Network Object Access! Source IP is internal, False-positives? NO !! This event generates every time the network share object was modified which means file permissions are changed either by users or adversaries. Hunting the permission changes with Security Identifiers ( SID ) will provide more insights on attacker files and a special set of permissions assigned by the intruders.
What are Security Identifiers?
Each account in the Windows operating systems will be tagged to a SID Number that looks something like this. S-1-5-21-40882390-58657388-3385413796-500 , These SIDs will identify the user’s security group or security principal. Security Principle represents any unit that can be authenticated by the operating systems, user account, computer account, or a thread or process that runs on the machine.
Security principles will be controlling access to securable resources on Windows computers. Next time a user signs in, the system creates an access token for that user. The access token contains the user’s SID, user rights, and the SIDs for any groups the user belongs to. This token provides the security context for whatever actions the user performs on that computer.
Domain-specific SIDs that are assigned to specific users and groups, there are well-known SIDs that identify generic groups and generic users. SIDs are a fundamental building block of the Windows security model. They work with specific components of the authorization and access control technologies in the security infrastructure of the Windows Server operating systems. This helps protect access to network resources and provides a more secure computing environment.
SID is represented in the format – S-R-X-Y1-Y2-Yn-1-Yn
S – denotes Indicates that the string is a SID
R – Indicates the revision level
X – Indicates the identifier authority value
Y – Represents a series of sub authority values, where n is the number of values
In this example, (-Y1-Y2-Yn-1) is the domain identifier – For Example: XYZ company PVT ltd
-Yn – Represents and distinguishes one account or group from all other accounts and groups in the domain.
Also Read : Soc Interview Questions and Answers – CYBER SECURITY ANALYST
SID Information Extraction:
Windows Management Instrumentation Command-line can be used to retrieve the information of accounts and their respective Sids.
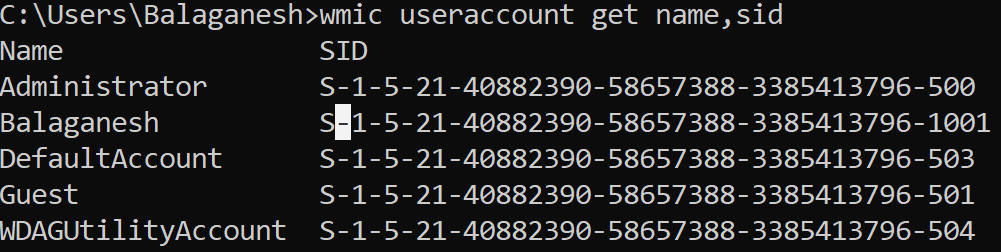
Breaking the SID Structure & Well-Known SIDs :
The following table lists the universal well-known SIDs.
For Example : Administrator S-1-5-21-40882390-58657388-3385413796-500
Above SID – S-1-5 represents the NT authority and 21-40882390-58657388-3385413796 represents domain identifier and 500 is account-level information which is RID. 500 is unique and it only is tagged to the admin account.
| Value | Universal Well-Known SID | Identifies |
|---|---|---|
| S-1-0-0 | Null SID | A group with no members. This is often used when a SID value is not known. |
| S-1-1-0 | World | A group that includes all users. |
| S-1-2-0 | Local | Users who log on to terminals that are locally (physically) connected to the system. |
| S-1-2-1 | Console Logon | A group that includes users who are logged on to the physical console. |
| S-1-3-0 | Creator Owner ID | A security identifier to be replaced by the security identifier of the user who created a new object. This SID is used in inheritable ACEs. |
| S-1-3-1 | Creator Group ID | A security identifier to be replaced by the primary-group SID of the user who created a new object. Use this SID in inheritable ACEs. |
| S-1-3-2 | Creator Owner Server | |
| S-1-3-3 | Creator Group Server | |
| S-1-3-4 | Owner Rights | A group that represents the current owner of the object. When an ACE that carries this SID is applied to an object, the system ignores the implicit READ_CONTROL and WRITE_DAC permissions for the object owner. |
| S-1-4 | Non-unique Authority | A SID that represents an identifier authority. |
| S-1-5 | NT Authority | A SID that represents an identifier authority. |
| S-1-5-80-0 | All Services | A group that includes all service processes configured on the system. Membership is controlled by the operating system. |
Also Read: Threat Hunting Using Windows Security Log
Identifier Authority:
| SID | Display Name | Description |
|---|---|---|
| S-1-5-1 | Dialup | A group that includes all users who are logged on to the system by means of a dial-up connection. |
| S-1-5-113 | Local account | You can use this SID when restricting network logon to local accounts instead of “administrator” or equivalent. This SID can be effective in blocking network logon for local users and groups by account type regardless of what they are actually named. |
| S-1-5-114 | Local account and member of Administrators group | You can use this SID when restricting network logon to local accounts instead of “administrator” or equivalent. This SID can be effective in blocking network logon for local users and groups by account type regardless of what they are actually named. |
| S-1-5-2 | Network | A group that includes all users who are logged on by means of a network connection. Access tokens for interactive users do not contain the Network SID. |
