Agent Tesla is an extremely popular spyware Trojan written for the .NET framework that has been observed since 2014 with many iterations since then. It is used to steal sensitive information from a victim’s device such as user credentials, keystrokes, clipboard data, credentials from browsers, and other information. This information can then be traded or used for business intelligence or ransom.
Agent Tesla is most commonly delivered via phishing campaigns and is sold and distributed across a number of hacking forums and platforms for anyone to purchase and use. This spyware is easy to get and easy to customize which makes it very popular.
Agent Tesla Infection Chain:
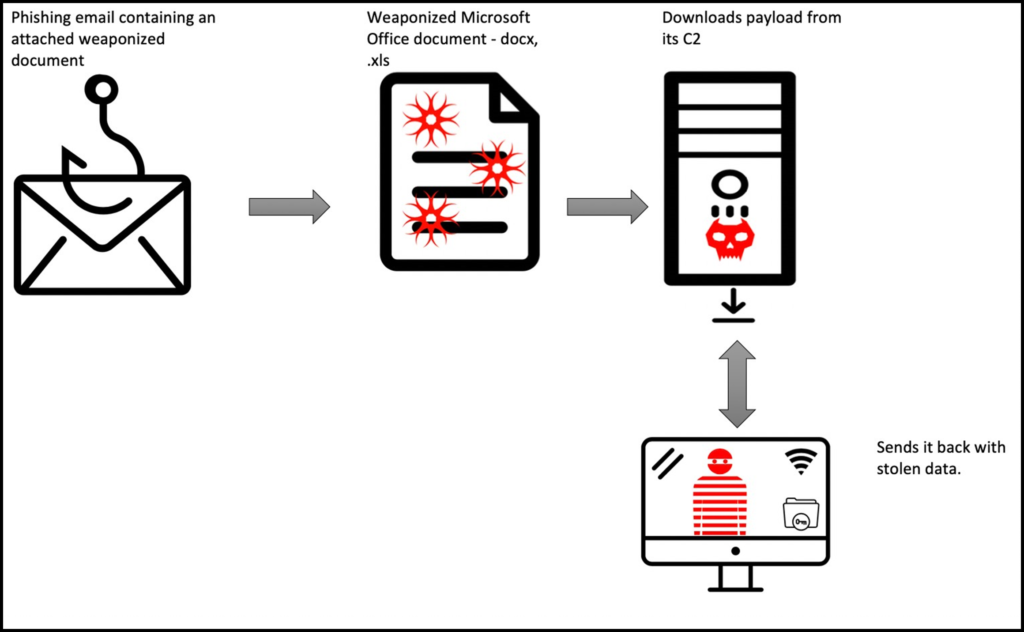
Malicious attachments in phishing emails are the most common deployment method for Agent Tesla. It has been observed dropping from weaponized documents that download the malware.
Also Read: Bumblebee malware loader is now active in the wild – Detection & Response
To trick security solutions, attackers leverage Microsoft Object Linking and Embedding as well as many control words in the RTF body, so parsers ignore anything they don’t know and security tools don’t block the document from being malicious.
When a victim opens the file, it initially sends an HTTP request to download the executable Agent Tesla payload and execute it.
Stealing data
The new process begins by searching the host for information such as the active computer name, email clients, FTP utilities, VNC clients, and web browsers.
Most Agent Tesla samples contain a large, predefined list of Internet browsers that the malware attempts to find on the victim’s machine. If those browsers are found, it then checks for the “User Data” directory and “Login Data” file which contains mail ids and credentials of stored profiles.
