Security researchers at Zscalar ThreatLabz have been closely monitoring the activities of a threat actor which targets users in various US-based organizations with malicious voicemail-notification-themed emails in an attempt to steal their Office365 and Outlook credentials.
In this new instance of the campaign, the threat actor has targeted users in US-based organizations in specific verticals including software security, US military, security solution providers, healthcare / pharmaceutical, and the manufacturing supply chain.
Key points
- Voicemail-themed phishing campaigns continue to be a successful social engineering theme used by this threat actor to lure victims in opening a malicious attachment.
- Multiple key industry verticals in the US such as military, software security vendors, healthcare, pharmaceuticals, and the manufacturing supply chain were targeted by this threat actor.
- The goal of the threat actor is to steal credentials of Office365 and Outlook accounts, both of which are widely used in large enterprises.
- A CAPTCHA is used by the threat actor to guard the final credential phishing page from automated URL analysis algorithms.
- Each URL is specifically crafted for the targeted individual and the targeted organization.
Attack chain
The attack flow involves a voicemail-themed notification email sent to the victim. The email contains an HTML attachment which, when opened, will redirect the user to a credential phishing site. The goal of the threat actor is to harvest Office 365 credentials of the victim.
The email theme is focused on a voicemail notification that tells the victim they have a missed voicemail, prompting the user to open the HTML attachment. This social engineering technique has worked successfully for the threat actor in previous campaigns.
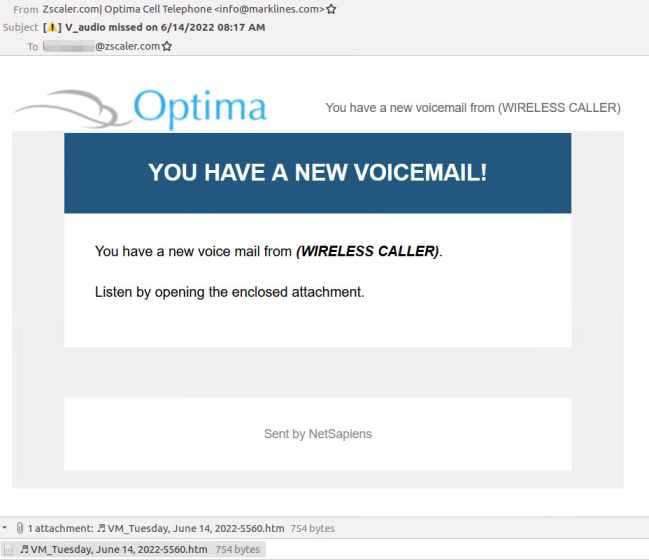
Analysis of the email headers shows that the threat actor leveraged email servers located in Japan.
