Matanbuchus Loader is advertised as a new malware-as-a-service (MaaS). Malware loaders are malicious software that typically drops. Second-stage malware from command and control (C2) infrastructures can be observed.
last year February 2021 this loader’s ability to launch a .exe or .dll file in memory and leverage schtasks.exe to add or modify task schedules. Also, launch custom PowerShell commands and standalone executable to load the DLL.
Threat researchers (pr0xylife & executemalware ) have discovered new malware loaders that have been discovered in phishing attacks, featuring HTML smuggling and signed binaries embedded into the malicious zip file.
‘HTML smuggling’, which spreads malware via email, is increasingly targeting banking organizations, Microsoft has claimed.
If the target opens the HTML in their web browser, the malicious script is decoded and the payload is deployed on their device.
Malware Flow:
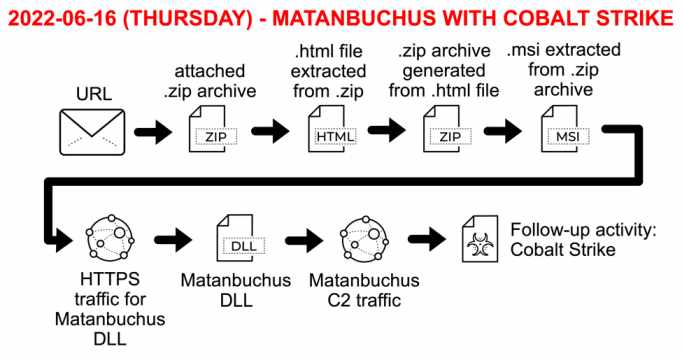
At the initial level of infection malware leveragers well-known Microsoft system binaries such as regsvr32.exe, and msiexec.exe for the malware deployment and executions.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
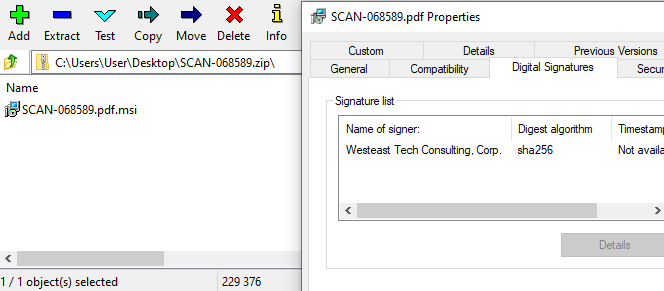
The above figure shows the Malware binary is signed with Westeast Tech Consulting, Corp.
Traffic From an Infected Windows Host
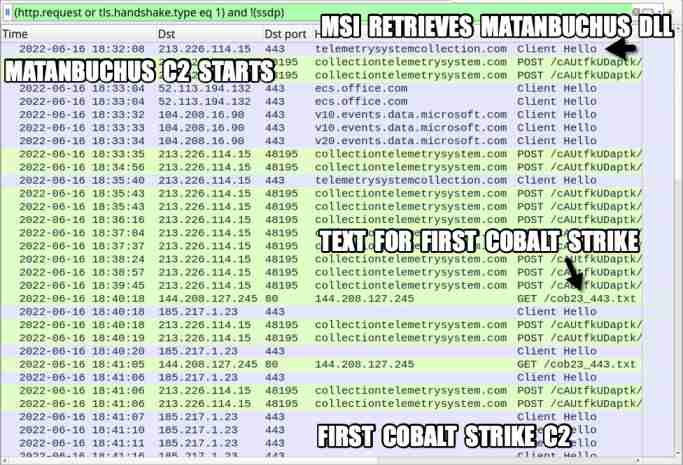
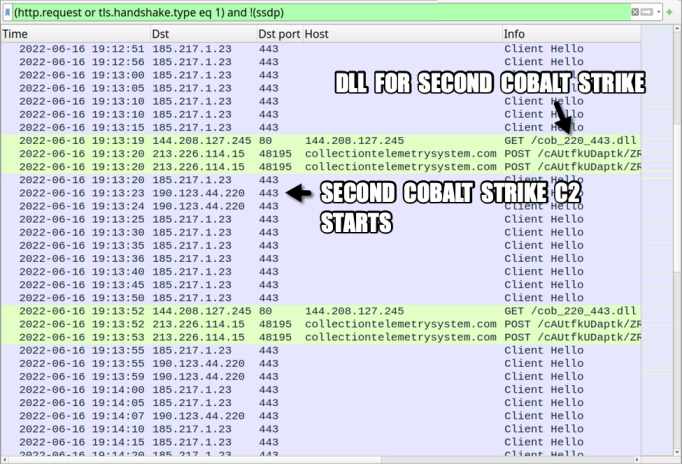
Network traffic shows malware DLL connects with COBALT STRIKE C2 and later the same approach is followed for the second C2 server.