| S-1-5-3 | Batch | A group that includes all users who have logged on by means of a batch queue facility, such as task scheduler jobs. |
| S-1-5-4 | Interactive | A group that includes all users who log on interactively. A user can start an interactive logon session by logging on directly at the keyboard, by opening a Remote Desktop Services connection from a remote computer, or by using a remote shell such as Telnet. In each case, the user’s access token contains the Interactive SID. If the user signs in by using a Remote Desktop Services connection, the user’s access token also contains the Remote Interactive Logon SID. |
| S-1-5-5- X–Y | Logon Session | The X and Y values for these SIDs uniquely identify a particular logon session. |
| S-1-5-6 | Service | A group that includes all security principals that have signed in as a service. |
| S-1-5-7 | Anonymous Logon | A user who has connected to the computer without supplying a user name and password. The Anonymous Logon identity is different from the identity that is used by Internet Information Services (IIS) for anonymous web access. IIS uses an actual account—by default, IUSR_ ComputerName, for anonymous access to resources on a website. Strictly speaking, such access is not anonymous because the security principal is known even though unidentified people are using the account. IUSR_ ComputerName (or whatever you name the account) has a password, and IIS logs on the account when the service starts. As a result, the IIS “anonymous” user is a member of Authenticated Users but Anonymous Logon is not. |
| S-1-5-8 | Proxy | Does not currently apply: this SID is not used. |
| S-1-5-9 | Enterprise Domain Controllers | A group that includes all domain controllers in a forest of domains. |
| S-1-5-10 | Self | A placeholder in an ACE for a user, group, or computer object in Active Directory. When you grant permissions to Self, you grant them to the security principal that is represented by the object. During an access check, the operating system replaces the SID for Self with the SID for the security principal that is represented by the object. |
| S-1-5-11 | Authenticated Users | A group that includes all users and computers with identities that have been authenticated. Authenticated Users does not include Guest even if the Guest account has a password. This group includes authenticated security principals from any trusted domain, not only the current domain. |
| S-1-5-12 | Restricted Code | An identity that is used by a process that is running in a restricted security context. In Windows and Windows Server operating systems, a software restriction policy can assign one of three security levels to code: unrestricted, restricted, or disallowed. When code runs at the restricted security level, the Restricted SID is added to the user’s access token. |
| S-1-5-13 | Terminal Server User | A group that includes all users who sign in to a server with Remote Desktop Services enabled. |
| S-1-5-14 | Remote Interactive Logon | A group that includes all users who log on to the computer by using a remote desktop connection. This group is a subset of the Interactive group. Access tokens that contain the Remote Interactive Logon SID also contain the Interactive SID. |
| S-1-5-15 | This Organization | A group that includes all users from the same organization. Only included with Active Directory accounts and only added by a domain controller. |
| S-1-5-17 | IIS_USRS | An account that is used by the default Internet Information Services (IIS) user. |
| S-1-5-18 | System (or LocalSystem) | An identity that is used locally by the operating system and by services that are configured to sign in as LocalSystem. System is a hidden member of Administrators. That is, any process running as System has the SID for the built-in Administrators group in its access token. When a process that is running locally as System accesses network resources, it does so by using the computer’s domain identity. Its access token on the remote computer includes the SID for the local computer’s domain account plus SIDs for security groups that the computer is a member of, such as Domain Computers and Authenticated Users. |
| S-1-5-19 | NT Authority (LocalService) | An identity that is used by services that are local to the computer, have no need for extensive local access, and do not need authenticated network access. Services that run as LocalService access local resources as ordinary users, and they access network resources as anonymous users. As a result, a service that runs as LocalService has significantly less authority than a service that runs as LocalSystem locally and on the network. |
| S-1-5-20 | Network Service | An identity that is used by services that have no need for extensive local access but do need authenticated network access. Services running as NetworkService access local resources as ordinary users and access network resources by using the computer’s identity. As a result, a service that runs as NetworkService has the same network access as a service that runs as LocalSystem, but it has significantly reduced local access. |
