CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES, and Blowfish, creating binary and hex dumps, compression, and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
Tool Download:
You can download this tool here. or Access the online version here.
Use case: Company A got a phishing email with a document file and you are given the job to analyze and hunt for malicious actions & extract IOCs.
Also Read: Cooking Malicious Documents with Cyberchef – Detect & Respond
Collecting Senders Information :

- Above figure shows user has received an email to inbox.We need to gather more information on such emails that is originating IP addresses, Sender Email Addressess and embedded urls.
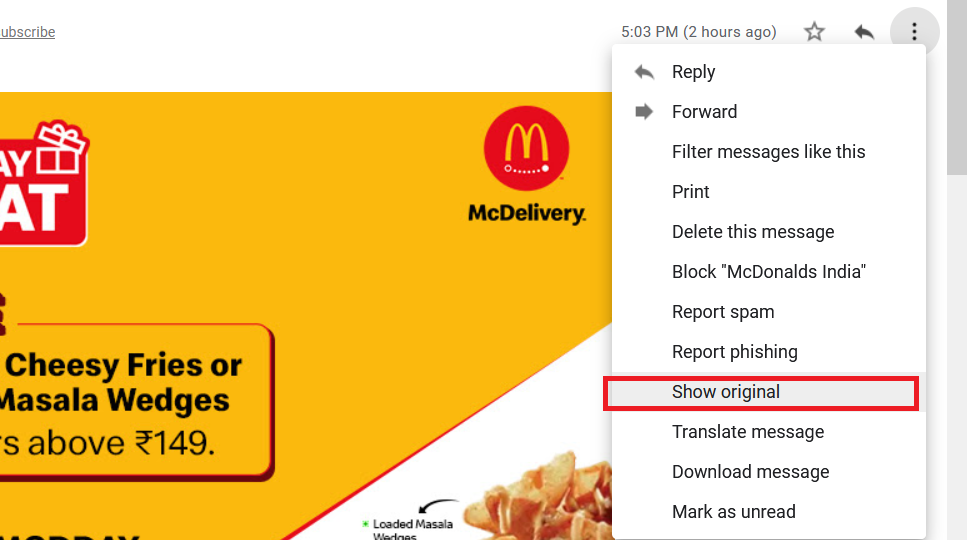
- Clicking on ( Show Original ) will retrive the email headers information were we can see lots of useful stuffs for our analysis.
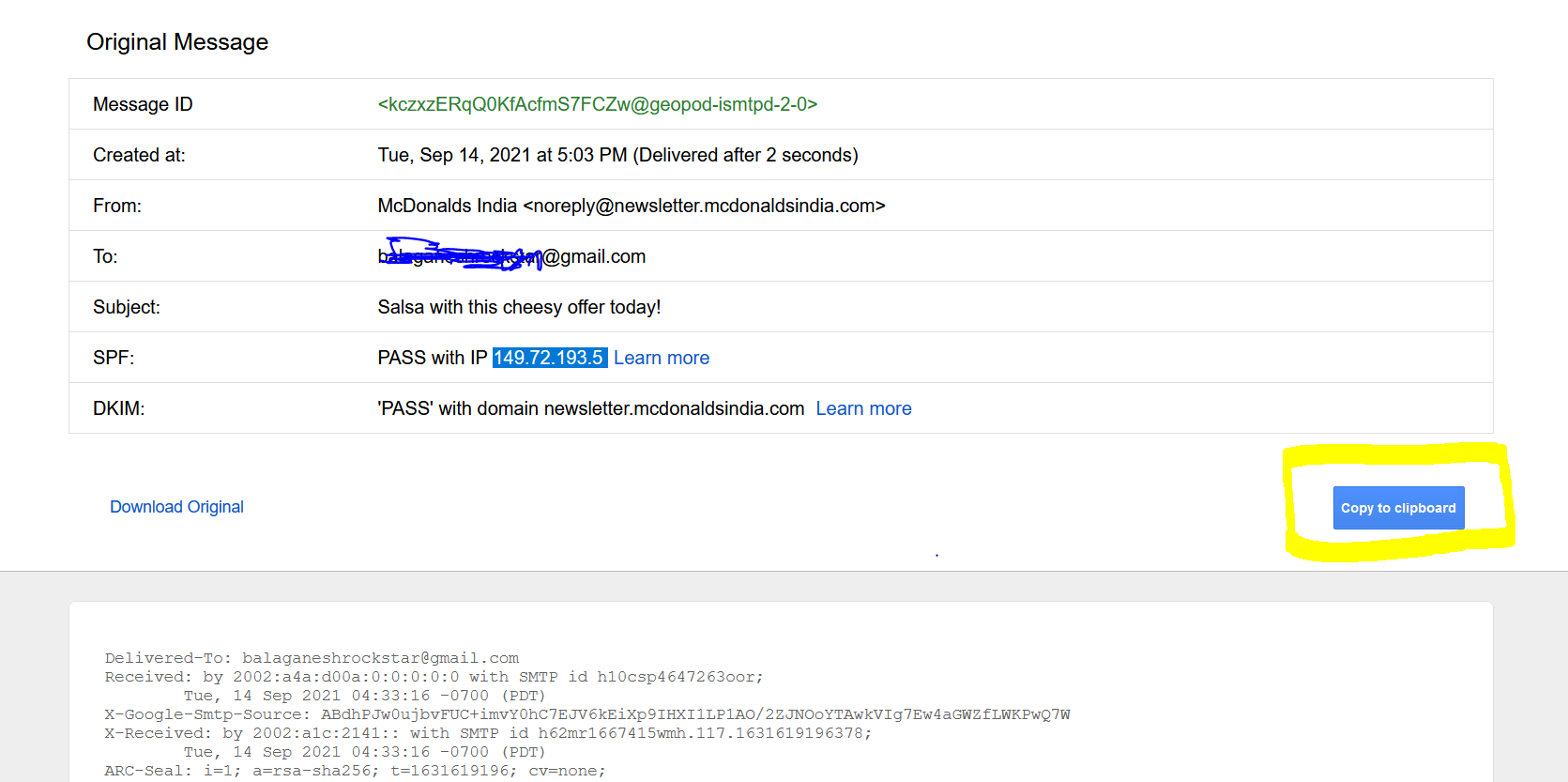
- Above figure shows , We have copied the entire email headers informations as clipboard , Now its time to play with cyberchef.
