Microsoft warns of a new campaign focused on MSSQL servers, threat actors are launching brute-forcing attacks against poorly secured Microsoft SQL Server (MSSQL) database servers using weak passwords.
While this isn’t necessarily the first time MSSQL servers have been targeted in such attacks. In the past threat actors used the legitimate sqlps.exe tool to Run a SQL Server PowerShell mini-console without a Module and ScriptBlock Logging which refers to MITRE T1218.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
“The attackers achieve fileless persistence by spawning the sqlps.exe utility, a PowerShell wrapper for running SQL-built cmdlets, to run recon commands and change the start mode of the SQL service to LocalSystem,” the Microsoft Security Intelligence team revealed.
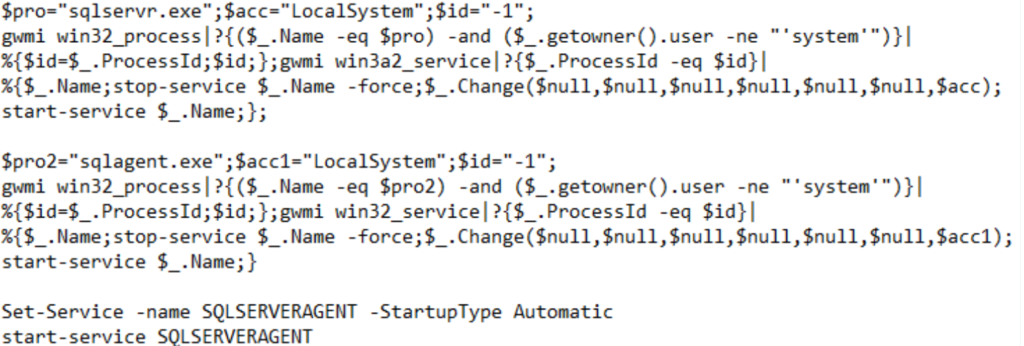
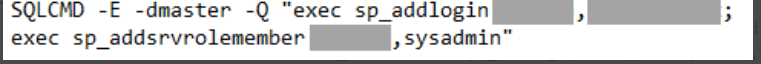
“The attackers also use sqlps.exe to create a new account that they add to the sysadmin role, enabling them to take full control of the SQL server. They then gain the ability to perform other actions, including deploying payloads like coin miners.”
Using sqlps, a utility that comes included with the Microsoft SQL Server and allows loading SQL Server cmdlets, as a LOLBin, enables the attackers to execute PowerShell commands without worrying about defenders detecting their malicious actions.
It also helps ensure that they don’t leave any traces to be found while analyzing their attacks since using sqlps is an effective way to bypass Script Block Logging, a PowerShell capability that would otherwise log cmdlet operations to the Windows event log.
Also Read: Threat Hunting Using Powershell and Fileless Malware Attacks
Detection & Response:
- Monitor sqlps.exe and PowerShell wrapper for running in SQL-built cmdlets. Hunt for suspicious recon commands such as
$_.getowner().user , stop-service , $_.Change,$acc=LocalSystem,start-servicewhich is the indicator of start mode of the SQL service to LocalSystem. - Monitor for commands
sp_addlogin sp_addsrvrolemember, Attackers use sp_addrolemember to add a member to a fixed database or user-defined role.
It is recommended to not expose MSSQL servers online, secure them with strong admin credentials, apply the latest security updates, and enable logging to monitor for potential attack patterns.



































