Organizations without modern threat-intelligence capabilities face escalating breach costs, wasted resources, and operational inefficiencies that hit the bottom line. But by deploying high-fidelity solutions like Threat Intelligence Lookup, businesses can turn security into a cost-saving engine by preventing incidents, optimizing workflow, and accelerating response.
What You’ll Learn
- Prevention pays: Instant threat visibility stops million-dollar breaches before they start by giving analysts the full picture in seconds.
- Context kills noise: Rich threat enrichment eliminates the costly cycle of alert fatigue and false positive investigation that burns through analyst time.
Threat Intelligence Lookup main page: click search bar to see parameters
- Speed saves money: Immediate access to behavioral analysis and attack context slashes incident response time, protecting revenue and customer trust.
- Intelligence scales: Automated threat tracking keeps pace with evolving attacks without expanding headcount or research budgets.
- Integration protects investments: Modern threat lookup capabilities enhance existing tools rather than replacing them.
The Price of Flying Blind: Three Expensive Security Gaps
1. Operating in Crisis Mode Burns Out Your Team
Your SOC analysts start each shift facing thousands of alerts. Without deep context on each indicator, they manually pivot between tools, search databases, cross-reference findings, and compile reports — only to discover most alerts are benign or duplicates. This isn’t security work; it’s digital archaeology that drains morale and budgets simultaneously.
Every investigation pulls resources from genuine threats. The human cost shows up as turnover and burnout, while the financial impact appears as overtime costs and recruitment expenses.
The numbers don’t lie:
- Organizations waste $1.3 million annually investigating false positives.
- Burned-out analysts are 200% more likely to quit, triggering expensive replacement cycles.
2. Slow Threat Identification Multiplies Damage
Speed determines survival in modern cyber defense. When analysts must manually research threats, attackers gain precious time to establish persistence, move laterally, and exfiltrate data.
The gap between detection and understanding creates a window where minor incidents become major disasters. Without immediate access to comprehensive threat context, security teams make decisions based on incomplete information, often missing critical behavioral indicators that reveal an attack’s true scope.
The stakes are astronomical:
- Average breach costs hit $4.4 million per incident.
- 60% of small and medium businesses never recover from a successful cyberattack.

The outcomes of low detection rates
3. Compliance Failures Trigger Regulatory Penalties
Regulatory frameworks increasingly expect organizations to maintain current threat intelligence and demonstrate proactive defense measures. Without automated threat enrichment showing detailed attack context and response actions, compliance becomes an expensive guessing game.
Manual processes create gaps in documentation, while slow threat research extends the time between detection and response: both red flags during audits.
The regulatory price tag:
- GDPR violations can cost 4% of global annual revenue or €20 million, whichever is higher.
- HIPAA breaches carry fines exceeding $1.5 million per incident.
Five Ways Intelligent Threat Lookup Protects Your Bottom Line
1. Transform Indicators into Instant Understanding
Traditional threat analysis creates dangerous delays. An analyst spots a suspicious file hash, URL, or IP address, then the research marathon begins: checking reputation databases, searching threat feeds, reviewing historical incidents, and hoping to find relevant context. By the time they piece together the threat landscape, the attack may have already succeeded.
Modern threat lookup capabilities eliminate this gap entirely. Instead of beginning an investigation from zero, analysts query a single artifact and instantly receive comprehensive intelligence: indicator verdict, geotargeting and urgency, associated campaigns, targeting patterns, related indicators, and MITRE ATT&CK mappings.
