Adversaries use windows operating in a possible way to deliver the malware and here we have the windows utility which helps an attacker to deliver a compressed file in target, Extract and execute malicious files with windows inbuilt functionalities itself, Here we have a .cab file ( file format), which is likely to look suspicious from the name itself. Before suspecting sometime, Inspect such file behaviors in an Isolated/Sandboxed environment and observe the activity is legitimate or suspicious.
What is Cab File?
.Cab is the Archive format of Microsoft, File names with .cab extension indicates the file is compressed and it is in Microsoft archived format., Either the content of the archives may have can have legitimate software for operating system functionality or It may contain a piece of malware codes also.
How Threat Actors build .cab files?
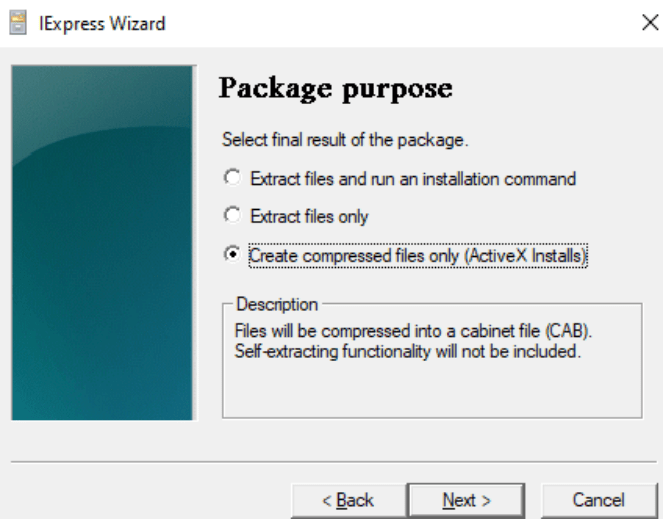
There are lots of ways to do this from the attacker’s perspective, But one of the easiest methods is to use the windows operating system inbuild programs to create .cab files. Here we use the simple internal tools ( Iexpress wizard ) in any windows operating system. This helps compress the files and extract them as .cab file executables files and extract as .cab files. Alternate ways to create this file is to search Google for exe to .cab converter keywords, It helps attackers right!
What is Extrac32.exe?
Extrac32.exe is the windows legitimate Process used to uncompress one or more compressed data ( .cab files )
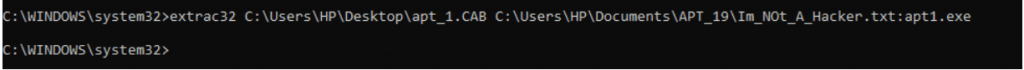
Extrac32 utility supports destination file copy, download, extraction in the Windows filesystem. Adversaries use these functionalities to extract the malicious executables and transfer the malicious data into the NTFS ADS ( Alternate Data Stream ), hidden malicious data inside the NTFS ADS filesystem can be leveraged for later execution. Hiding of data is not limited to extrac32, there are lots of ways in which malicious data can be hidden in the filesystem. Extrac32 is one among them.
Also Read : Malware Hiding Techniques in Windows Operating System
To Detect these malicious activities?
Gather the suspicious signs of artifacts, track the actor timeline, and possible additional clues on endpoints and network. Don’t rush your analysis as false-positive when windows utility is running in the endpoint. Despite of windows operating systems legitimate inbuilt utility, Collect the list of hashes & windows command-line arguments observed from this legitimate utility and action them according. Below we used a free open source tool to export the malicious files from NTFS ADS
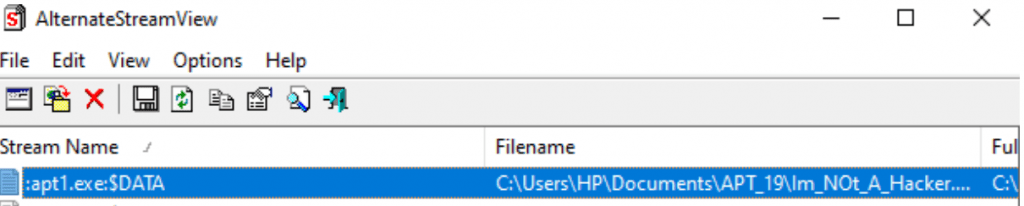
Alternate stream viewer is the software which is used to find the hidden data in the NTFS ADS.Above image shows we have some .exe data hiding on the file ”Im_Not_A_Hacker.txt” , Lets hunt !!
