Running a Security Operations Center (SOC) is like playing a high-stakes game where the board keeps changing, the pieces shift on their own, and the consequences of missing a move can cost millions. Add to that the challenge of keeping up with evolving attack techniques and integrating new tools into already complex workflows, and it’s clear SOCs need more than just manpower: they need actionable, real-time intelligence to stay ahead.
Why Threat Intelligence Is SOC’s Secret Weapon
Threat intelligence is not just about knowing what threats are out there; it’s about understanding how they work, who’s behind them, and what they’re targeting. By providing detailed insights into Indicators of Compromise (IOCs), Indicators of Attack (IOAs), and Tactics, Techniques, and Procedures (TTPs), threat intelligence helps analysts prioritize alerts, accelerate investigations, and block attacks before they cause harm.
ANY.RUN’s Threat Intelligence Lookup: A Game-Changer for SOCs
Threat Intelligence Lookup transforms how security teams access and leverage threat intelligence. Unlike services that deliver static indicators with minimal context, TI Lookup provides intelligence derived from real malware analysis sessions of over 15,000 corporate security teams investigating actual attacks in their environments.
Here’s what makes this platform exceptional: every piece of intelligence comes with behavioral analysis. When you query a suspicious file hash, IP address, or domain, you don’t just get a “malicious” verdict. You get the full story – how the threat behaves, what it communicates with, how it attempts to persist, what data it seeks, and how it tries to evade detection.
| ANY.RUN’s threat intelligence is now available for FREE. Enrich IOCs with live attack data from investigations across 15K SOCs. Try it now! |
This intelligence is generated through ANY.RUN’s interactive sandbox, where security analysts can observe malware in action, document its capabilities, and share their findings with the broader security community.
When Intelligence Could Have Changed Everything
The 2023 MOVEit Supply Chain Attack
In May 2023, the Cl0p ransomware gang exploited a zero-day vulnerability in MOVEit, a widely used file transfer software. Over 2,600 organizations were hit, with data breaches costing companies like Maxar Technologies and Siemens Energy millions in recovery, legal fees, and lost business. The attack spread through supply chains, amplifying the damage. Threat intelligence could have made a difference by identifying early IOCs, such as malicious domains or file hashes, from sandbox analyses.
With services like ANY.RUN’s Threat Intelligence Lookup, SOCs could have correlated these indicators with real-time data from global malware submissions, enabling faster detection and blocking of the exploit before it reached critical systems.
The 2020 SolarWinds Orion Breach
The SolarWinds attack saw state-sponsored hackers compromise the Orion software, infiltrating thousands of organizations, including Fortune 500 companies and government agencies. The breach went undetected for months, leading to significant data theft and operational disruption. Threat intelligence feeds could have flagged unusual network traffic patterns or malicious IPs linked to the attackers’ command-and-control servers. By integrating real-time intelligence, SOCs could have identified and isolated compromised endpoints early, preventing widespread damage.
Threat Intelligence That Powers Business
ANY.RUN’s Threat Intelligence Lookup directly supports critical business and security objectives that keep organizations resilient in the face of evolving threats:
- Risk Reduction: Early detection of threats minimizes financial and reputational damage.
- Cost Efficiency: Faster investigations and fewer breaches cut operational costs.
- Compliance: Detailed reports and IOCs support regulatory requirements like GDPR and HIPAA.
- Strategic Planning: Insights into attack trends inform long-term security investments.
- Employee Training: Sandbox sessions provide real-world examples for training staff to spot threats.
By delivering actionable intelligence, TI Lookup helps businesses protect assets, maintain customer trust, and stay ahead of adversaries.
Now Free: Why This Is a Big Deal
In a bold move, ANY.RUN has made Threat Intelligence Lookup available on the free plan, democratizing access to elite-level intelligence. For security teams operating on constrained budgets, this is transformational. You can now investigate suspicious indicators with the same depth and context as Fortune 500 security operations centers. For growing organizations, it provides a pathway to build threat intelligence capabilities without significant upfront investment.
