Website Malware:
Malware is often used by hackers to attack legitimate websites. They prefer to attack websites that aren’t well-protected because it’s easier to infect them. Infecting websites can be done in a variety of ways. They use phishing, fraudulent websites, backdoors, source code alteration, disguised plugins, and drive-by downloads to spread malware.
Malicious software (malware) is installed on a website when it is hacked, either by altering existing files or folders or by adding new files. Malware is software that is designed to harm your website and is difficult to detect. Figuring out whether part of the code is malware that has to be removed can be difficult if you are unfamiliar with how website code looks. Because each hack is unique, it’s simply a matter of searching through your website’s files and figuring out what’s not supposed to be there.
Steps to find Malware on your Website:
At first, you need to know whether your website has been hacked. It could be acting strangely for a variety of reasons such as
- Your website visitors are being redirected to illegitimate website
- Your website is defaced
- Your website loading speed had slowed drastically
- Your website is sending emails on its own
- You observe suspicious files, folders, and code on your website
You can check this by running free online web scanners like Virus Total, Sucuri, Hosted Scan Security, Upguard, Observatory.
You can check Google’s safe browsing site status page if you think your site is being blocked due to malware. If Google’s software has scanned the site and determined it to be unsafe to access, it will inform you.
Follow the steps below, which will explain how to clean up the problem.
Back Up Your Website
A backup of your website is a copy of all of your data, files, and databases. Its goal is to prevent data loss if something happens with your current site breakdown.
you have three options for backing up your site: Using FTP and phpMyAdmin manually. Download a full website backup and use the one-click restoration feature in CPanel. Download a full account, home directory, and selected file backups from cPanel.
Reset Login Credentials
You have no idea where the infection came from at this point. It could have originated from a compromised account in which the attacker found or guess the password. First, search the CMS for any accounts that should no longer be active or have no reason to exist. Deactivate each and every one of those accounts. Second, all valid accounts’ passwords should be changed. The administrative account is included in this. Make that the new passwords are secure.
Remove or Uninstall all Unused Plugins or Extensions
Plugins and extensions downloaded from unknown sources may be dangerous. Others may be poorly written and vulnerable to security breaches, or they may be obsolete versions with obvious vulnerabilities. Any of these could have been used by an intruder. If they aren’t eliminated, they may become a source of re-infection after the problem has been resolved.
Remove any components from your website’s software that are unwanted, outdated, or no longer accessible. Check to see if the legitimate components are the most recent version available from the publisher. This may or may not solve the problem, but it will certainly make the site less vulnerable to future attacks.
Review the environment configuration files
Many websites are created with a content management system (CMS) that includes the PHP programming language and is hosted on the Apache Web server. The following assumes that your website is built on the PHP programming language. There will be minor modifications in the method with other Web servers, such as Nginx.
php.ini and.user.ini are PHP configuration files that are used to change PHP functionality. If these files are compromised, malicious PHP files could be preloaded or post loaded. They might change permission settings to give hackers more access to websites and give attackers more control.
The .htaccess file in the Apache setup includes rules for how the Web server will handle HTTP requests. Changing this file is a common approach used by traffic-stealing malware. Users can be redirected to a scam site by changing one line in .htaccess. The following line, for example, will redirect all website pages to a different domain:
http://scamwebsite.com/ 301 redirect
Look over your .htaccess file for any strange “redirect” directives or other abnormalities. Check your current.htaccess file against the one that came with your CMS. This will assist you in recognizing all changes and detecting any infections.
Remove malware from a CMS
If your website is built with a CMS, a smart place to start is with the original installation files, which are free to download and are not infected. Download your CMS’s installation files. It must be the same version as the one you already have installed.
In File Manager, open the installation files on your computer and compare them to the list of infected files. If the infected file isn’t found in the installation files and isn’t part of an extension or template, it’s most likely malware that should be uninstalled entirely. If the infected file is part of the installation files, replace it with the file from the installation that you just downloaded.
If the configuration file (configuration.php, wp-config.php) with your database connection details is infected, you must add the login details for your database. If the infected file is part of a plugin, extension, template, or other modules you’ve installed in your CMS, you can uninstall it and reinstall the plugin later.
After you’ve gone through all of the files and either altered or deleted them, you’ll want to make sure your CMS is up to date. The same may be said for your templates, themes, extensions, and other extensions.


Manual Malware Removal from Files and Database
1.Check Recently Modified Files
You can identify hacked files by seeing if attackers were recently modified files,
- Use an FTP client or an SSH terminal to connect to your server.
- If you’re using SSH, type the following command to see a list of all files that have been edited in the last 15 days:
$ find ./ -type f -mtime -15
- If you’re using SFTP, go through all of the files on the server and look at the last changed date column.
- Make a note of any recently updated files.
2. Examine Modified Files and Other files
In some scenarios, such as if your website is custom-built, you may need to remove the malicious payload from the file. It will be tough to tell what is malware and what isn’t unless you are skilled with coding.
Malware code is usually placed to the top or bottom of the file in most situations. Malware is frequently composed of large sequences of text that appear to be lengthier than the remainder of the file’s code. We recommend editing the file in File Manager because it displays the syntax in color, making it simpler to notice any code that doesn’t seem right. Remove the malware from the file and hit Save once you’ve detected it.
3. Investigate database rows
Custom configuration, website pages, theme settings, analytics, and much more are all stored in the database tables. This functionality can be used by malware makers to inject harmful content such as JavaScript, PHP shells, and backdoors. A complete website audit needs to dumping the CMS database’s content and looking for evidence of malware.
mysqldump, phpMyAdmin, and Adminer are all tools that can be used to dump a database. Any PHP code in the database should be thoroughly examined for malware. To find PHP, look for the following symbols:
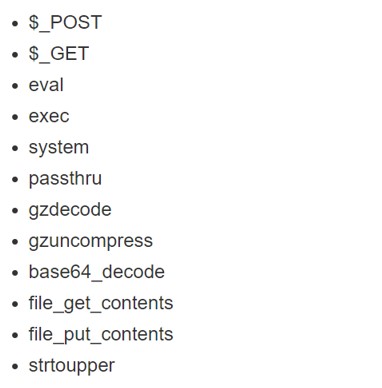
Post Cleanup and Hardening
Once your website is malware-free, take proactive measures to harden the configuration and set up periodic checks to ensure the site remains secure.
- Upgrade all Existing Software to the Latest Version
- Reset all Passwords
- Harden Your Website Using .htaccess
- Set up Daily Backups
- Enable External Security Monitoring
- Enable Internal Security Monitoring
- Use the Web Application Firewall
Conclusion
This collection of articles provides a detailed summary of all the places to find information on how to fix your website once it has been hacked. Manually eradicating malware from a website is a challenging feat. It requires a great deal of knowledge and experience.
Contact Us for Website Malware removal – [email protected]



































