Antivirus tools are great at spotting known threats but not the ones that hide. Modern malware often stays quiet during scans, waiting for a real system or a specific action before doing anything suspicious. If nothing happens, it stays invisible.
That’s the problem: antivirus engines don’t interact with files; they just look at them. So, if a threat needs to be opened, or clicked, it can easily slip through.
Let’s look at how you can detect these threats quickly without risking any damage.
Techniques Malware Uses to Evade Antivirus Engines
To avoid detection, malware often relies on techniques that help it stay hidden during scans and initial inspection. Here are some of the most common ones:
- Delayed execution – the malware stays inactive for a set time or until triggered
- User interaction dependency – it only runs after a specific action like clicking or opening a file
- Password-protected payloads – harmful files are hidden inside encrypted or locked archives
- Code obfuscation – malicious code is scrambled or encrypted to avoid recognition by scanners
These tactics are built to bypass the static analysis that most antivirus engines rely on, making detection harder and giving attackers more time to operate unnoticed.
Detecting Malware That Antivirus Missed: A Real-World Example
Although antivirus engines often miss these newer types of malware, interactive sandboxes like ANY.RUN can detect them in seconds. By actually running the file and simulating real user interaction, the sandbox can quickly reveal whether a file or link is malicious.
For security teams, this kind of fast, accurate detection means less time wasted on guesswork, fewer false positives, and faster incident response when it matters most.
Let’s take a look at a real SVG-based attack inside the sandbox to see how fast and easy detection can be.
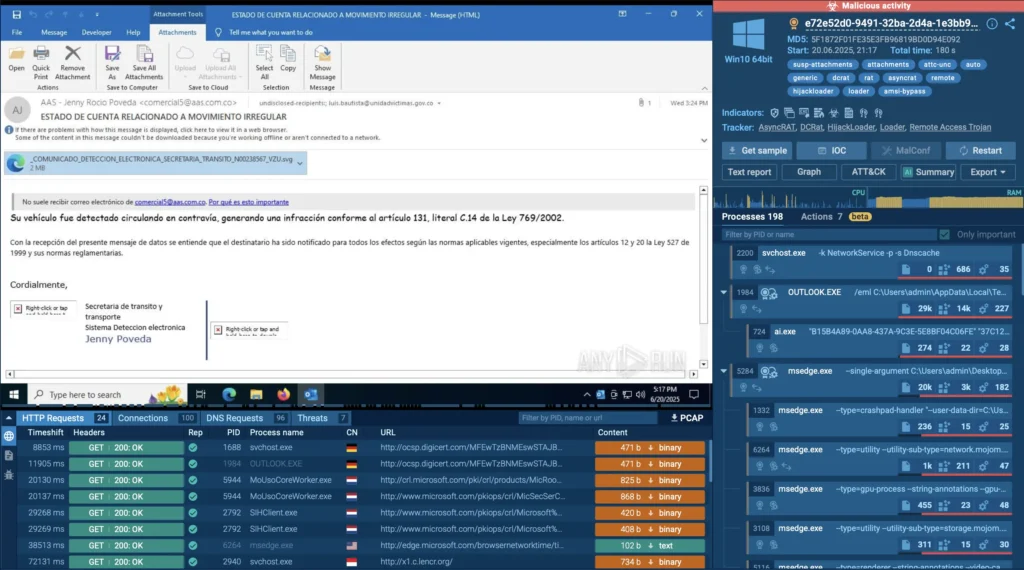
.svg file analyzed inside ANY.RUN’s sandbox
It starts with a phishing email that includes a seemingly harmless .svg file. Once you open it, you’re shown official-looking text and a fake fine notification. Embedded in that message is a link to download a supposed PDF attachment.
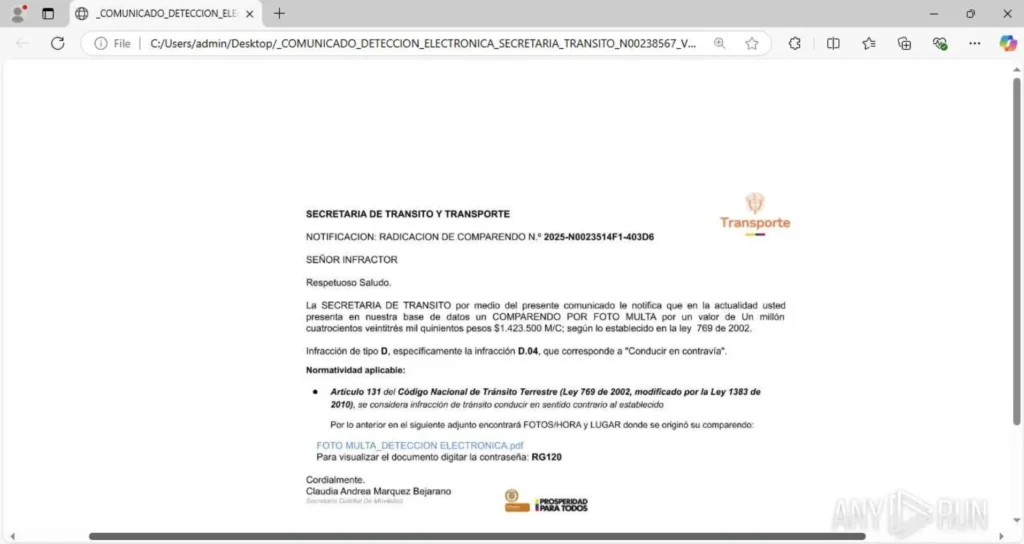
Malicious pdf attachment displayed inside ANY.RUN sandbox
But here’s where it gets tricky:
That “PDF” turns out to be a password-protected archive. Most antivirus engines won’t flag this because there’s nothing clearly malicious at this stage.