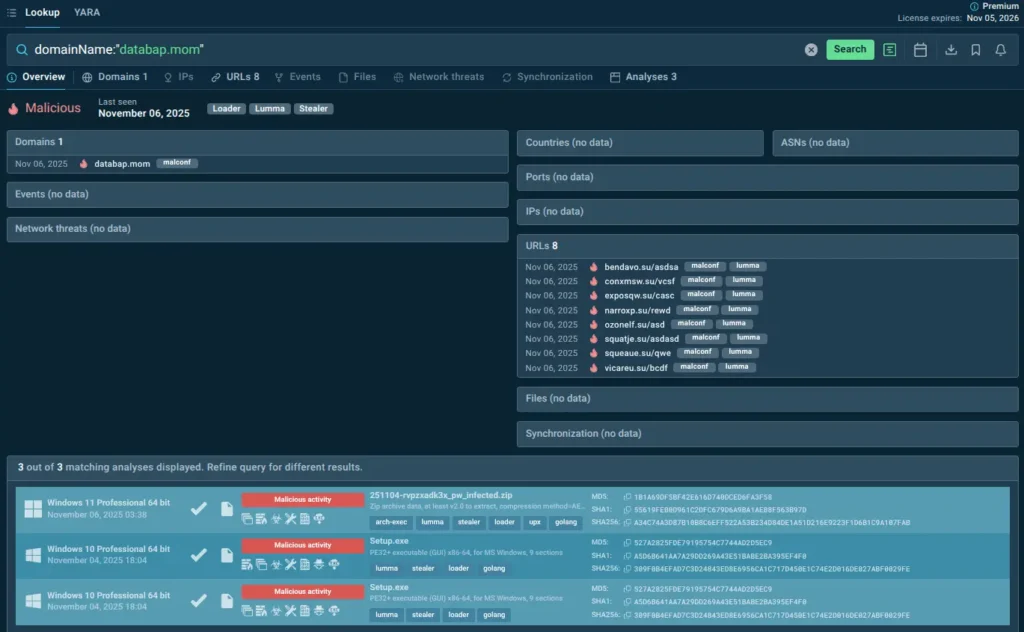
Lookup results: IOC verdict, additional IOCs, sandbox analyses
This transforms every alert from a question mark into an informed decision point.
| Catch attacks early with instant IOC enrichment in TI Lookup Request trial for your team |
How ANY.RUN Helps:
Query a single suspicious indicator and receive instant access to complete attack intelligence drawn from 15,000+ active SOC environments.
2. Stop Paying for Phantom Threats
Alert fatigue isn’t just annoying. It’s expensive. When analysts spend 70% of their time investigating alerts that turn out to be false positives or low-severity events, you’re essentially paying professional wages for busywork. Exhausted teams miss real threats while burning budget on meaningless investigations.
Without immediate access to contextual threat intelligence showing whether an indicator is genuinely malicious, what campaign it belongs to, and what tactics it employs, every alert demands equal attention. This democratic approach to triage guarantees resource waste.
How ANY.RUN Helps:
The enrichment through TI Lookup integration delivers complete threat context, including TTPs, campaign associations, and behavioral indicators, directly into analyst workflows. For example, a suspicious domain may signal a ClickFix attack technique in action:
domainName:”googleserviceteg.com”
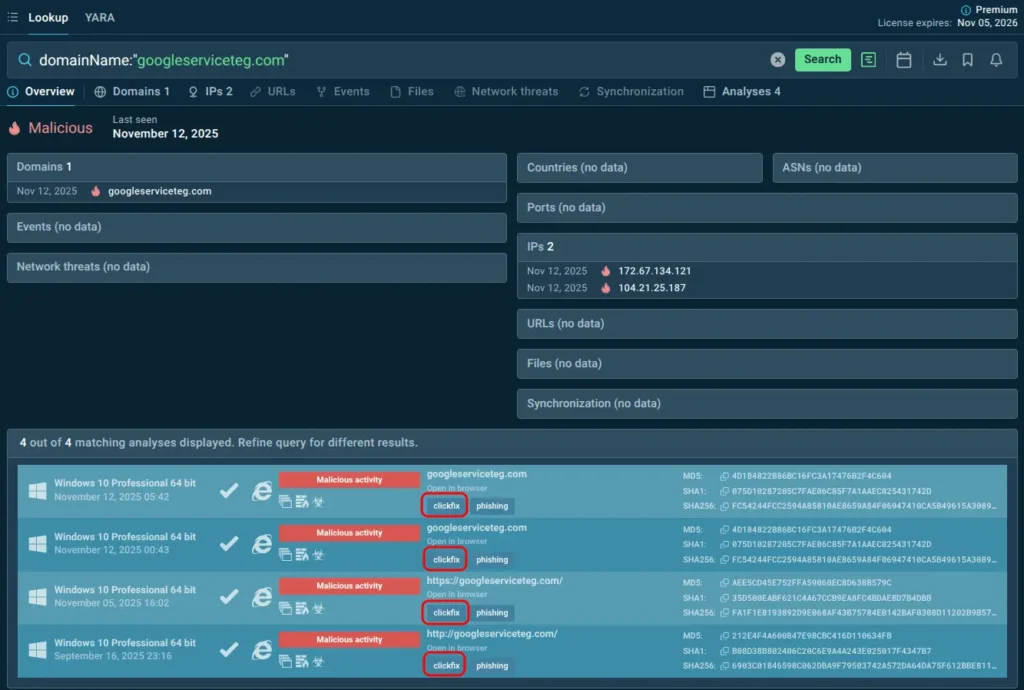
Domain associated with ClickFix attacks
Teams instantly distinguish critical threats from noise, redirecting investigation time toward genuine security events.
