In my previous blog post, I demonstrated the process of identifying executable packers and static analysis tools. In this blog, we will explore how to analyze the sample using a powerful Disassembler called IDA Pro.
Also Read: How to Perform Static Code Analysis on Packed Malware ?
IDA Pro, developed by Hex-Rays, is a renowned software program utilized for reverse engineering binary code. As a disassembler and debugger, it enables users to delve into the intricate details of executable files, including executables, shared libraries, object files, and firmware. With its support for diverse processor architectures and file formats, IDA Pro proves to be a versatile tool for code analysis across various platforms.
Let’s explore the built-in features of IDA Pro:
- Disassembly
- Code Analysis
- Debugger
- Processor and File Format Support
- Graph View
- Scripting Interface
- Collaboration and Sharing
Upon launching IDA, you will encounter the initial window, which presents the option to “Disassemble a New File” for opening.
Fig 1: Opening Window
Fig 2: Basic View of IDA Pro
IDA Pro automatically identifies and recognizes the file format of the executable upon opening. Also, it thoroughly analyzes the entire executable file and generates an .idb (IDA database) archive. This archive serves as a comprehensive database containing the disassembled code, analysis results, and other relevant information extracted from the executable.
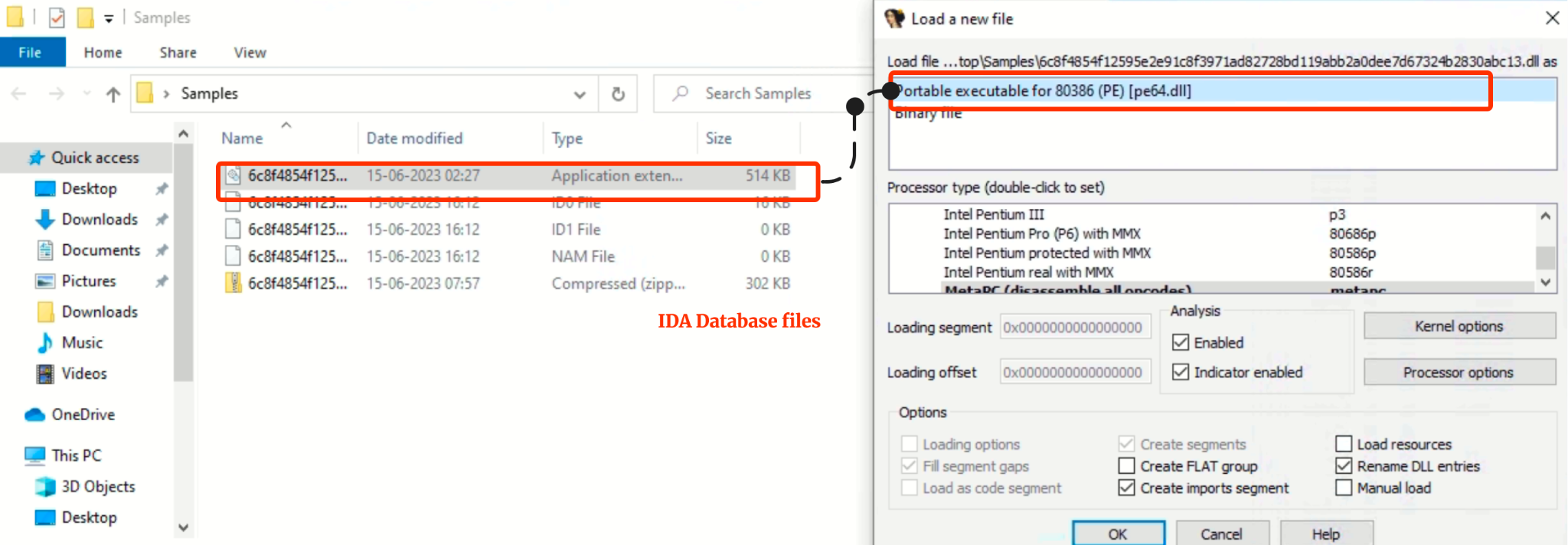
Fig 3: Loading a new file
Within IDA Pro, specific files serve distinct purposes:
ID0: This file contains the contents of the B-tree style database. It stores the actual data and structures used by IDA Pro for analysis, disassembly, and various other operations.