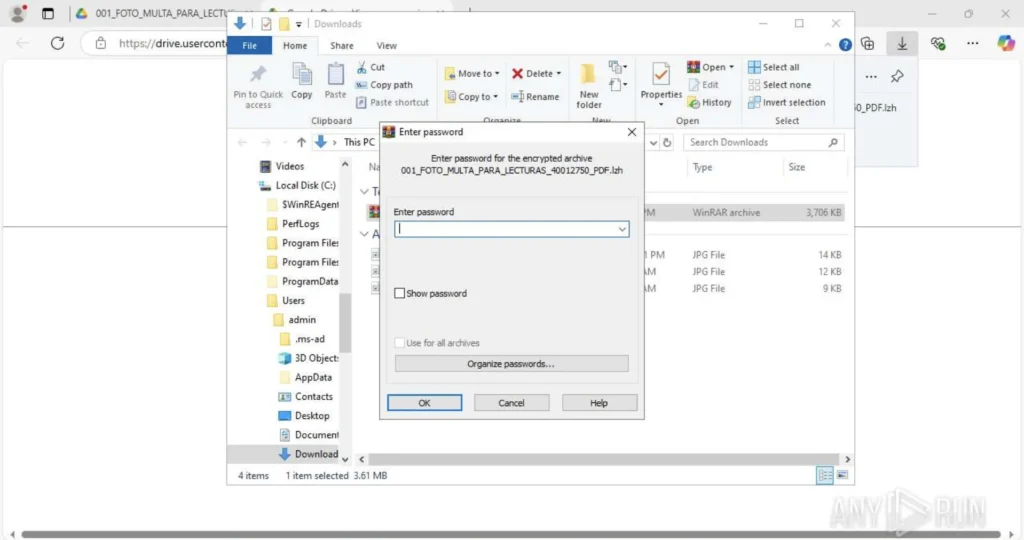
Password-protected archive exposed inside interactive sandbox
To move forward, you need to manually enter the password and open the archive, something static scanners and automated sandboxes can’t handle. This step requires human interaction.
| Cut investigation time, catch what antivirus misses, and get clear, real-time insights with ANY.RUN. Sign up now with your business email |
Inside the sandbox, that interaction becomes fast and risk-free. ANY.RUN displays the required actions on the right side of the screen, such as “opening an email attachment,” or “launching a file from the Startup directory.” You can approve each one with a single click, making it easy to detonate the attack safely and move forward. This saves time, reduces guesswork, and helps your team respond to threats faster.
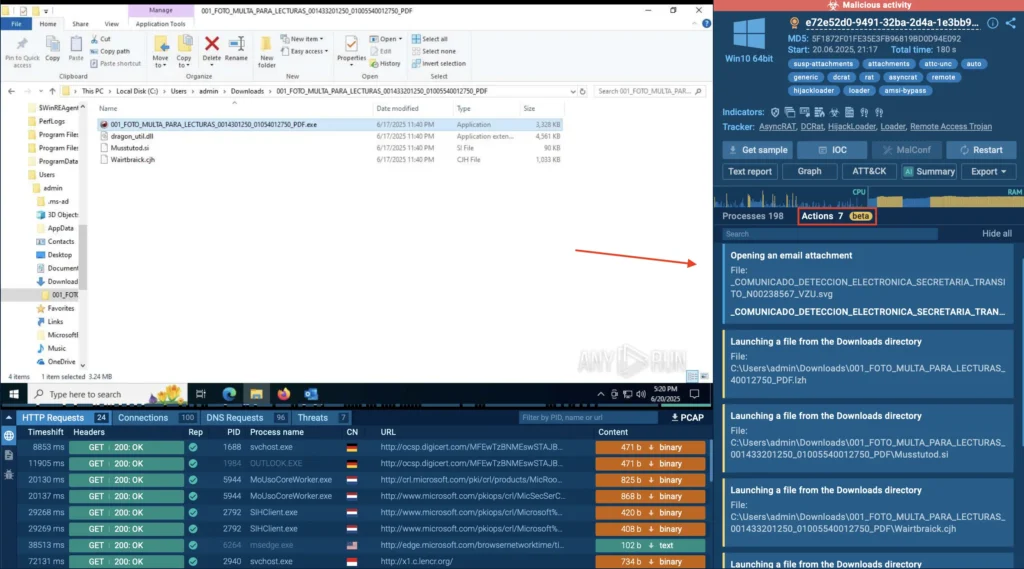
Interactive sandbox revealing actions needed to move forward in the attack
On the right side of the sandbox, the Process Tree shows each step the malware takes, along with its behavior, related MITRE ATT&CK techniques, threat level, and how it links to other system activity.
