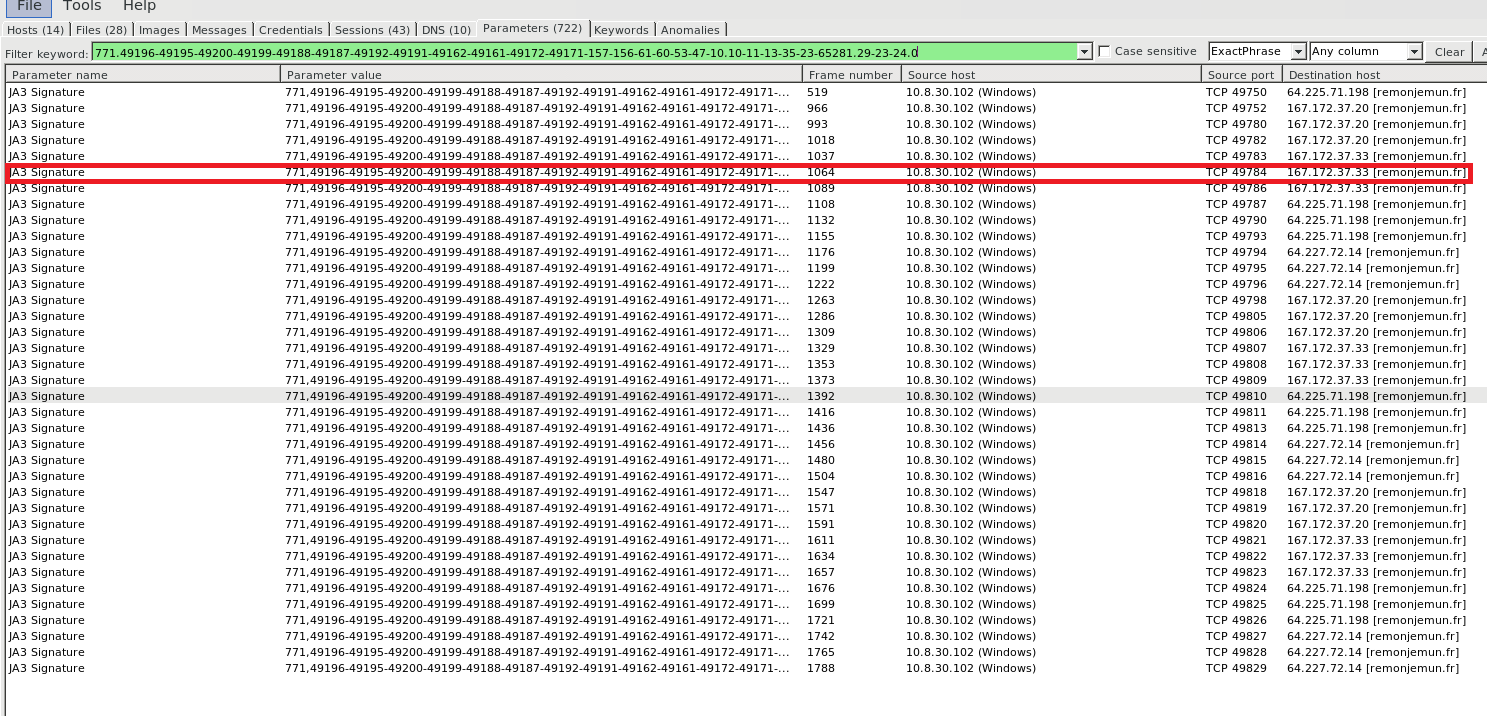
- Here we choose one of the JA3S Hash paremeter copied.
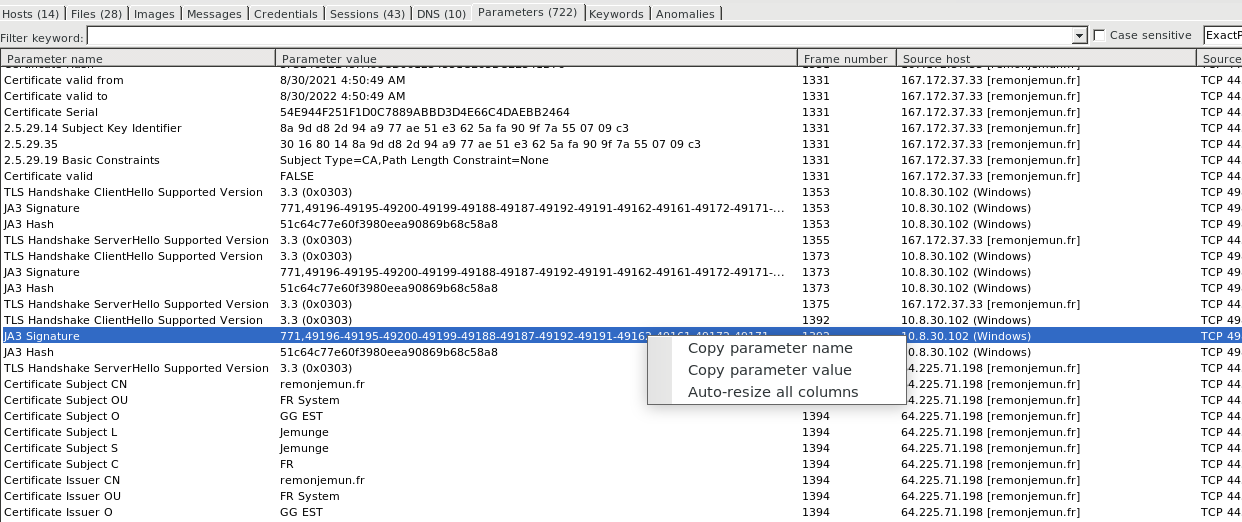
- Searching the JA3 Signature in parameter tab , shows the list of TLS fingerprints genrated by JA3 Hash for the malware communicating for the domain remonjemun[.]fr , The frequency of commuincation is high and internal Clients each TLS connections are sniffed to populate this indicators and the malware hostnames are gathered from TLS hannshake ( Client Hello Packet )