3. Replace Manual Labor with Intelligent Automation
Manual threat research is security’s most expensive hidden cost. The financial impact extends beyond salaries. Manual investigation creates bottlenecks where Tier 1 analysts must escalate to Tier 2 for context they can’t gather themselves. This escalation dance wastes both teams’ time while slowing incident response.
Automated threat enrichment through the integration of ANY.RUN’s TI solutions enables SOCs to drop escalations dramatically. Tier 1 teams can independently assess threats, make containment decisions, and document incidents.
How ANY.RUN Helps:API and SDK integrations enable automatic enrichment of every indicator entering your security stack. Whether through SIEM integration, SOAR playbooks, or EDR workflows, ANY.RUN delivers comprehensive threat intelligence without human intervention. Investigation time drops from hours to seconds, escalations decrease by 60%, and your existing team handles significantly higher alert volumes without burnout.
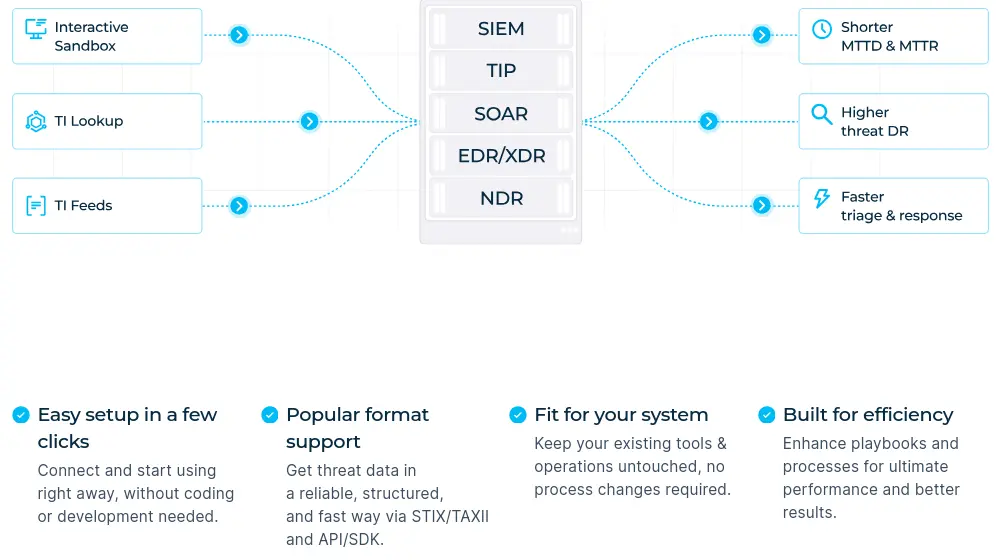
ANY.RUN integrations benefits
4. Accelerate Response Before Damage Compounds
In cybersecurity, time literally is money. Research shows that each hour of delay during incident response increases breach costs exponentially. Downtime accumulates, data exposure grows, and recovery becomes more complex.