For instance, in the following process malicious .exe is revealed. The system immediately flags HijackLoader behavior. That “HijackLoader” label means the executable is part of a known malware loader family that injects or downloads other malicious payloads into the system.
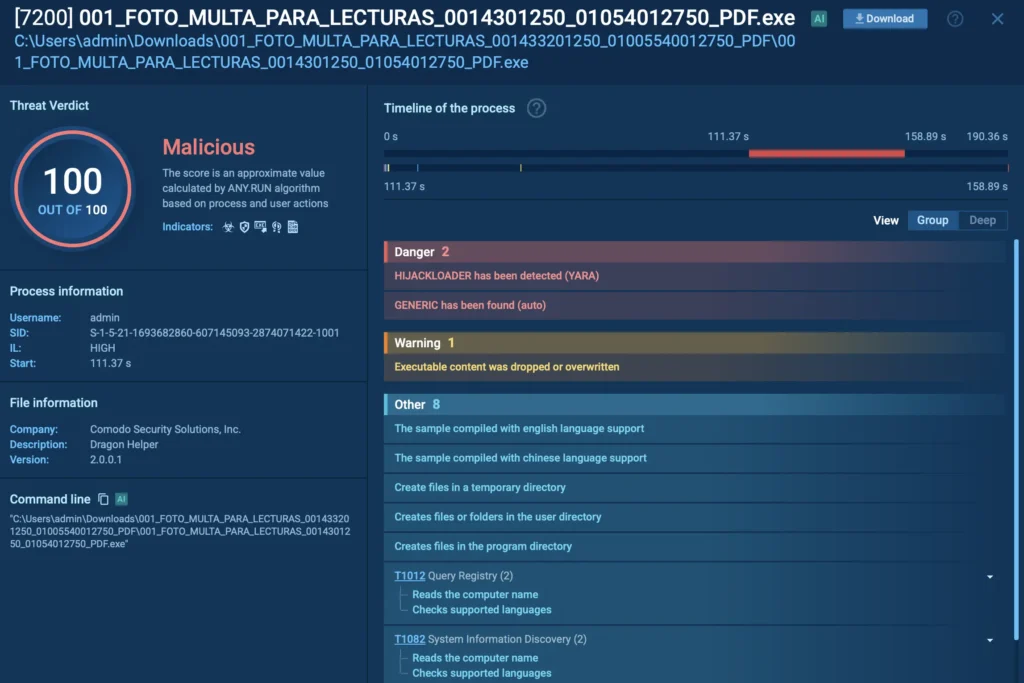
.exe file detected as malicious inside ANY.RUN sandbox
In the upper-right corner, we get an instant verdict on the attachment. Malicious activity is clearly highlighted in red, along with threat labels like HijackLoader, RAT, and more. These tags give immediate context about the type of attack we’re dealing with.
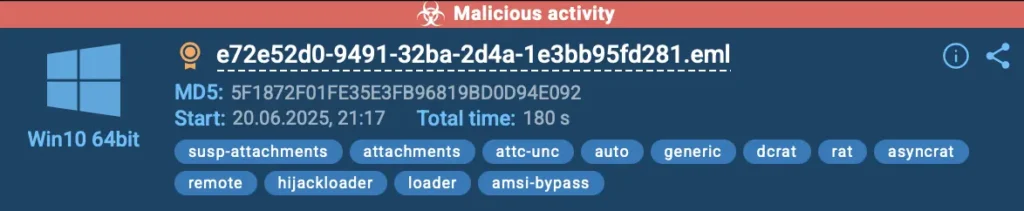
ANY.RUN provides a fast verdict and relevant threat labels to speed up response
This kind of fast, reliable detection is key, especially when dealing with malware designed to bypass antivirus tools. It helps your team act quickly, contain threats early, and avoid costly delays in investigation.
Why Fast Detection Makes a Difference
The faster your team can confirm whether a file is dangerous, the faster you can contain the threat, avoid escalation, and keep your operations running smoothly.
With advanced threats now designed to bypass traditional tools, fast detection gives you a critical edge. It means:
- Catching what others miss – even malware hidden behind user actions or encrypted files
- Reducing investigation time – no more digging through logs or guessing based on limited alerts
- Responding with clarity – when you know exactly what you’re dealing with, you act faster and smarter
- Protecting your business and brand – minimize risk, avoid costly breaches, and build trust with customers and stakeholders
Sign up now with your business email and start detecting threats with speed and confidence.



































