Ransomware attacks can affect everyone. It starts from small businesses to giant corporates. Without a doubt, ransomware is a danger to organizations all over the world today. With the rise of cryptocurrencies like Bitcoin, ransomware attacks got popular.”It’s crucial for organizations to stay vigilant and implement robust cybersecurity measures, including choosing the best crypto trading platform for secure transactions.
What is a Ransomware?
Ransomware is a kind of malicious software (malware) that threatens to leak or prevent access to data or a computer system until the victim pays a ransom (usually USD & Cryptocurrency) to the attacker.
How does ransomware work?
Initially, the malware gets into the device and the entire operating system or particular files are encrypted depending on the type of ransomware. The victim is then demanded to pay a ransom. You should use high-quality ransomware security software if you want to reduce the chances of a ransomware attack.
Ransomware uses asymmetric encryption. In this cryptography, keys are used to encrypt and decrypt files. The attacker can decrypt the victim’s files on his server using the public key, while the victim’s data can be accessed using the private key.
Ransomware Removal Options:
Paying the ransom is the first option, however, it is not recommended. Remember that paying the ransom does not guarantee that you will get your data back.
The second option is to go to www.nomoreransom.org to see if you’ve been infected with one of the ransomware types for which there are free decryption tools.
If this isn’t possible, there’s just one option which is to restore your device to factory settings.
Also Read: Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
NoMoreRansome.org:
NoMoreRansome.org site is a fantastic resource and it will be more helpful when you try to recover from a ransomware attack. No More Ransom (NMR) is a collaboration between Europol’s European Cybercrime Centre, the Netherlands’ National High Tech Crime Unit, and McAfee to assist victims of ransomware in recovering their encrypted data without having to pay the attackers.
NoMoreRansomware.org is not a techie site and you don’t have to be highly skilled to use it. It’s available to anyone who has been affected by ransomware, and you may recommend this site to your friends and families if you want to help them in the event of a ransomware attack.
NoMoreRansomware website can be accessed at www.nomoreransom.org
We will have a look around on the NoMoreRansome.org website.
From the Homepage, you can get awareness for Ransomware attacks. At the bottom of the homepage, we can find several different ransomware families that have been identified; certain variants of these families include encryption keys. The site also includes a separate category called Decryption Tools that includes a full list of Ransomware decryption keys for various ransomware types.
This Site contains the main Five Tabs which is listed below,
- Crypto Sheriff
- Ransomware: Q&A
- Prevention Advice
- Decryption Tools
- Report a Crime
First, let’s have a look at the Crypto Sheriff Tab
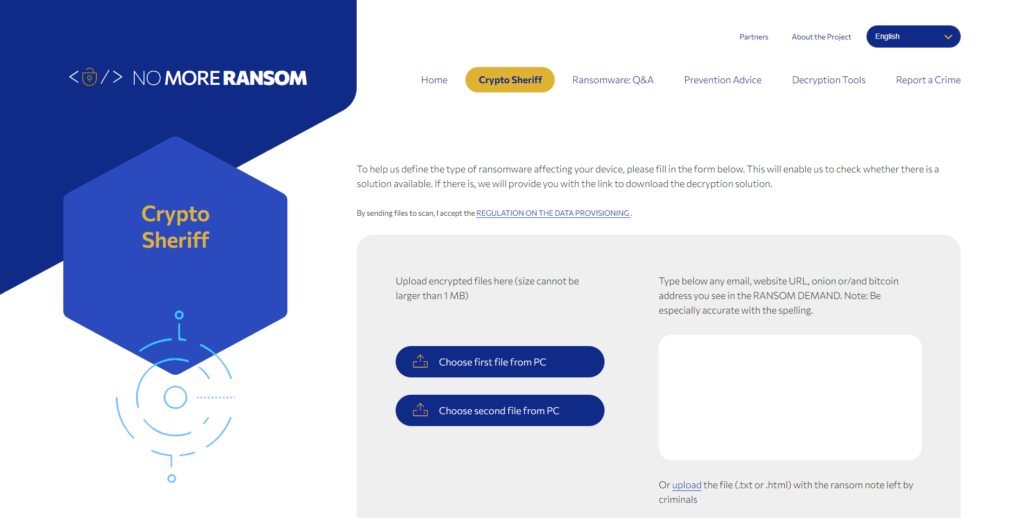
This Crypto Sheriff Tab will assist you in identifying the specific variant or family of ransomware that has infected your PC. This should be done by uploading the encrypted files to the site. You can see options to upload files from your PC on the Crypto Sheriff page, and you can upload two different files. However, before you upload anything to the site, please educate yourself on the data rules and regulations.
