Introduction:
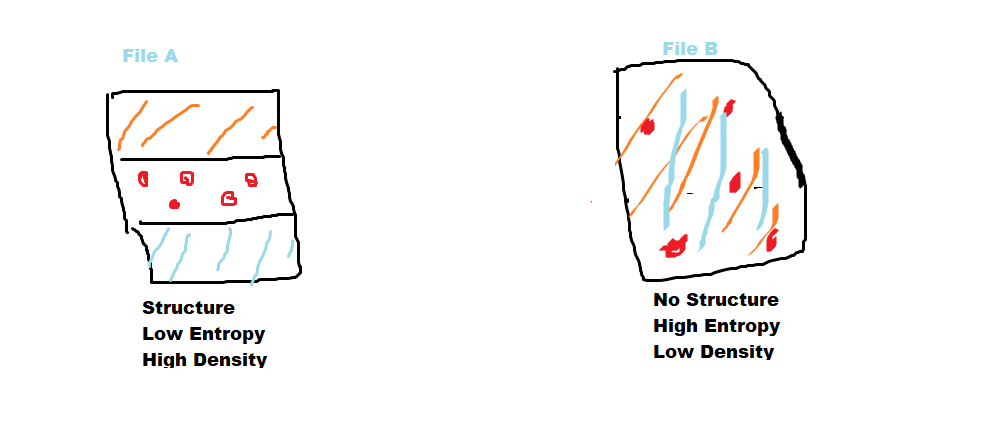
Densityscout calculates the density ( like entropy ) for files of any file system and makes analysts quickly find the packed malware in the potentially infected machine. It was written by Christian Wojner. In general, a normal file will have a proper structure, Low entropy, and High density, But abnormal malware packed files structure won’t be normal, there will be high entropy and low density.
Therefore it takes advantage of the typical approach of malware authors to protect their “products” with obfuscation like run-time-packing and encryption.
What Does DensityScout Do?
DensityScout’s main focus is to scan the desired file-system-path by calculating the density of each file to finally print out an accordingly descending list. Usually, most Microsoft Windows executables are not packed or encrypted in any way which throws the hits of malicious executables to the top of the list where one can easily focus on.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Usage / Syntax
DensityScout is a command-line based tool
DensityScout (Build 45)
Author: Christian Wojner, CERT.at
Syntax: densityscout [options] file_or_directory
options: -a ………….. Show errors and empties, too
-d ………….. Just output data (Format: density|path)
-l density …… Just files with density lower than the given value
-g density …… Just files with density greater than the given value
-n number ……. Maximum number of lines to print
-m mode ……… Mode ABS (default) or CHI (for filesize > 100 Kb)
-o file ……… File to write output to
-p density …… Immediately print if lower than the given density
-P density …… Immediately print if greater than the given density
-r ………….. Walk recursively
-s suffix(es) … Filetype(s) (i.e.: dll or dll,exe,…)
-S suffix(es) … Filetype(s) to ignore (i.e.: dll or dll,exe)
-pe …………. Include all portable executables by magic number
-PE …………. Ignore all portable executables by magic number
Note: Packed and/or encrypted data usually has a much higher density than
normal data (like text or executable binaries).
Modes: ABS … Computes the average distance from the ideal quantity for each
byte-state according to the overall byte-quantity of the
evaluated file.
Typical ABS-density for a packed file: < 0.1 Typical ABS-density for a normal file: > 0.9
CHI … Just the same as ABS but actually squaring each distance.
Typical CHI-density for a packed file: < 100.0 Typical CHI-density for a normal file: > 1000.0
Also Read: Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
Suspicious PE file Scan
DensityScout to only select PE (Portable Executable) files by checking them against the magic number (“MZ”) of portable executables. Below scan is packed or encrypted malware files with the value are less than”0.1″ which denotes low density and something abnormal files structures was observed. Here we have initiated a scan on the windows downloads folder to hunt suspicious files from the internet.
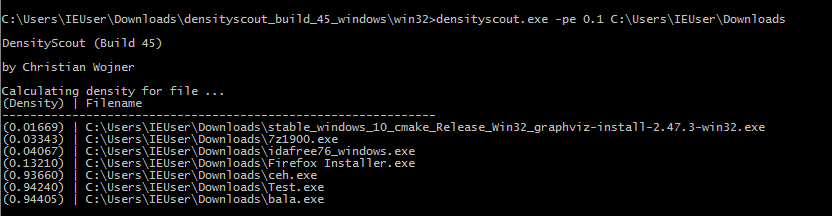
The above figure shows, Scan was completed successfully and found some obfuscated malicious files on the user disk. Here we will upload the file “Test.exe” to virustotal to check the scan accuracy.