ID1: The .id1 file holds flags that provide descriptions for each program byte. These flags help characterize and identify specific characteristics of the code during analysis.
NAM: The .nam file serves as an index that houses information related to named program locations. It assists in efficiently referencing and accessing named entities within the disassembled code, aiding in the overall understanding of the program’s structure.
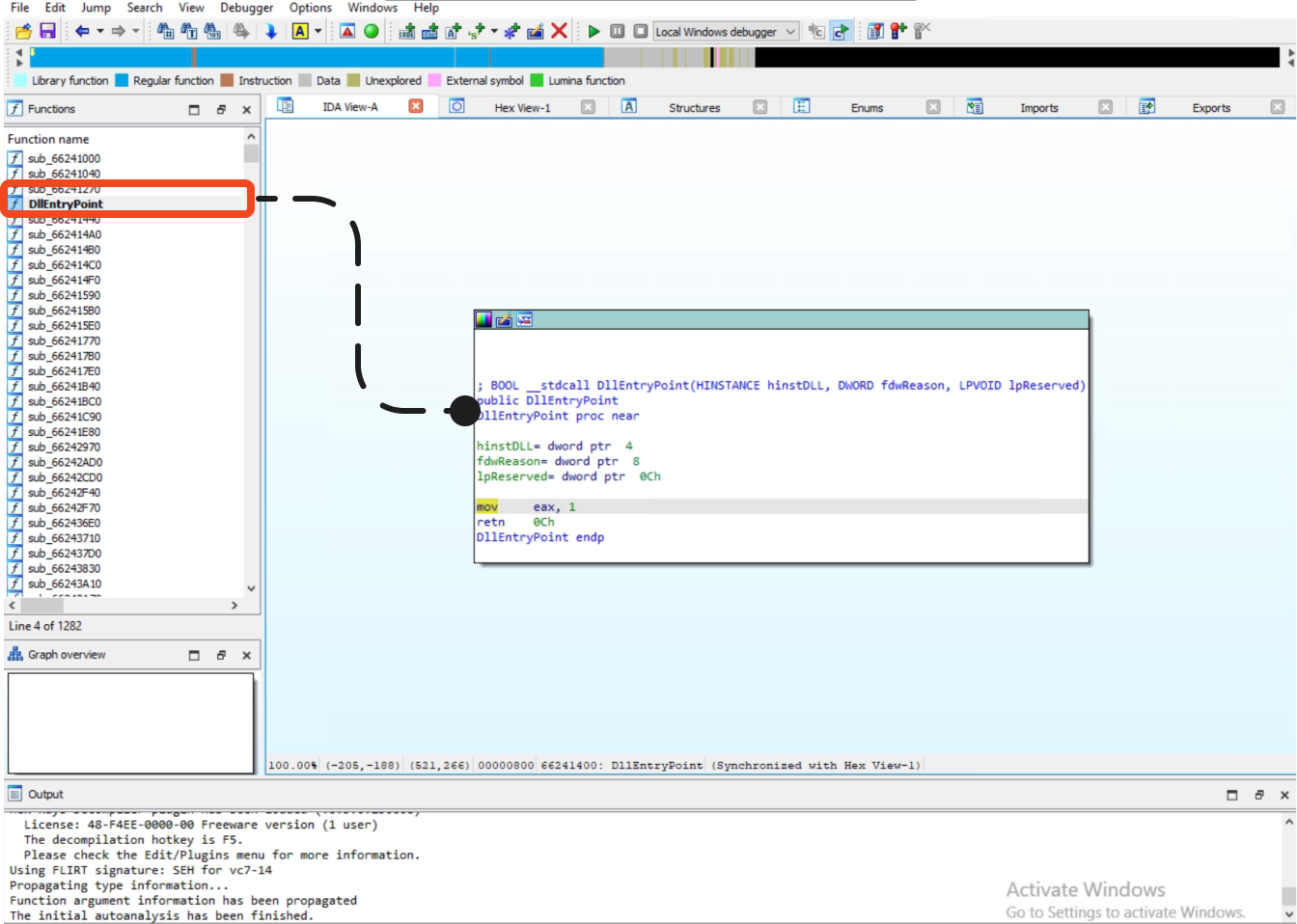
Fig 4: Loaded Sample’s EntryPoint
Also Read: Pestudio: Initial Malware Assessment Made Simple
IDA Pro Interfaces:
Let’s see the important and useful interfaces of IDA Pro.