Also Read : Soc Interview Questions and Answers – CYBER SECURITY ANALYST
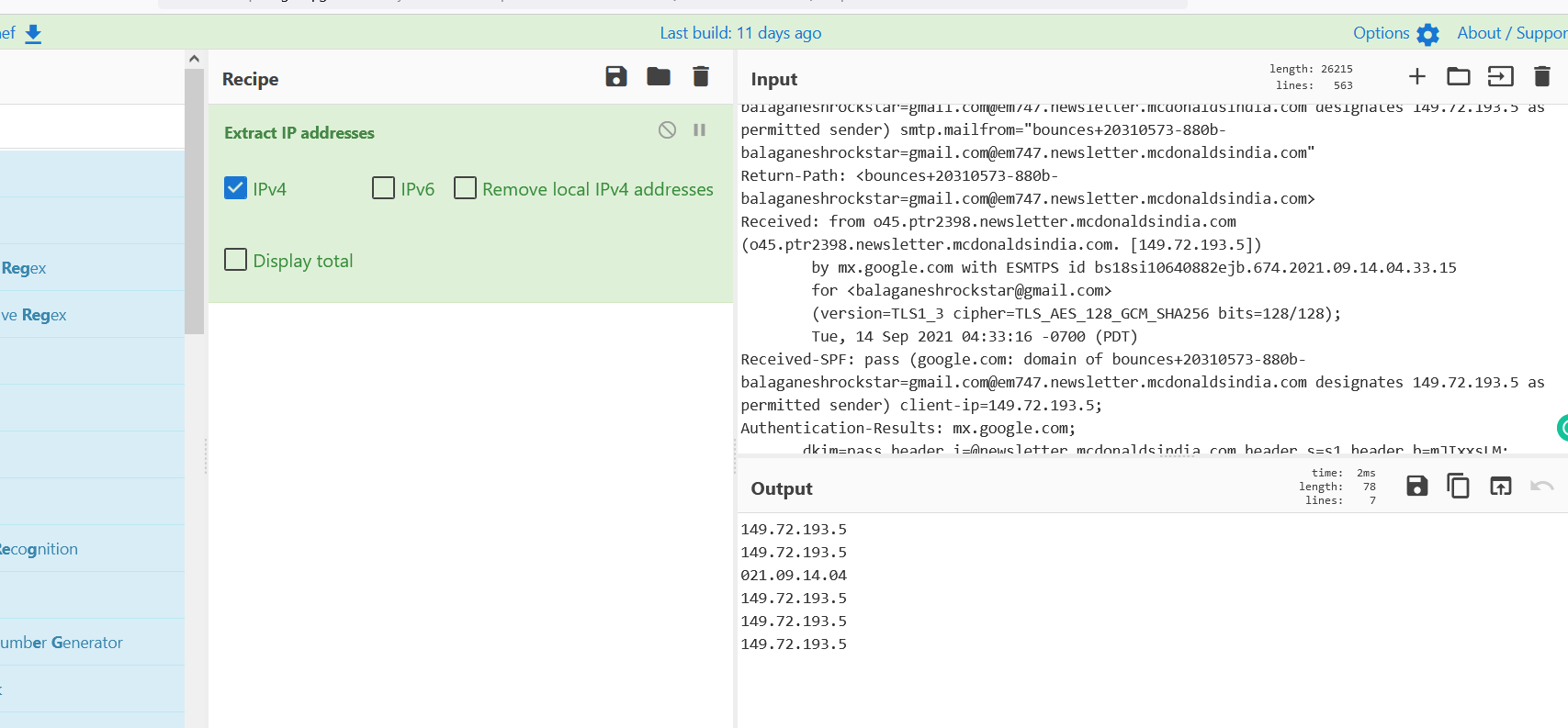
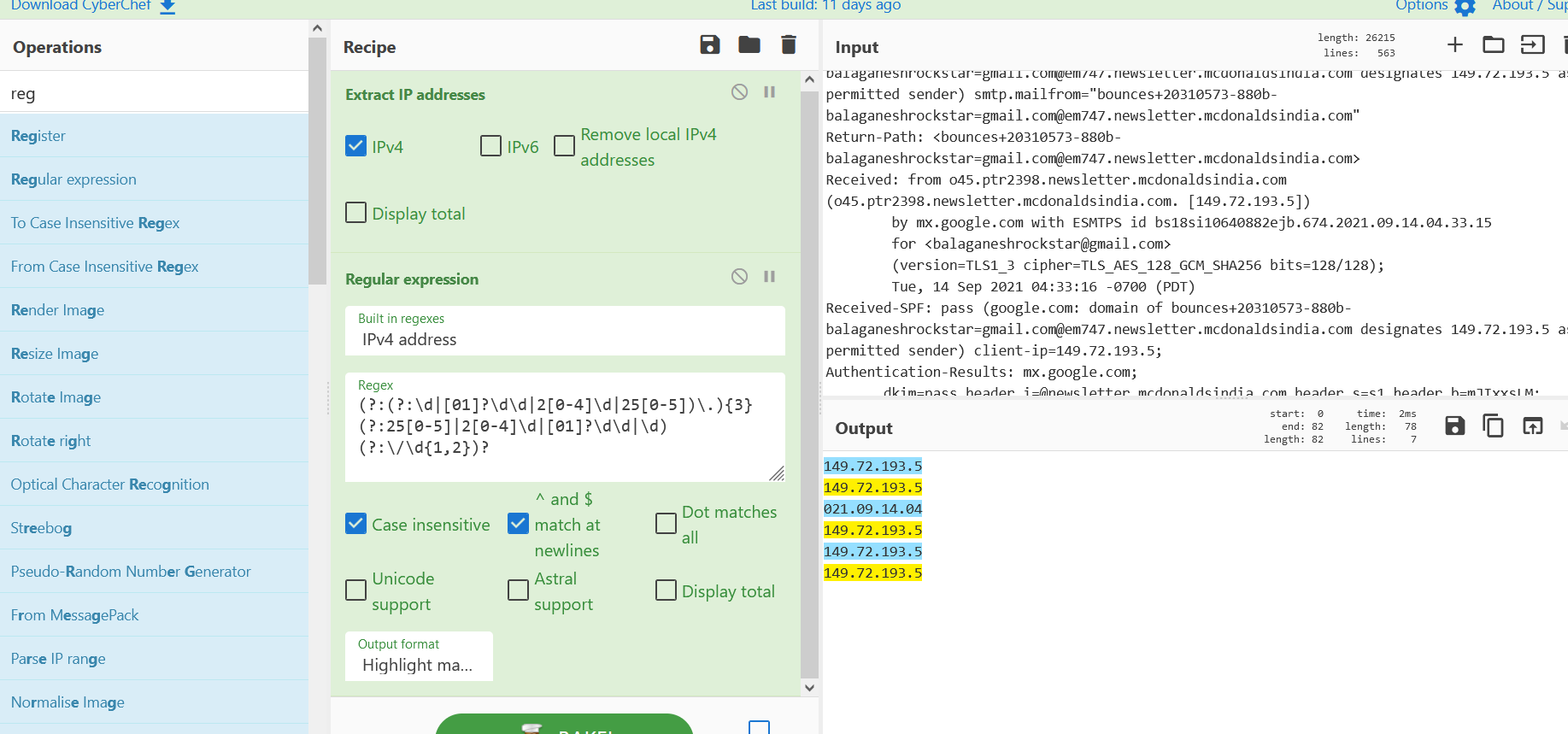
- Above figure shows , Extracted email headers are pasted on input section of cyber chef and adding the Extract IP addresses recipe quickly proivdes the list of IP addressses in the output section. In the example we see 021.09.14.04 , which is not a IP address , This can be ignored.