| S-1-5-domain-500 | Administrator | A user account for the system administrator. Every computer has a local Administrator account and every domain has a domain Administrator account. The Administrator account is the first account created during operating system installation. The account cannot be deleted, disabled, or locked out, but it can be renamed. By default, the Administrator account is a member of the Administrators group, and it cannot be removed from that group. |
| S-1-5-domain-501 | Guest | A user account for people who do not have individual accounts. Every computer has a local Guest account, and every domain has a domain Guest account. By default, Guest is a member of the Everyone and the Guests groups. The domain Guest account is also a member of the Domain Guests and Domain Users groups. Unlike Anonymous Logon, Guest is a real account, and it can be used to log on interactively. The Guest account does not require a password, but it can have one. |
| S-1-5-domain-502 | krbtgt | A user account that is used by the Key Distribution Center (KDC) service. The account exists only on domain controllers. |
| S-1-5-domain-512 | Domain Admins | A global group with members that are authorized to administer the domain. By default, the Domain Admins group is a member of the Administrators group on all computers that have joined the domain, including domain controllers. Domain Admins is the default owner of any object that is created in the domain’s Active Directory by any member of the group. If members of the group create other objects, such as files, the default owner is the Administrators group. |
| S-1-5-domain-513 | Domain Users | A global group that includes all users in a domain. When you create a new User object in Active Directory, the user is automatically added to this group. |
| S-1-5-domain-514 | Domain Guests | A global group, which by default, has only one member: the domain’s built-in Guest account. |
| S-1-5-domain-515 | Domain Computers | A global group that includes all computers that have joined the domain, excluding domain controllers. |
| S-1-5-domain-516 | Domain Controllers | A global group that includes all domain controllers in the domain. New domain controllers are added to this group automatically. |
| S-1-5-domain-517 | Cert Publishers | A global group that includes all computers that host an enterprise certification authority. Cert Publishers are authorized to publish certificates for User objects in Active Directory. |
| S-1-5-root domain-518 | Schema Admins | A group that exists only in the forest root domain. It is a universal group if the domain is in native mode, and it is a global group if the domain is in mixed mode. The Schema Admins group is authorized to make schema changes in Active Directory. By default, the only member of the group is the Administrator account for the forest root domain. |
| S-1-5-root domain-519 | Enterprise Admins | A group that exists only in the forest root domain. It is a universal group if the domain is in native mode, and it is a global group if the domain is in mixed mode. The Enterprise Admins group is authorized to make changes to the forest infrastructure, such as adding child domains, configuring sites, authorizing DHCP servers, and installing enterprise certification authorities. By default, the only member of Enterprise Admins is the Administrator account for the forest root domain. The group is a default member of every Domain Admins group in the forest. |
| S-1-5-domain-520 | Group Policy Creator Owners | A global group that is authorized to create new Group Policy Objects in Active Directory. By default, the only member of the group is Administrator. Objects that are created by members of Group Policy Creator Owners are owned by the individual user who creates them. In this way, the Group Policy Creator Owners group is unlike other administrative groups (such as Administrators and Domain Admins). Objects that are created by members of these groups are owned by the group rather than by the individual. |
| S-1-5-domain-553 | RAS and IAS Servers | A local domain group. By default, this group has no members. Computers that are running the Routing and Remote Access service are added to the group automatically. Members of this group have access to certain properties of User objects, such as Read Account Restrictions, Read Logon Information, and Read Remote Access Information. |
| S-1-5-32-544 | Administrators | A built-in group. After the initial installation of the operating system, the only member of the group is the Administrator account. When a computer joins a domain, the Domain Admins group is added to the Administrators group. When a server becomes a domain controller, the Enterprise Admins group also is added to the Administrators group. |
| S-1-5-32-545 | Users | A built-in group. After the initial installation of the operating system, the only member is the Authenticated Users group. |
