The Windows Registry is a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry on runtime. Adversaries use various techniques to achieve persistence on the network and connect back to their CnC ( Command and Control ) server. The most common way is Registry key value modification.
What are Run keys in Registry?
The registry holds a set of keys, which will handle the operating system setting for the device drivers, services, Security Accounts Manager, and user interface, etc. Adding the new string under the run key will execute a specific program at user boot or logon.
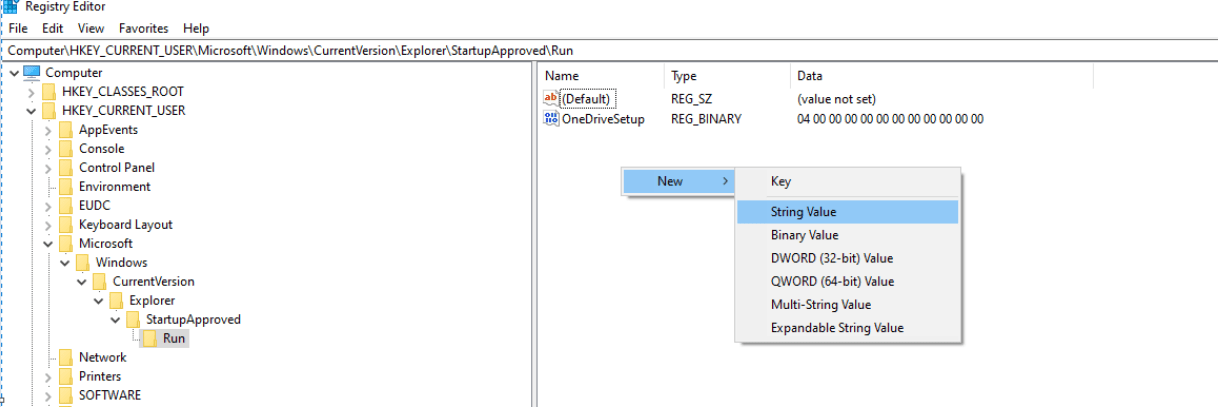
How Threat Actors intercept those keys?
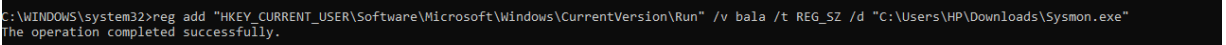
Threat actors May use windows terminal to add their specific application which needs to be executed the next boot time. Here we are using “reg add” to interact with the registry and add a new string under the HKCU ( HKEY_CURRENT_USER ) hive to execute the malware on runtime. However, the file “sysmon.exe” will be executed only on the next boot.
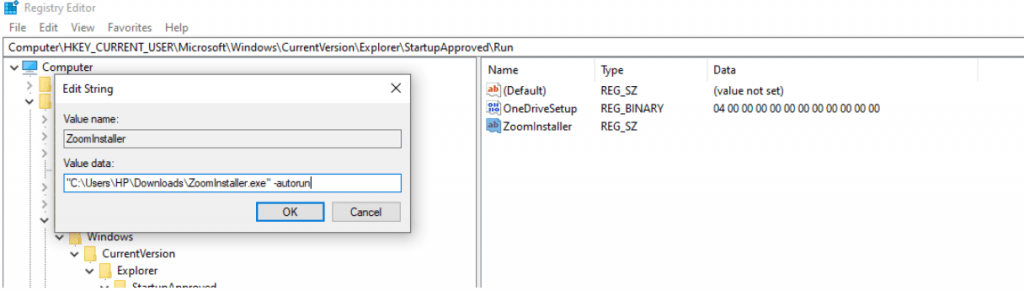
Similar persistence can be achieved with GUI also, Here we are trying to execute the “zoom installer” with auto-run on run time.
Also Read: APT-Hunter – Threat Hunting Tool For Windows Event Logs
Additional keys for Malware Persistence
Below registry keys can also help attackers to be persistent on windows for a long time and steal confidential data and exfiltrate to their domains. Be cautious when you see an alert with your EDR ( Endpoint Detection and response ) or AV Antivirus products for such behaviors.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\Session Manager
In addition with one of above behavior ,Figure out & find the Event ID : 4657 in you Log analytics tool.This event ID will help soc analysts /Incident responder to find the registry value changes .
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Note: Investigate your incidents according, This event ID is logged only if the auditing feature is set for the registry key in its SACL ( A system access control list )
Successful combination of these registry attempts with event ID 4657 illustrates the bad actor successfully accessed your systems and backdoor files are uploaded to the victim machine. Happy Hunting !!!



































