Introduction:
The various processes that are running in a Windows computer. Some of the processes are parts of the operating system, while others are applications automatically launched at startup or manually by the user or hackers. Knowing What’s normal on windows helps you to cut through the noise to quickly locate potential malware.
This blog is the reference to know what is normal in windows and to focus your attention on threat hunting. In this article, you may come to know what are the important process in windows and How legitimate processes will look alike when malware is executed.
1.Svchost.exe(service host)
Description:
The generic host process for Windows Services. It is used for running service DLLs. Windows will run multiple instances of svchost.exe, each using a unique “-k” parameter for grouping similar services. Typical “-k” parameters include BTsvcs, DcomLaunch, RPCSS, LocalServiceNetworkRestricted, netsvcs, LocalService, NetworkService, LocalServiceNoNetwork, secsvcs, and LocalServiceAndNoImpersonation.
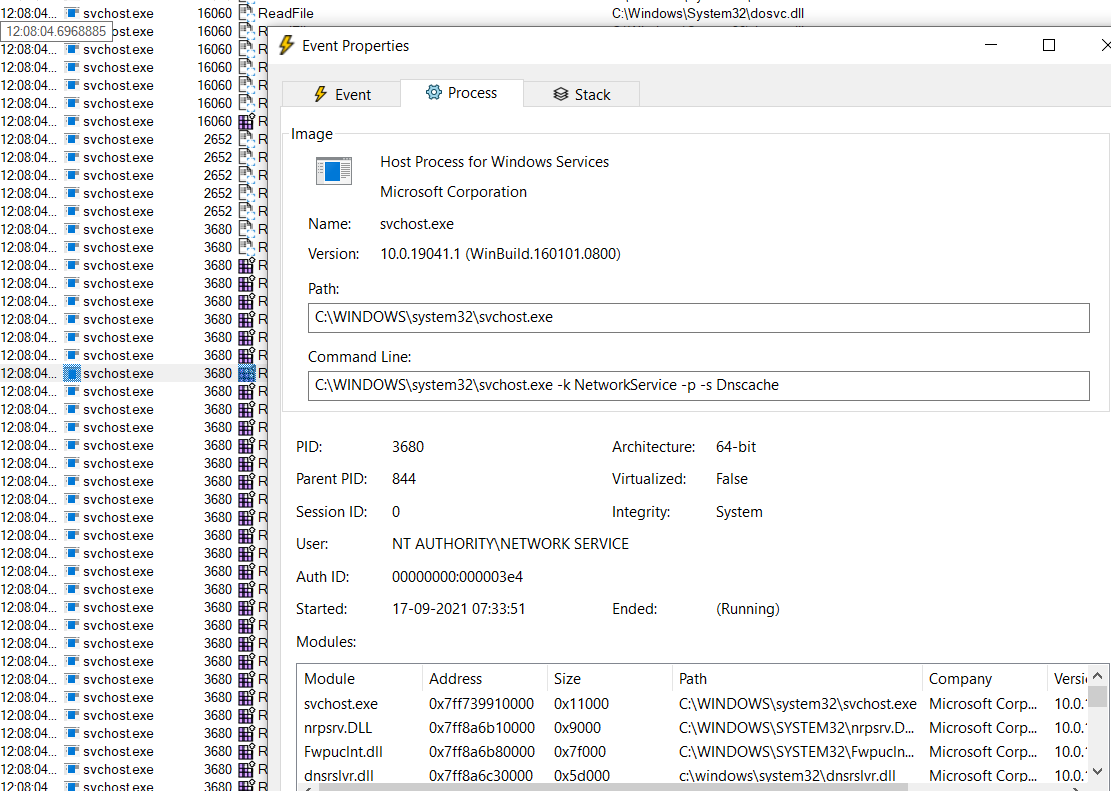
Image Path:
%SystemRoot%\System32\svchost.exe
Parent Process:
services.exe
Number of Instances:
Five or more
User Account:
Varies depending on svchost instance, though it typically will be Local System, Network Service, or Local Service accounts. Instances running under any other account should be investigated.
Legitimate svchost runs on
%SystemRoot%\System32\svchost.exe and it should be the children of services.exe
Threat Hunting Tips:
This process can be used to launch malicious services (malware installed as a service). Once the malicious service is launched, “-k” will not be present. This process hides in plain sight through misspellings of words. Another method to utilize this process for malicious purposes is to place it in different directories and paths; However, note in such a case, services.exe would not be the parent process.
