Source/Credits/Written By: Jamie St. Patrick
This article is my first post on the PowerShell Empire Framework. In this, I will cover the basics of Empire, and eventually, I will provide a deep-dive technical analysis on advanced exploits. Empire is an open-source, cross-platform remote administration and post-exploitation framework that is publicly available on GitHub. It is one of the widely used hacking tools for penetration testers and criminals.
General Description:
Empire can be used to elevate privileges from a standard user account to an administrator, find out what hosts and services are present, move between hosts,s and gather credentials. All of these are vital components of a modern-day hack.PowerShell Empire is accomplished through three main components: the process (listener) that listens for a connection from the machine you are attacking, a snippet of code (stager) that allows your malicious code to be run via the agent on the compromised host, and finally a program (agent) that maintains a connection between your computer and the compromised host.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Execution Process:
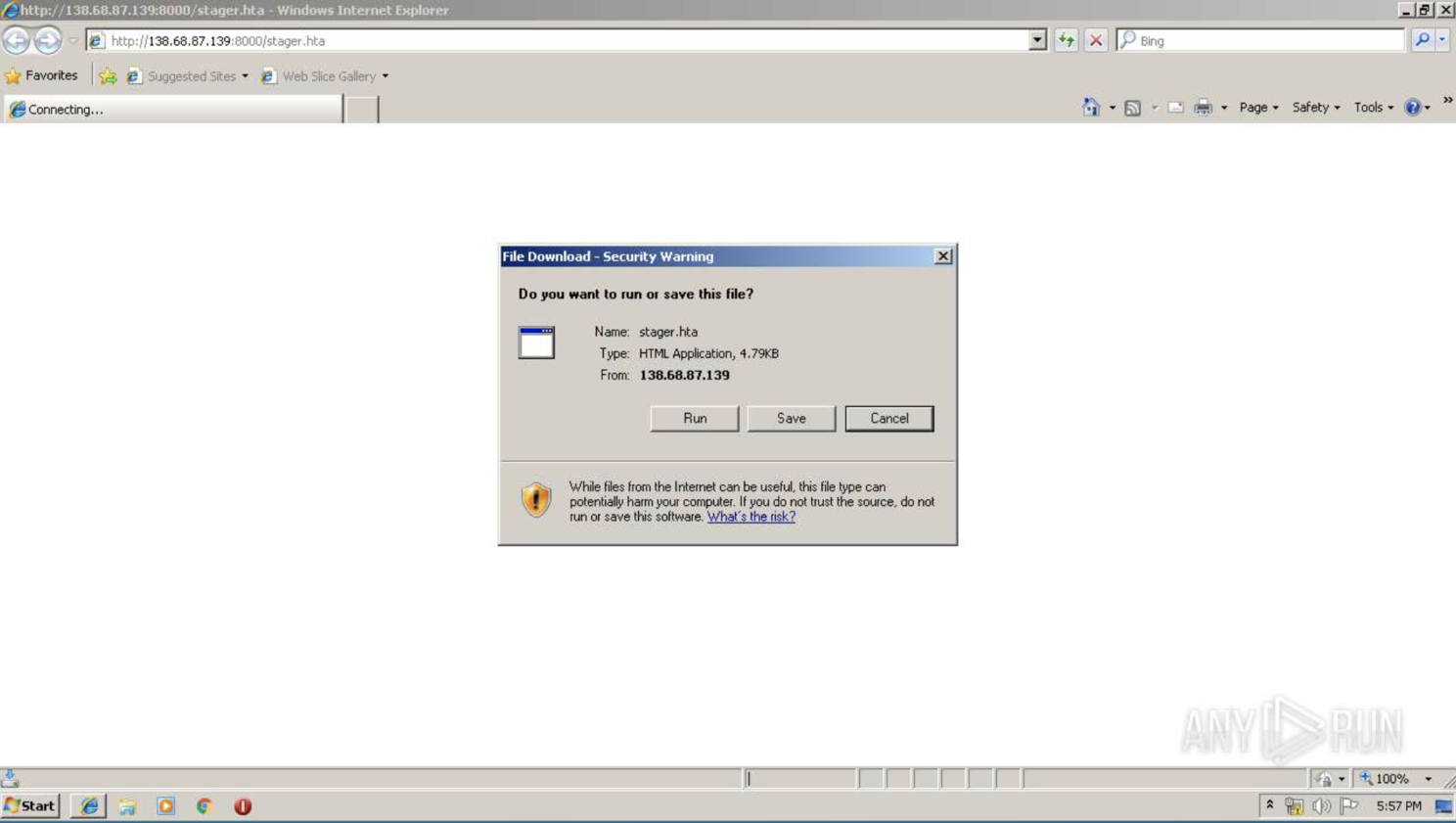
The execution process is quite straightforward. Once an attacker has gained access to a compromised device, their system becomes their playground, and tools like Empire become their toy box. When the stager URL is executed on the web browser of a compromised device, it runs the mshta.exe. The mshta.exe executes the empire PowerShell script and runs modules (malicious commands) to maintain connection between the attacker and the compromised host.