These delays are particularly devastating for fast-moving threats like ransomware, where attackers can encrypt entire networks in hours.
How ANY.RUN Helps:
TI Lookup search results include direct access to interactive sandbox sessions showing the threat’s actual behavior on a live system. Analysts don’t just read about the attack, they watch it unfold, see registry modifications, observe network traffic, and identify persistence mechanisms. This visual intelligence enables precise, rapid containment tailored to the specific threat, dramatically reducing dwell time and minimizing financial impact.
| Power your response and proactive defense with data from 15K SOCs Try TI Lookup with 50 trial search requests |
5. Stay Current Without Constant Manual Research
Threat landscapes shift daily as attackers modify infrastructure, launch new campaigns, and exploit fresh vulnerabilities. By the time intelligence is compiled, analyzed, and distributed to security teams, attacks may already be in progress. The gap between threat emergence and defensive readiness remains a persistent financial risk.
Modern threat lookup platforms solve this through continuous, automated intelligence updates. Instead of monitoring dozens of sources, analysts create focused queries around threats relevant to their environment — specific malware families, targeting patterns, or attack techniques — and receive automatic notifications when new intelligence emerges. This transforms passive research into active surveillance without manual effort.
How ANY.RUN Helps: Query Updates functionality automatically tracks threats you care about. Set up custom searches for sector-specific attacks, emerging malware families, or particular threat actors, then receive instant notifications when new samples, indicators, or infrastructure appear.
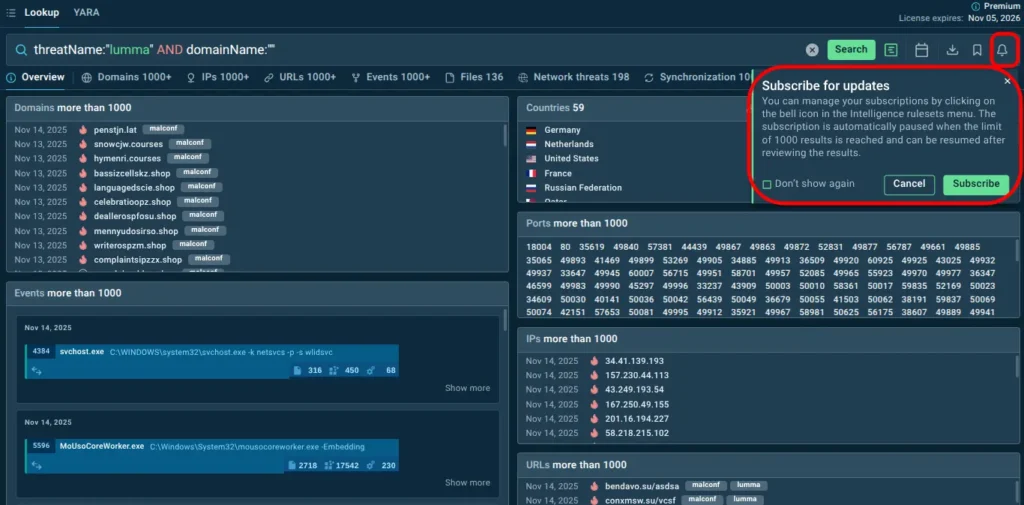
Turn on query updates and receive new IOCs automatically
Conclusion
Threat Intelligence Lookup is not merely a technical add-on; it’s an operational multiplier and a strategic safeguard. By combining data enrichment, automation, and real-time context, it allows organizations to:
- Detect and contain threats faster, minimizing business interruption.
- Optimize human and financial resources.
- Strengthen compliance posture and reduce regulatory exposure.
- Translate security investments into measurable business outcomes.
In the end, every saved hour of analyst time and every prevented breach directly contribute to profitability and resilience. That’s the real power of TI Lookup: not just saving time, but saving money, reputation, and trust.
| Protect your revenue, investments, and client trust. See ANY.RUN in action with 14-day trial. |



































