Adversaries use several techniques to hide the malware on the disk. One of the most common is NTFS ADS, as this helps attackers to hide malicious files for later execution. Here we will see one of the windows disk utilities which help attackers to achieve the data hiding on the disk. Before moving on, we need to know about NTFS( New Technology File System ) and ADS ( Alternate Data Stream ) in the Windows filesystem.
What is Alternate Data Stream ( ADS )?
NTFS is the filesystem developed by Microsoft to store, retrieve, and finding files on a hard disk efficiently. NTFS ADS is the sub-property to handle the information of the file properties or attributes such as filename, date & Time, Volume name, etc. These attributes manage and store the user’s file properties which are known to be an Alternate data stream.
What is Disk Fragmentation?
Imagine that you have deleted lots of files in the past, now deleted file space in the hard disk will be empty and if you write any new file to the hard disk, this existing free space will consume parts of your new file which is known to be Fragmentation.
Example: You have deleted the 2 MB file on disk, now you have copied a new file to your system which is 5 MB. Now 2 MB will be costumed by the existing deleted space and 3 MB will be written to the end of the disk.
Also Read: Process Injection Techniques used by Malware – Detection & Analysis
What is Disk Defragmentation?
Disk Defragmentation is the process of moving and reordering the chunk files from the fragmented areas towards the original files on the end of the disk. This sequential way to improve disk performance.
Example: As per the above example, now this 2 MB (Fragmented area) will be moved to the end of the original file which will improve the disk performance.
What is Esentutl.exe?
Esentutl.exe is a command-line utility for the windows to do the disk Defragmentation. This tool can be leveraged to hide malicious data inside Alternate data streams.
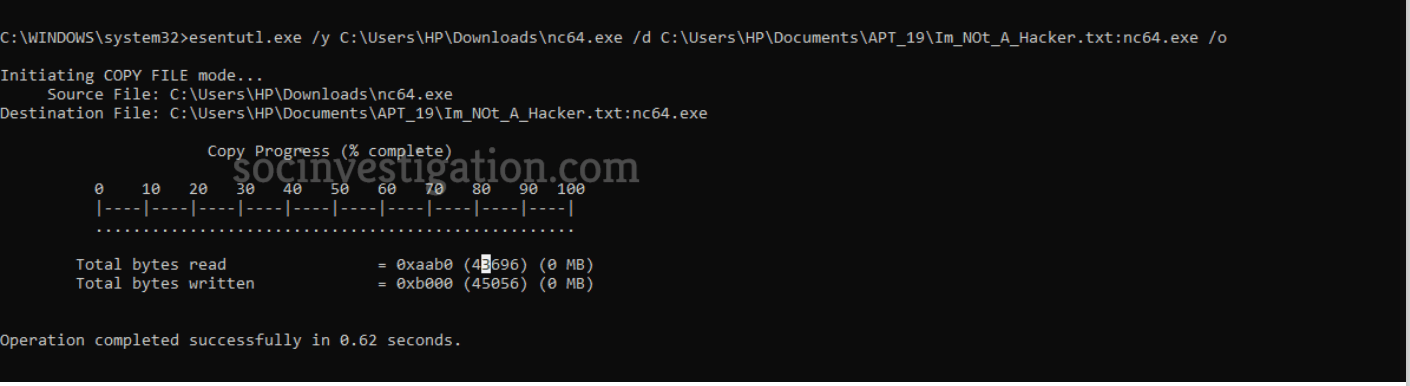
Adversaries abuse the “Esentutl.exe” utility to copy a file from the disk and hide them on NTFS ADS for later execution. Here are the options/y loads a file from the path which looks “nc64.exe” netcat software and option /d is for defragmentation location.
Also, Read Top Malware Hiding Techniques in Windows Operating System
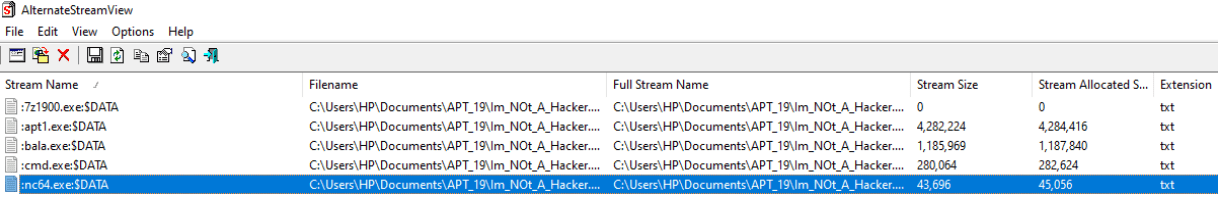
This is a free tool, which can be used to find the malicious files hiding under the data streams. We have used the “alternateStreamview” Tool to reveal the data hiding on the stream!! Hunt your EDR for such threats, Create group policies in the active directory to block such utilities that can be accessed by insiders or malicious actors!!! Happy Hunting !!