- IDA View-A
- Hex View-A
- Strings
- Imports
- Exports
- Switches
- Help window
IDA View-A:
IDA View-A represents the primary disassembly view in IDA Pro, showcasing the code disassembly of the program. It presents the disassembly instructions, function boundaries, and control flow of the analyzed binary code. This view provides a comprehensive overview of the program’s assembly instructions, allowing users to navigate, analyze, and understand the functionality and logic of the code.
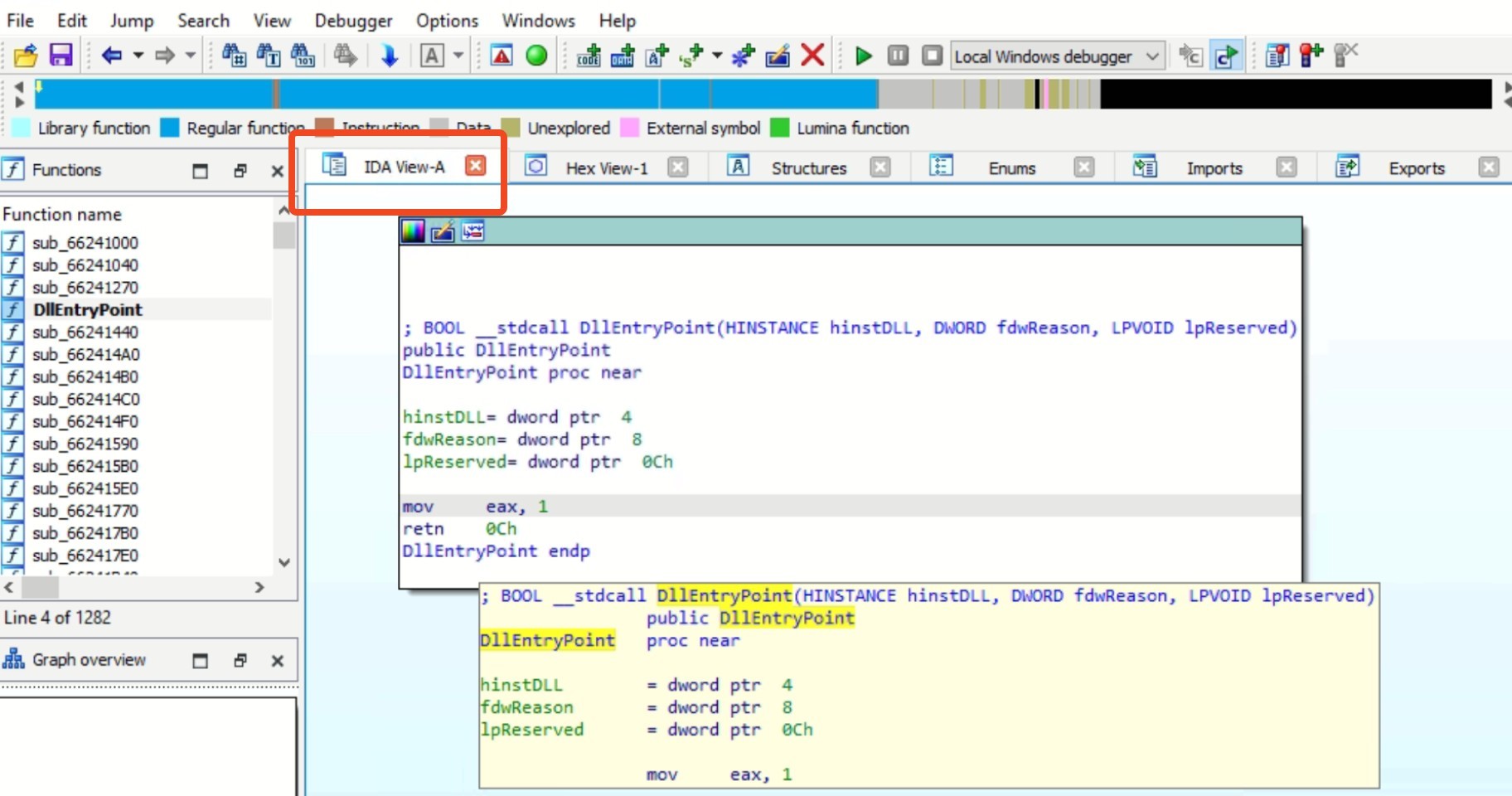
Fig 5: Normal IDA View-A
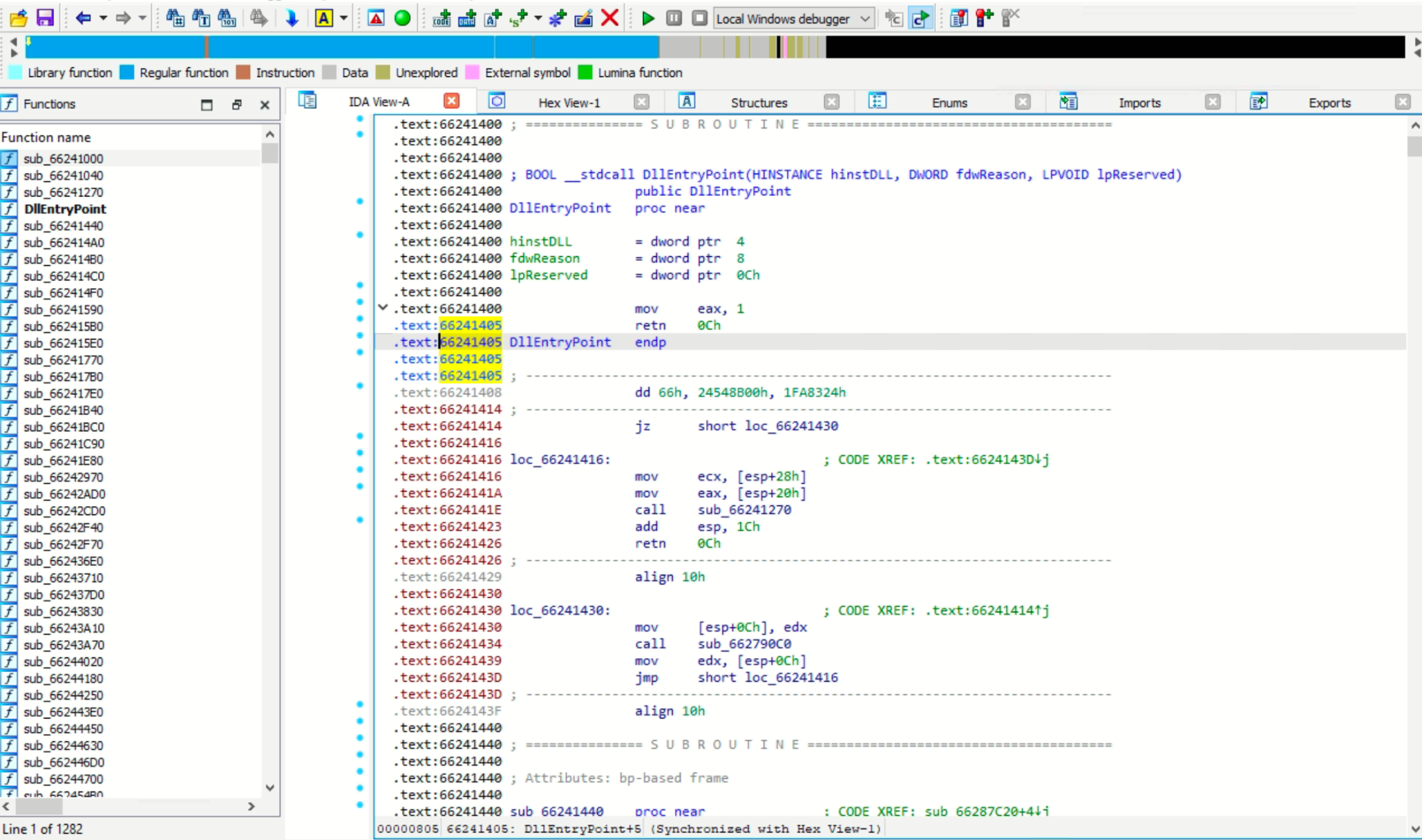
Fig 6: Detailed IDA View
Hex View:
Displays the hexadecimal representation of the program, which easily correlates the hexadecimal representation with the disassembly instructions, facilitating a comprehensive analysis of the program’s binary code.
