DNS acts as a phone directory for the internet, allowing IP addresses and domain names to be translated. Long strings of numbers are difficult for humans to remember. A web address (such as extrahop.com/network-attack-library) is easy to remember and provides some information about your destination. Since web browsers employ IP addresses, you’ll need an option to transform the two.
DNS Tunneling:
“DNS tunneling is a technique which exploits DNS protocol for tunneling data via DNS query and response packet”
- DNS tunneling requires the compromised machines to run a DNS Tunneling client program besides the attacker runs a DNS Tunneling server program on his authoritative DNS server (C&C Server).
- The DNS client program sends data encoded in the hostname label of a DNS Query and the server sends data encoded into the Resource Record (RR) of a DNS Response packet.
- DNS Tunnel can be used for C&C server communication, data exfiltration and tunneling of any Internet Protocol (IP) traffic via DNS Protocol.
- DNS tunneling routes DNS requests to the attacker’s server, providing attackers a covert command and control channel, and data exfiltration path and it also known as difficult-to-detect attack.
- This technique is difficult to detect because DNS is a noisy protocol, making it harder to distinguish a normal host query and normal DNS traffic from malicious activity.
The botnet’s C&C communication channel refers to the protocol used to communicate between the bots and the botnet’s C&C Server. To use DNS Tunneling as a C&C communication channel, the attacker embeds the DNS Tunneling mechanism in the malware’s binary and the malware binary is also hardcoded with the domain name where the C&C server was hosted. To establish a connection with the C&C server, the bot would send a DNS query to resolve the IP address of the C&C server.
How does DNS Tunneling work?
Basic working procedure:
- Hackers have a server with malware running on it, as well as a domain linking to it.
- The attacker searches for the attacker-controlled domain using a server that has been infected with malware.
- When the DNS resolver routes the query, it builds a tunnel between the attacker and their target, allowing them to obtain data, remotely control the host, or otherwise proceed with the attack.
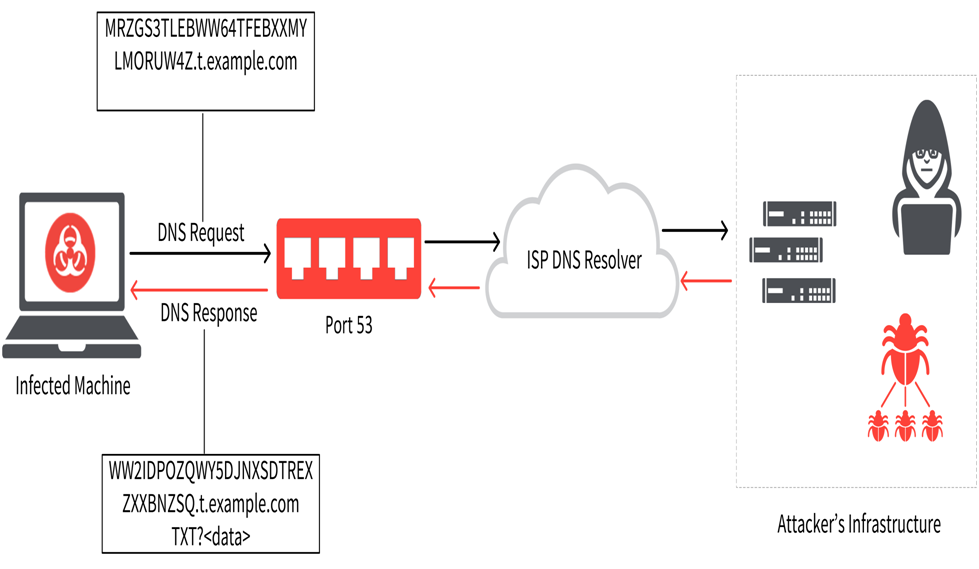
Detailed Explanation:
- DNS Tunneling malware encodes the payload data in a DNS Query packet using the base64 encoding algorithm, and then sends it to the server as a DNS Query.
- The hostname of a DNS Query is prepended to the payload data.
- Using the RDATA field of various DNS Resource Record (RR) types, the server responds to the query with its base64 encoded payload data in a DNS Response packet.
Example:
An attacker first registers a domain name, such as “dns.com”. Then points its nameserver records towards the server where the DNS tunneling server program is running. The server acts as an authoritative name server for that domain name and its sub-domain to facilitate server-side tunneling and decapsulating the payload data by running DNS tunnel server daemon on the server
- If the attacker registers the domain dns.com, then data can be transmitted as a DNS request to <base64_encoded_data>.dns.com
- The client computer could send an A record query where the data is encoded within the hostname. DNS Query: gewsSqJhs7AopOS34f32fgqqe.dns.com
- Then the server could send any command/data by responding to the A query with a CNAME record as response. DNS Response: ZwsAq5sT43jgcDkhuH6rsp.dns.com
DNS Tunneling records:
Attackers will use different types of DNS Tunneling record types in which to embed their attack. The most popular DNS tunneling records are TXT, NULL, and CNAME. TXT records are often used because they have the largest and most diverse payload structure.