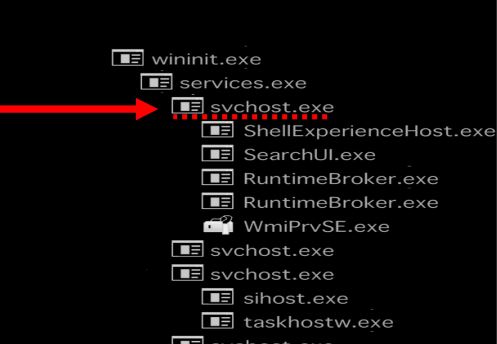
2.Services.exe
Description:
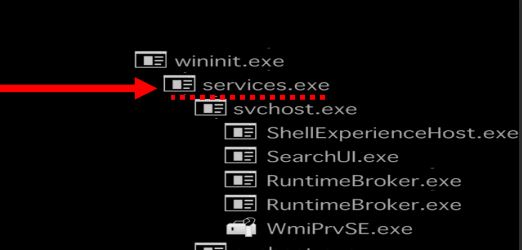
services.exe launches the Services Control Manager which is primarily responsible for handling system services including starting and ending services, and interacting with services. Services are defined in HKLM\SYSTEM\CurrentControlSet\Services. “services.exe” is the parent process of svchost.exe, dllhost.exe, taskhost.exe,spoolsv.exe, etc.
Image Path:
%SystemRoot%\System32\services.exe
Parent Process:
wininit.exe
Number of Instances:
One
User Account:
Local System
Threat hunting tips:
There must only be 1 instance of “services.exe”. This is a protected process that makes it difficult to tamper with. Also track Event ID Event ID 4697 ( security ) & Event ID 7045 (system )
Also Read: Topmost Signs of Compromise Detected with Windows operating System
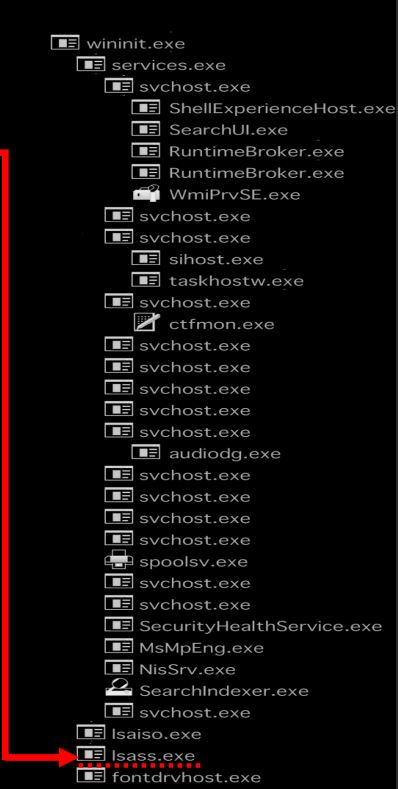
3.Lsass.exe(Local Security Authority Subsystem Service)
Description:
The Local Security Authentication Subsystem Server process is responsible for authenticating users by calling an appropriate Security Service Provider (SSP) authentication package specified in HKLM\SYSTEM\CurrentControlSet\Control\Lsa. Only one instance of this process should occur and it should never have child processes.
Image Path:
%SystemRoot%\System32\lsass.exe
Parent Process:
wininit.exe
Number of Instances:
One
User Account:
Local System
Threat hunting tips:
The lsass.exe threats are often hidden in plain sight; we recommend you check for any misspellings such as “lass.exe” or “lsasss.exe”.
Also Read: Defending and Preventing Against Active Directory Kerberos Attacks
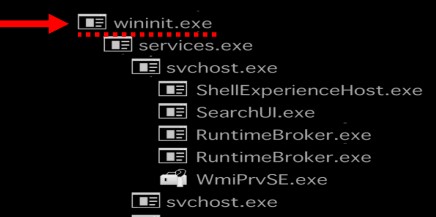
4.Wininit.exe(windows initialization)
Description:
This process is an essential part of the Windows OS and it runs in the background. “wininit.exe” is responsible for launching the Windows Initialization process. Wininit starts key background processes within Session 0. It starts with the Service Control Manager (services.exe), the Local Security Authority process (lsass.exe), and the Local Session Manager (lsm.exe).
Image Path:
%SystemRoot%\System32\wininit.exe
Parent Process:
Created by an instance of smss.exe that exits, so tools usually do not provide the parent process name.