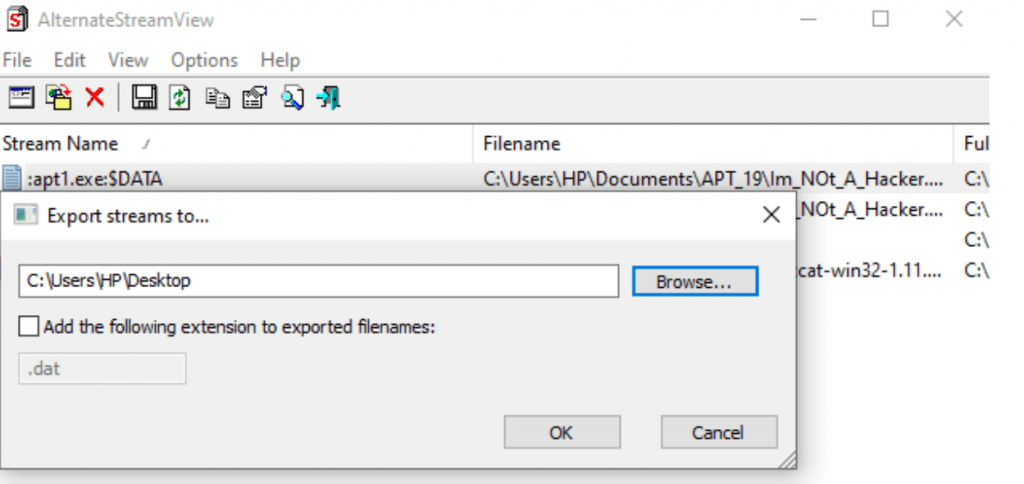
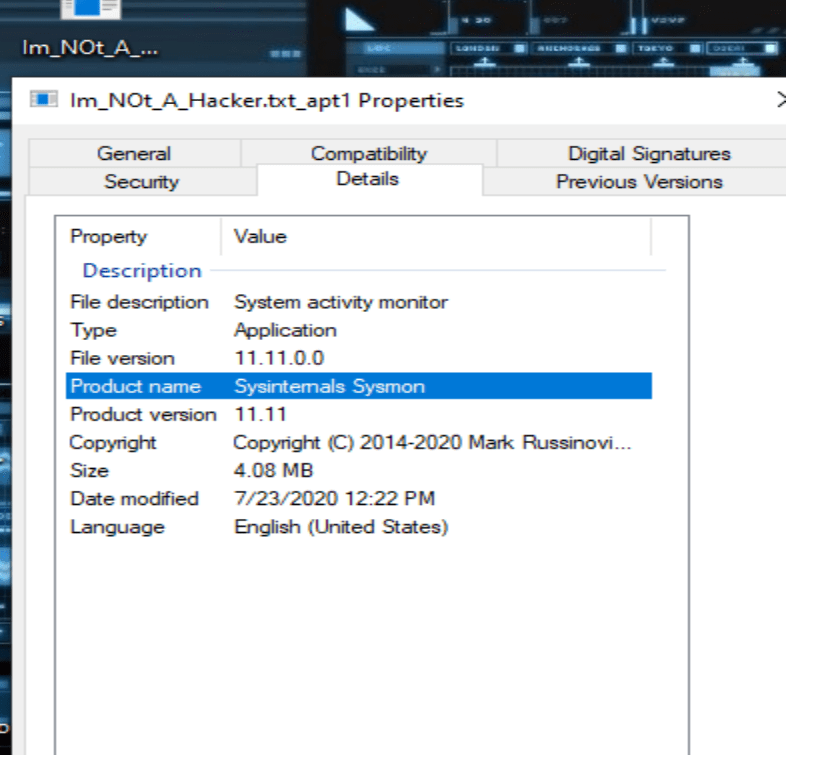
Here We found a file name, “SYSMON” which is legitmate. In similar ways, Malicious files can also be hidden and executed.
Happy Hunting !!!



