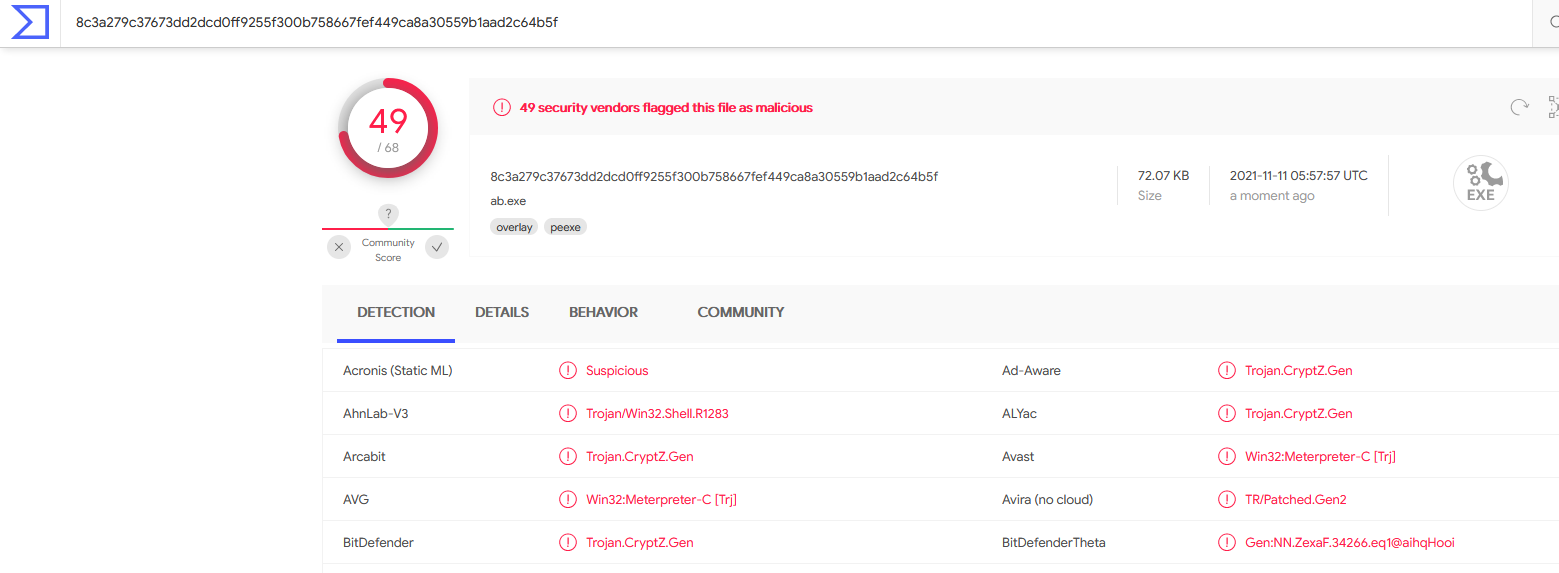
The above figure shows the file is found to be a Trojan.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Scan Other File Formates
DensityScout is not limited only to PE files, We have a good option to scan other files’ structure and density checks too. below scan we have initiated for list of files to hunt, I.E cpl ,exe,dll etc , Options -p Immediately print if lower than the given density , Here we have given 0.1 density.
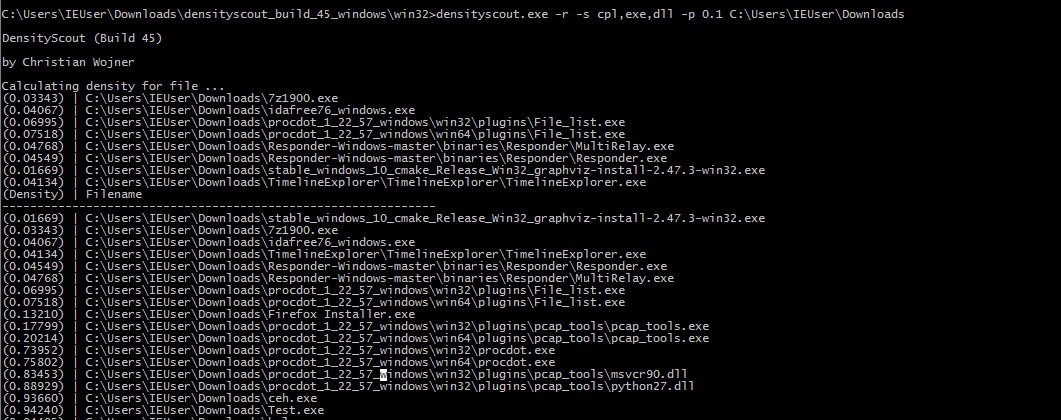
The Above figure shows , Densityscout has completed the scan and found the list of other malicious files on the disk. You can download the tool by clicking here.
Also Read: Latest Cyber Security News – Hacker News !
Conclusion
DensityScout is a good tool available for both Linux and windows and isn’t’ only good for finding malicious executables – it can also be used to find packed or encrypted data containers and the like!
Happy Hunting !!!