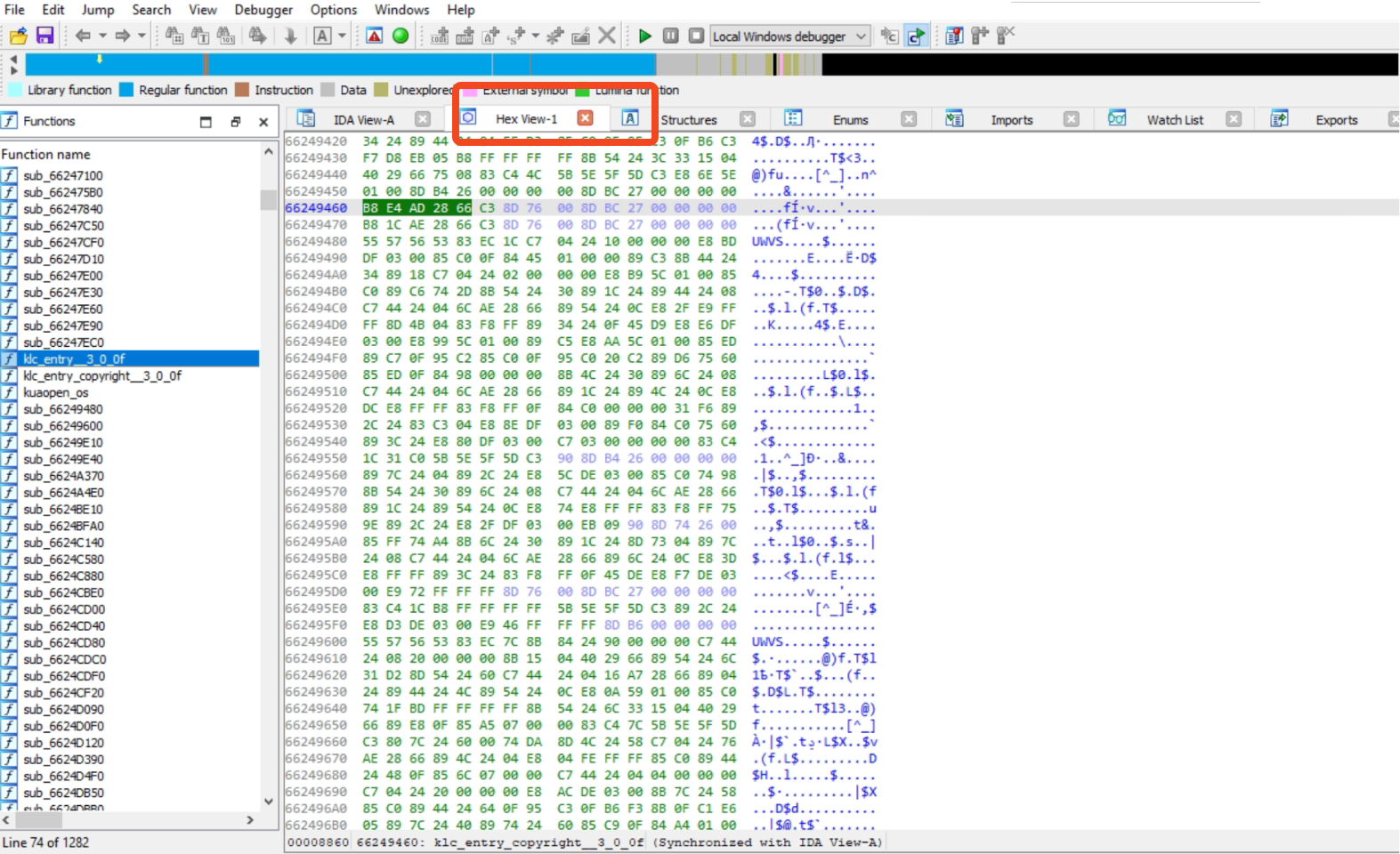
Fig 7: Hex-View Window
String View:
Strings window organizes the extracted strings into a list, allowing users to browse, search, and manipulate them. Each string entry typically includes the string value itself, the address where it was found, and additional contextual information.
The Strings window enables users to view cross-references to strings from different parts of the disassembled code. This feature helps identify how the strings are utilized and provides insights into program functionality.