- Also adding regular expression recipe to highlight the IP addresses information .Now we are able to see the right IP addresses on the output section.
Also Read : DnsTwist Tool – Proactive Approach for Handling Phishing Cases
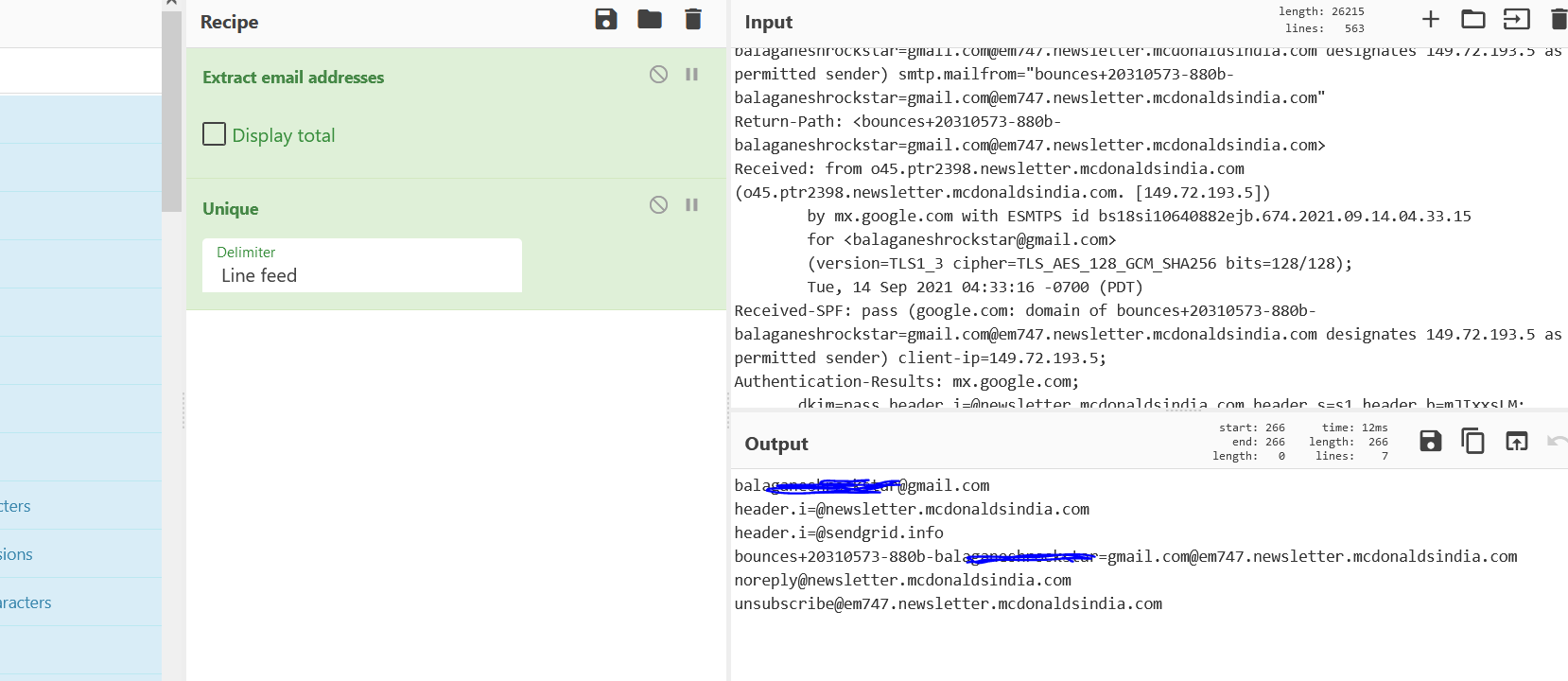
- Above figure , We have added the Extract Email Addresses recipe to quickly filter out list of other email addresses in the email header.
