Ask any SOC team what slows them down, and the answers sound the same; too many alerts, not enough context, and tools that make them wait. Every alert takes minutes that add up to hours, turning routine triage into an endless race against time.
Each extra step delays containment and stretches your MTTR. Meanwhile, attackers don’t wait.
That’s why saving 20 minutes per incident is the edge that keeps your SOC focused, fast, and in control.
What Saving 20 Minutes Really Means for Your SOC
In cybersecurity, 20 minutes can feel like nothing until you multiply it by every alert, every day. Those minutes are where fatigue builds, where incidents pile up, and where attackers quietly move forward.
Cutting just 20 minutes from each investigation doesn’t only speed things up but it also reshapes how your SOC operates.
- Faster containment: Threats are isolated before they spread across systems.
- Sharper focus: Analysts spend less time on noise and more on what actually matters.
- Fewer escalations: Clearer insights mean fewer handoffs and faster decisions.
- Stronger morale: Less pressure, less burnout, and a more confident team.
It’s all about reclaiming control over your time, your workflow, and your defense.
The Fastest Path to Lower MTTR Per Incident
One of the safest and easiest ways to shorten investigations is by checking suspicious files and links inside a cloud-based, intuitive sandbox like ANY.RUN.
Instead of waiting on static scans or switching between tools, analysts can watch threats unfold in real time; every process, registry change, and network connection revealed as it happens. That instant visibility turns hours of uncertainty into minutes of clarity.
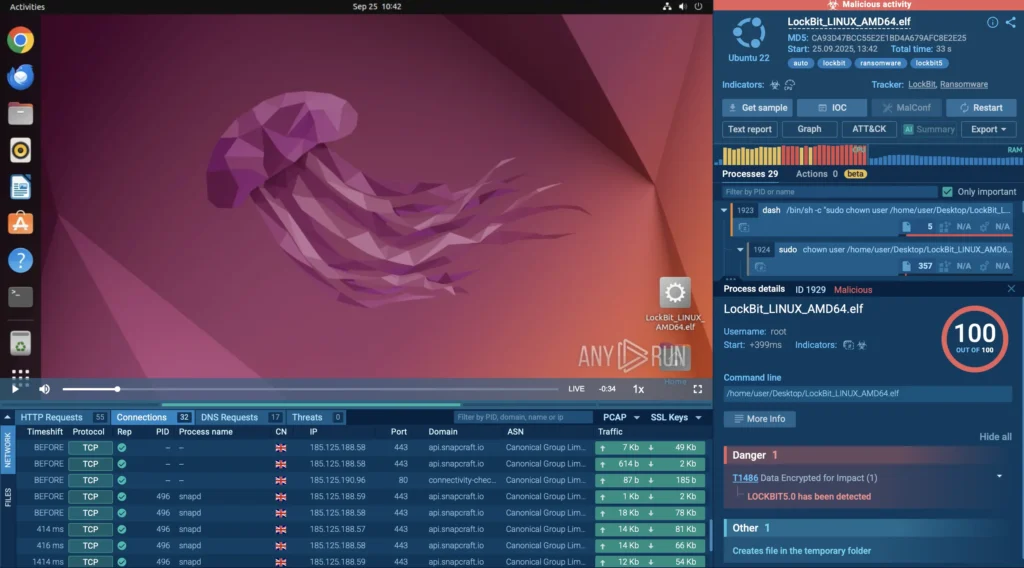
ANY.RUN’s sandbox exposing LockBit attack inside a safe environment
Across real SOC environments, this visibility gives measurable results:
- 20 minutes faster MTTR per case, based on average reductions achieved by SOC teams using ANY.RUN.
- 88% of threats fully exposed within 60 seconds, giving analysts an immediate verdict to act on.
- 30% fewer Tier-1 to Tier-2 escalations, since interactive behavior analysis helps even junior analysts make confident decisions.
- 36% higher detection rate, thanks to real-time interactivity that forces evasive malware to reveal its actions.
| Ready to turn faster analysis into measurable ROI? Connect with ANY.RUN experts and discover what 20 minutes saved really means for your SOC. Talk to ANY.RUN Experts |
When you can see what the malware is doing the moment it runs, you detect and decide faster. And that’s how 20 minutes disappear from every incident, without adding new tools or headcount.
How Interactive Sandboxing Makes the Difference
Here’s how interactive sandboxes transforms your SOC workflow:
Fewer dead ends, faster context
Instead of chasing incomplete alerts or manually piecing together telemetry from multiple sources, analysts get a unified view of what’s happening. The sandbox correlates process behavior, registry modifications, file activity, network traffic, and MITRE ATT&CK techniques in real time.
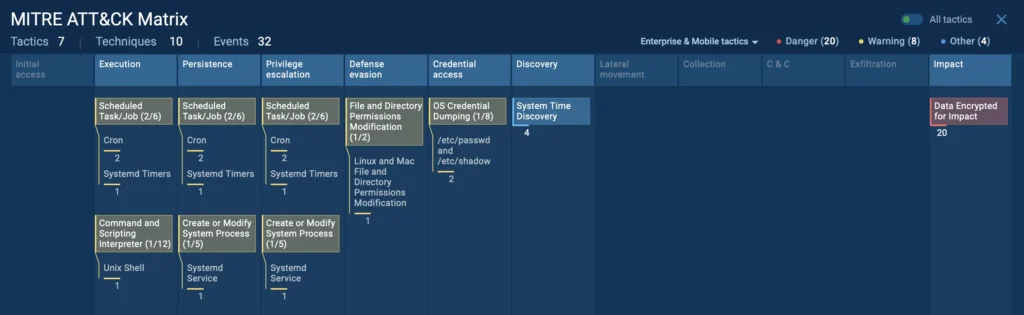
MITRE ATT&CK techniques detected by ANY.RUN sandbox
That means your team doesn’t waste cycles switching between SIEM, EDR, and packet capture tools; they see the full context in one interface and can make decisions faster, with fewer follow-up investigations.