DNS Tunneling Attacks:
- Command and control (C2) : Malware is introduced through an infected device that bypasses TCP/UDP connections to send commands and upload data. From here, infiltrators can employ any number of common attacks.
- IP-over-DNS tunneling: This will make it easier for criminals to carry out their plans, because some tools/programs use DNS inquiry reaction convention to activate the IP stack.
- Wifi Abuse & Policy Bypass: By abusing systems that allow IP traffic out, an attacker can construct a complete IPv4 tunnel. This allows them to enter an internal network without paying for WiFi and evading security and IT policy firewalls.
- Data Exfiltration : Attackers use DNS to steal valuable information. Given the added encoding and overheads, this isn’t the most efficient method for getting data from a victim’s PC, but it does work.
Data Exfiltration via DNS Tunneling:
- Step 1: The DNS tunneling client malware on the infected machine (Bots) read the data to be exfiltrated line by line.
- Step 2: Slices the data into small chunks and performs base64 encoding on each line.
- Step 3: The base64 encoded data is then encapsulated as subdomain labels suffixed with the attacker’s domain name and sent to the Recursive DNS Server in a DNS query.
- Step 4: The DNS query is processed by the Recursive DNS Server, Root, and TLD Servers, which locate the name server authoritative for the attacker’s registered domain name and direct the “DNS query” to that server.
- Step 5: When the DNS query with payload data arrives on to the authoritative DNS server of the attacker’s registered domain, the attacker can track down those DNS queries logs, parse them and decode the base64 encoded labels (subdomains) to reassemble the stolen data from the client (Infected bot).
- Step 6: The server then sends the client a DNS Response packet with the new command encoded as a Resource Record (RR) in the DNS Response packet.
Data is transferred back and forth via DNS Tunnel in this manner. To avoid caching, DNS answers have a short TTL value. The DNS protocol does not allow the server to create a connection with the client; instead, the client must make a query to the attacker’s DNS server on a regular basis to obtain new commands (C&C Server).
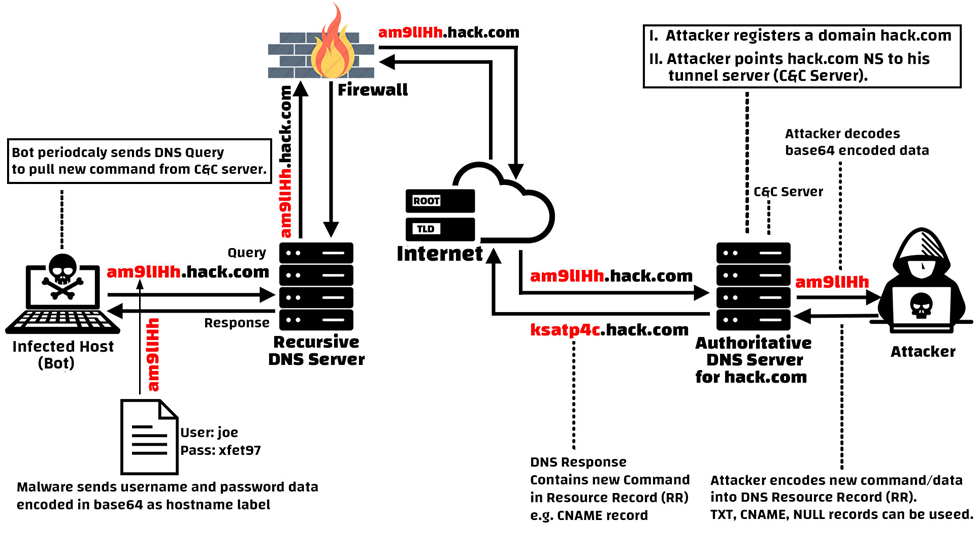
DNS Tunneling Impacts:
- Malicious actors use DNS to tunnel several protocols, such as HTTP or SSH, allowing them to pass stolen data or IP traffic silently.
- For an inside host that has already been abused, the DNS tunnel can be used as a full controller channel. This enables fraudsters to download code to malware, steal data from the organisation in secret, and gain total remote access to the servers, among other things.
- DNS tunnels can also be used to bypass captive portals, so they don’t need to pay for wi-fi services.
- DNS tunneling is a client-server model that leverages the DNS protocol to tunnel information and malware.
- DNS tunneling flaws could create an accessible backchannel for attackers to exfiltrate stolen data. DNS provides a covert means of correspondence to bypass firewalls.
How to identify DNS tunneling attacks?
The detection techniques will be discussed in two separate categories, payload analysis, and traffic analysis.
