The term “zero-day” refers to the period between the discovery of a software defect and the availability of a fix. Since the security companies are unaware of it, no patch is available. A zero-day vulnerability is a previously undisclosed computer software flaw that attacks silently before security teams are aware of it. Many of the vulnerabilities that fall under the category of application security can be classified as zero-day vulnerabilities, since they are generally unique to a particular application, they will never be listed in a common vulnerability database.
Also Read: Account Manipulation and Access Token Theft Attacks
Zero-Day Exploit:
A zero-day exploit starts with a software developer releasing insecure code that a malicious actor discovers flaw and exploits it. The attacker then either succeeds in committing identity or information theft, or the developer produces a patch to limit the spread of the attack. The exploit is no longer referred to be a zero-day exploit once a fix has been produced and applied.
Security experts have divided the timeline of zero-day exploitation into seven steps:
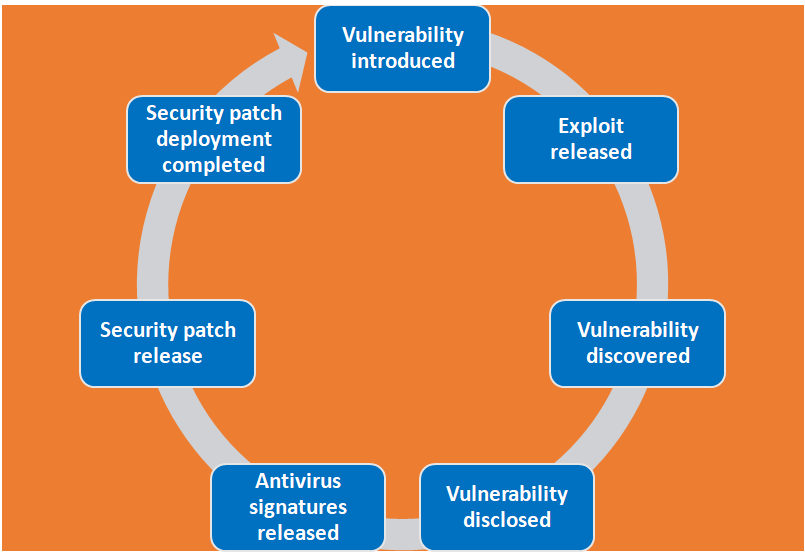
Stage 1 – Vulnerability introduced:
The developer creates software and while testing it, it shows as green. Without knowingly, the software contains vulnerable code. Vulnerability is introduced here.
Stage 2 – Exploit released:
The next stage is the exploit has been released. A malicious actor discovers the vulnerability before the developer is aware of it or has had a chance to fix or patch it. While the vulnerability is still open, the hacker writes and deploys exploit code.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Stage 3 – Vulnerability discovered:
Now the vendor becomes aware of the vulnerability but does not have a patch available and a vulnerability has been detected.
Stage 4 – Vulnerability disclosed:
The vendor and/or security researchers publicly acknowledge the vulnerability, informing users and attackers of its existence. The Vulnerability is revealed here.
Stage 5 – Antivirus signatures released:
Antivirus signatures have been made public. If attackers create zero-day malware to exploit the vulnerability, antivirus vendors can quickly recognize its signature and provide protection against it. However, if there are other ways to exploit the vulnerability, systems may remain vulnerable.
Also Read: Latest Cyber Security News – Hacker News !
Stage 6 – Security patch released:
A security patch has been issued. The vendor issues a public patch to address the vulnerability. The length of time it takes to arrive is determined by the complexity of the problem and how high a priority it is in its development process.
Stage 7 – Security patch deployment completed:
The installation of the security patch is now complete.The release of a security patch does not provide an immediate fix because it may take some time for users to deploy it. As a result, organizations and individual users should enable automatic software updates and pay attention to update notifications.
How to Defend Against Zero-Day Exploits:
- Deploying a web application firewall (WAF) on the network edge to review incoming traffic and filter out malicious inputs that could target security vulnerabilities is one of the best ways to prevent zero-day attacks.
- Solutions that scan for vulnerabilities can simulate attacks on software code, review code for errors, and try to identify new issues introduced by a software update. This approach, however, will not detect all zero-day exploits, and scanning alone will not be enough. To prevent an exploit, businesses must act quickly on the results of a scan and review code.