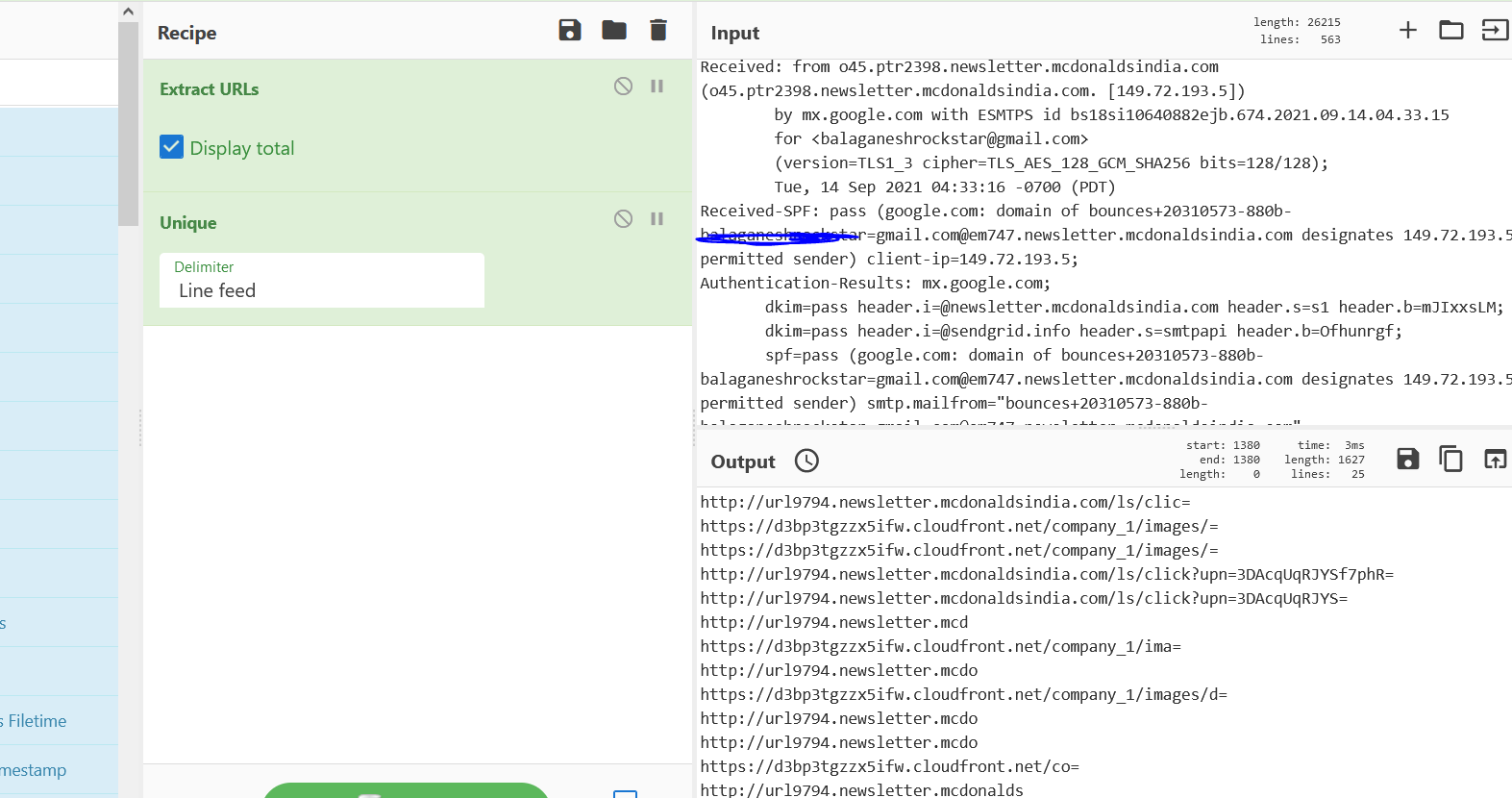
- Above figure shows , Adding the Extract URLS Recipe provides all the list of urls that are used in the email communication.
- So far , We analyzed a email and extracted IP addresses , Email addresses and embedded urls using cyberchef. In this case , this is legitmate email & Clean.
- Now we will apply the same techiques on real Phishing email.
Also Read : Common Vulnerabilities and Exposures – New CVE’s
Analyzing the Phishing Email:
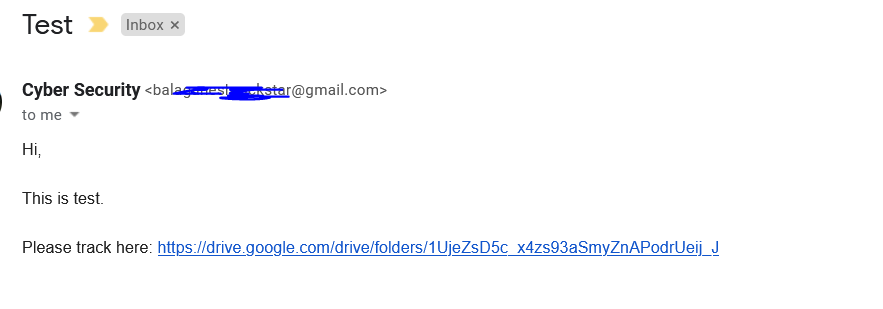
- Above figure , You can see a email which refers to a google drive. Intial you might think , when an user clicks this link it will land on Google Drive ? Yes , In some case it will. But most cases , this url will be mapped to another malicious urls. Lets find it !
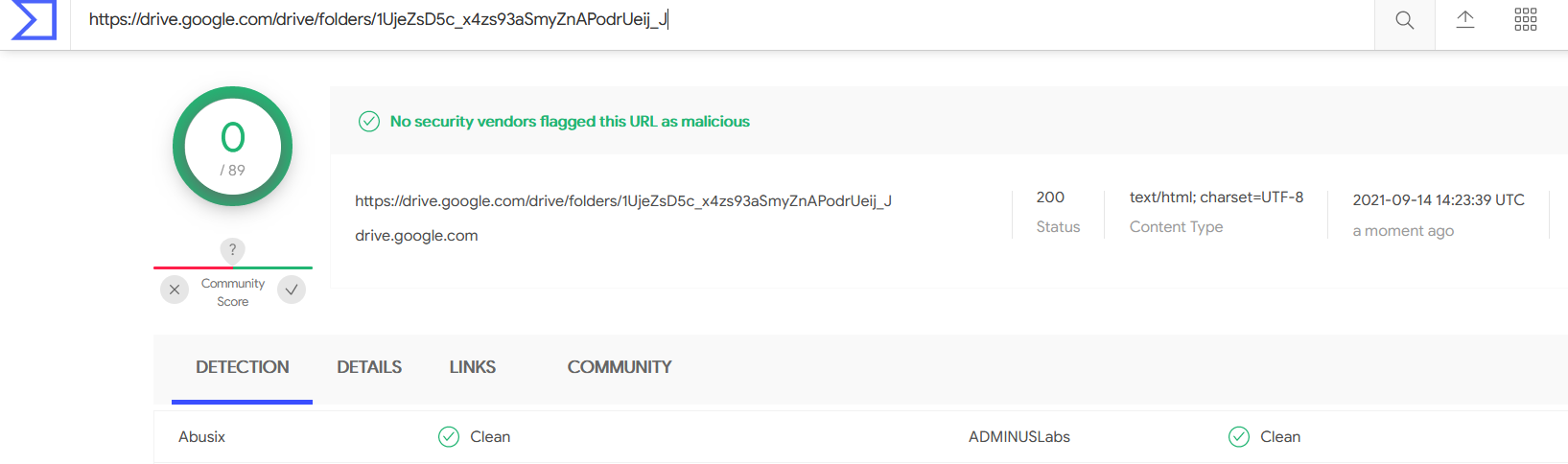
- Above figure shows threat intel says this is clean and good , Definitely not gonna trust this ! Lets figure it out !
