Certificate Transparency ( CT ) is a open source framework to monitor and detect the forged or fake SSL certificates , usually users browsers detects such forged SSL certificates , But in most cases certificate authorities ( CA ) issues trusted certificates to all newly registered domains.This newly registered domains intention may be to build a legitimate business or to impersonate a band and hook top organizations for cyber attacks. Lack of validation issues on CA’s are putting the high risk for industries into digital world.
Today in this post , we will study the CT logs to detect and confirm the site is malicious or not.There are lots of online tools or manual procedure to check and validate Certificate logs.Here i am choosing the CENSYS.IO
Impersonation Domains
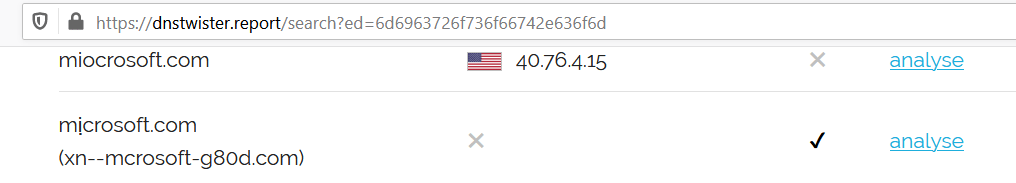
Here we have an domain which looks similar to the original brand , microsoft.This is a Punycode domains. We have detected such domains with the help of dnstwister , awesome tool for incident responders and soc analysts to handle phishing cases proactively.
Also Read : DnsTwist Tool – Proactive Approach for Handling Phishing Cases
What is PunnyCode Domains ?
Domains which can be registered in your native language , for example, mⅰcrosoft[.]com , where letter “i” is alternative unicode character. Now the domain register will save this domain as Punny code ,I.E xn--mcrosoft-j75d[.]com , Now all the browsers support & accept this punny code conversion , so when an phishing domains is delivered , it appears as mⅰcrosoft[.]com
Note : Not all the Domains zones will support this punnycode , check and purchase.

Analysis of Punny Code Domain Certificate Transparency
Let us check the certificate details on the censys.io , checking the certificate transparency is not limited to punny codes domains , You can check any other domains in censys.io to proof the phishing activity with SSL validation.
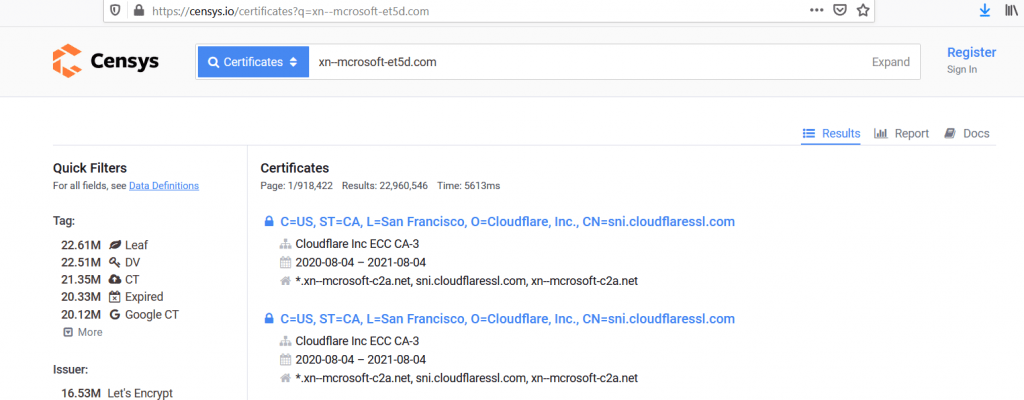
Above figure shows, punny code xn--mcrosoft-j75d[.]com of mⅰcrosoft[.]com is submitted on the censys search.
Note : Some organization may use this kind this punny code for legitimate purposes also. Investigate accordingly.

Above Figure shows the Cloudflare as the CA , But in some cases , Punny codes domains are redirected to the original site itself , this shows the legitimate business has bought such domains to stop further threats.