Hidden threats exposed early
Many advanced threats don’t execute fully unless they detect user interaction; a click, a form entry, or a file open. Interactive sandboxes, such as ANY.RUN, reproduces those real conditions safely, forcing dormant payloads to reveal themselves.
View LockBit attack exposed fully in 30 seconds
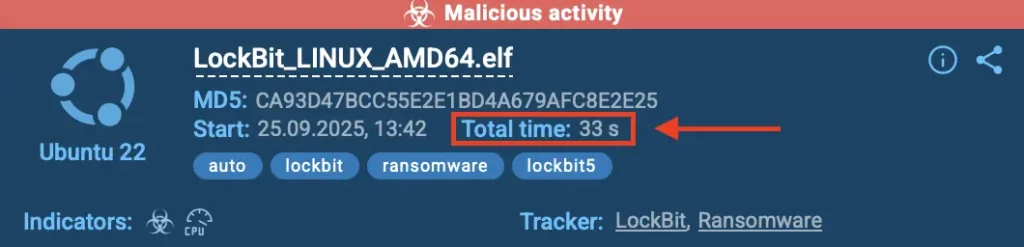
LockBit exposed with its full attack chain inside ANY.RUN sandbox in 33 seconds
This gives your SOC visibility into second-stage behavior that static scans often miss, allowing containment actions to start immediately and preventing lateral movement or data exfiltration.
Instant intelligence sharing
Once analysis is complete, the sandbox automatically extracts indicators of compromise (IOCs), correlates them with known TTPs, and maps activity to MITRE techniques.
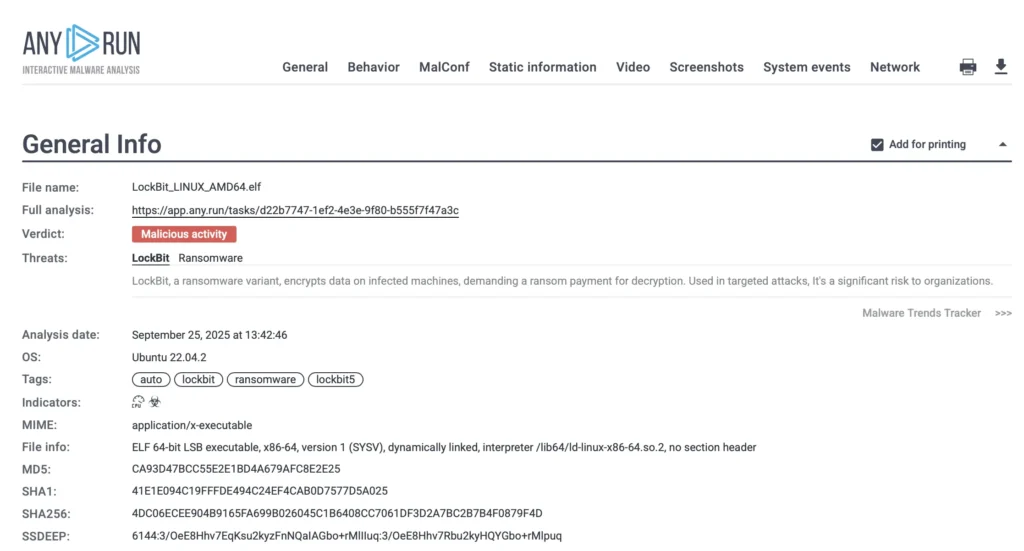
Well-structured report of LockBit attack for easy sharing and fast access to data
These results are instantly available through integrations with your SIEM, SOAR, or threat intelligence platform, meaning your team doesn’t have to manually copy data between systems.
Smarter resource allocation
By providing complete behavioral context upfront, the sandbox empowers Tier-1 analysts to resolve a large portion of alerts independently. This cuts unnecessary escalations by up to 30% and allows Tier-2 and Tier-3 experts to focus on complex, high-impact threats or proactive hunting.
Over time, this balances workloads, reduces burnout, and builds a more capable, confident team at every level.
Data-driven management
Interactive sandboxing doesn’t just improve investigations; it gives you metrics to prove it. Managers can track average time spent per case, escalation rates, and MTTR improvements across specific alert types. With that data, you can identify bottlenecks, quantify ROI, and demonstrate the operational value of faster analysis to executives or clients.
Transform Your SOC’s Speed Today
Faster detection comes from giving analysts the visibility and control they need to act without hesitation.
Interactive sandboxing is that catalyst. By revealing full attack behavior in seconds, cutting down escalations, and making every workflow measurable, it turns your SOC into a faster, more focused operation.
To lower MTTR and empower faster, smarter decisions, give your team what they need most; real visibility from the very first alert.
Contact ANY.RUN experts to learn how your SOC can save up to 20 minutes per incident and take investigation speed to the next level.



