Also Read: SocGholish Malware on The Rise – Detection & Response
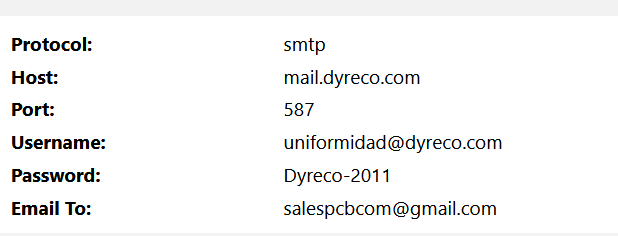
Once the malware has retrieved all available credentials and other data from the victim, it sends it over SMTP protocol:

Indicators of Compromise
File names:
82257e59fa6ef3d52701a20122f0522b5a6784b885496ba35807ba8a02985b9a
DNS/SMTP Request:
mail[.]dyreco.com
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentImage" ilike '%\OUTLOOK.EXE' or "ParentImage" ilike '%\WINWORD.EXE' or "ParentImage" ilike '%\excel.exe' or "ParentImage" ilike '%\powerpnt.exe') and ("Image" ilike '%\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe' or "Image" ilike '%.exe') and ("Process CommandLine" ilike '%\Users\Admin\AppData\Local\Temp\%')Splunk:((ParentImage="*\\OUTLOOK.EXE" OR ParentImage="*\\WINWORD.EXE" OR ParentImage="*\\excel.exe" OR ParentImage="*\\powerpnt.exe") AND (Image="*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe" OR Image="*.exe") AND (CommandLine="*\\Users\\Admin\\AppData\\Local\\Temp\\*")) AND source="WinEventLog:*"Elastic Query:(process.parent.executable:(*\\OUTLOOK.EXE OR *\\WINWORD.EXE OR *\\excel.exe OR *\\powerpnt.exe) AND process.executable:(*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe OR *.exe) AND process.command_line:*\\Users\\Admin\\AppData\\Local\\Temp\\*)CarbonBlack:(parent_name:(*\\OUTLOOK.EXE OR *\\WINWORD.EXE OR *\\excel.exe OR *\\powerpnt.exe) AND process_name:(*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe OR *.exe) AND process_cmdline:*\\Users\\Admin\\AppData\\Local\\Temp\\*)Crowstike:((ParentBaseFileName="*\\OUTLOOK.EXE" OR ParentBaseFileName="*\\WINWORD.EXE" OR ParentBaseFileName="*\\excel.exe" OR ParentBaseFileName="*\\powerpnt.exe") AND (ImageFileName="*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe" OR ImageFileName="*.exe") AND ((CommandLine="*\\Users\\Admin\\AppData\\Local\\Temp\\*") OR (CommandHistory="*\\Users\\Admin\\AppData\\Local\\Temp\\*")))Fireeye:(metaclass:`windows` pprocess:[`*\OUTLOOK.EXE`,`*\WINWORD.EXE`,`*\excel.exe`,`*\powerpnt.exe`] process:[`*\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe`,`*.exe`] args:`\Users\Admin\AppData\Local\Temp\\`)Graylog:(ParentImage.keyword:(*\\OUTLOOK.EXE *\\WINWORD.EXE *\\excel.exe *\\powerpnt.exe) AND Image.keyword:(*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe *.exe) AND CommandLine.keyword:*\\Users\\Admin\\AppData\\Local\\Temp\\*)Logpoint:(ParentImage IN ["*\\OUTLOOK.EXE", "*\\WINWORD.EXE", "*\\excel.exe", "*\\powerpnt.exe"] Image IN ["*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe", "*.exe"] CommandLine IN "*\\Users\\Admin\\AppData\\Local\\Temp\\*")Microsoft Defender:DeviceProcessEvents | where ((InitiatingProcessFolderPath endswith @"\OUTLOOK.EXE" or InitiatingProcessFolderPath endswith @"\WINWORD.EXE" or InitiatingProcessFolderPath endswith @"\excel.exe" or InitiatingProcessFolderPath endswith @"\powerpnt.exe") and (FolderPath endswith @"\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe" or FolderPath endswith ".exe") and (ProcessCommandLine contains @"\Users\Admin\AppData\Local\Temp\"))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((ParentProcessName endswith @'\OUTLOOK.EXE' or ParentProcessName endswith @'\WINWORD.EXE' or ParentProcessName endswith @'\excel.exe' or ParentProcessName endswith @'\powerpnt.exe') and (NewProcessName endswith @'\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe' or NewProcessName endswith '.exe') and (CommandLine contains @'\Users\Admin\AppData\Local\Temp\'))RSA Netwitness:((ParentImage contains '\OUTLOOK\.EXE', '\WINWORD\.EXE', '\excel\.exe', '\powerpnt\.exe') && (Image contains '\SecuriteInfo\.com\.BackDoor\.SpyBotNET\.25\.302\.exe', '.exe') && (CommandLine contains '\Users\\Admin\\AppData\\Local\\Temp\\\'))Sumologic:(_sourceCategory=*windows* AND (ParentImage = "*\OUTLOOK.EXE" OR ParentImage = "*\WINWORD.EXE" OR ParentImage = "*\excel.exe" OR ParentImage = "*\powerpnt.exe") AND (Image = "*\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe" OR Image = "*.exe") AND (CommandLine = "*\Users\Admin\AppData\Local\Temp\\*"))AwsOpensearch:(process.parent.executable:(*\\OUTLOOK.EXE OR *\\WINWORD.EXE OR *\\excel.exe OR *\\powerpnt.exe) AND process.executable:(*\\SecuriteInfo.com.BackDoor.SpyBotNET.25.302.exe OR *.exe) AND process.command_line:*\\Users\\Admin\\AppData\\Local\\Temp\\*)Google Chronicle:(principal.process.file.full_path = /.*\\OUTLOOK\.EXE$/ or principal.process.file.full_path = /.*\\WINWORD\.EXE$/ or principal.process.file.full_path = /.*\\excel\.exe$/ or principal.process.file.full_path = /.*\\powerpnt\.exe$/) and (target.process.file.full_path = /.*\\SecuriteInfo\.com\.BackDoor\.SpyBotNET\.25\.302\.exe$/ or target.process.file.full_path = /.*\.exe$/) and target.process.command_line = /.*\\Users\\Admin\\AppData\\Local\\Temp.*/



