Number of Instances:
One
User Account:
Local System
Threat hunting tips:
There must be only one instance of wininit.exe. You should check the parent process to see if it is spawning wininit.exe. You should also check whether this process is located somewhere other than its usual path. You should also check the spelling.
5.Csrss.exe(Client/Server Run-Time Subsystem)
Description:
This process is an essential subsystem that must be running at all times. It is responsible for console windows process/thread creation and thread deletion.
Image Path:
%SystemRoot%\System32\csrss.exe
Parent Process:
Created by an instance of smss.exe that exits, so analysis tools usually do not provide the parent process name.
Threat Hunting Tips:
Malware authors can disguise their malware to appear as this process by hiding in plain sight. They can change the malware name from ‘csrss.exe’ to something similar but with a misspelling; for instance, cssrss, crss, cssrs, csrsss.

Also Read : Soc Interview Questions and Answers – CYBER SECURITY ANALYST
6.Winlogon.exe ( Windows Logon Process )
Description:
Winlogon handles interactive user logons and logoffs. It launches LogonUI.exe, which accepts the username and password at the logon screen and passes the credentials to lsass.exe to validate the credentials. Once the user is authenticated, Winlogon loads the user’s NTUSER.DAT into HKEY_CURRENT_USER Registry Hive and starts the user’s shell (explorer.exe) via Userinit.exe.
Image Path:
%SystemRoot%\System32\winlogon.exe
Parent Process:
Created by an instance of smss.exe that exits, so analysis tools usually do not provide the parent process name.
Threat Hunting Tips:
The abuse within this process often comes within the different components of the login process. Malware sometimes mishandles the SHELL registry value. This value should be explorer.exe.
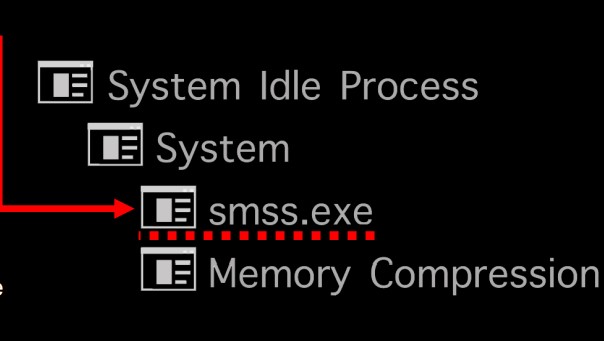
7.Smss.exe(Session Manager Subsystem)
Description:
This process manages the start of user sessions and various other activities including launching Winlogon.exe and Csrss.exe processes, setting system variables, and other activities. If the 2 processes end normally after launch, smss.exe shuts down the system and if they end unexpectedly, smss.exe causes the system to hang.
Image Path:
%SystemRoot%\System32\smss.exe
Parent Process:
System
Threat hunting tips:
“smss.exe” that starts with csrss.exe and wininit.exe or with csrss.exe and winlogon.exe, are normal. Additional sessions may be created by RDP and Fast User Switching on shared computers. Remember, only 1 instance of smss.exe must run.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
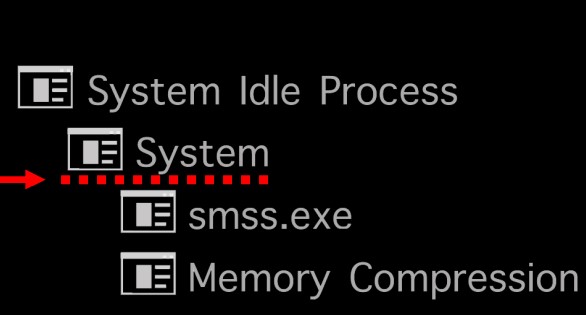
8.System.exe ( System )
The System process is a single thread running on each processor. It is also the host of all kinds of device drivers such as USB, Touchpad, Ports, Audio, Network, etc.
Image Path: N/A – Not generated from an executable image
Parent Process: None
Threat hunting tips:
Usually, the System processes malicious activities that occur in kernel-mode threads. The System process includes some DLLs as well as the kernel executable. Thus we absolutely recommend making a baseline or whitelist from these DLLs.
Also, recommend to look for any misspellings and have them run from an actual folder for executables such as ntoskrnl.exe.
Conclusion:
Stay tuned for upcoming blogs with more windows-based malware executions and detections. Happy Hunting



