OR
You can upload the ransom note or ransom demand that was displayed on the screen, or put it in the box if you can find the text or HTML file.
Also Read: Latest Cyber Security News – Hacker News !
Note: Please be accurate with the spelling.
After you’ve completed the above steps, tap the “Go! FIND OUT button and NoMoreRansome.org will attempt to identify the ransomware family and variant that has infected your machine.
The second Tab is Ransomware: Q&A
This Tab will provide all details about the ransomware attacks, so we can understand more about ransomware, and also it provides a different screenshot of the encryption ransomware that you might see on your screen. There is a vast amount of information here if you want to familiarize yourself with ransomware it also provides you some advice on whether or not should you pay the ransom.
The third Tab is Prevention Advice
Prevention is always better than cure. This tab provides some advice on ransomware prevention and we can see that the number one piece of advice they give is the good old boring backup of a backup. The reason for this is that having strong backups is the most effective and sometimes the fastest way to recover from a ransomware attack.
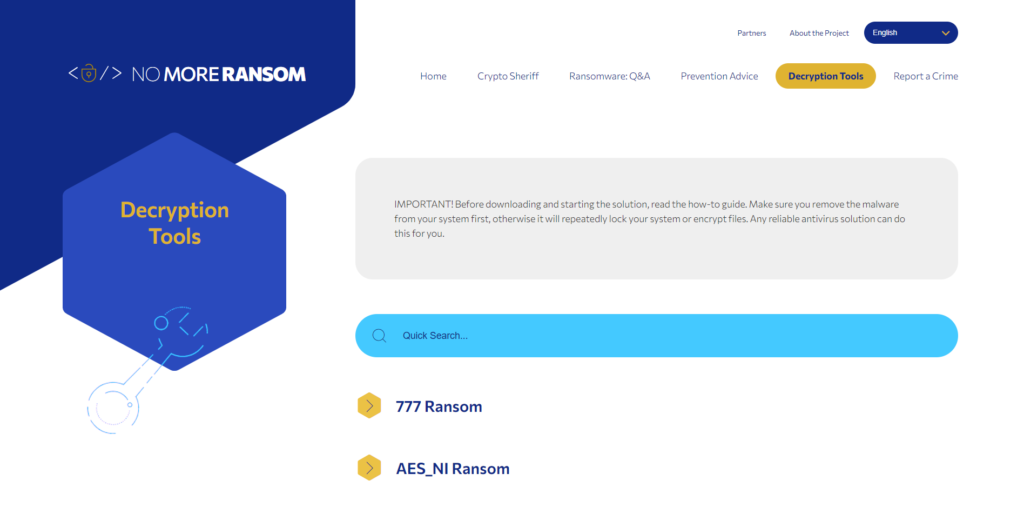
The fourth Tab is Decryption Tools
This is the site’s decryption tool area, where you can examine all of the numerous ransomware families for which decryption tools are available. They still do not contain encryption solutions for all the varieties of ransomware.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
When we click on the Ransom tools, we will see the below information:
For which ransomware versions was this tool created?
You’ll find a link to a tutorial on how to do it.
Which anti-virus vendors created the tool?
Link to download the tools
Each decryption tool has its own set of limitations. Some decryption tools are designed to decrypt files encrypted by specific ransomware variants. For example, the Intel security decrypter will only decrypt files with the following extensions: .mp3, .micro, .xxx, and.TTT.
IMPORTANT! Before downloading and starting the solution, read the how-to guide. Make sure you remove the malware from your system first, otherwise it will repeatedly lock your system or encrypt files. Any reliable antivirus solution can do this for you.