Here are a few examples of how TI Lookup works on the free plan:
Efficient Triage and Response
When suspicious domains appear in network traffic analysis, a quick request to TI Lookup provides actionable intelligence:
domainName:”www.chinaclean.xyz”
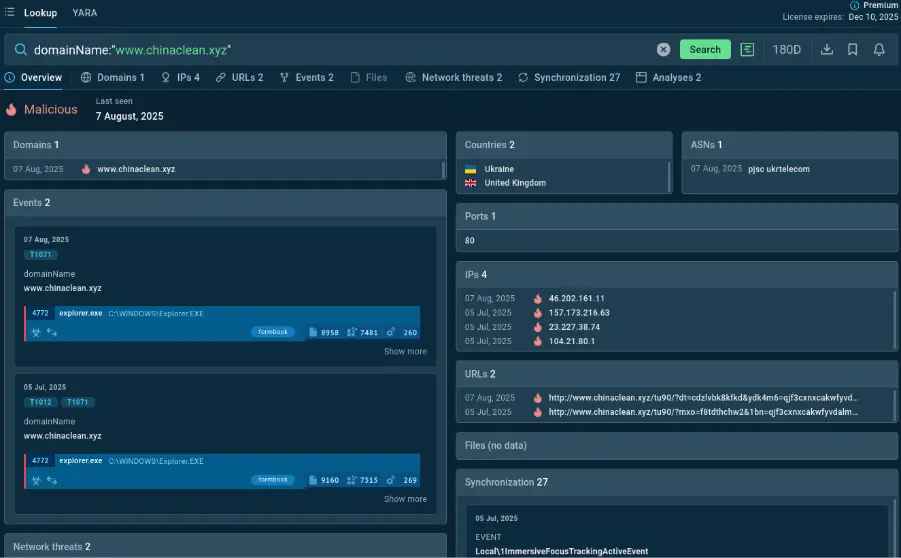
TI Lookup domain search results
The “Malicious” tag would be enough for incident escalation. But we also get a variety of other IOCs associated with the domain, several malware samples analyzed in ANY.RUN’s Sandbox that utilize the domain in question, and a ”last seen” date that lets us know that the domain has been spotted in most recent cyber incidents and is supposed to be a part of an active malicious infrastructure.
Threat Hunting for Proactive Defense
TI Lookup takes threat discovery to the next level fueling it with data on recent incidents and emerging threats. For instance, to assess whether specific malware targets particular geographic regions, combine the threat identifier with location data:
threatName:”tycoon” AND submissionCountry:”ca”
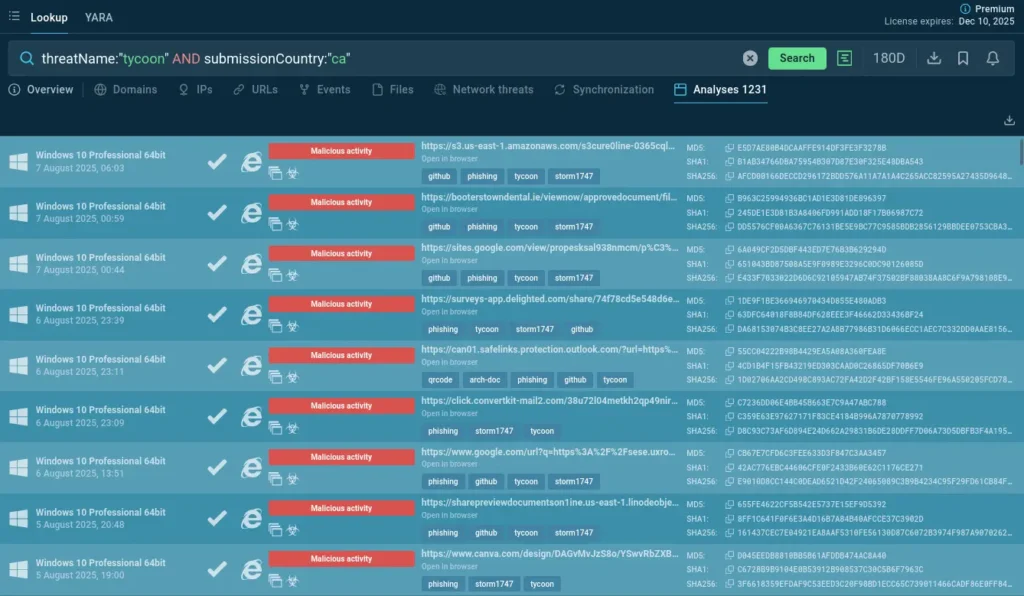
Recent Tycoon phishing operations targeting Canadian companies
Search results link to Interactive Sandbox public investigations of Tycoon 2FA phishing samples submitted by Canadian users. Each analysis session shows malware’s attack chain in details, and provides IOCs for monitoring and detection.