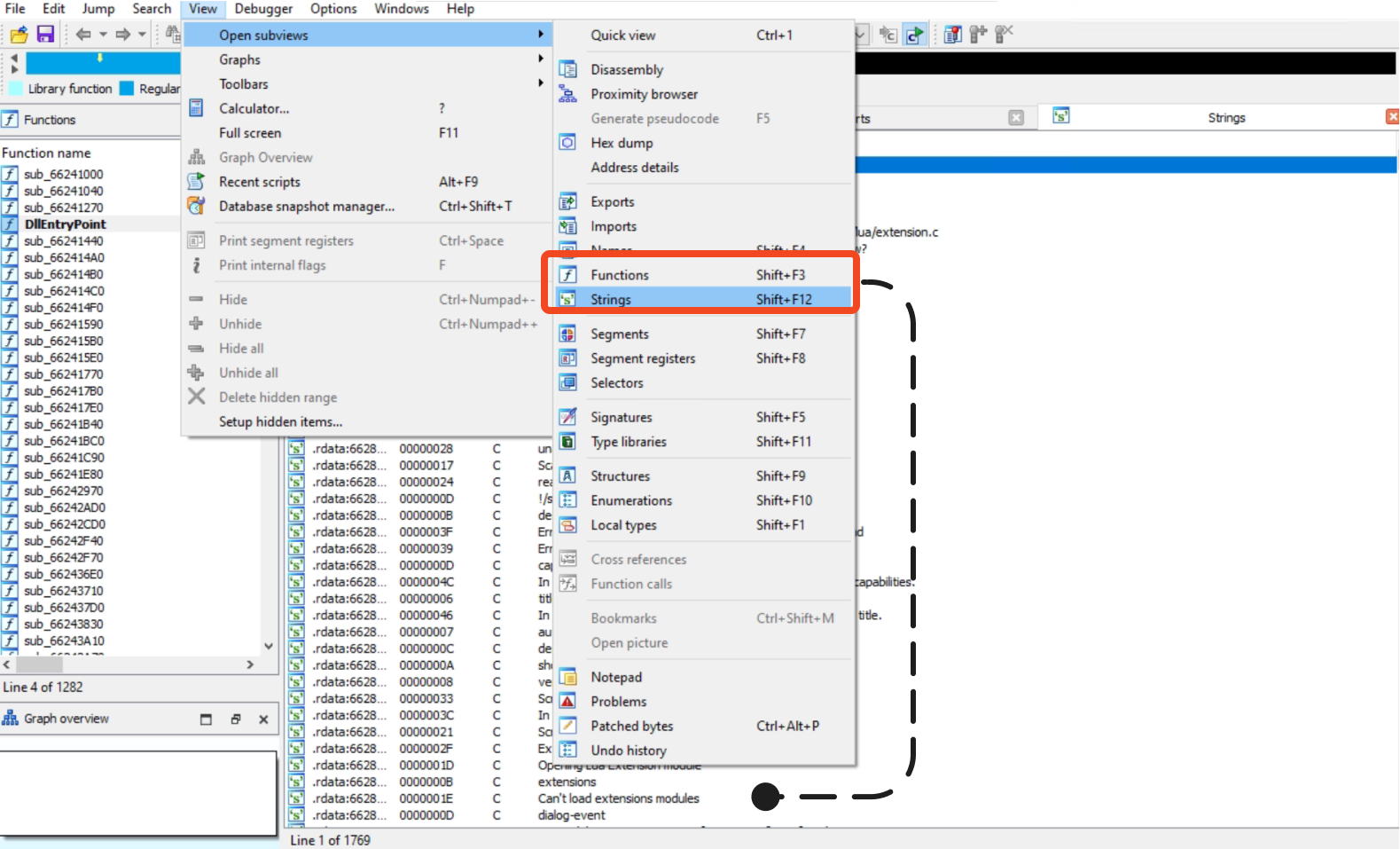
Fig 8: Strings Window
Exports & Imports Window:
Exports: This section displays the functions or symbols exported by the analyzed program. Exported functions are typically accessible to other modules or executables, allowing them to be used as an interface for external components.
Imports: In this section, the window lists the functions or symbols that the analyzed program imports from external libraries or modules. Imported functions are references to functions that the program relies on but are implemented externally.
