Cryptographic hashes are used to determine the integrity of files. We have come across hashing algorithms like MD5, SHA256, SHA512, etc. Simple principle of Attackers/ Malware authors is to change the file content ,but the Malware functionality remains the same. To detect such activates , we have to look around SSDEEP hash.
What is SSDEEP hashing?
SSDEEP is the context triggered piecewise hashing (CTPH) technique to identify the files with previous files,I.E to find the duplicate content .This SSDEEP can be used effectively to compare the content similarity searches with existing well-known malware database.Most of the Antivirus providers use this fuzzy technique to find a new malware.
Example:
Normal text File: My new Pet name is ransomware.
SSDeep hash Detection: My new Pet name is ransomware & virus
Highlighted text indicates that ssdeep is capable to find the existing values on the previous sample and Now the word “& virus” is sometimes new in my text ,which needs to be analyzed.
Practical approach as offender and defender to understand things better.
Offender Thoughts :
Assume a scenario that you are a Attacker with good programming background to reverse an existing malware binary and rewrite additional malicious codes to change the integrity ( HASH ) and do some code obfuscation. Your task is to infect a well known organization ( ABC ) which has less security practices in place.
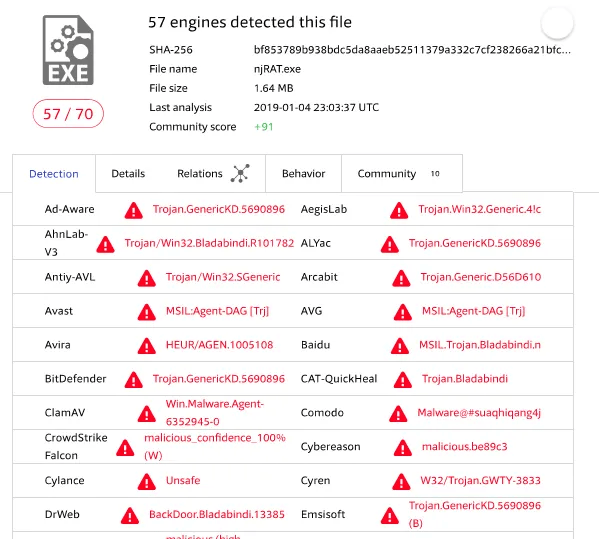
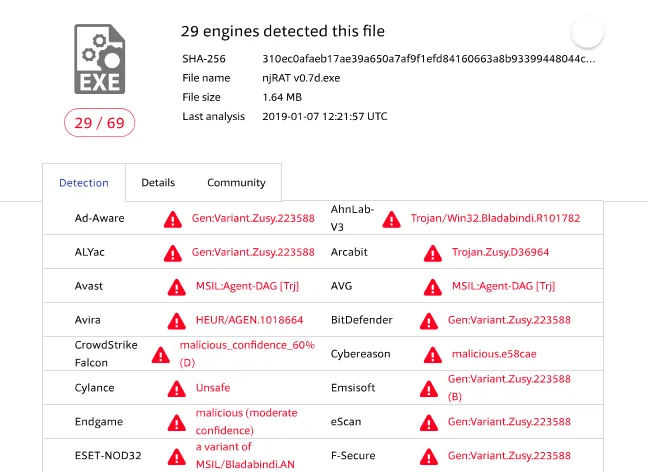
You are given a NJRAT Trojan Which is also called a RAT (Remote Access Trojan) which controls a compromised machine. You can be easily get caught with corporate AV/EDR’s as this is well known Trojan.Below VirusTotal result shows 57/70 AV vendors says this has Malware Agent.
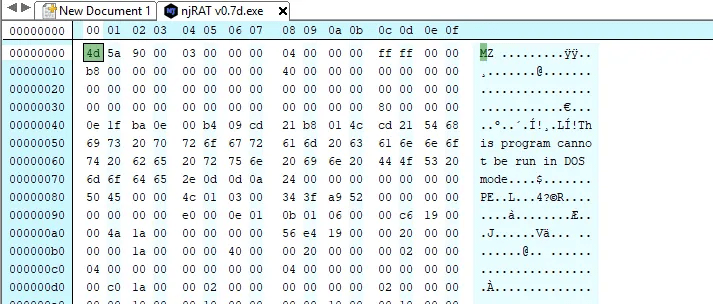
Now attacker has opened a well known malware in Hex editor and changed some specific lines without affecting the software functionality.
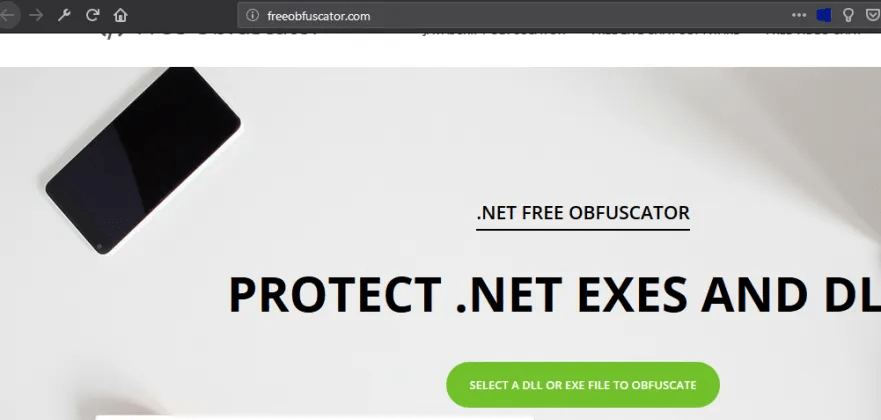
Using software code obfuscation tools to obfuscate the existing codes and giving tough times to antivirus vendors to detect this sample as virus or legit.
After Obfuscation
Now our malicious code is ready for delivery and 29/69 Antivirus Vendors says this as malware ,My target Av vendor says this as not a malware.
Post Exploitation , Attacker has gained some confidential files from ABC organization and later got detected with behavior analysis from EDR. But still goal is accomplished from attackers perspective.
Defender Thoughts :
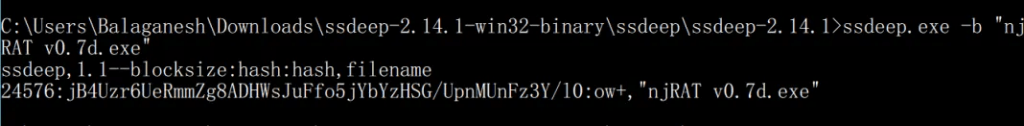
AV vendors will have a list of existing well-known malware and its ssdeep hash. Here I have calculated the SSDEEP hash for the original file njRAT v0.7d.exe ( Before obfuscation ). Context triggered piecewise hashing ( CTPH ) is up and ready now.
Compare the Obfuscated executable with SSDEEP hash
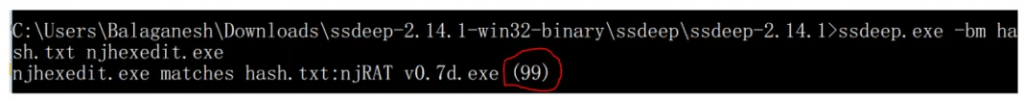
When we compare the obfuscated file with existing malware ssdeep file hashes , It is found that 99% of the content is matched with an existing malware sample. Hope now we can mark this unknown file as malicious.
Happy Hunting !