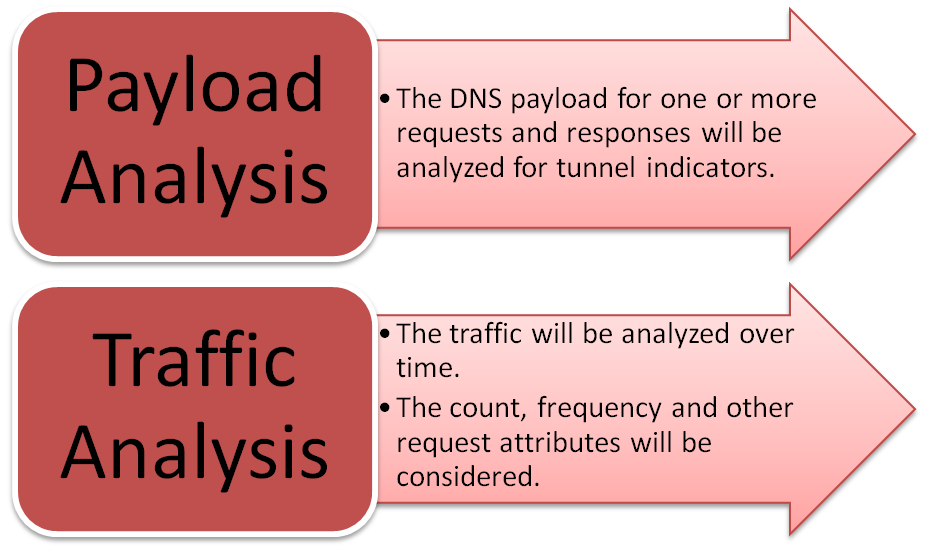
1-Payload Analysis:
Some of the payload analysis techniques are:
1.1-Size of request and response: One technique involves analyzing the size of the request and response. DNS tunneling utilities usually try to put as much data into requests and responses as possible. Thus, it is likely that tunneling requests will have long labels, up to 63 characters, and long overall names up to 255 characters.
1.2-Entropy of hostnames: DNS tunnels can be detected based on the entropy of requested hostnames. Legitimate DNS names often have dictionary words or something that looks meaningful. Encoded names have a higher entropy and more even use of the characters set. Although, there are exceptions to this where DNS names are used to represent some type of information. Looking for DNS names that have high entropy can be an indicator of tunneling.
1.3-Statistical Analysis: Looking at the specific character makeup of DNS names is another method that can be used to detect tunneling. Legitimate DNS names tend to have few numbers whereas encoded names can have a lot of numbers. Looking at the percentage of numerical characters in domain names has been proposed.
1.4-Uncommon Record Types: Looking for records that are not commonly used by a typical client e.g. ‗TXT‘ records is another possible detection method.
1.5-Policy Violation: If a policy requires all DNS look-ups to go through an internal DNS server, violations of that policy could be used as a detection method. Traffic could be monitored for DNS requests directly to the internet. Most DNS tunneling utilities are designed to function even when forwarding requests through an internal DNS server.
1.6-Specific Signatures: In some cases, researchers have provided signatures for specific DNS tunneling utilities. A signature can be used to check specific attributes in a DNS header and check for specific content in the payload. For example, a Snort signature was developed for detecting NSTX DNS tunneling.
2-Traffic Analysis:
Traffic Analysis involves looking at multiple requests/response pairs over time. The amount and frequency of requests can be used for an indication of tunneling. Some of the traffic analysis detection techniques are:
- Volume of DNS traffic per IP address
- Volume of DNS traffic per domain
- Number of hostnames per domain
- Geographic location of DNS server
- Domain history
- Volume of NXDomain responses
Preventive Measures for DNS Tunneling:
- The technology should be built to detect both more complicated data extraction techniques and attacks that use preloaded toolkits.
- Defense in depth is a security strategy where there are multiple layers of security. If one layer fails to detect malicious activity, another layer is in place to also detect it. By implementing rules using both payload analysis and traffic analysis some level of defense in depth is achieved.
- To prevent data possession, a tool must be deployed that blacklists the destinations from which data will be extracted. This is something that needs to be done on a frequent basis.
- A DNS firewall should be configured and designed in such a way that any intrusion is rapidly detected. Exfiltration can be facilitated by using a firewall.
- When a DNS solution includes real-time analytics that evaluates any strange queries or patterns, users will be able to make better informed security decisions. Tracking the state of the network by the DNS protected solution is more efficient.
Conclusion:
DNS is critical for all businesses. Unfortunately, preventing DNS-based threats is a big task, and hackers are taking advantage of its inescapable but not totally evident exploitable surface. The above-mentioned techniques will be useful to detect and prevent DNS tunneling.



