| S-1-5-32-546 | Guests | A built-in group. By default, the only member is the Guest account. The Guests group allows occasional or one-time users to log on with limited privileges to a computer’s built-in Guest account. |
| S-1-5-32-547 | Power Users | A built-in group. By default, the group has no members. Power users can create local users and groups; modify and delete accounts that they have created; and remove users from the Power Users, Users, and Guests groups. Power users also can install programs; create, manage, and delete local printers; and create and delete file shares. |
| S-1-5-32-548 | Account Operators | A built-in group that exists only on domain controllers. By default, the group has no members. By default, Account Operators have permission to create, modify, and delete accounts for users, groups, and computers in all containers and organizational units of Active Directory except the Builtin container and the Domain Controllers OU. Account Operators do not have permission to modify the Administrators and Domain Admins groups, nor do they have permission to modify the accounts for members of those groups. |
| S-1-5-32-549 | Server Operators | Description: A built-in group that exists only on domain controllers. By default, the group has no members. Server Operators can log on to a server interactively; create and delete network shares; start and stop services; back up and restore files; format the hard disk of the computer; and shut down the computer. |
| S-1-5-32-550 | Print Operators | A built-in group that exists only on domain controllers. By default, the only member is the Domain Users group. Print Operators can manage printers and document queues. |
| S-1-5-32-551 | Backup Operators | A built-in group. By default, the group has no members. Backup Operators can back up and restore all files on a computer, regardless of the permissions that protect those files. Backup Operators also can log on to the computer and shut it down. |
| S-1-5-32-552 | Replicators | A built-in group that is used by the File Replication service on domain controllers. By default, the group has no members. Do not add users to this group. |
| S-1-5-32-554 | Builtin\Pre-Windows 2000 Compatible Access | An alias added by Windows 2000. A backward compatibility group that allows read access on all users and groups in the domain. |
| S-1-5-32-555 | Builtin\Remote Desktop Users | An alias. Members in this group are granted the right to log on remotely. |
| S-1-5-32-556 | Builtin\Network Configuration Operators | An alias. Members in this group can have some administrative privileges to manage configuration of networking features. |
| S-1-5-32-557 | Builtin\Incoming Forest Trust Builders | An alias. Members of this group can create incoming, one-way trusts to this forest. |
| S-1-5-32-558 | Builtin\Performance Monitor Users | An alias. Members of this group have remote access to monitor this computer. |
| S-1-5-32-559 | Builtin\Performance Log Users | An alias. Members of this group have remote access to schedule logging of performance counters on this computer. |
| S-1-5-32-560 | Builtin\Windows Authorization Access Group | An alias. Members of this group have access to the computed tokenGroupsGlobalAndUniversal attribute on User objects. |
| S-1-5-32-561 | Builtin\Terminal Server License Servers | An alias. A group for Terminal Server License Servers. When Windows Server 2003 Service Pack 1 is installed, a new local group is created. |
| S-1-5-32-562 | Builtin\Distributed COM Users | An alias. A group for COM to provide computer-wide access controls that govern access to all call, activation, or launch requests on the computer. |
| S-1-5-32-569 | Builtin\Cryptographic Operators | A built-in local group. Members are authorized to perform cryptographic operations. |
| S-1-5-32-573 | Builtin\Event Log Readers | A built-in local group. Members of this group can read event logs from local computer. |
| S-1-5-32-574 | Builtin\Certificate Service DCOM Access | A built-in local group. Members of this group are allowed to connect to Certification Authorities in the enterprise. |
| S-1-5-32-575 | Builtin\RDS Remote Access Servers | A built-in local group. Servers in this group enable users of RemoteApp programs and personal virtual desktops access to these resources. In Internet-facing deployments, these servers are typically deployed in an edge network. This group needs to be populated on servers running RD Connection Broker. RD Gateway servers and RD Web Access servers used in the deployment need to be in this group. |
| S-1-5-32-576 | Builtin\RDS Endpoint Servers | A built-in local group. Servers in this group run virtual machines and host sessions where users RemoteApp programs and personal virtual desktops run. This group needs to be populated on servers running RD Connection Broker. RD Session Host servers and RD Virtualization Host servers used in the deployment need to be in this group. |
| S-1-5-32-577 | Builtin\RDS Management Servers | A builtin local group. Servers in this group can perform routine administrative actions on servers running Remote Desktop Services. This group needs to be populated on all servers in a Remote Desktop Services deployment. The servers running the RDS Central Management service must be included in this group. |