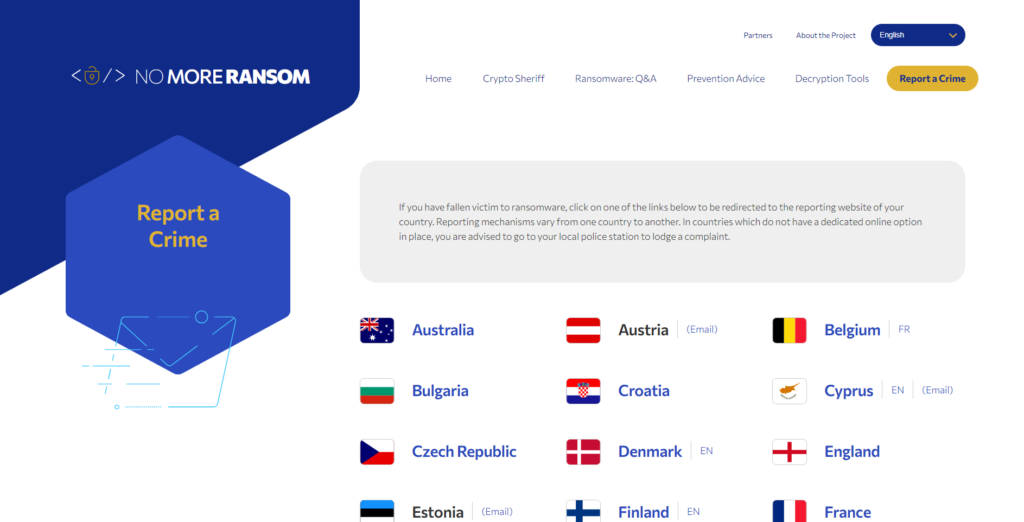
Report to Crime Tab
Remember! RANSOMWARE is a Crime, and you need to report it to law enforcement.
Bringing cybercriminals to justice happens with your help. Many law enforcement agencies are becoming more equipped with resources specifically dedicated to cybercrime. Still, they need victims of ransomware attacks and other cybercrimes to do their part by reporting attacks. It’s even possible that a government agency has a decrypter that can decrypt your files without the threat actor having to be contacted. Unless you reach out and report the incident, you’ll never know!
Partners Tab
It lists out the partners and creators of this initiative.

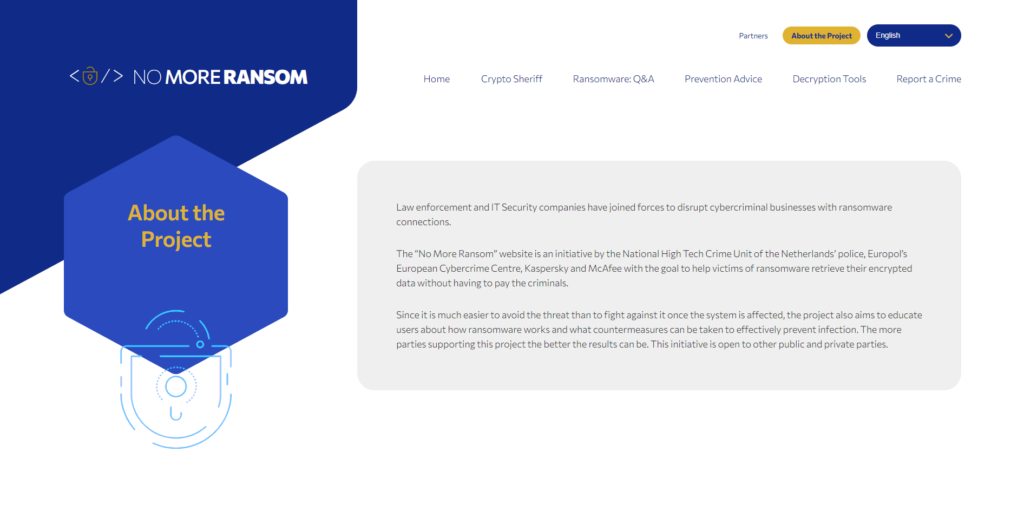
About the Project Tab
This tab will give you an overview of the nomoreransome.org project. It is an incredibly valuable resource if you’re trying to recover from a ransomware attack.
Also Read: Common Vulnerabilities and Exposures – New CVE’s
Conclusion:
If you’re compromised already with any ransomware attack, kindly visit the Nomoreransom.org site to check any available free decryption tools for the same. This site still does not contain encryption solutions for all the variants of ransomware, so it’s worth checking this site continuously as new tools are added on a regular basis.



