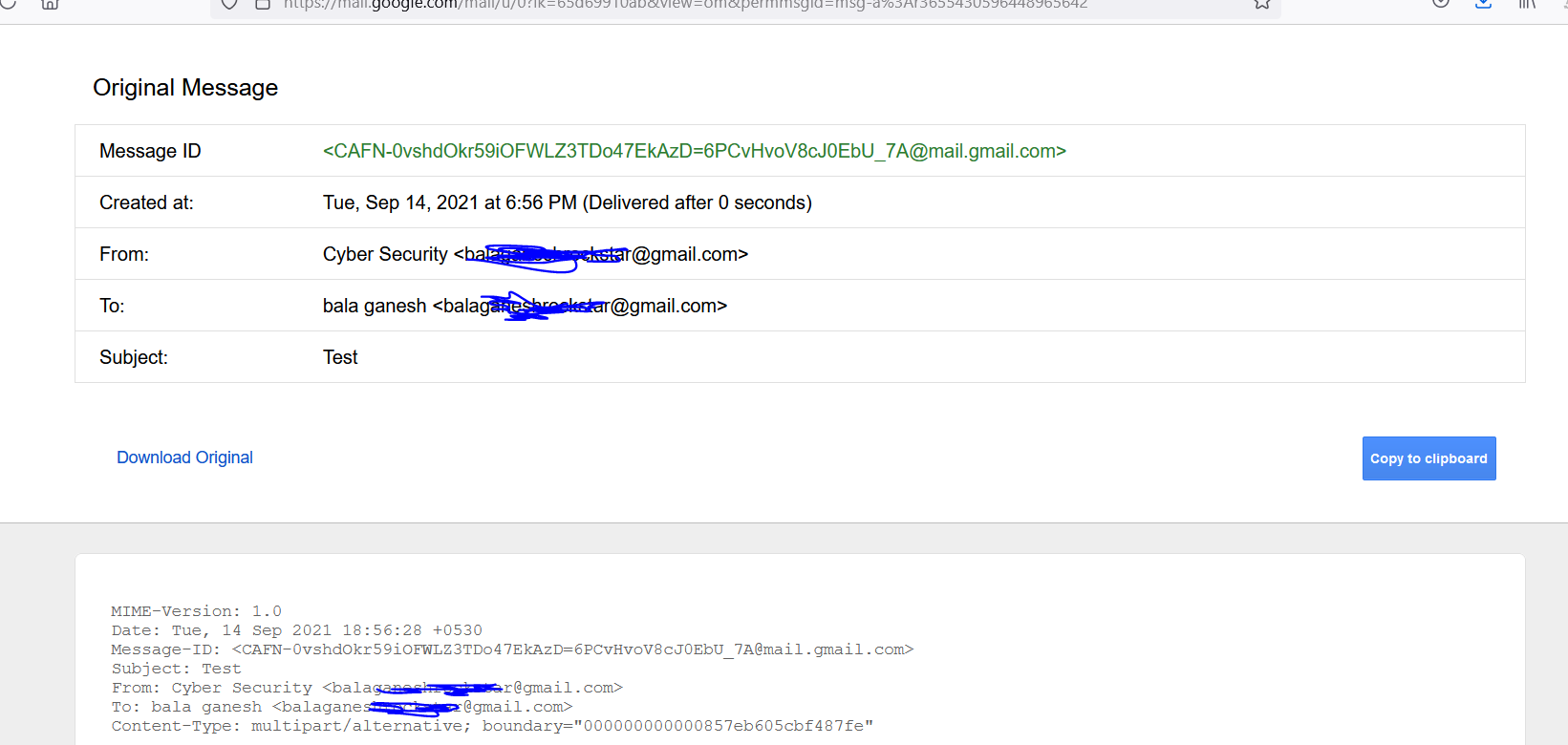
- Above figure shows , As we already did , We are going to copy the email header infromation and import those on cyberchef.
