GRR is an incident response framework that is mainly focused on remote live forensics. It is based on client-server architecture, so the agent should be installed on the targeted system.
Server feature:
A fast and simple collection of hundreds of digital forensics artifacts.
Client feature:
Detailed monitoring of client CPU, memory, IO usage, and self-imposed limits. Supports cross-platform os.
Installation:
First of all, we need to install the GRR server. Download Here
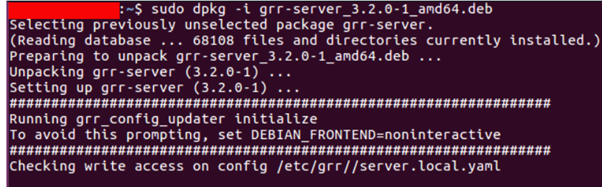
After installation has been completed, you can access the Admin UI.
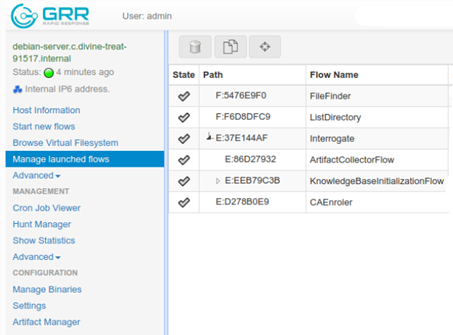
Now download the agent package and install that agent on the client’s machine. As you can see above the Google GRR client will automatically call back.
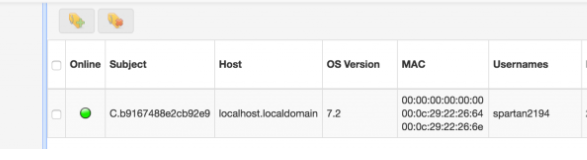
All our client-server setup is done, It’s time to start our live remote forensics.
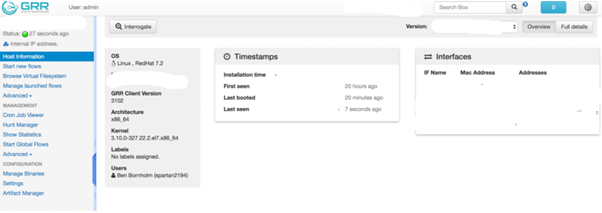
- Host Information:
In order to start interacting with the client, firstly we need to get the details of the client machine. In this host information, you can see Hostname, Mac address, IP address, User, Label, Time of Last Update date.
Also Read : Latest Cyber Security News – Hacker News !
2. Start new Flows:
When trying to deal with thousands of clients at the same time, it might hoarding many unneeded resources. So to avoid this problem, flows were created. Flows are server-side code entities that call client-side actions.
In inflows, you may get the process list, Network details, Registry details, File types, Memory details of that particular client system.
For Example, if you want to get the Network details of the client, Click start new flows–>Network–>Netstat.
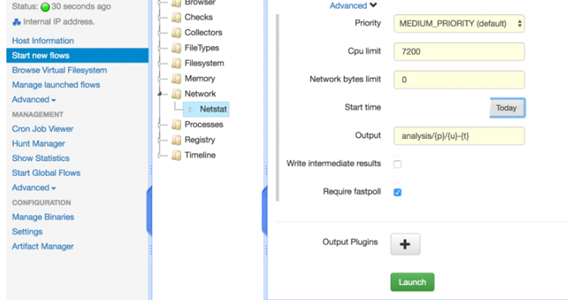
When the flow completes, this is the output of the results.
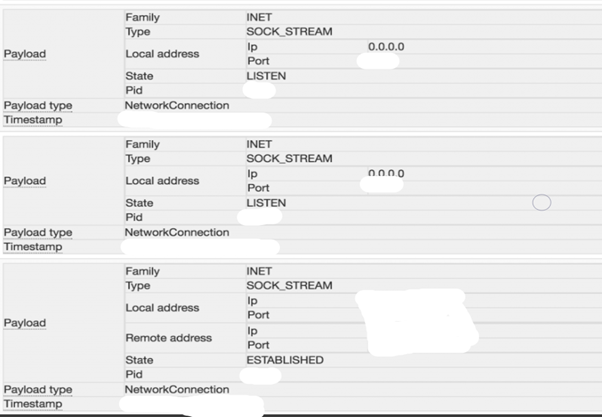
3. Virtual File System:
GRR server saves the client-side file system when every time collects the forensics information from the client.It is called as a virtual file system.
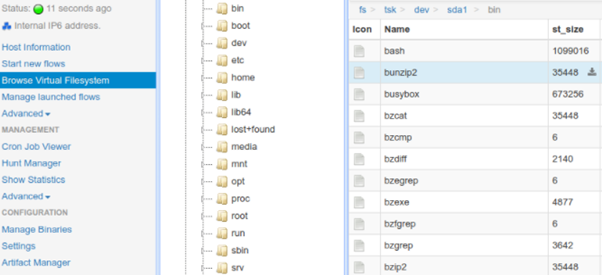
4. Manage Launched Flows:
This tab is used to see the progress of the flow(point 2)
5. Cron Job Viewer:
Cron Job is used for scheduling tasks to be executed sometime in the future. Same as the definition, GRR also has a few cron jobs that run periodically to clean up and maintenance tasks. You can also use a cron job for periodical hunts.
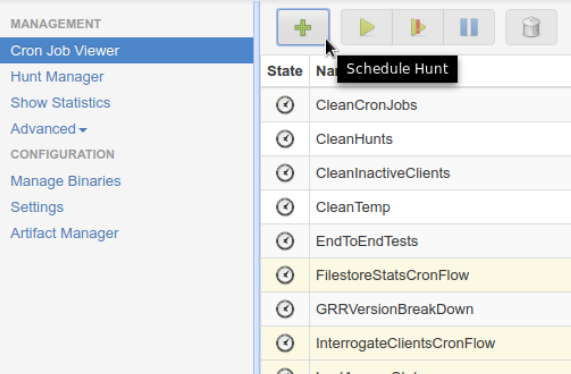
Also Read: Threat Hunting using Proxy Logs – Soc Incident Response Procedure
6. Hunt Manager:
If we found anything valuable by using the hunt rule in one client, this hunt manager helps to do the same on thousands of clients at the same time.
7. Artifacts:
The goal is to describe the artifacts precisely enough and to collect information without user input. They built a framework to describe forensic artifacts that allows them to be collected and customized quickly using GRR.
Requirements
- Ubuntu server
- Recommend > 1GB RAM
- Some clients to talk to the server. OSX, Windows and Linux agents are supported.



































