DMARC is an open email authentication protocol that provides domain-level protection of the email channel. DMARC authentication detects and prevents email spoofing techniques used in phishing, business email compromise (BEC) and other email-based attacks.
We have already discussed about working architecture of DMARC in previous blog. Now we are going to discuss how DMARC can prevent email spoofing.
Also Read: Email Header Analysis – Use Cases Including SPF, DKIM & DMARC
How DMARC is used to reduce spoofed emails?
- DMARC is a method for helping email senders and recipients in determining whether or not a particular message is truly coming from the sender.
- This makes it simpler to recognize spam and phishing messages and prevents users from receiving them in their inboxes.
- A proposed standard called DMARC enables email senders and recipients to collaborate in sharing information about the emails they send to one another.
- The infrastructure for mail authentication can be improved with the use of this information, enabling senders to authenticate all of their email.
- Additionally, it provides the legitimate owner of an Internet domain with a method to request that fraudulent messages—such as spam that has been faked or phishing—be rejected outright or sent directly to the spam folder
DMARC can’t protect the emails in following scenario:
- DMARC isn’t intended to stop all phishing attempts; it’s simply made to protect against direct domain spoofing. Example.com’s owners or operators may use DMARC to protect that domain, but it would have no impact on example.com or example.net.
- While phishing and other malicious activities frequently use the technique of impersonating a certain domain, DMARC does not cover all possible attack routes. For instance, DMARC does not handle display name abuse or cousin domain attacks (sending from a domain that resembles the target being abused, such as exampl3.com vs. example.com) (i.e. modifying the “From” field to look as if it comes from the target being abused).
Anatomy of a DMARC resource record in the DNS:
Below is the Tag Name explanation:
| Tag Name | Purpose | Sample |
| v | Protocol version: Identifies the record retrieved as a DMARC record. It must be the first tag in the list. | v=DMARC1 |
| pct | Percentage of messages subjected to filtering | pct=20 |
| ruf | Reporting URI for forensic reports; Addresses to which message-specific failure information is to be reported. Comma separated plain-text list of DMARC URIs. | ruf=mailto:[email protected] |
| rua | Reporting URI of aggregate reports; Addresses to which aggregate feedback is to be sent. Comma separated plain-text list of DMARC URIs. | rua=mailto:[email protected] |
| p | Policy for organizational domain; Policy to apply to email that fails the DMARC test. Valid values can be ‘none’, ‘quarantine’, or ‘reject’. | p=quarantine |
| sp | Policy for subdomains of the OD | sp=reject |
| adkim | Alignment mode for DKIM | adkim=s |
| aspf | Alignment mode for SPF | aspf=r |
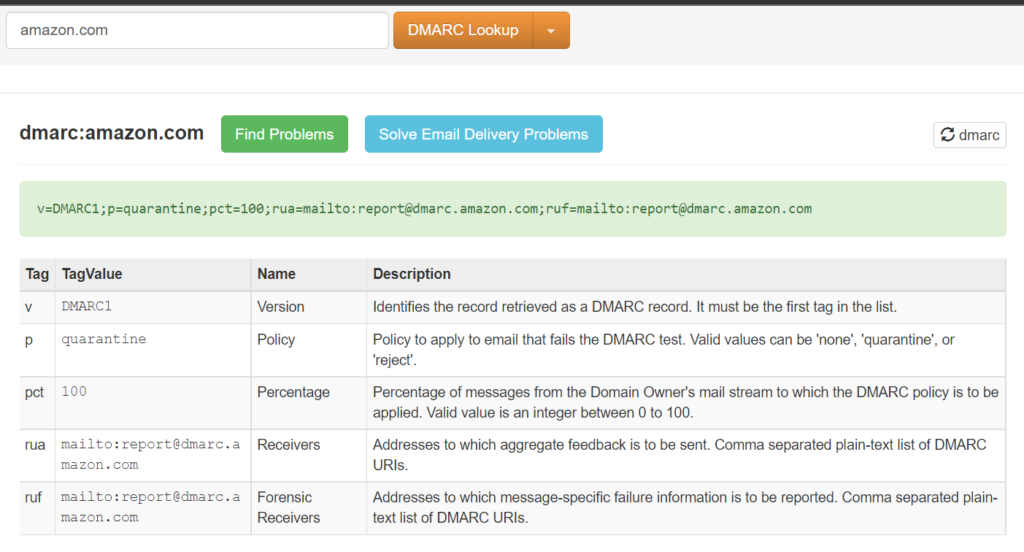
Sample DMARC record of the domain “amazon.com”:
v=DMARC1;p=quarantine;pct=100;rua=mailto:[email protected];ruf=mailto:[email protected]
In the above txt record,
- Version is DMARC
- Policy of the email that fails DMARC test is “quarantine” which means whenever DMARC test fails, it will be automatically rejected.