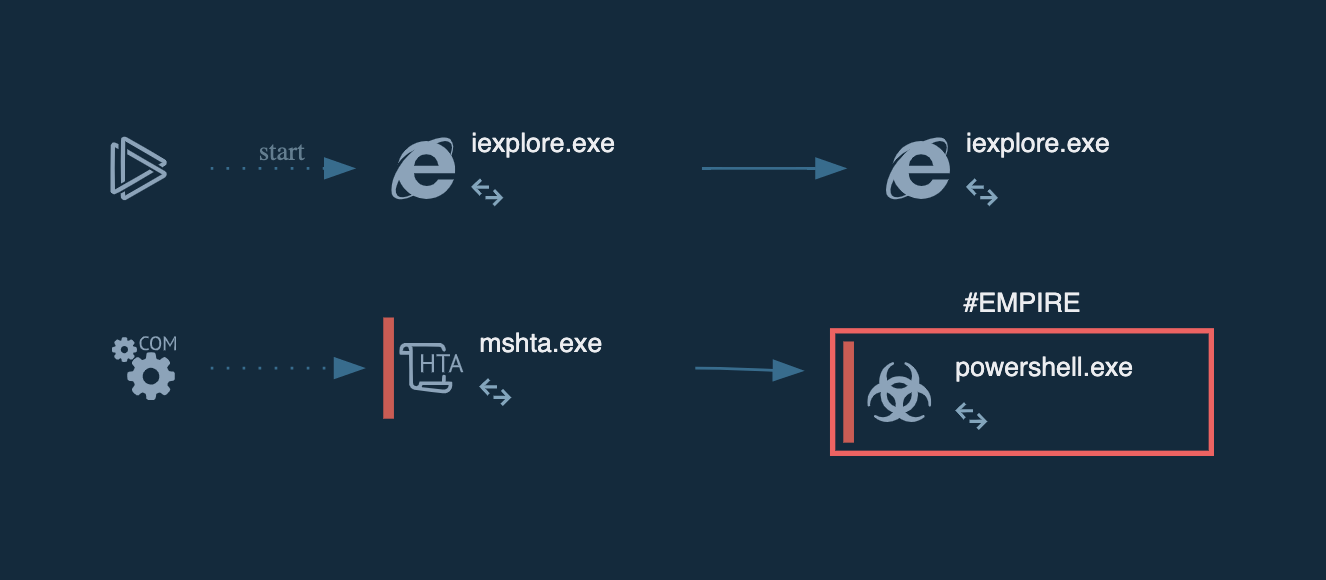
The mshta.exe is a native binary executable on windows that loads HTA files. When an HTA file is accessed on the Web, it typically produces a dialog box that enables an attacker to run scripts on the compromised machine.
Detection:
An early sign of empire detection requires active monitoring of PowerShell launcher string in the PowerShell windows event logs:
powershell -noP -sta -w 1 -enc
By default, the launcher string is present in Empire HTTP listeners. However, it can be easily changed. In many instances, it is commonly not changed by attackers, making it an effective signature. Additionally, the base64 encoded launcher script body can also be used as a signature.
Also Read: Threat Hunting Using Powershell and Fileless Malware Attacks
Detecting empire after the event can vary depending on the toy an attacker takes out of their toolbox. A forensic examiner can filter keywords on PowerShell event logs for the following strings to identify malicious events.
Invoke-TokenManipulation:
Attackers may modify access tokens to operate under a different user to perform actions and bypass access controls.
Invoke-RunAs:
Attackers may create a new process with a different token to escalate privileges and bypass access controls.
Install-SSP / Invoke-Mimikatz:
Attackers may abuse security support providers (SSPs) to execute DLL when the system boots. This can be used to retrieve plaintext passwords that are stored in Windows.
Invoke-PSRemoting:
Attackers may use this to allow commands to be run on a remote computer.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
New-GPOImmediateTask:
Attackers may modify a GPO that will install and execute a malicious Scheduled Task on a compromised system.
Invoke-PSInject:
Attackers may inject code into processes in order to evade process-based defenses as well as possibly elevate privileges.
Invoke-DCOM:
Attackers can leverage remote COM execution for lateral movement.
Invoke-Kerberoast:
Attackers can use this to request service tickets and return crackable ticket hashes.
Invoke-SessionGopher:
Attackers can use this to extract private key and session information.
Conclusion:
The Empire framework is a great tool for post-exploits. I hope this covers all the basics you need to know about this framework.
Source
This article wouldn’t be possible without the work of others. Here are the sources I’ve used during my investigation:
- CISA. (2021, July 19). (AA21-200A) Joint Cybersecurity Advisory – Tactics, Techniques, and Procedures of Indicted APT40 Actors Associated with China’s MSS Hainan State Security Department.. Retrieved August 12, 2021.
- https://attack.mitre.org/software/S0363/ Last accessed: Thu 17 Feb, 2022
- https://github.com/EmpireProject/Empire Last accessed: Thu 17 Feb, 2022
- https://www.powershellempire.com/ Last accessed: Thu 17 Feb, 2022



