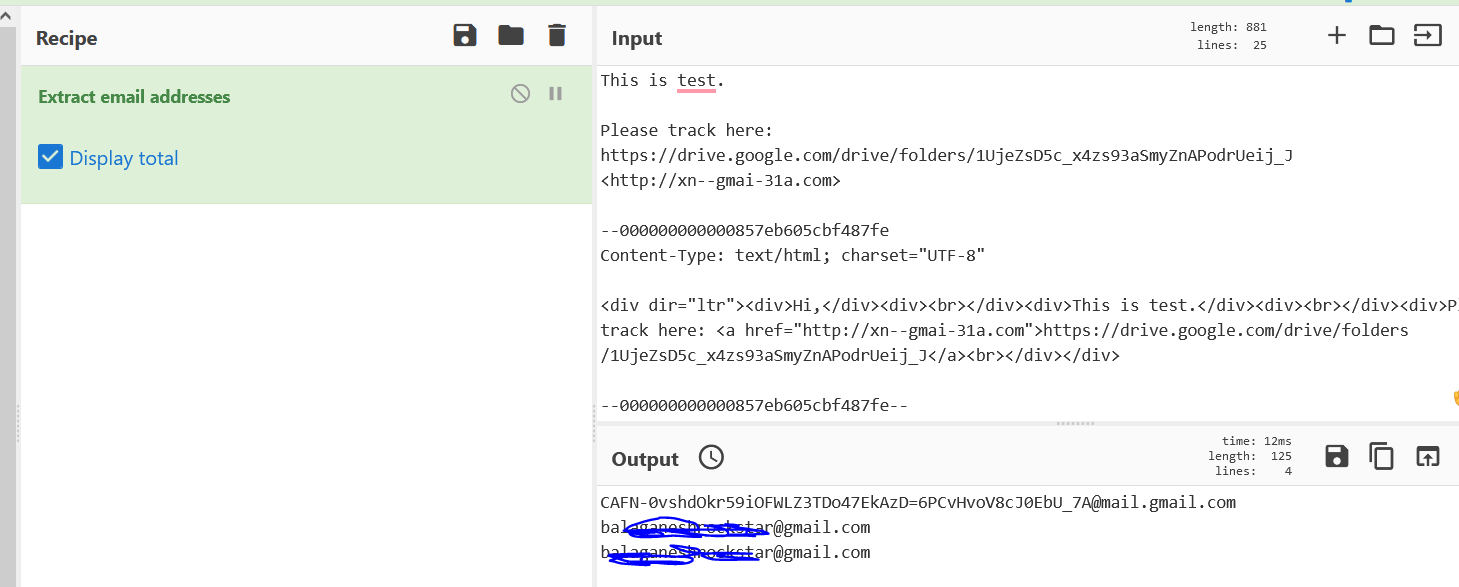
- Now you see the extracted email addrees information in the output section , This is completly fine. Most phishing exercises will be sent out from legitimate email providers only.
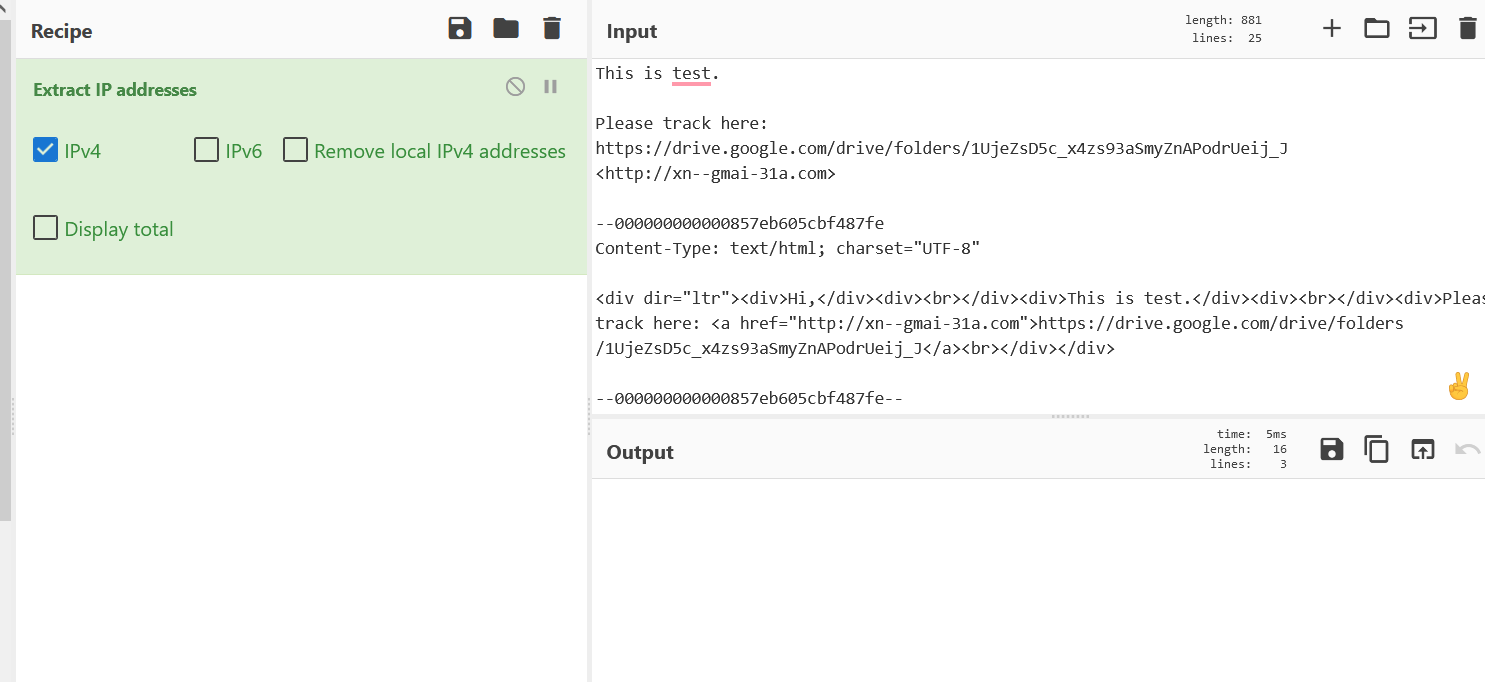
- Above figure shows , Extract IP addresses recipe didn’t providing any IP address information. We will find it out with another ways !