- Reporting URI for forensic reports & aggregate reports is set to the email address report@dmarc[.]amazon[.]com which means the aggregated rejected email report will sent to the particular email id.
How to identify whether the domain has DMARC Record or not?
Used Website: https://mxtoolbox.com/dmarc.aspx
Example 1:
Domain Name: amazon.com
The above mentioned domain has DMARC record and attached the screenshot below for the reference:
Also Check : Generate Your safe & Strong Password Today – Online password generator
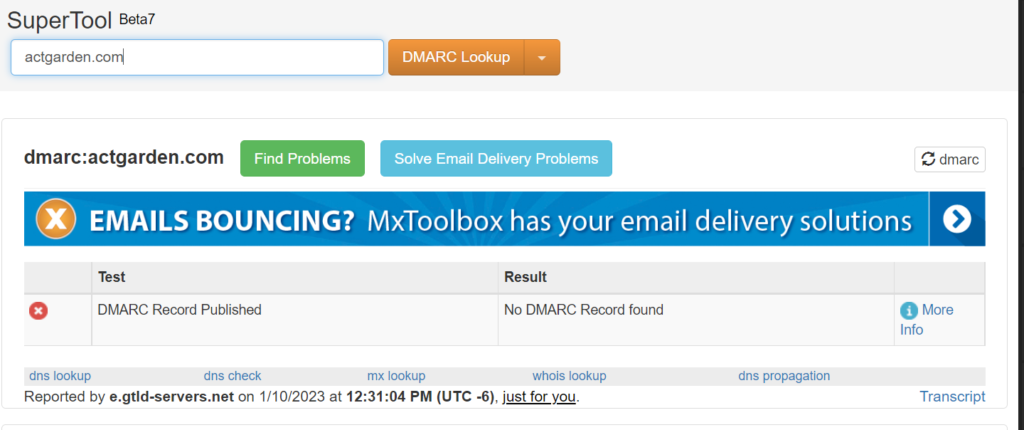
Example 2:
Domain Name: actgarden.com
The above domain doesn’t had a DMARC record and there is high chance of getting the spoofed emails.
Also Check : Web Malware Removal | How to Remove Malware From Your Website?
How to enable DMARC policy:
Setting up DMARC for the custom domain includes these steps:
- Step 1: Identify valid sources of mail for your domain
- Step 2: Set up SPF for your domain
- Step 3: Set up DKIM for your custom domain
- Step 4: Form the DMARC TXT record for your domain
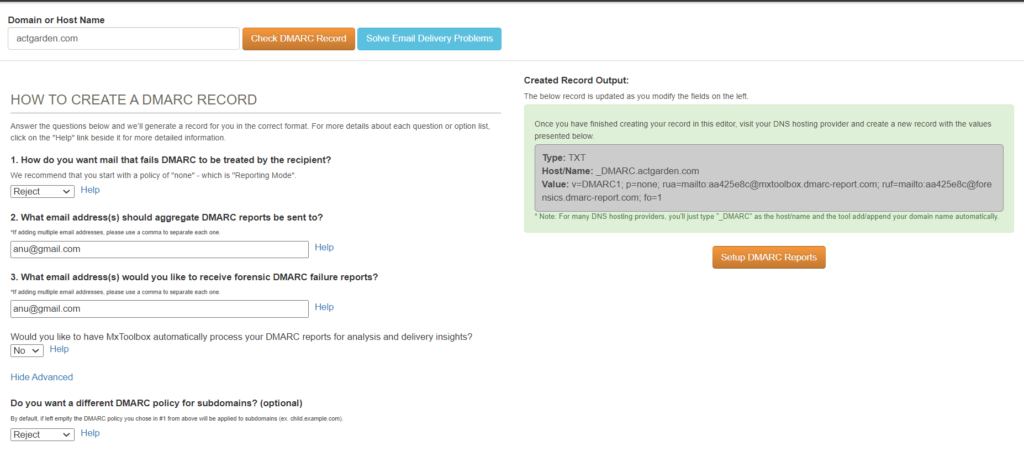
How to enable DMARC TXT record?
Domain Name: actgarden.com
We have many online services to generate DMARC record. Here I have used the website : https://mxtoolbox.com/DMARCRecordGenerator.aspx
- Decide the domain for which the DMARC record needs to be generated
- Paste the domain and click on “check DMARC Record”
- The record will be auto generated now
- The tag value can be custom defined and we can change it according to our need
- Once done, copy the created record which is in right side box and add it to the DNS record
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Conclusion:
DMARC implementation is beneficial for any size business. It offers complete domain visibility, oversight of email traffic, and protection from spoofers and phishers. Additionally, DMARC is believed to increase deliverability since if your emails authenticate correctly, mailbox providers may check that you are a real sender.
Contact our support team to set DMARC – Please reach [email protected] for any assistance.



































