FormBook Malware is an information stealer/trojan and is available in the dark web market as a Malware-as-Service. It is first seen in July 2016 and has been quite active since then. In 2020 it affected 4% of organizations worldwide and was among the top 3 list of trending malware.
It logs and monitors keystrokes, searches and accesses files, takes screenshots, harvests credentials from different browsers, drops files, downloads, and executed stealthier malware as per commands received from Command-and-Control-Server (C2).
FormBook is mainly distributed using email campaigns, various infecting mechanisms, and different types of file attachments including pdfs, doc, RTF documents, exe, zip, rar etc.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Security researcher JAMESWT_MHT has spotted recent activities of formbook. It is spread via spam email and contains the email subject Payment Advice – Advice Ref:[GLV211429671] / ACH credits / Customer Ref:[ACHKACH120210215104455BND] , A false payment request bait for Formbook. The email ace attachment contains a malicious executable file.
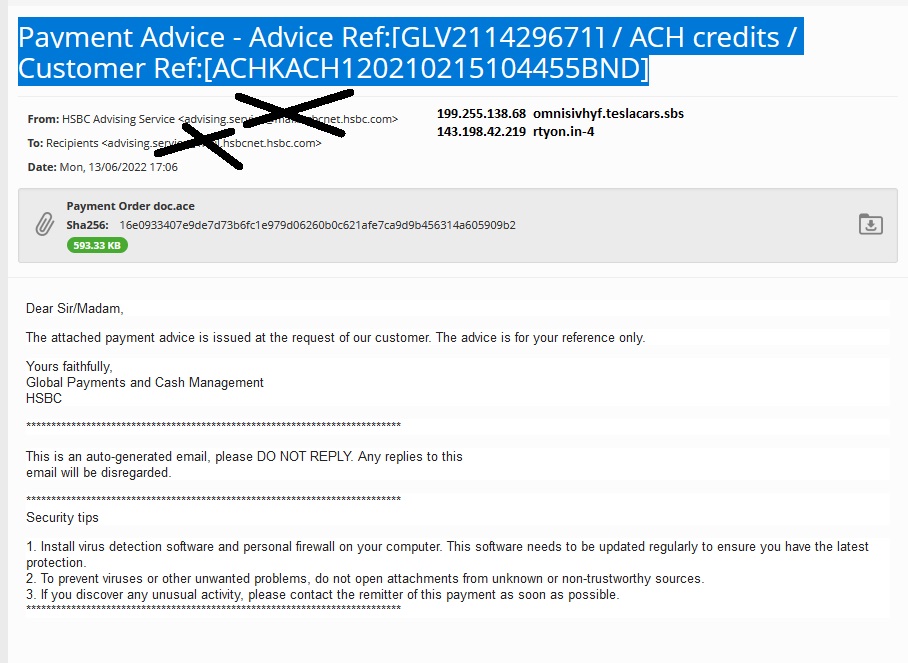
It leverages an executes system process that injects code into a set of files in the System32 folder, and later executes a command-line /c del to delete the initial infection dropper from the AppData Temp folder.
Also Read: Ngrok Threat Hunting: Detect Hackers at the End of the Tunnel
Formbook, through the keylogger function, is able to acquire everything the user types. It can also steal email and browser credentials, as well as take screenshots.
Finally, it has the ability to remotely issue commands on the infected PC, such as downloading additional payloads or updating those present.
Indicator of Compromise:
File Hash:
c2611311dcf606304c1dcff55aee197f17a3f46d12680732d97e64af99d91c9d
16e0933407e9de7d73b6fc1e979d06260b0c621afe7ca9d9b456314a605909b2
hawkonline[.]club
unitedkingdomvoip[.]site
tbrme[.]com
ysxol[.]xyz
oviagrooming[.]com
pokerdominogame[.]com
perabett463[.]com
orderjoessteaks[.]com
sjczyw[.]com
christensonbrothers[.]com
stanegroupe[.]com
residencialseniorspa[.]com
eyetechlabs[.]com
lens-experts[.]com
69988[.]club
skateboardlovers[.]com
ourhighlandacres[.]net
dskensho343[.]xyz
dance985[.]com
iran-style[.]com
autism-101[.]com
hdwiz[.]online
atomcapital[.]net
seelenmedicus144[.]com
range4tis[.]com
affordablebathroomsbyfrank[.]net
sosienna[.]com
forge21[.]xyz
sinergiberkaryabersama[.]com
christinesyquia[.]com
newleafremodel[.]com
doitlive[.]online
hyiptron[.]com
hobartiamusic[.]com
dvfdressoutlet[.]com
puzzlelux[.]com
arkdia[.]xyz
turnerverve[.]quest
detectorlifestyle[.]com
milanoineout[.]com
zjins[.]com
globalfrances[.]com
cactus-aio[.]com
fzl-fs[.]com
freshiestuning[.]com
vertiney[.]com
mayclaim[.]com
8m1id[.]online
fiercefantasyshop[.]com
genesisrofprc[.]xyz
eventsp[.]xyz
morningvibecoffee[.]com
angellogordon[.]com
peopleonhealth[.]com
batuhanasut[.]com
fabianmarin[.]com
5starrentertainment[.]com
tauikrychy[.]space
magnetstudios[.]global
korenshop[.]com
mbljbspro[.]com
takeyourshot3500[.]pro
sjsteinhardt[.]com
cabanatvs[.]com
jenaeeaginshair[.]com
Also Read: Process Injection Techniques used by Malware – Detection & Analysis
Detection & Response:
Splunk:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentCommandLine" ilike 'C:\Windows\System32\%' or "ParentCommandLine" ilike 'C:\Windows\SysWOW64\%') and "ParentCommandLine" ilike '%.exe' and "Process CommandLine" ilike '%/c%' and "Process CommandLine" ilike '%del%' and "Process CommandLine" ilike '%C:\Users\%' and "Process CommandLine" ilike '%\AppData\Local\Temp\%' and ("Process CommandLine" ilike '%.exe' or "Process CommandLine" ilike '%.ace')Elastic Query:
(process.parent.command_line:(C\:\\Windows\\System32\\* OR C\:\\Windows\\SysWOW64\\*) AND process.parent.command_line:*.exe AND process.command_line:*\/c* AND process.command_line:*del* AND process.command_line:*C\:\\Users\\* AND process.command_line:*\\AppData\\Local\\Temp\\* AND (process.command_line:*.exe OR process.command_line:*.ace))Qradar:SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentCommandLine" ilike 'C:\Windows\System32\%' or "ParentCommandLine" ilike 'C:\Windows\SysWOW64\%') and "ParentCommandLine" ilike '%.exe' and "Process CommandLine" ilike '%/c%' and "Process CommandLine" ilike '%del%' and "Process CommandLine" ilike '%C:\Users\%' and "Process CommandLine" ilike '%\AppData\Local\Temp\%' and ("Process CommandLine" ilike '%.exe' or "Process CommandLine" ilike '%.ace')Aws OpenSearch:(process.parent.command_line:(C\:\\Windows\\System32\\* OR C\:\\Windows\\SysWOW64\\*) AND process.parent.command_line:*.exe AND process.command_line:*\/c* AND process.command_line:*del* AND process.command_line:*C\:\\Users\\* AND process.command_line:*\\AppData\\Local\\Temp\\* AND (process.command_line:*.exe OR process.command_line:*.ace))FireEye:(metaclass:`windows` rawmsg:[`C:\Windows\System32\\`,`C:\Windows\SysWOW64\\`] rawmsg:`.exe` args:`/c` args:`del` args:`C:\Users\\` args:`\AppData\Local\Temp\\` (args:`*.exe` OR args:`*.ace`))GrayLog:(ParentCommandLine.keyword:(C\:\\Windows\\System32\\* C\:\\Windows\\SysWOW64\\*) AND ParentCommandLine.keyword:*.exe AND CommandLine.keyword:*\/c* AND CommandLine.keyword:*del* AND CommandLine.keyword:*C\:\\Users\\* AND CommandLine.keyword:*\\AppData\\Local\\Temp\\* AND (CommandLine.keyword:*.exe OR CommandLine.keyword:*.ace))LogPoint:(ParentCommandLine IN ["C:\\Windows\\System32\\*", "C:\\Windows\\SysWOW64\\*"] ParentCommandLine="*.exe" CommandLine="*/c*" CommandLine="*del*" CommandLine="*C:\\Users\\*" CommandLine="*\\AppData\\Local\\Temp\\*" (CommandLine="*.exe" OR CommandLine="*.ace"))Microsoft Sentinel:SecurityEvent | where EventID == 1 | where ((ParentCommandLine startswith @'C:\Windows\System32\' or ParentCommandLine startswith @'C:\Windows\SysWOW64\') and ParentCommandLine endswith '.exe' and CommandLine contains '/c' and CommandLine contains 'del' and CommandLine contains @'C:\Users\' and CommandLine contains @'\AppData\Local\Temp\' and (CommandLine endswith '.exe' or CommandLine endswith '.ace'))RSA Netwitness:((ParentCommandLine contains 'C:\\Windows\\System32\\\', 'C:\\Windows\\SysWOW64\\\') && (ParentCommandLine contains '.exe') && (CommandLine contains '/c') && (CommandLine contains 'del') && (CommandLine contains 'C:\Users\\') && (CommandLine contains 'AppData\Local\Temp\\') && ((CommandLine contains '.exe') || (CommandLine contains '.ace')))Sumo Logic:(_sourceCategory=*windows* AND (ParentCommandLine = "C:\Windows\System32\\*" OR ParentCommandLine = "C:\Windows\SysWOW64\\*") AND ParentCommandLine="*.exe" AND CommandLine="*/c*" AND CommandLine="*del*" AND CommandLine="*C:\Users\\*" AND CommandLine="*\AppData\Local\Temp\\*" AND ((CommandLine="*.exe" OR CommandLine="*.ace")))Microsoft Defender:DeviceProcessEvents | where ((InitiatingProcessCommandLine startswith @"C:\Windows\System32\" or InitiatingProcessCommandLine startswith @"C:\Windows\SysWOW64\") and InitiatingProcessCommandLine endswith ".exe" and ProcessCommandLine contains "/c" and ProcessCommandLine contains "del" and ProcessCommandLine contains @"C:\Users\" and ProcessCommandLine contains @"\AppData\Local\Temp\" and (ProcessCommandLine endswith ".exe" or ProcessCommandLine endswith ".ace"))Powershell:Get-WinEvent | where {(($_.message -match "ParentCommandLine.*C:\\Windows\\System32\\.*" -or $_.message -match "ParentCommandLine.*C:\\Windows\\SysWOW64\\.*") -and $_.message -match "ParentCommandLine.*.*.exe" -and $_.message -match "CommandLine.*.*/c.*" -and $_.message -match "CommandLine.*.*del.*" -and $_.message -match "CommandLine.*.*C:\\Users\\.*" -and $_.message -match "CommandLine.*.*\\AppData\\Local\\Temp\\.*" -and ($_.message -match "CommandLine.*.*.exe" -or $_.message -match "CommandLine.*.*.ace")) } | select TimeCreated,Id,RecordId,ProcessId,MachineName,MessageSource/Credits: ht://twitter.com/JAMESWT_MHT



