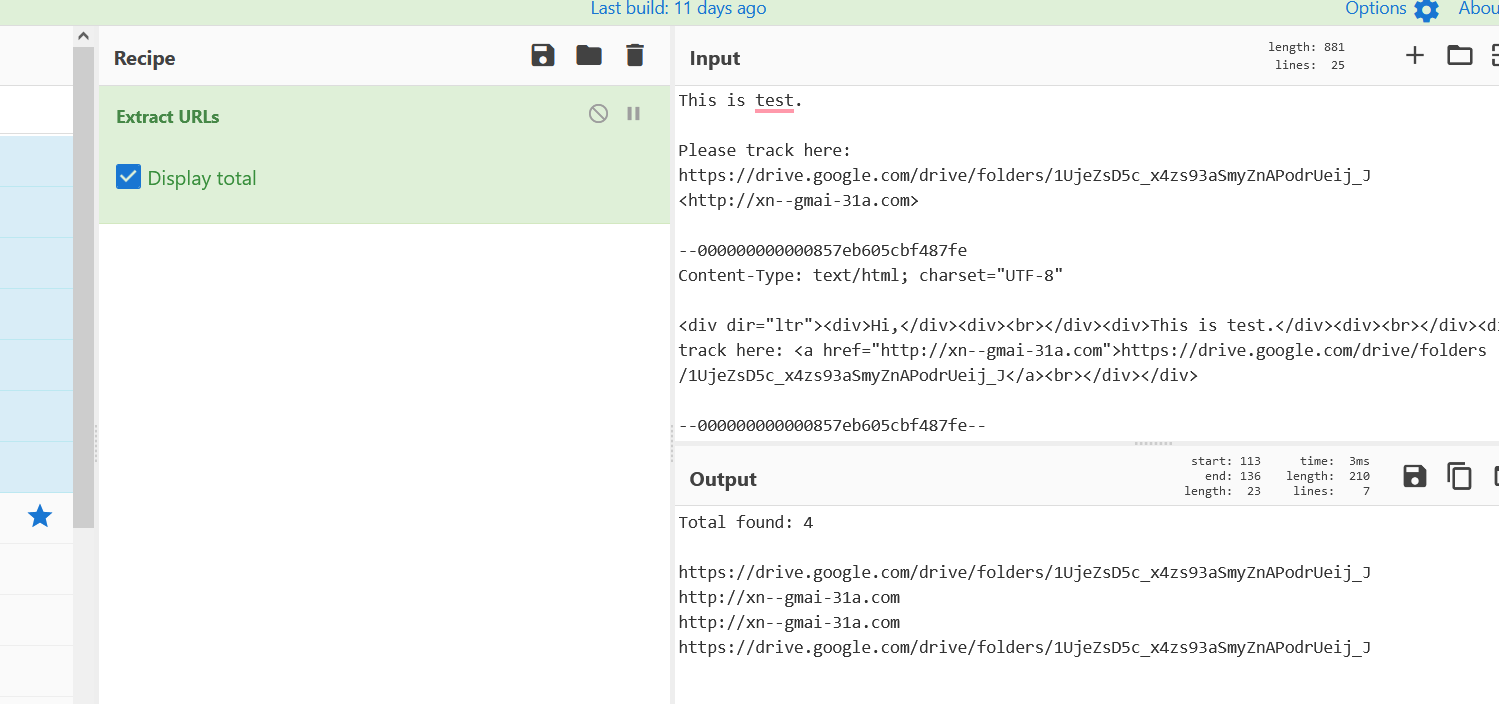
- Above figure shows , Adding Extract URLs recipe. We found interesting items , Punny Code Domains are used and embedded on the email. As are normal user we cant see only the google drive link on the email body.
- Punny Code ? Punny codes are Unicode that converts words that cannot be written in ASCII, like the Greek word for thank you ‘ευχαριστώ’ into an ASCII encoding, like ‘xn--mxahn5algcq2e’ for use as domain names. This can be used for malicious intents also.
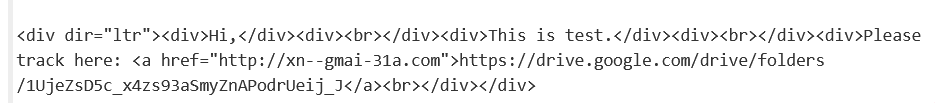
- Above figure shows , Phishing is delivered from the punny code domains “http://xn--gmai-31a.com” , But this is masked and showcased as Google Drive links on email body. Now lets decode the punnycode domains to see the actual domain name.
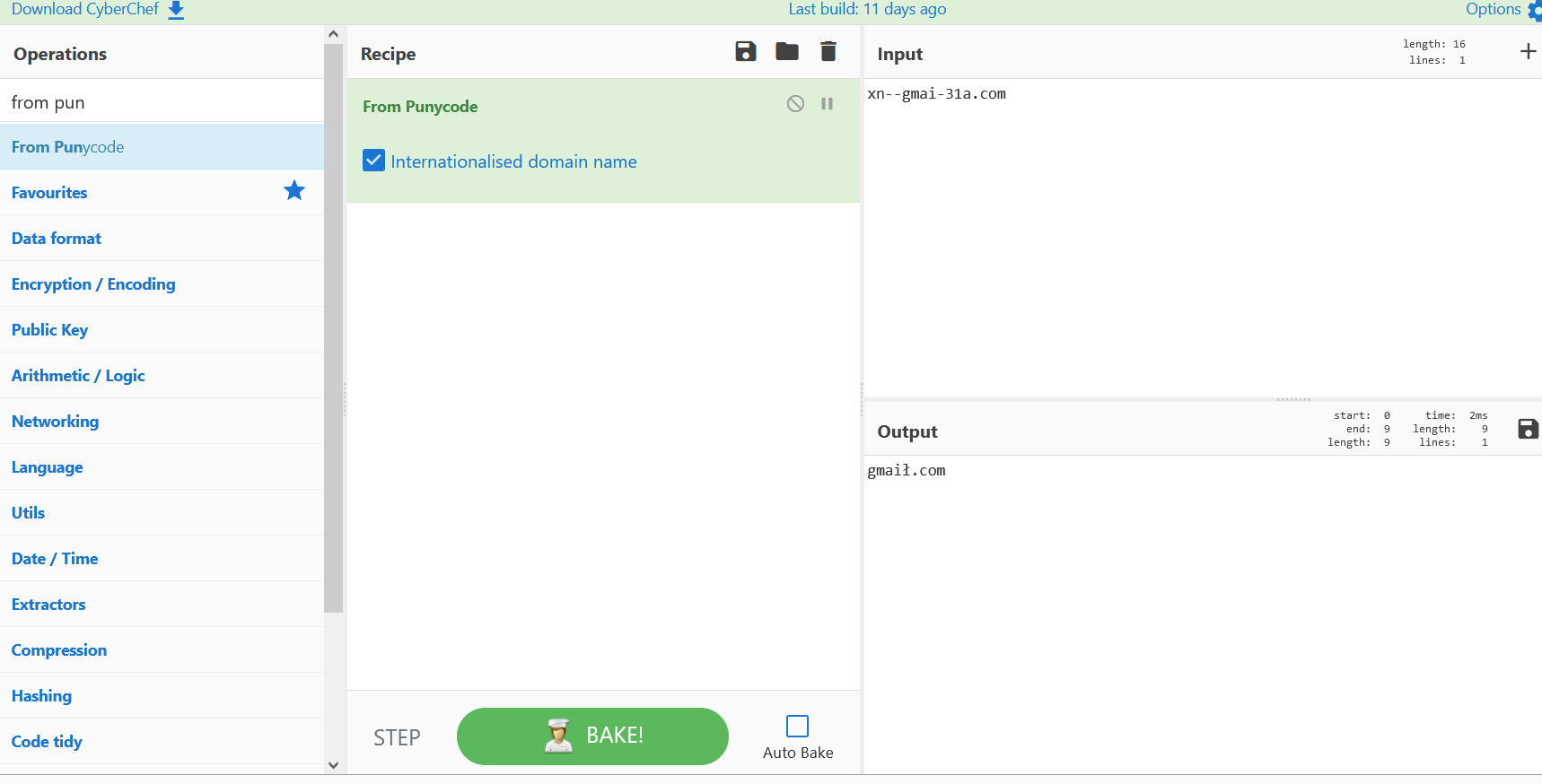
- Above figure shows , Adding the from Punny code recipe decodes the actual domain on the output section. This output section domain will be the real landing page for the user , Post clicking the Google Drive links.
