Most of the top-rated attacks vector seems to be a phishing email. While checking the last year’s stats, 70% of attacks were initiated with phishing emails. A wide range of categories is there in phishing emails. Let’s see how we can identify phishing emails, scenarios, and prevention methods.
How to spot a phishing email?
1-Analyze Suspicious Email Addresses, Links, and Domain Names:
Hacker-generated email addresses, links, and domain names are frequently easy to identify. Here are some things to look out for:
- If someone’s real email address is [email protected] and you receive an email from [email protected] or [email protected], it could be a phishing attempt. The attacker may even try to explain that the IT department assigned them a new email address. Regardless of what is in the email, double-check the sender’s identity.
- Since many emails contain links, it’s easy to trust the wrong one, especially if it appears to come from someone or an organization you know. Always double-check the contents of a link before clicking on it, and keep in mind that links can download malware or redirect you to a bogus website that appears legitimate but is designed to install malicious software on your computer.
- Sometimes we will get emails from genuine domains or client addresses, but the links will be malicious. In this case, the sender’s address might be compromised.
Phishing is the most used weapon to attack large organizations as well as single users. So we need to analyze the emails wider.
If you are are looking to create email approval workflows using google forms, then check out Lido.app.
2-Errors in Grammar and Spelling:
The errors in a phishing attack are frequently far more odious, with mistakes such as:
- Misspelling the company name
- Misspelling your name or the name of the supposed sender
- Rearranging key sentence elements, such as placing an adjective after a noun rather than before it
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
3-Suspicious Attachments:
In a legitimate email, attachments are usually alluded to within the body. For example, the sender could say, “I am attaching the report.” This makes checking the attachment simply because its name should correspond to what was mentioned in the message. The attachment in a phishing email may have nothing to do with the email’s body content. It may also be unnecessary. For example, an email discussing a report but including an attachment with instructions on how to reset your password.
4-Threats or a Sense of Urgency:
Many phishing attacks use scare tactics to convince victims to reveal personal information. An attacker may also attempt to make the target feel embarrassed, leaving them with no choice but to act to prevent others from discovering some alleged secret. For example, they may claim that the victim has downloaded malware on their computer and must provide their login information so that “the IT department” can remove it. An employee may accept the invitation to share this information to rectify the situation without having to admit they made a mistake.
5-Emails requesting login information, payment information, or sensitive information:
- Any email requesting personal information should be considered suspicious. Many phishing emails request information that they should already have access to, such as contact information you have provided in the past.
- Companies have also decided not to request login information for payment data via email, specifically to avoid phishing attacks. If you receive an email that appears to be legitimate but requests personal or sensitive information, it is best to contact the company directly by composing a new email with the appropriate address rather than responding to the one you were sent.
Analysis of a Phishing Email:
Step 1: Whenever a user reports an email, first need to check whether the sender is a VIP user or not. If yes, need to respond to the reported user/need to act within a maximum of 30 minutes. Why means, that most of the hackers target VIP users since their Email IDs are available on open websites.
Step 2: Need to analyze the header of the email to confirm whether it is spoofed or not. If the sender address the email and in the header, mismatches mean, there is a high range of possibility to address it as a spoofed email. Sometimes the sender and reply-to address mismatches in spoofed email scenarios. We can use MX Toolbox to analyze the header of the email and we need to check the below-mentioned details:
- From
- Return-Path
- Reply-To
- Recipient
- X-Distribution
- X-Mailer
- Bcc: or X-UIDL
- X-Spam score, X-Spam flag, and X-Spam status
- DMARC record
- Initiating IP
Step 3:Need to check the content of the email. In a phishing email, mostly the use of the sender domain won’t match with content. As said in the above paragraphs, need to check whether anything matches. There is no assurance that all phishing emails must have malicious URLs or attachments.
Step 4: Check if there are any links in the email. If yes, analyze the URL in the isolated sandbox or in open tools like app.any.run, urlscan.io, etc. We will get to know more details like redirecting URLs and so on. Mostly all organizations have isolated sandbox to analyze the URL interactively. App.any.run is an effective interactive sandbox.
Step 5: Check whether there is an attachment. If yes, download the file and upload it in VT to check the reputation or analyze it in the sandbox.
Step 6: After analyzing the above steps, reply to the email.
Examples:
Scenario 1:- Spoofed email:
Email Details:
Sender: Rahul Thomas <customersupport@hdfc[.]com>
Recipient: [email protected]
Subject: Hello
MessageDate: 2022-03-15 01:07:55
Url/Attachment: NA
Email content:
Hello,
Good day!!! Your account was locked due to an incorrect pin. Please use the below link to unlock it.