- Run a free website scanner on a regular basis to check for malware and vulnerabilities. Since the best weapon is a great offense, patch any new vulnerabilities before someone else does.
- Patch management: Deploying software patches as soon as a software vulnerability is discovered can reduce the risk of an attack. It cannot, however, prevent an attack if the hacker develops their exploit faster than the patch is deployed. The longer the patching process takes, the more likely it is that a zero-day attack will occur.
- With the help of Virtual LANs, you can protect the content of individual transmissions.Always use password-protected Wi-Fi.
- Perform penetration testing on your applications. This will help you in finding the weak points in your security and fixing them before the hackers do.
- It is essential to keep the software up to date with the most recent software updates and patches.
- Install a good anti-virus policy to prevent such attacks.
- Use Secure Socket Layer (SSL)-protected websites (SSL).
- Many companies are helping with projects focused on providing information on upcoming attacks.
- The zero-day initiative is a program that rewards security researchers for disclosing vulnerabilities instead of selling them on the black market. Its goal is to build a community of vulnerability researchers who find software bugs before hackers do. Furthermore, organizations provide bug bounty programs in which individuals are compensated for reporting vulnerabilities to them.
Also Read: What is a WAF? | Web Application Firewall Explained
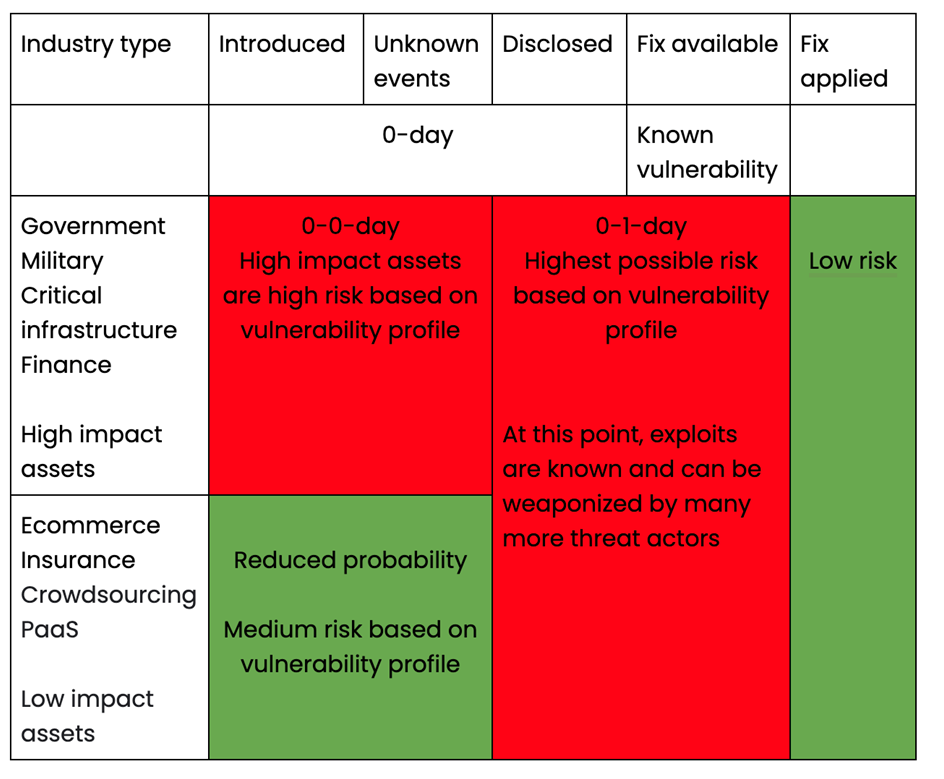
Measuring the Severity of Zero-Day Impact:
The zero-day impact chart below depicts the severity of impact on a given organization based on industry type and vulnerability timeline.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Conclusion:
Each zero-day has its own history to narrate, and not all zero-days have a devastating impact. The extent of a zero-day exploit is determined by a variety of criteria, including the organization’s industry, size, and other characteristics. Zero-day attacks are rarely discovered in time to prevent significant damage. It can take days, months, or even years for a developer to discover a vulnerability that has resulted in an attack and data breach.



