Advanced Proactive Security with ANY.RUN’s Premium Plan
When your security team targets ultimate operational efficiency, it’s the time for Premium upgrade. Maximize your KPIs and ROI:
- Cut Investigation Costs: Advanced search capabilities with 40+ parameters enable analysts to pinpoint threats in minutes rather than hours, dramatically cutting labor costs and accelerating incident resolution.
- Remove Security Blind Spots: Complete historical intelligence access provides comprehensive attack visibility, ensuring your team never misses critical threat patterns that could indicate ongoing campaigns against your organization.
- Shift to predictive security: Automated monitoring alerts enable your team to identify threats targeting your industry before they reach your infrastructure.
- Make Data-Driven Investments: Expert intelligence reports provide executive-level insights on emerging attack trends, enabling informed budget allocation and strategic security planning decisions.
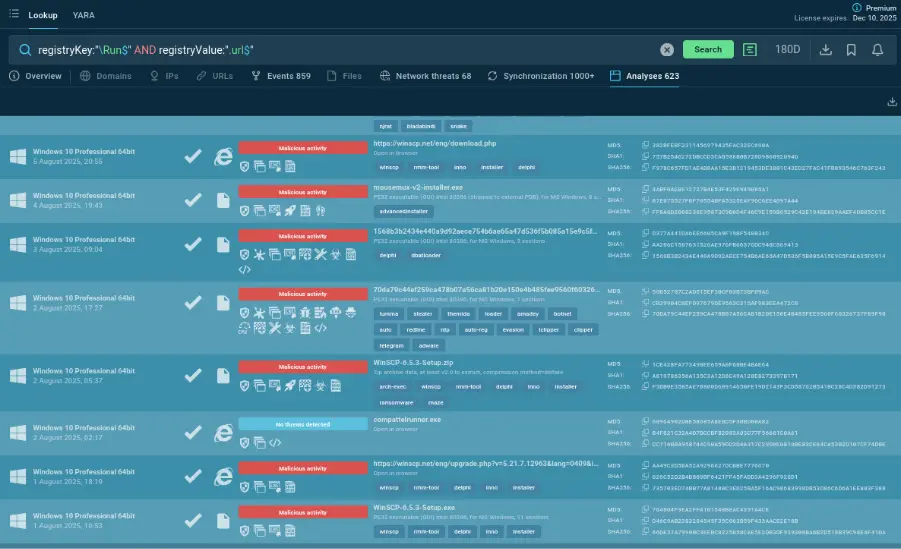
TI Lookup search on Premium plan: more options and results
Among the benefits of the Premium plan are over 40 search parameters and the unlimited access to sandbox analysis sessions relevant to the search request.
| Request Premium trial access to TI Lookup Cut MTTR, stop incidents early, and reduce business risks |
Transform Your SOC Starting Today
The cyber threat landscape will continue evolving, but your response doesn’t have to lag behind. ANY.RUN’s Threat Intelligence Lookup provides the intelligence foundation your security operations center needs to shift from reactive response to proactive defense.
Start using Threat Intelligence Lookup in your SOC immediately, and here’s what will improve most quickly:
- Investigation Speed: What used to require cross-referencing multiple databases and manual analysis now happens with a single query.
- Detection Confidence: When your monitoring tools flag suspicious activity, you’ll have immediate access to behavioral intelligence that confirms whether it’s a genuine threat or a false positive.
- Threat Context: Understanding not just what is malicious, but how it operates, what it targets, and how it fits into broader attack campaigns enables more strategic security decisions and better resource allocation.
- Team Expertise: Regular use of comprehensive threat intelligence naturally builds your team’s knowledge about current attack techniques, malware families, and threat actor behaviors.
- Organizational Resilience: Perhaps most importantly, access to real-time threat intelligence helps your organization stay ahead of the threats specifically targeting your industry, geography, and infrastructure.
The asymmetry that has favored attackers for too long is finally shifting. With solutions like ANY.RUN’s Threat Intelligence Lookup now freely available, security teams of all sizes can access the same intelligence that was once exclusive to the largest organizations.



































