It is essential to earn money in the chance to enjoy a lavish lifestyle. But it is extremely important how we earn it. Nowadays, attackers are targeting most individuals and organizations to profit from a hard weapon – ransomware. Every year, the number and severity of ransomware attacks expand. Ransomware is a type of malware that encrypts your files and demands a ransom payment in exchange for restoring access to your data.
In this article, we’ll lay out how attackers perform a ransomware attack. As a blue team, we must learn how an offense is carried out. Let’s look at Ransomware offensive side.
Image Source Credits: Will
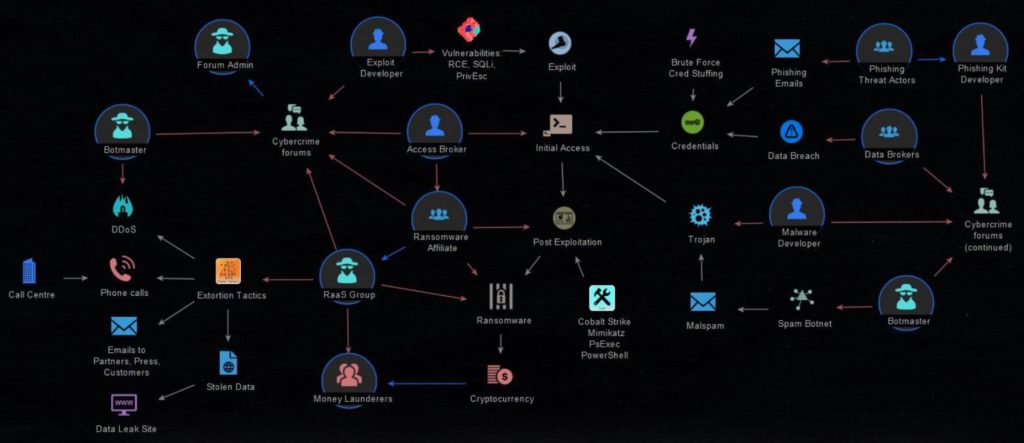
Ransomware Techniques & Tactics:
- Initial access
- Post Exploitation
- Ransomware Affiliate
- RaaS Group
- Extortion Tactics
Cybercrime Forums:
Before going inside deeper, these are all the forums where all the ideas will be exchanged to perform the attack. We will involve all these forums inside each stage.
- Forum Admin – The forum administrator oversees the technical aspects of the site’s operation. As such, they can promote or demote members, manage the rules, create sections and sub-sections, and perform database operations.
- Exploit Developer – The exploit developer interacts with the application in the same way that a user would, entering malformed and malicious inputs in an attempt to find exploitable vulnerabilities.
- Access Broker – Access brokers compromise networks and sell credentials to other threat actors, such as ransomware operators, who steal data and extort money from victims.
- Ransomware Affiliate – For the affiliate model to work with ransomware developers, the developers generate specific code within the ransomware to their affiliates, with a unique identifier embedded within it. This causes the ransom payout to get directed to the affiliate that infected the victim.
- RaaS Group – Ransomware as a Service (RaaS) is a business model used by ransomware developers, in which they lease ransomware variants in the same way that legitimate software developers lease SaaS products. RaaS gives everyone, even people without much technical knowledge, the ability to launch ransomware attacks just by signing up for a service.
- Money Launderers – Money laundering is essential for criminal organizations that wish to use illegally obtained money effectively.
- Botmaster – A botmaster is a person who operates the command and control of botnets for remote process execution. The botnets are typically installed on compromised machines via various forms of remote code installation.
- Malware Developer – Malware developers create malware for the purpose of making money, reselling information, playing with a company’s systems or networks, or simply proving that it can be done.
- Data Brokers – An information broker, also known as a data broker, is an individual or company that specializes in collecting personal data or data about companies, mostly from public records but sometimes sourced privately, and selling or licensing such information to third parties for a variety of uses.
Also Read: Anatomy Of An Advanced Persistent Threat Group
- Phishing Kit Developer – A phishing kit is a set of software tools, such as HTML, pictures, and code that fraudsters can use to construct and launch phishing attacks. Phishing kits allow anyone with little or no phishing experience to quickly build hundreds or thousands of phishing sites and attack a wider audience. The one who develops a phishing kit is called the Phishing Kit Developer.
- Phishing Threat Actors – Threat actors use phishing to trick people into handing over sensitive information such as passwords and health data. This method typically leverages email to trick users into giving up credentials or downloading software intended to damage or control a device or network.
Let’s get into the techniques involved in a ransomware attack.
