We have already gone through the five golden search commands. Here we are going to see the next 3 commands:
- Append
- Chart
- Dedup
1-append:
Use the append command to append the results of a sub search to the results of your current search. In a simpler way, we can say it will combine 2 search queries and produce a single result. The append command will run only over historical data; it will not produce correct results if used in a real-time search.
Synopsis:
Appends subsearch results to current results.
Syntax:
append [subsearch-options]*subsearch
Required arguments:
subsearch:
Description: A search pipeline. Read more about how sub searches work in the Search manual.
Optional arguments:
subsearch-options
Syntax: maxtime=<int> | maxout=<int> | timeout=<int>
Description: Controls how the subsearch is executed.
Subsearch options:
maxtime
Syntax: maxtime=<int>
Description: The maximum time (in seconds) to spend on the subsearch before automatically finalizing. Defaults to 60.
maxout
Syntax: maxout=<int>
Description: The maximum number of result rows to output from the subsearch. Defaults to 50000.
timeout
Syntax: timeout=<int>
Description: The maximum time (in seconds) to wait for subsearch to fully finish. Defaults to 120.
Example:
Scenario 1:
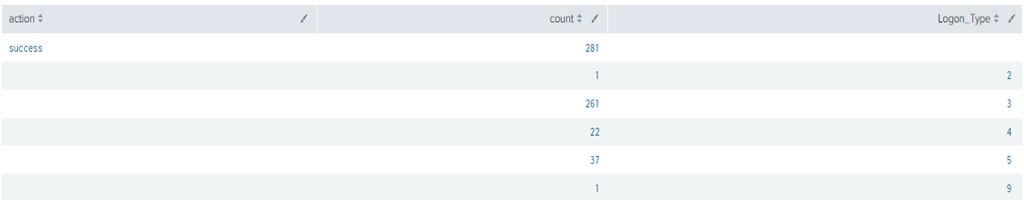
There was a sudden increase in the logins and analysts were not sure from where it got initiated. So, the user tried to gather the action and to Identify the logon type initiated the connection with the below query:
“|search index=”wineventlog” EventCode=4624
| stats count by action
| append [ search sourcetype=WinEventLog | stats count by Logon_Type ]“
In the first search query, we have specified index and success logon event code and then produce the output with stats count command to give the exact count of success login as the first search. That’s the result in the first line. Then we have used the append command to combine the 2nd search which will also add the count of logon_type.
Output:
Scenario 2:
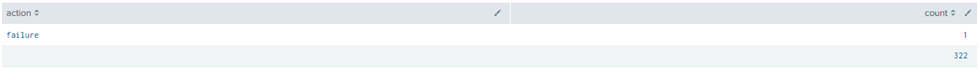
Security analysts need to fetch the count of interactive logon events and the total number of failed and success logon count at the time.
“sourcetype=WinEventLogEventCode=4624 OR EventCode=4625
| where Logon_Type=2
| stats count by action
| append [ search sourcetype=WinEventLog | where EventCode IN (4624,4625) | stats count ]“
In the 1st search query, we have produced the successful and failed action counts of the interactive login.
That’s the result in the first line. Then we have used the append command in the 2nd query and produced the total count of the success & failed event code logs. That’s the count in the second line.
Output:
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
2-Chart
Use the chart command to create charts that can display any series of data that you want to plot. You can decide what field is tracked on the x-axis of the chart. The chart, time chart, stats, event stats, and stream stats are all designed to work in conjunction with statistical functions.
Synopsis
Returns results in a tabular output for charting.
Syntax
chart [sep=<string>] [cont=<bool>] [limit=<int>] [agg=<stats-agg-term>] (
<stats-agg-term> | <sparkline-agg-term> | <eval-expression>…) [ by <field>
(<bucketing-option> )… [<split-by-clause>] ] | [ over <field>
(<bucketing-option>)… (by <split-by-clause>] ]
Required arguments
agg
Syntax: agg=<stats-agg-term>
Description: Specify an aggregator or function. For a list of stats functions with descriptions and examples, see “Functions for stats, chart, and timechart”.
sparkline-agg-term
Syntax: <sparkline-agg> [AS <wc-field>]
Description: A sparkline specifier option all renamed to a new field.
eval-expression
Syntax: <eval-math-exp> | <eval-concat-exp> | <eval-compare-exp> |
<eval-bool-exp> | <eval-function-call>
Description: A combination of literals, fields, operators, and functions that represent the value of your destination field. For more information, see the Functions for eval. For these evaluations to work, your values need to be valid for the type of operation. For example, with the exception of addition, arithmetic operations may not produce valid results if the values are not numerical. Additionally, Splunk can concatenate the two operands if they are both strings. When concatenating values with ‘.’, Splunk treats both values as strings regardless of their actual type.
