Adversaries may manipulate accounts to maintain access to victim systems. Account manipulation may consist of any action that preserves adversary access to a compromised account, such as modifying credentials or permission groups. These actions could also include account activity designed to subvert security policies, such as performing iterative password updates to bypass password duration policies and preserve the life of compromised credentials. In order to create or manipulate accounts, the adversary must already have sufficient permissions on systems or the domain.
Persistence consists of techniques that adversaries use to keep access to systems across restarts, changed credentials, and other interruptions that could cut off their access. Techniques used for persistence include any access, action, or configuration changes that let them maintain their foothold on systems, such as replacing or hijacking legitimate code or adding start-up code.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Hunting the Suspicious Account Remote Password Resets:
- Compromised account tries to reset user password to stay Persistence across systems. To Track such activities. For the Event ID 4624 ( An account was successfully logged on ) , Drill down the network logon activities which is Logon Type 3 and retrieve unique Logon IDs. This will populate the list of accounts of users or administrator with successful logons on the network.
- Next stage, try to figure out the Logon ID that is unique and Event IDs are different. So Each Event ID should have the Logon ID “0x853237” , In this example we have Logon ID “0x853237” , In you environment this number will change. Investigate accordingly.
- Here we see Logon ID “0x853237” matches for the Event ID “5145” which is network share object (file or folder) is accessed. The Share information has Relative target name which is known to be an accessed file or folder.
Also Read: Threat Hunting with EventID 5145 – Object Access – Detailed File Share
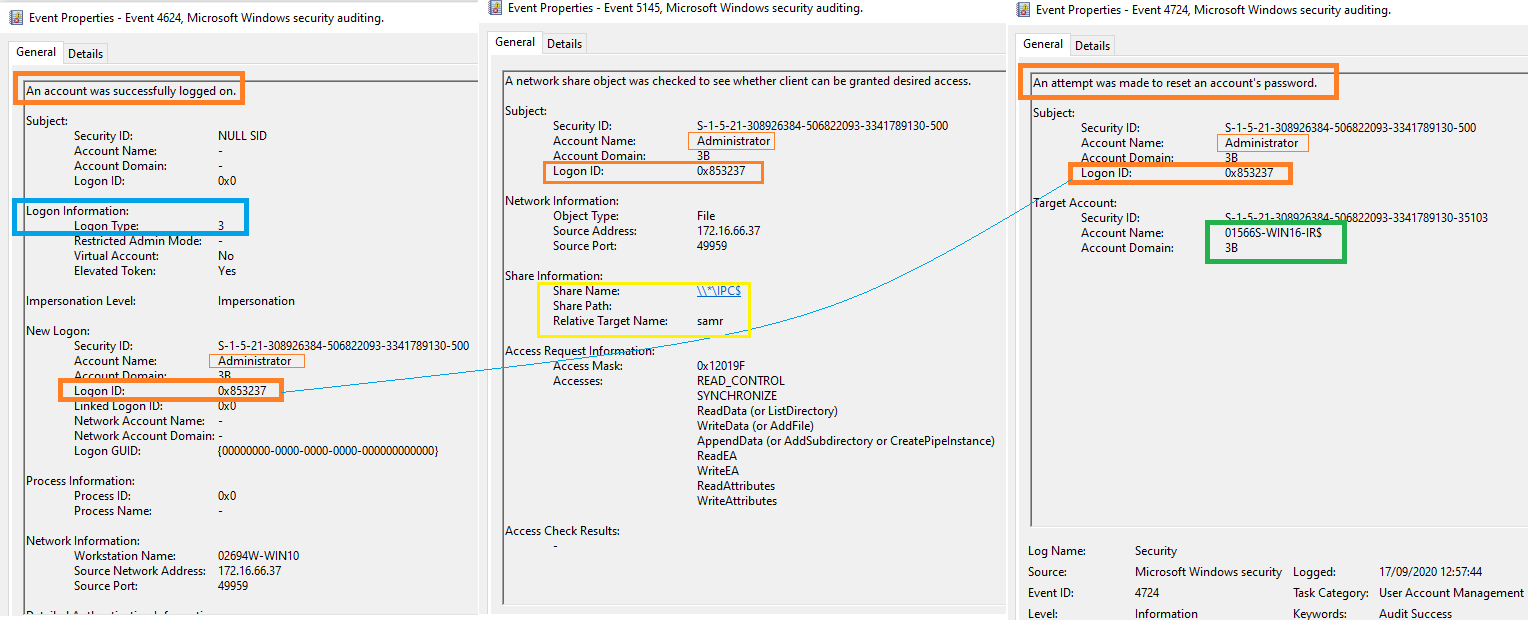
- Finally Track for the Event ID “4724” ( An attempt was made to reset an accounts password ) with the Logon ID “0x853237” to check the accounts the is targeted.
- Drill down with Event ID 4724 , Target account information reveals the Attacker has targeting the account name “01566S-WIN16-IR$” which is highlighted in green colour.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Specifically, an event code 4624, followed by an event code of 4724 is triggered when the vulnerability is exploited on hosts.
- Event ID “4738” ( A user account was changed ) triggers when an attacker has successfully resets the password.
- Possible Use cases includes, MimiKatz usage , Attempts to changes a user password , Account manipulation Detection, Anonymous logons.
Hunt Query:
query = ”’sequence by host.id with maxspan=5m [authentication where event.action==”logged-in” and
/* event 4624 need to be logged */ winlog.logon.type:”Network” and event.outcome == “success” and source.ip != null and
source.ip != “127.0.0.1” and source.ip != “::1”] by winlog.event_data.TargetLogonId /* event 4724 need to be logged */
[iam where event.action == “reset-password”] by winlog.event_data.SubjectLogonId
Source/Credit: https://twitter.com/SBousseaden
Happy Hunting!



