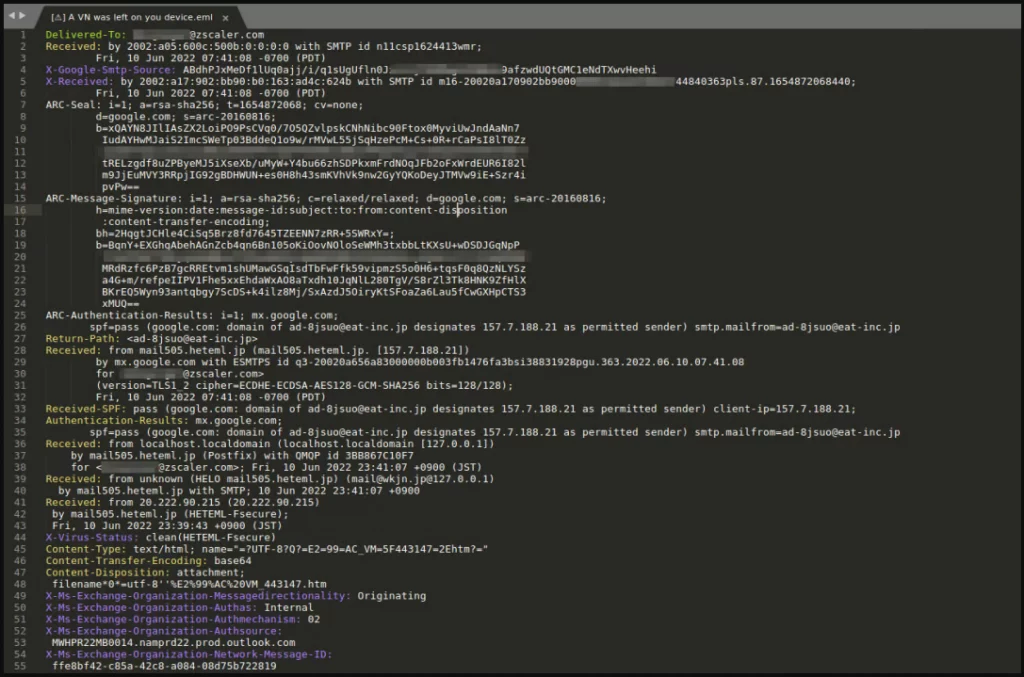
HTML attachment analysis
For the purpose of analysis, we will consider the HTML attachment with the MD5 hash: dd0ddbc951de5cad9c8ace516c514693
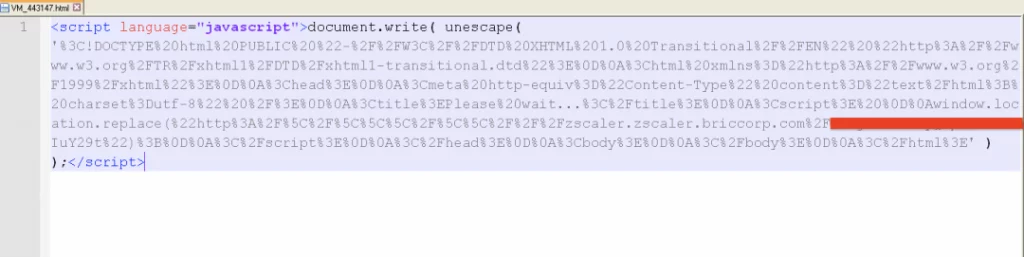
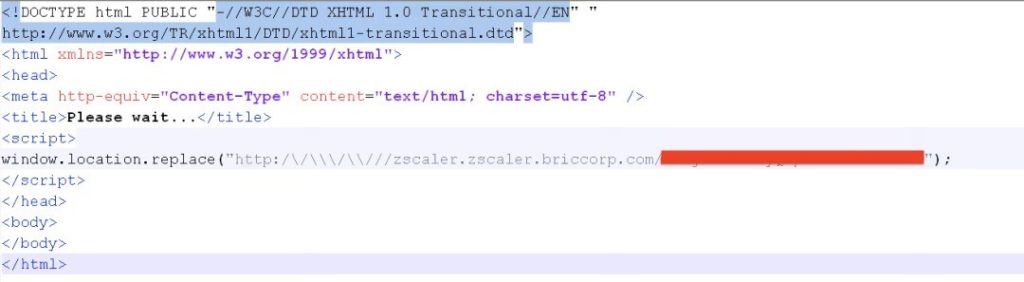
The above shows the resulting code after deobfuscation.
URL analysis
[Stage-1 URL] – Redirector
The URL inside the HTML attachment is a redirector URL that redirects the user to the final credential phishing page.
In each instance of the attack, the URL followed a consistent format which included the name of the targeted organization as well as the email address of the targeted individual. Figure 6 below highlights the format.
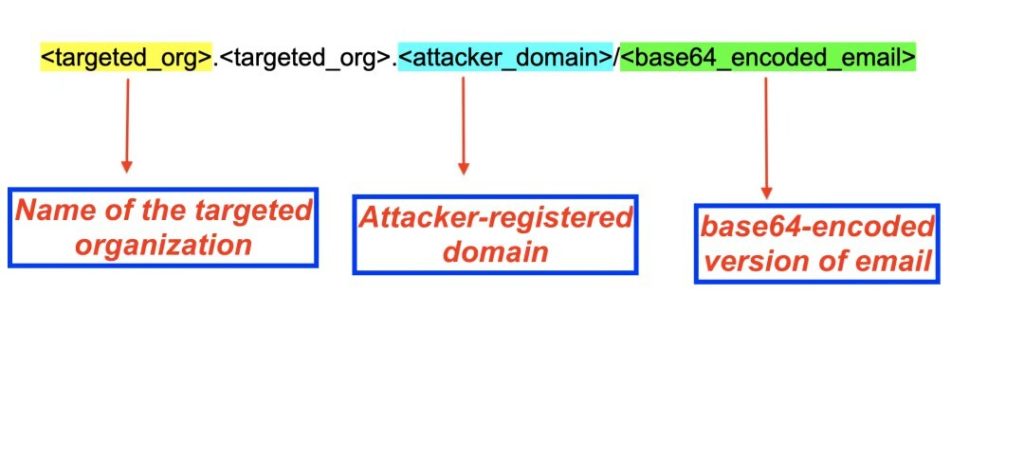
For instance, when an individual in Zscaler was targeted, the URL used the following format:
zscaler.zscaler.briccorp[.]com/<base64_encoded_email>
Since the format of the URL gives away critical information about the target, we used that information from our collected telemetry to enumerate the list of targeted organizations and individuals.
Based on the analysis of this telemetry, we can conclude with a high confidence level that the targets chosen by the threat actor are organizations in the US military, security software developers, security service providers, healthcare/pharmaceutical and supply-chain organizations in manufacturing and shipping.
It is important to note that if the URL does not contain the base64-encoded email at the end; it instead redirects the user to the Wikipedia page of MS Office or to office.com.
[Stage 2 URL] CAPTCHA check
The Stage 1 URL in the HTML attachment will redirect the user to the Stage 2 URL which requires the user to solve a Captcha before presenting the actual Office credential phishing page.
For Captcha, it uses the Google reCAPTCHA technique. This helps the threat actor evade automated URL analysis tools.