Also Read: Windows Event ID 5379 to Detect Malicious Password-Protected File unlock
Indicator of Compromise:
File names:
SHA256 cc08642ddbbb8f735a3263180164cda6cf3b73a490fc742d5c3e31130504e97c
SHA256 2d8740ea16e9457a358ebea73ad377ff75f7aa9bdf748f0d801f5a261977eda4
Similar IOCs check here.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Detection & Response:
Splunk:
(((Image="*\\msedge.exe" OR Image="*\\chrome.exe") AND CommandLine="*C:\\Users\\*" AND CommandLine="*.html*") OR (Image="*\\msiexec.exe" AND CommandLine="*\\AppData\\Local\\*" AND CommandLine="*Temp\\*" AND CommandLine="* /i*" AND CommandLine="*.pdf.msi*") OR (Image="*\\regsvr32.exe" AND (CommandLine="*/i:*" OR CommandLine="*Install*" OR CommandLine="*\\AppData\\Local\\*") AND CommandLine="*main.dll")) AND source=WinEventLog:* | table CommandLine,ParentCommandLineQradar:SELECT UTF8(payload), "Process CommandLine", "ParentCommandLine" from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ((("Image" ilike '%\msedge.exe' or "Image" ilike '%\chrome.exe') and "Process CommandLine" ilike '%C:\Users\%' and "Process CommandLine" ilike '%.html%') or ("Image" ilike '%\msiexec.exe' and "Process CommandLine" ilike '%\AppData\Local\%' and "Process CommandLine" ilike '%Temp\%' and "Process CommandLine" ilike '% /i%' and "Process CommandLine" ilike '%.pdf.msi%') or ("Image" ilike '%\regsvr32.exe' and ("Process CommandLine" ilike '%/i:%' or "Process CommandLine" ilike '%Install%' or "Process CommandLine" ilike '%\AppData\Local\%') and "Process CommandLine" ilike '%main.dll'))Elastic Query:((process.executable:(*\\msedge.exe OR *\\chrome.exe) AND process.command_line:*C\:\\Users\\* AND process.command_line:*.html*) OR (process.executable:*\\msiexec.exe AND process.command_line:*\\AppData\\Local\\* AND process.command_line:*Temp\\* AND process.command_line:*\ \/i* AND process.command_line:*.pdf.msi*) OR (process.executable:*\\regsvr32.exe AND process.command_line:(*\/i\:* OR *Install* OR *\\AppData\\Local\\*) AND process.command_line:*main.dll))ArcSight:(((((deviceProcessName CONTAINS "*\\msedge.exe" OR deviceProcessName CONTAINS "*\\chrome.exe" OR destinationProcessName CONTAINS "*\\msedge.exe" OR destinationProcessName CONTAINS "*\\chrome.exe" OR sourceProcessName CONTAINS "*\\msedge.exe" OR sourceProcessName CONTAINS "*\\chrome.exe")) AND (((deviceCustomString1 CONTAINS "*C:\\Users\\\\*" OR destinationServiceName CONTAINS "*C:\\Users\\\\*")) AND ((deviceCustomString1 CONTAINS "*.html*" OR destinationServiceName CONTAINS "*.html*")))) OR (((deviceProcessName CONTAINS "*\\msiexec.exe" OR destinationProcessName CONTAINS "*\\msiexec.exe" OR sourceProcessName CONTAINS "*\\msiexec.exe")) AND (((deviceCustomString1 CONTAINS "*\\AppData\\Local\\\\*" OR destinationServiceName CONTAINS "*\\AppData\\Local\\\\*")) AND ((deviceCustomString1 CONTAINS "*Temp\\\\*" OR destinationServiceName CONTAINS "*Temp\\\\*")) AND ((deviceCustomString1 CONTAINS "* /i*" OR destinationServiceName CONTAINS "* /i*")) AND ((deviceCustomString1 CONTAINS "*.pdf.msi*" OR destinationServiceName CONTAINS "*.pdf.msi*")))) OR (((deviceProcessName CONTAINS "*\\regsvr32.exe" OR destinationProcessName CONTAINS "*\\regsvr32.exe" OR sourceProcessName CONTAINS "*\\regsvr32.exe")) AND ((deviceCustomString1 CONTAINS "*/i:*" OR deviceCustomString1 CONTAINS "*Install*" OR deviceCustomString1 CONTAINS "*\\AppData\\Local\\\\*" OR destinationServiceName CONTAINS "*/i:*" OR destinationServiceName CONTAINS "*Install*" OR destinationServiceName CONTAINS "*\\AppData\\Local\\\\*")) AND ((deviceCustomString1 CONTAINS "*main.dll" OR destinationServiceName CONTAINS "*main.dll")))))CarbonBlack:((process_name:(*\\msedge.exe OR *\\chrome.exe) AND process_cmdline:*C\:\\Users\\* AND process_cmdline:*.html*) OR (process_name:*\\msiexec.exe AND process_cmdline:*\\AppData\\Local\\* AND process_cmdline:*Temp\\* AND process_cmdline:*\ \/i* AND process_cmdline:*.pdf.msi*) OR (process_name:*\\regsvr32.exe AND process_cmdline:(*\/i\:* OR *Install* OR *\\AppData\\Local\\*) AND process_cmdline:*main.dll))Crowdstike:(((ImageFileName="*\\msedge.exe" OR ImageFileName="*\\chrome.exe") AND (CommandHistory="*C:\\Users\\*" OR CommandLine="*C:\\Users\\*") AND (CommandHistory="*.html*" OR CommandLine="*.html*")) OR (ImageFileName="*\\msiexec.exe" AND (CommandHistory="*\\AppData\\Local\\*" OR CommandLine="*\\AppData\\Local\\*") AND (CommandHistory="*Temp\\*" OR CommandLine="*Temp\\*") AND (CommandHistory="* /i*" OR CommandLine="* /i*") AND (CommandHistory="*.pdf.msi*" OR CommandLine="*.pdf.msi*")) OR (ImageFileName="*\\regsvr32.exe" AND ((CommandHistory="*/i:*" OR CommandHistory="*Install*" OR CommandHistory="*\\AppData\\Local\\*") OR (CommandLine="*/i:*" OR CommandLine="*Install*" OR CommandLine="*\\AppData\\Local\\*")) AND (CommandHistory="*main.dll" OR CommandLine="*main.dll"))) | table CommandHistory,CommandLineFireEye:(metaclass:`windows` ((process:[`*\msedge.exe`,`*\chrome.exe`] args:`C:\Users\\` args:`.html`) OR (process:`*\msiexec.exe` args:`\AppData\Local\\` args:`Temp\\` args:` /i` args:`.pdf.msi`) OR (process:`*\regsvr32.exe` args:[`/i:`,`Install`,`\AppData\Local\\`] args:`*main.dll`)))Google Chronicle:(((target.process.file.full_path = /.*\\msedge\.exe/ or target.process.file.full_path = /.*\\chrome\.exe/) and target.process.command_line = /.*C:\\Users.*/ and target.process.command_line = /.*\.html.*/) or (target.process.file.full_path = /.*\\msiexec\.exe/ and target.process.command_line = /.*\\AppData\\Local.*/ and target.process.command_line = /.*Temp.*/ and target.process.command_line = /.* \/i.*/ and target.process.command_line = /.*\.pdf\.msi.*/) or (target.process.file.full_path = /.*\\regsvr32\.exe/ and (target.process.command_line = /.*\/i:.*/ or target.process.command_line = /.*Install.*/ or target.process.command_line = /.*\\AppData\\Local.*/) and target.process.command_line = /.*main\.dll/))GrayLog:((Image.keyword:(*\\msedge.exe *\\chrome.exe) AND CommandLine.keyword:*C\:\\Users\\* AND CommandLine.keyword:*.html*) OR (Image.keyword:*\\msiexec.exe AND CommandLine.keyword:*\\AppData\\Local\\* AND CommandLine.keyword:*Temp\\* AND CommandLine.keyword:*\ \/i* AND CommandLine.keyword:*.pdf.msi*) OR (Image.keyword:*\\regsvr32.exe AND CommandLine.keyword:(*\/i\:* *Install* *\\AppData\\Local\\*) AND CommandLine.keyword:*main.dll))LogPoint:((Image IN ["*\\msedge.exe", "*\\chrome.exe"] CommandLine="*C:\\Users\\*" CommandLine="*.html*") OR (Image="*\\msiexec.exe" CommandLine="*\\AppData\\Local\\*" CommandLine="*Temp\\*" CommandLine="* /i*" CommandLine="*.pdf.msi*") OR (Image="*\\regsvr32.exe" CommandLine IN ["*/i:*", "*Install*", "*\\AppData\\Local\\*"] CommandLine="*main.dll"))Microsoft Defender:DeviceProcessEvents | where (((FolderPath endswith @"\msedge.exe" or FolderPath endswith @"\chrome.exe") and ProcessCommandLine contains @"C:\Users\" and ProcessCommandLine contains ".html") or (FolderPath endswith @"\msiexec.exe" and ProcessCommandLine contains @"\AppData\Local\" and ProcessCommandLine contains @"Temp\" and ProcessCommandLine contains " /i" and ProcessCommandLine contains ".pdf.msi") or (FolderPath endswith @"\regsvr32.exe" and (ProcessCommandLine contains "/i:" or ProcessCommandLine contains "Install" or ProcessCommandLine contains @"\AppData\Local\") and ProcessCommandLine endswith "main.dll"))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where (((NewProcessName endswith @'\msedge.exe' or NewProcessName endswith @'\chrome.exe') and CommandLine contains @'C:\Users\' and CommandLine contains '.html') or (NewProcessName endswith @'\msiexec.exe' and CommandLine contains @'\AppData\Local\' and CommandLine contains @'Temp\' and CommandLine contains ' /i' and CommandLine contains '.pdf.msi') or (NewProcessName endswith @'\regsvr32.exe' and (CommandLine contains '/i:' or CommandLine contains 'Install' or CommandLine contains @'\AppData\Local\') and CommandLine endswith 'main.dll'))RSA Netwitness:(((Image contains '\msedge\.exe', '\chrome\.exe') && (CommandLine contains 'C:\Users\\') && (CommandLine contains '.html')) || ((Image contains 'msiexec.exe') && (CommandLine contains 'AppData\Local\\') && (CommandLine contains 'Temp\\') && (CommandLine contains ' /i') && (CommandLine contains '.pdf.msi')) || ((Image contains 'regsvr32.exe') && (CommandLine contains '/i:', 'Install', '\AppData\\Local\\\') && (CommandLine contains 'main.dll')))SumoLogic:(_sourceCategory=*windows* AND ((((Image = "*\msedge.exe" OR Image = "*\chrome.exe") AND CommandLine="*C:\Users\\*" AND CommandLine="*.html*") OR (Image="*\msiexec.exe" AND CommandLine="*\AppData\Local\\*" AND CommandLine="*Temp\\*" AND CommandLine="* /i*" AND CommandLine="*.pdf.msi*") OR (Image="*\regsvr32.exe" AND (CommandLine = "*/i:*" OR CommandLine = "*Install*" OR CommandLine = "*\AppData\Local\\*") AND CommandLine="*main.dll"))))Aws Opensearch:((process.executable:(*\\msedge.exe OR *\\chrome.exe) AND process.command_line:*C\:\\Users\\* AND process.command_line:*.html*) OR (process.executable:*\\msiexec.exe AND process.command_line:*\\AppData\\Local\\* AND process.command_line:*Temp\\* AND process.command_line:*\ \/i* AND process.command_line:*.pdf.msi*) OR (process.executable:*\\regsvr32.exe AND process.command_line:(*\/i\:* OR *Install* OR *\\AppData\\Local\\*) AND process.command_line:*main.dll))Source/Reference: hts://isc.sans.edu/forums/diary/Malspam+pushes+Matanbuchus+malware+leads+to+Cobalt+Strike/28752/ htts://cyware.com/news/matanbuchus-loader-a-new-malware-as-a-service-50c4e16f



