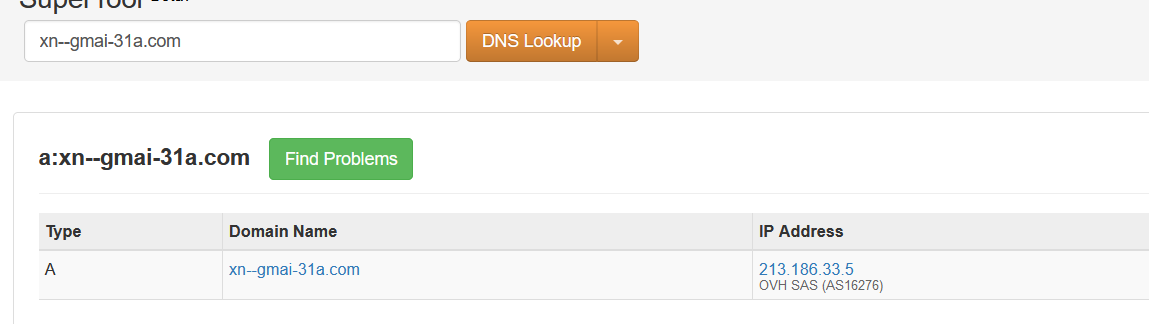
- Above figure shows , Checking the DNS looksups reveals the IP addresses of the domain.
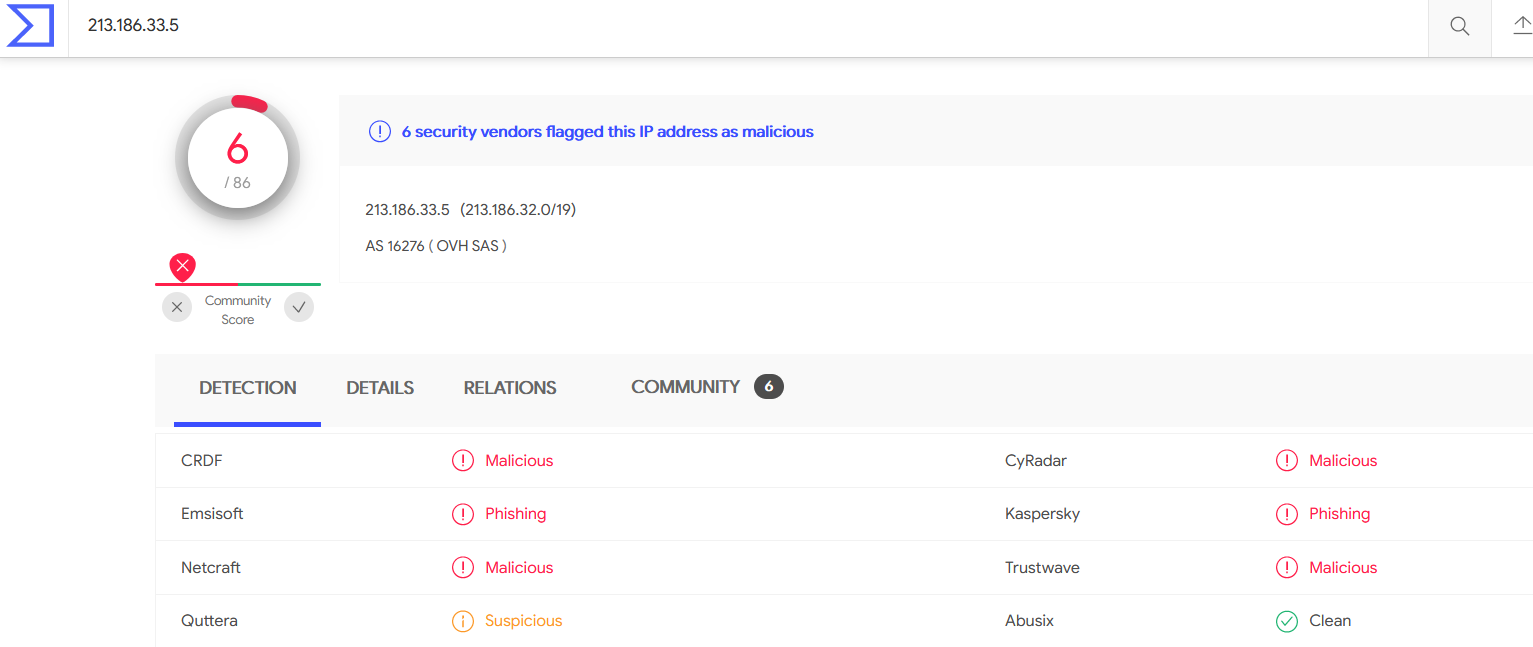
- Checking on the VirusTotal , It is Detected as Malicious & used for Phishing.