1-Initial Access:
Attackers will first gain initial access by using either of the below options:
A-Exploit:
Exploit developers will create new exploits or try to exploit already existing vulnerabilities. Mostly they will use the below techniques:
1-RCE – Remote code execution vulnerability allows an attacker to gain access to a victim’s machine and make changes, irrespective of where the machine is geographically located. This vulnerability can lead to a full compromise of the infected machine. RCE vulnerabilities can provide an attacker with the ability to execute malicious code and take complete control of an infected system with the privileges of the victim running the application.
2-SQLi – SQL Injection (SQLi) is a type of injection attack that makes it possible to execute malicious SQL statements. These statements control a database server behind a web application.
3-PrivEsc – For hackers, privilege escalation is the art of elevating privileges from initial access (typically, standard User or application account) to Administrator, root, or even full system access, on Windows referred to as NT Authority\System.
B-Trojan:
1-Malware Developer:
Malware developers will inject malware or Trojan to the targeted machine in the boot folder which will be executed every time when the machine boots up.
2-Botmaster:
- Spam Botnet – Spam botnets will send large amounts of spam emails to fetch details like valid email addresses, personal details, etc., and to further send phishing emails.
- Malspam – Malspam is a type of spam email that contains a virus. Such emails contain infected attachments, phishing messages, or harmful URLs to fool consumers. It can be used to spread ransomware, trojans, bots, information thieves, crypto miners, spyware, and keyloggers, among other types of malware.
- DDoS – Bots will continuously send abnormal packets to the targeted machine to make it down to enter into the system. A DDoS attack uses multiple servers and Internet connections to flood the targeted resource. A DDoS attack is one of the most powerful weapons on the cyber platform.
C-Credentials:
Attackers will gather user details and credentials by following methods:
- Phishing Threat Actors: They will send phishing emails with malicious URLs to fetch usernames/email IDs and credentials.
- Data Breach: Once attackers have breached the organizations, they will collect more data and will send it to Data Brokers. After that ransom groups will make a deal with data brokers and buy those data for money.
- Brute Force Credential Stuffing: Credential stuffing is a cyber attack in which credentials obtained from a data breach on one service are used to attempt to log in to another unrelated service.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
2-Post Exploitation:
Once initial access has been gained, attackers will try to hold on to the system to maintain a footpath. Some of the Post-Exploitation tools are:
- 1-Cobalt Strike – Cobalt Strike is a collection of threat emulation tools provided by HelpSystems to work in conjunction with the Metasploit Framework. Cobalt Strike, and other penetration testing tools, were originally created for network defenders to train them to understand vulnerabilities and possible avenues of infection by cybercriminals.
- 2-Mimikatz – Mimikatz is a leading post-exploitation tool that dumps passwords from memory, as well as hashes, PINs, and Kerberos tickets. Other useful attacks it enables are pass-the-hash, pass-the-ticket, or building Golden Kerberos tickets. This makes post-exploitation lateral movement within a network easy for attackers.
- 3-PsExec – PsExec is a portable tool developed by Microsoft, which allows you to run processes at a distance using other users’ credentials. It is a bit like a remote access program. Differently, PsExec controls the computer via command lines rather than a mouse. The PsExec tool can manage processes on a distant computer. It also redirects an application’s console output to your local computer, making it show as if the process running locally.
- 4-PowerShell – Cyber criminals are launching attacks on healthcare firms and other enterprises with ransomware created using Microsoft’sPowerShell scripting language for the system.
3-Ransomware Affiliate:
- Ransomware developers generate specific code within the ransomware to their affiliates, with a unique identifier embedded within it. This causes the ransom payout to get directed to the affiliate that infected the victim.
- Once a Ransomware attack is performed, they used to demand ransom in form of Cryptocurrency
- Money Launderers will collect that cryptocurrency and will give it to RaaS Group
4-RaaS Group:
- RaaS Group depends on Money Launderers to get the currency and Ransom affiliate.
- RaaS group will get in contact with Cybercrime forums where all the ideas will be exchanged to perform the next set of attacks.
5-Extortion Tactics:
Modern ransomware actors identify and target valuable data, often exfiltrating it from a victim’s network organization rather than simply encrypting it. This gives them another avenue for extortion: if a victim does not pay the ransom, the attacker can threaten to publicize the private data. For enterprises holding intellectual property data, proprietary information, private employee data, and customer data, this is a serious concern. Any data leak will come with regulatory penalties, lawsuits, and reputational damage. Some of the extortion is:
- Phone calls — from call center
- Emails to partners, press, customers
- Stolen data — > Data Leak Site
Conclusion:
IT leaders understand that ransomware is preventable—and they know how to protect against it. But still, increasingly many businesses are finding their computers locked, their files encrypted, or their customers’ personal data stolen. To make the organization healthy, we advise having SIEM rules, EDR rules, and similar measures in place.



