Fig 9: Export & Import Window
Import Functions:
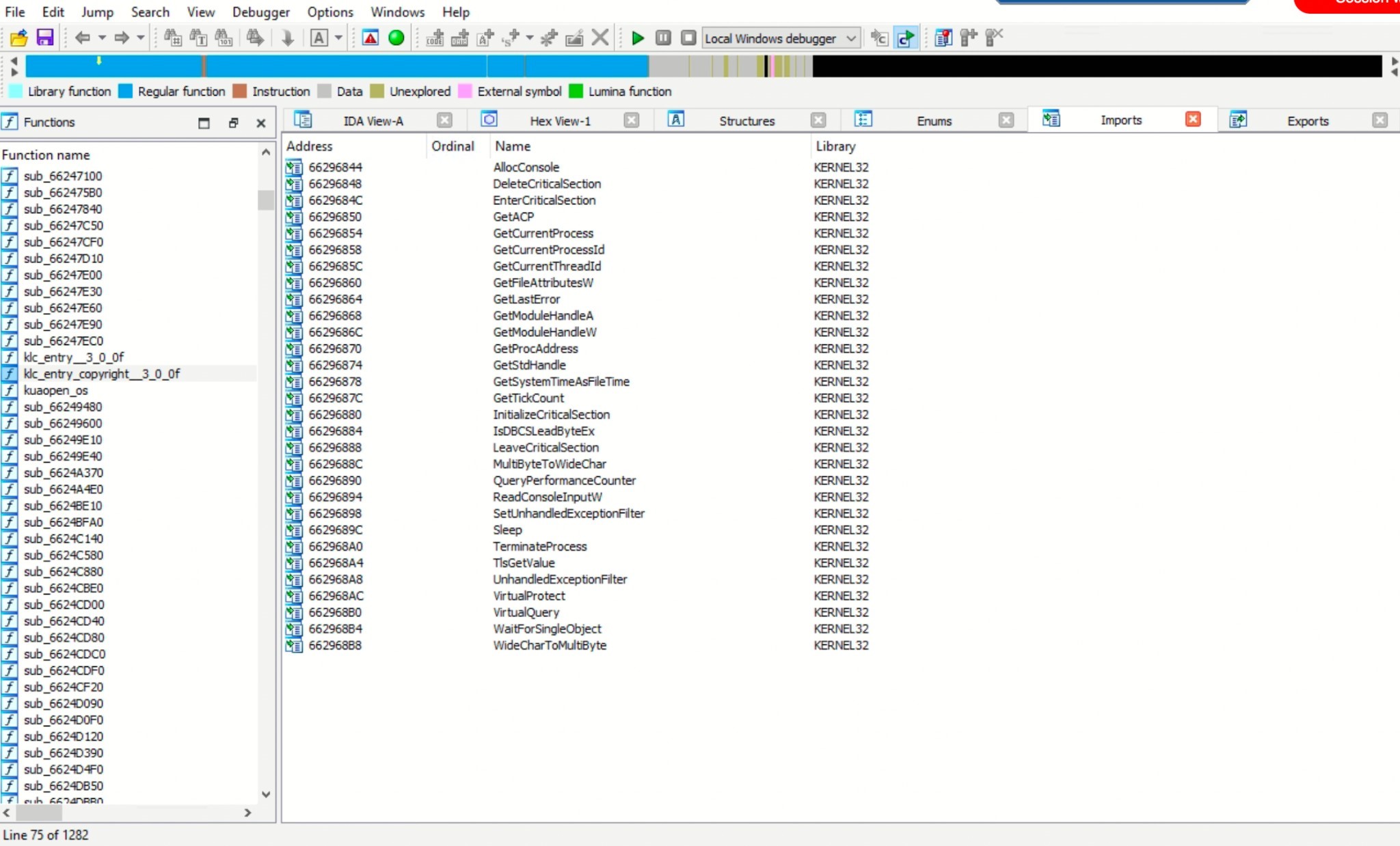
Fig 10: Import Functions
Export Functions:
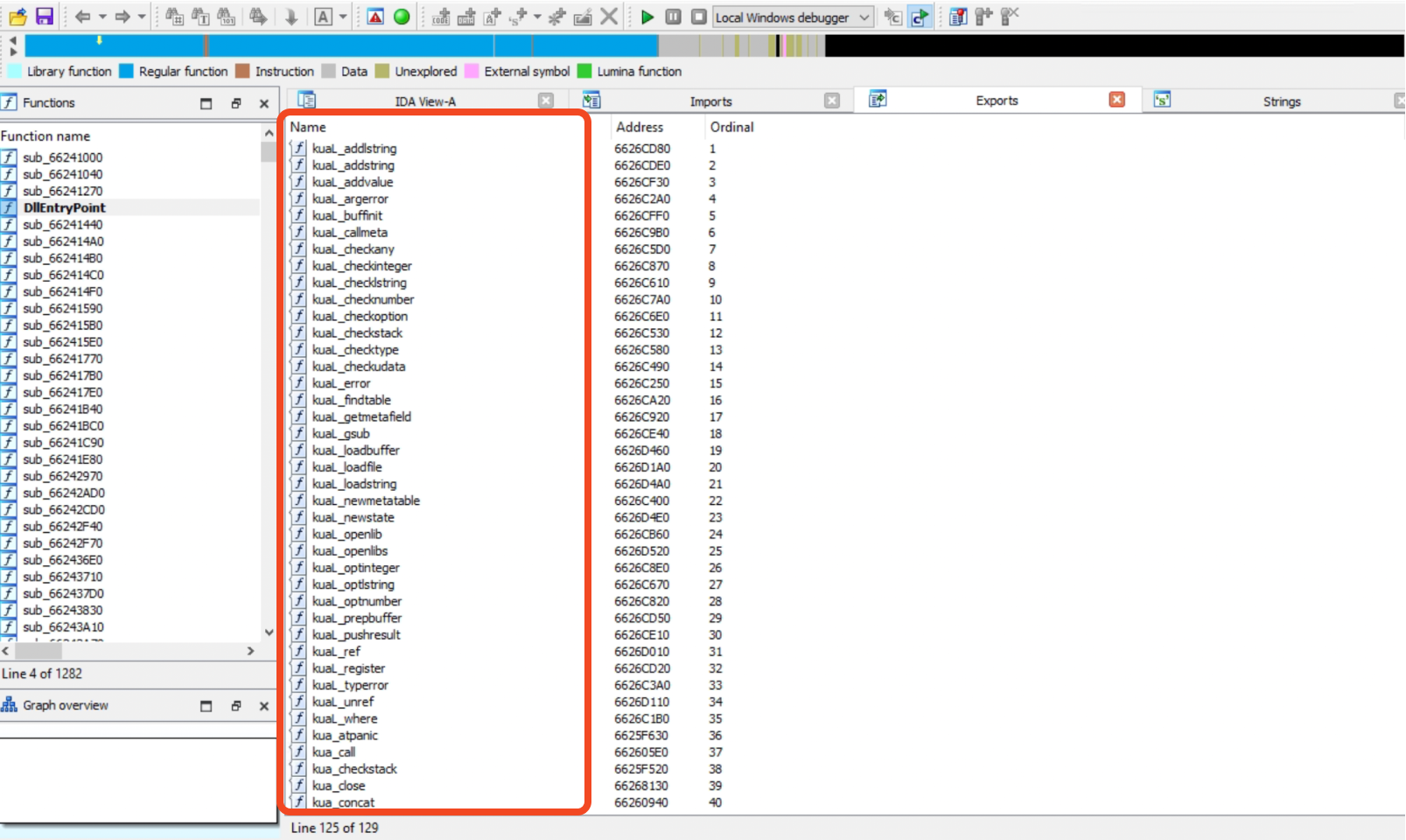
Fig 11: Export Functions
Switch Window:
Fig 12: Switching Shortcut Tiles
Help Window:
Fig 13: Help Window
Final Thoughts:
In short, IDA Pro is a powerful and versatile tool for reverse engineers, security researchers, and software analysts. Its robust features, such as disassembly, code analysis, debugging, and support for various processor architectures and file formats, enable in-depth analysis and understanding of binary code.
While this overview provides a glimpse into the capabilities of IDA Pro, security professionals can continue to expand their knowledge, skills, and application of this powerful tool, unlocking its full potential for complex security challenges.
Keep learning and be on the lookout for my next blog!! PD



