Regards,
Customer support
Analysis:
- Analyzed the header and found the following details:
- P1Sender: KAYWHITEHOUSE247@protonmail[.]com
- Reply-To: 9088734923mr@gmail[.]com
- IP address: 206.189.233.229
- The original sender, Reply-To address, and sender in the email are mismatched.
- In the email content, they mentioned clicking the link but there is no link. From the email sender, it seems to be an automated email from HDFC bank. But from the header, found that it originated from gmail.com.
- From these points, this can be concluded as a spoofed Email.
Also Read: Email Header Analysis – Use Cases Including SPF, DKIM & DMARC
Scenario 2:-Credential Phishing email:
Email Details:
Sender: Teddle@insurance[.]com via Smartsheet <user@app[.]smartsheet[.]com>
Recipient: [email protected]
Subject: Invoice
MessageDate: 2022-04-15 01:07:55
Url/Attachment: YES
Email Content:
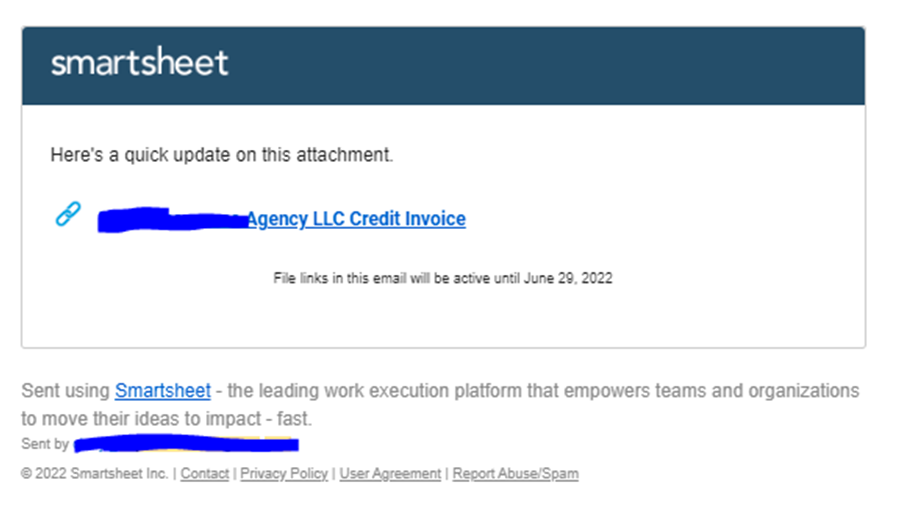
URL:
hXXps[:]//click.smartsheet[.]com/f/a/s4Bq3wtm_PxS9m_K1h8rAg~~/AARF7wA~/RgRkd2GkP0QkaHR0cHM6Ly9wa2VuNTA3My53aXhzaXRlLmNvbS93ZWJzaXRlVwNzcGNCCmKGpNyUYsOMOAVSGGdpbmEuc21pdGhAc3RhdGVhdXRvLmNvbVgEAAAAAA~~
Analysis:
- Analyzed the header and found that it was not originated from insurance[.]com. The email was sent from the application smartsheet[.]com.
- There is a link in the email. While analyzing it in an isolated sandbox, found that it is directed to the following page: “hxxps://pken5073[.]wixsite[.]com/website”
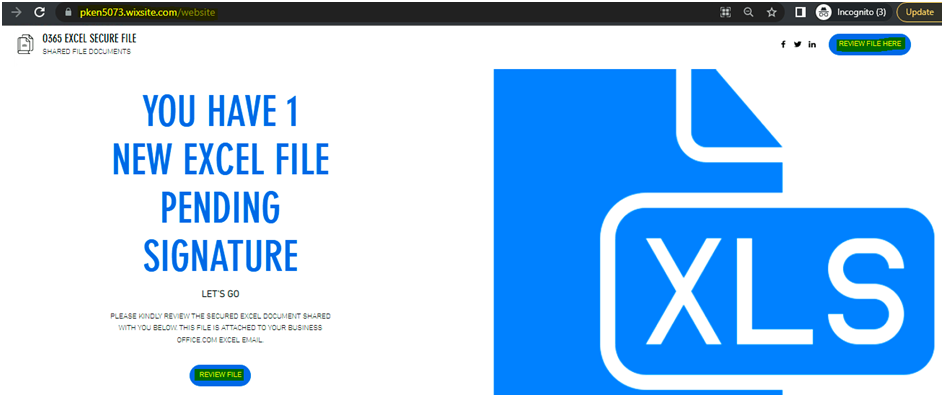
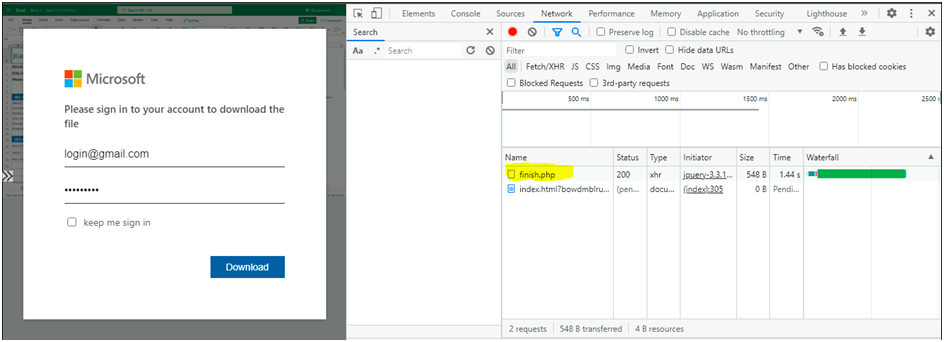
While clicking on the review button, it is redirecting to fake Microsoft login webpage.