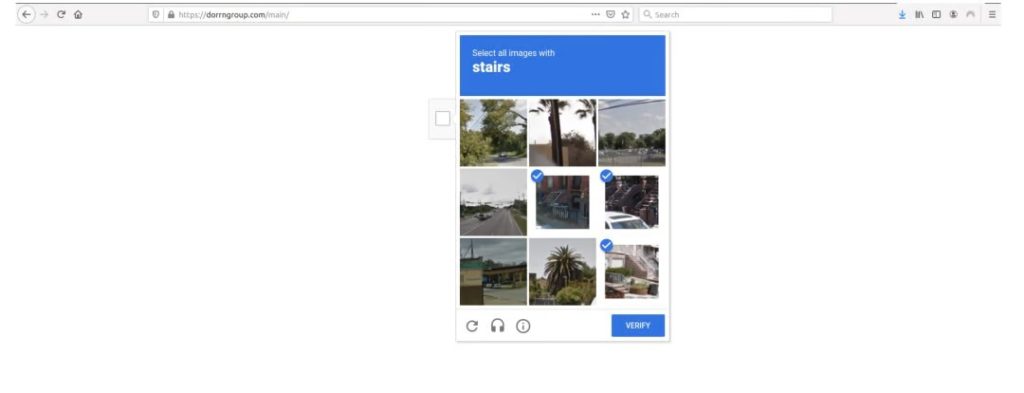
[Stage 3 URL] – Credential phishing page
Once the user solves the Captcha successfully, they will be redirected to the final credential phishing page which attempts to steal the Office 365 credentials of the user.
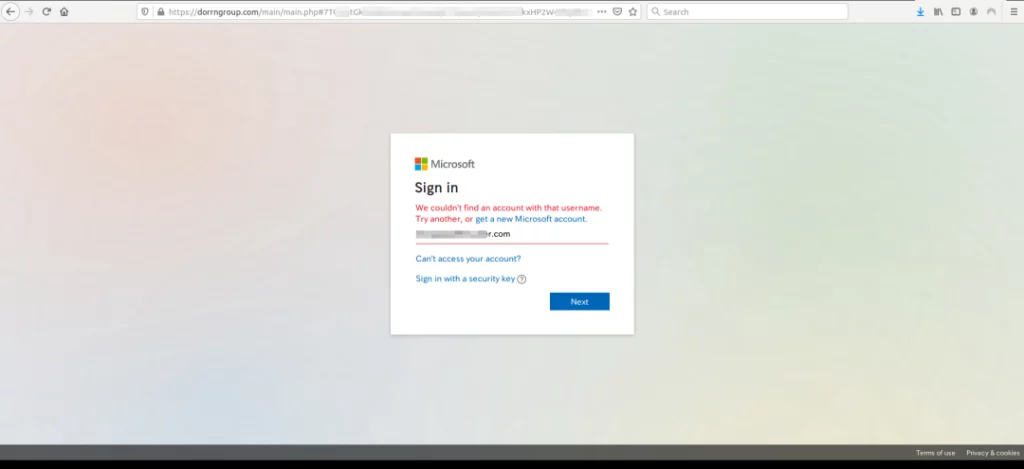
Zscaler’s Detection
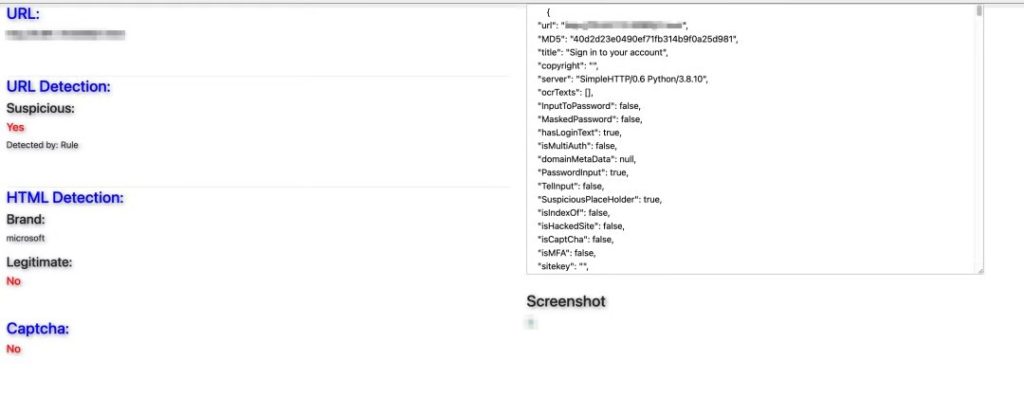
Indicators of compromise (IOCs)
# attacker-registered domains
briccorp[.]com
bajafulfillrnent[.]com
bpirninerals[.]com
lovitafood-tw[.]com
dorrngroup[.]com
lacotechs[.]com
brenthavenhg[.]com
spasfetech[.]com
mordematx[.]com
antarnex[.]com
Voicemail-themed phishing campaigns continue to be a successful social engineering technique for attackers since they are able to lure the victims to open the email attachments. This combined with the usage of evasion tactics to bypass automated URL analysis solutions helps the threat actor achieve better success in stealing the users’ credentials.
Source/Credits: https://www.zscaler.com/blogs/security-research/resurgence-voicemail-themed-phishing-attacks-targeting-key-industry



