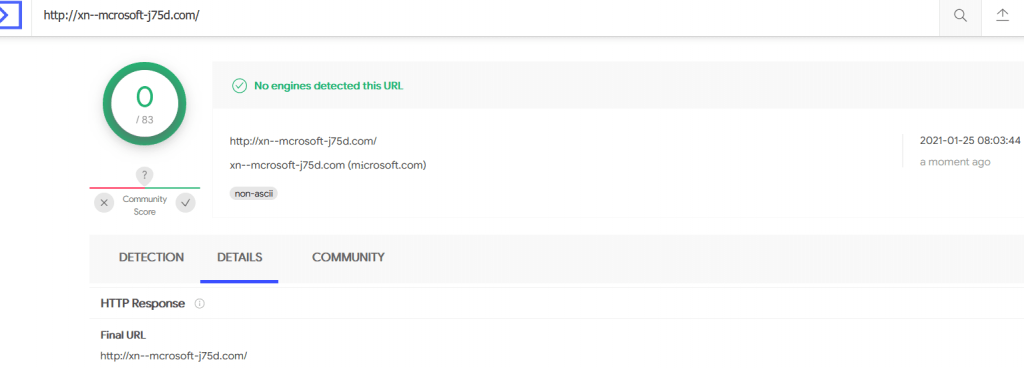
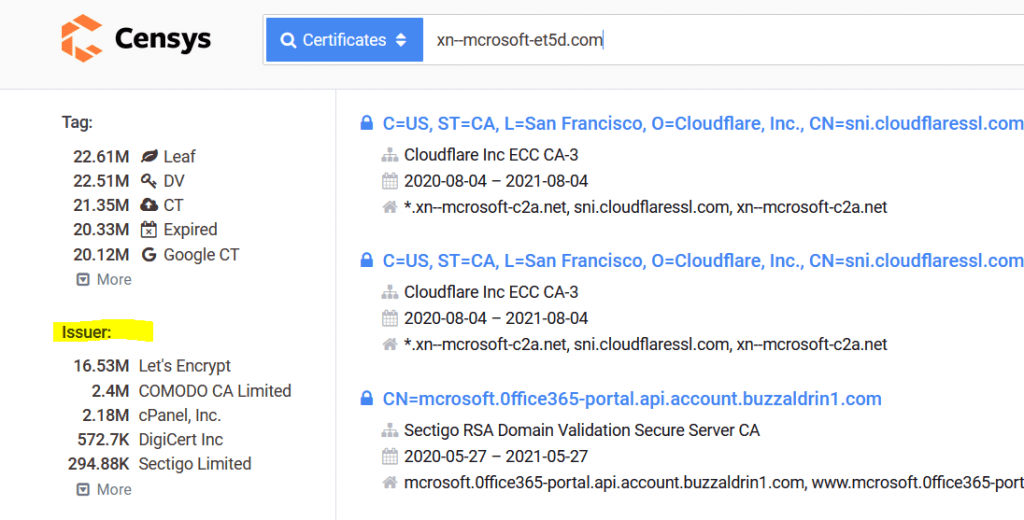
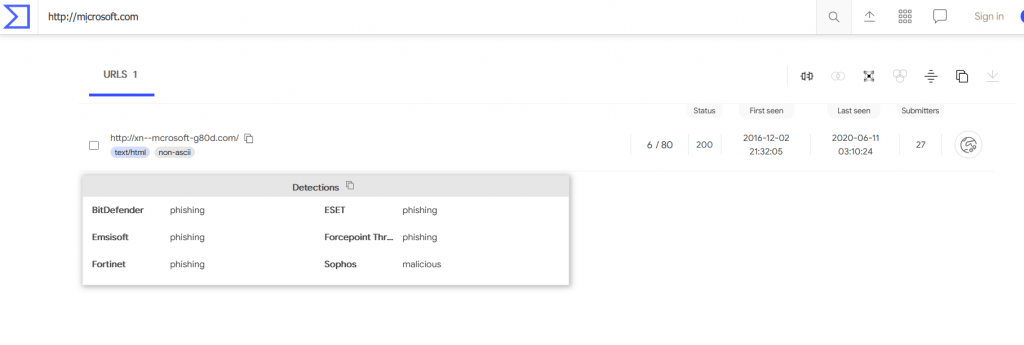
Using the SSL validation , Incident responders and soc analysts can compare the original site SSL with the phishing site to get insights as the domain is under legitimate business or this a phishing website to steal user credentials.



