Also Read: Finding the Evil in TLS 1.2 Traffic – Detecting Malware on Encrypted Traffic
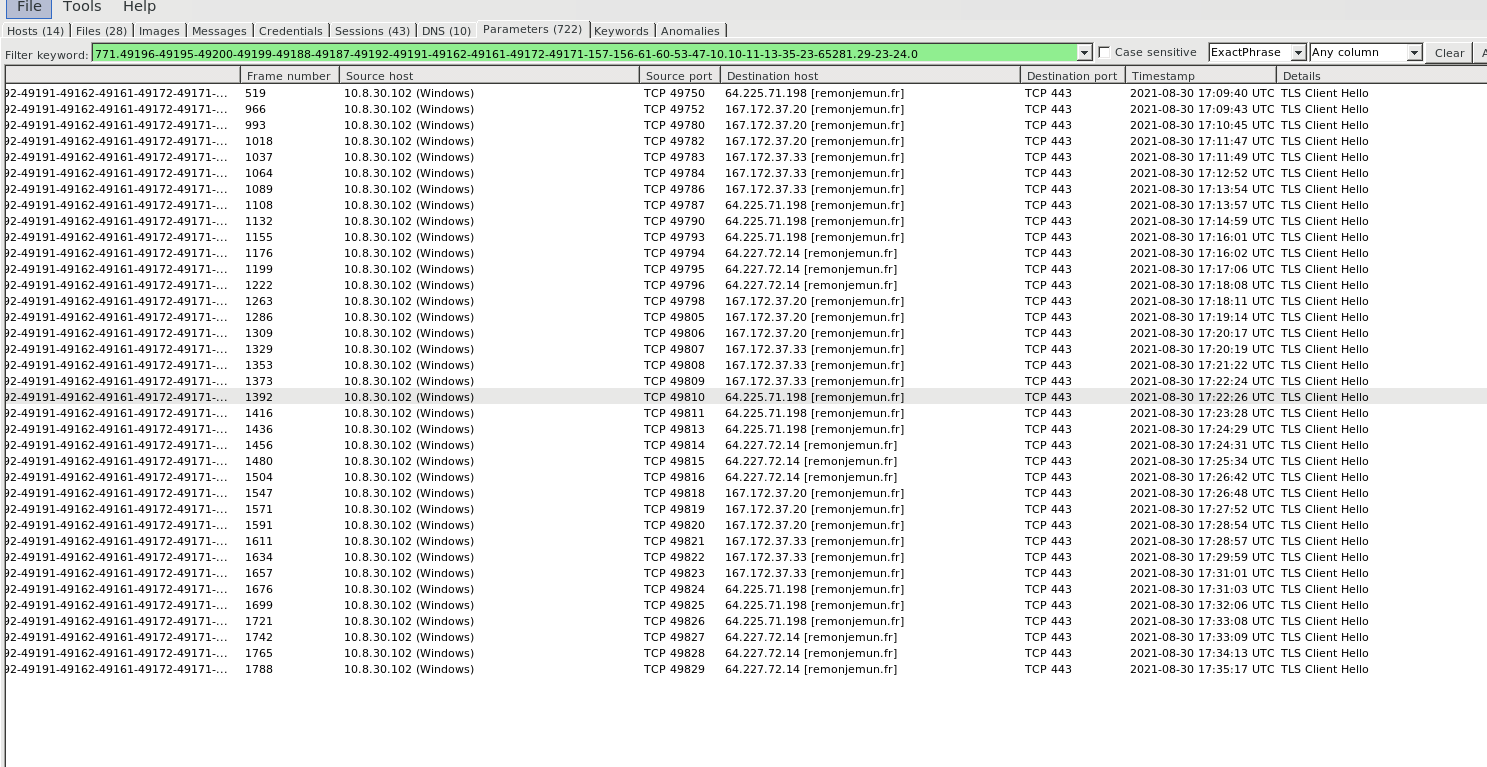
- Unless your PCAP has more information other tabs ( Images , Messages , Credentials , Keywords , Anomalies ) data will be populated.
As part of dynamic analysis, NetworkMiner is a pretty awesome tool to check the indicators of compromise with faster analysis.
Pcap source: Malware Traffic Analysis
Happy Hunting !!!



