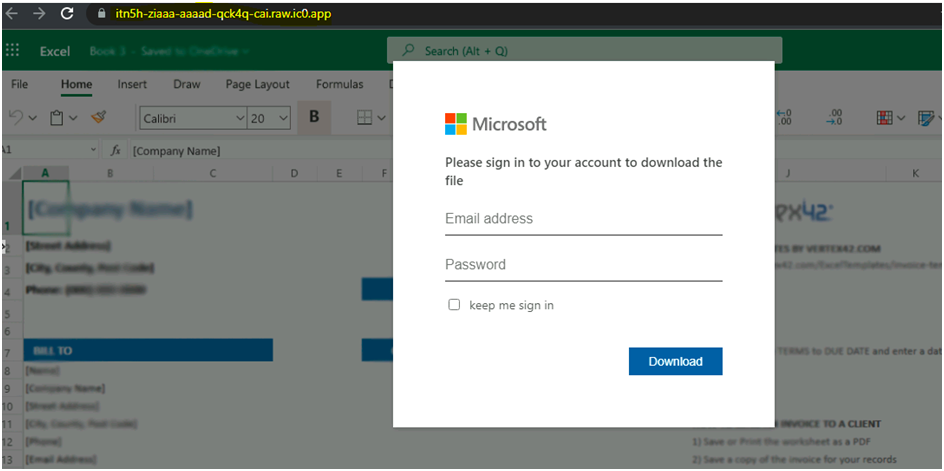
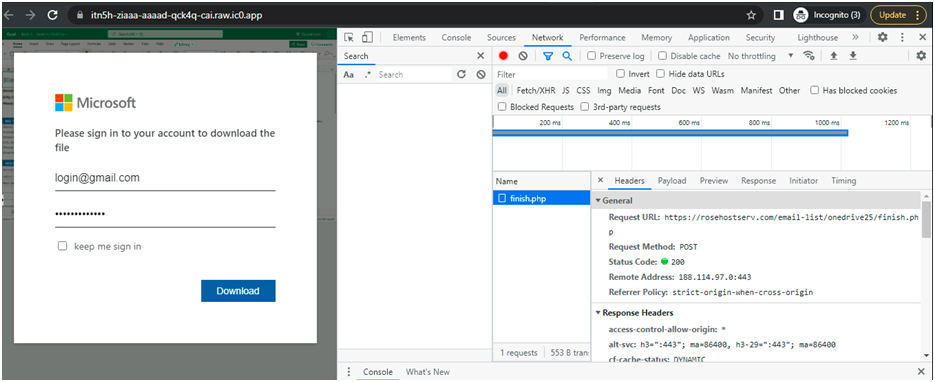
Next, we are going to find on what webpage they are going to save the entered credentials. For that navigate to the right corner dots– More Tools — Developer Tools — Network.
Also Read: How DKIM SPF & DMARC Work to Prevent Email Spoofing and Phishing
- While entering the credentials, the information are gathered and stored in one PHP page “finish.php” (URL: hxxps://rosehostserv[.]com/email-list/onedrive25/finish[.]php). In this case we need to block the url in the email as well as the redirecting url.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
- From these points, we can conclude it is a credential phishing email.
Conclusion:
Today we have discussed how to identify phishing emails and examples to make the analysis effective. Phishing is the most used weapon to attack large organizations as well as single users. So we need to analyze the emails wider.



