Optional arguments
agg
Syntax: <stats-agg-term>
Description: For a list of stats functions with descriptions and examples, see “Functions for stats, chart, and timechart”.
bucketing-option
Syntax: bins | span | <start-end>
Description: Discretization options. If a bucketing option is not supplied, timechart defaults to bins=300. This finds the smallest bucket size that results in no more than 300 distinct buckets.
cont
Syntax: <bool>
Description: Specifies whether it is continuous or not.
limit
Syntax: <int>
Description: Specify a limit for series filtering; limit=0 means no filtering.
single-agg
Syntax: count|<stats-func>(<field>)
Description: A single aggregation applied to a single field (can be evaled field). No wildcards are allowed. The field must be specified, except when using the special count aggregator that applies to events as a whole.
sep
Syntax: sep=<string>
Description: Used to construct output field names when multiple data series are used in conjunctions with a split-by field.
split-by-clause
Syntax: <field> (<tc-option>)* [<where-clause>]
Description: Specifies a field to split by. If the field is numerical, default discretization is applied; discretization is defined with tc-option.
Example:
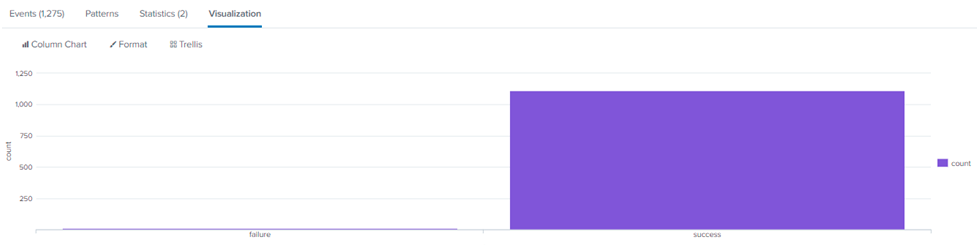
With the use of chart command, displayed the results of login action count in form of a chart.
“sourcetype=WinEventLog
| chart count by action span=log2“
Output:
Also Read: Latest Cyber Security News – Hacker News !
3-DEDUP:
Description
The dedup command lets you specify the number of duplicate events to keep based on the values of a field. You may also use the dedup command to sort by a set of fields. This will delete all duplicates before sorting the results by the sort-by field you specify. It’s worth noting that this will only work if your search yields several results. The other options allow you to provide additional criteria. For example, you might wish to maintain all events but eliminate duplicate values instead of the entire event. If you’re searching through a big amount of data, you won’t be able to use the dedup command against the _raw field. Doing this will impact your search performance.
Synopsis
Removes the subsequent duplicate results that match specified criteria.
Syntax
dedup [<N>] <field-list> [keepevents=<bool>] [keepempty=<bool>] [consecutive=<bool>] [sortby <sort-by-clause>]
Required arguments
<field-list>
Syntax: <string> <string> …
Description: A list of field names.
Optional arguments
consecutive
Syntax: consecutive=<bool>
Description: Specify whether to only remove duplicate events that are consecutive (true). Defaults to false.
keepempty
Syntax: keepempty=<bool>
Description: If an event contains a null value for one or more of the
specified fields, the event is either retained (true) or discarded. Defaults to false.
keepevents
Syntax: keepevents=<bool>
Description: When true, keep all events and remove specific values.
Defaults to false.
<N>
Syntax: <int>
Description: Specify the first N (where N > 0) number of events to keep, for each combination of values for the specified field(s). The non-option parameter, if it is a number, is interpreted as N.
<sort-by-clause>
Syntax: ( – | + ) <sort-field>
Description: List of fields to sort by and their order, descending ( – ) or
ascending ( + ).
Sort field options
<sort-field>
Syntax: <field> | auto(<field>) | str(<field>) | ip(<field>) | num(<field>)
Description: Options for sort-field.
<field>
Syntax: <string>
Description: The name of the field to sort.
auto
Syntax: auto(<field>)
Description: Determine automatically how to sort the field’s values.
ip
Syntax: ip(<field>)
Description: Interpret the field’s values as an IP address.
num
Syntax: num(<field>)
Description: Treat the field’s values as numbers.
str
Syntax: str(<field>)
Description: Order the field’s values lexicographically.
Example:
Scenario 1:
Remove duplicate results based on one field.
“| search app=web-browsing dest_ip!=10* | table dest_ip | dedup dest_ip”
The above query will show the unique IP results of the outbound browsing connections excluding the internal connections.
Scenario 2:
Keep the first 3 duplicate results
“| search app=web-browsing dest_ip!=10* | table dest_ip | dedup3 dest_ip”
The above query will show the results of the outbound browsing IP connections excluding the internal connections. Here since we include 3 after dedup, the first 3 duplicate entries will be displayed.
Scenario 3:
Keep results that have the same combination of values in multiple fields
“| search app=web-browsing dest_ip!=10* | table dest_ip | dedup 2 dest_ip, user”
The above search query will results in the same combination of destination IP AND user values, keep the first 2 that occur, and remove all subsequent values.