| S-1-5-32-578 | Builtin\Hyper-V Administrators | A built-in local group. Members of this group have complete and unrestricted access to all features of Hyper-V. |
| S-1-5-32-579 | Builtin\Access Control Assistance Operators | A built-in local group. Members of this group can remotely query authorization attributes and permissions for resources on this computer. |
| S-1-5-32-580 | Builtin\Remote Management Users | A built-in local group. Members of this group can access WMI resources over management protocols (such as WS-Management via the Windows Remote Management service). This applies only to WMI namespaces that grant access to the user. |
| S-1-5-64-10 | NTLM Authentication | A SID that is used when the NTLM authentication package authenticated the client |
| S-1-5-64-14 | SChannel Authentication | A SID that is used when the SChannel authentication package authenticated the client. |
| S-1-5-64-21 | Digest Authentication | A SID that is used when the Digest authentication package authenticated the client. |
| S-1-5-80 | NT Service | A SID that is used as an NT Service account prefix. |
| S-1-5-80-0 | All Services | A group that includes all service processes that are configured on the system. Membership is controlled by the operating system. SID S-1-5-80-0 equals NT SERVICES\ALL SERVICES. This SID was introduced in Windows Server 2008 R2. |
| S-1-5-83-0 | NT VIRTUAL MACHINE\Virtual Machines | A built-in group. The group is created when the Hyper-V role is installed. Membership in the group is maintained by the Hyper-V Management Service (VMMS). This group requires the Create Symbolic Links right (SeCreateSymbolicLinkPrivilege), and also the Log on as a Service right (SeServiceLogonRight). |
| S-1-16-0 | Untrusted Mandatory Level | A SID that represents an untrusted integrity level. |
| S-1-16-4096 | Low Mandatory Level | A SID that represents a low integrity level. |
| S-1-16-8192 | Medium Mandatory Level | This SID represents a medium integrity level. |
| S-1-16-8448 | Medium Plus Mandatory Level | A SID that represents a medium plus integrity level. |
| S-1-16-12288 | High Mandatory Level | A SID that represents a high integrity level. |
| S-1-16-16384 | System Mandatory Level | A SID that represents a system integrity level. |
| S-1-16-20480 | Protected Process Mandatory Level | A SID that represents a protected-process integrity level. |
| S-1-16-28672 | Secure Process Mandatory Level | A SID that represents a secure process integrity level. |
Also Read: What is Threat Intelligence – Importance , CTI Lifecycle & Pyramid of Pain
RIDs relative to each domain
| RID | Decimal value | Identifies |
|---|---|---|
| DOMAIN_USER_RID_ADMIN | 500 | The administrative user account in a domain. |
| DOMAIN_USER_RID_GUEST | 501 | The guest-user account in a domain. Users who do not have an account can automatically sign in to this account. |
| DOMAIN_GROUP_RID_USERS | 513 | A group that contains all user accounts in a domain. All users are automatically added to this group. |
| DOMAIN_GROUP_RID_GUESTS | 514 | The group Guest account in a domain. |
| DOMAIN_GROUP_RID_COMPUTERS | 515 | The Domain Computer group. All computers in the domain are members of this group. |
| DOMAIN_GROUP_RID_CONTROLLERS | 516 | The Domain Controller group. All domain controllers in the domain are members of this group. |
| DOMAIN_GROUP_RID_CERT_ADMINS | 517 | The certificate publishers’ group. Computers running Active Directory Certificate Services are members of this group. |
| DOMAIN_GROUP_RID_SCHEMA_ADMINS | 518 | The schema administrators’ group. Members of this group can modify the Active Directory schema. |
| DOMAIN_GROUP_RID_ENTERPRISE_ADMINS | 519 | The enterprise administrators’ group. Members of this group have full access to all domains in the Active Directory forest. Enterprise administrators are responsible for forest-level operations such as adding or removing new domains. |
| DOMAIN_GROUP_RID_POLICY_ADMINS | 520 | The policy administrators’ group. |
| RID | Decimal value | Identifies |
|---|---|---|
| DOMAIN_ALIAS_RID_ADMINS | 544 | Administrators of the domain. |
| DOMAIN_ALIAS_RID_USERS | 545 | All users in the domain. |
| DOMAIN_ALIAS_RID_GUESTS | 546 | Guests of the domain. |
| DOMAIN_ALIAS_RID_POWER_USERS | 547 | A user or a set of users who expect to treat a system as if it were their personal computer rather than as a workstation for multiple users. |
| DOMAIN_ALIAS_RID_BACKUP_OPS | 551 | A local group that is used to control the assignment of file backup-and-restore user rights. |
| DOMAIN_ALIAS_RID_REPLICATOR | 552 | A local group that is responsible for copying security databases from the primary domain controller to the backup domain controllers. These accounts are used only by the system. |
| DOMAIN_ALIAS_RID_RAS_SERVERS | 553 | A local group that represents remote access and servers running Internet Authentication Service (IAS). This group permits access to various attributes of User objects. |
Hunting with Event ID 5143 and relative SIDs:
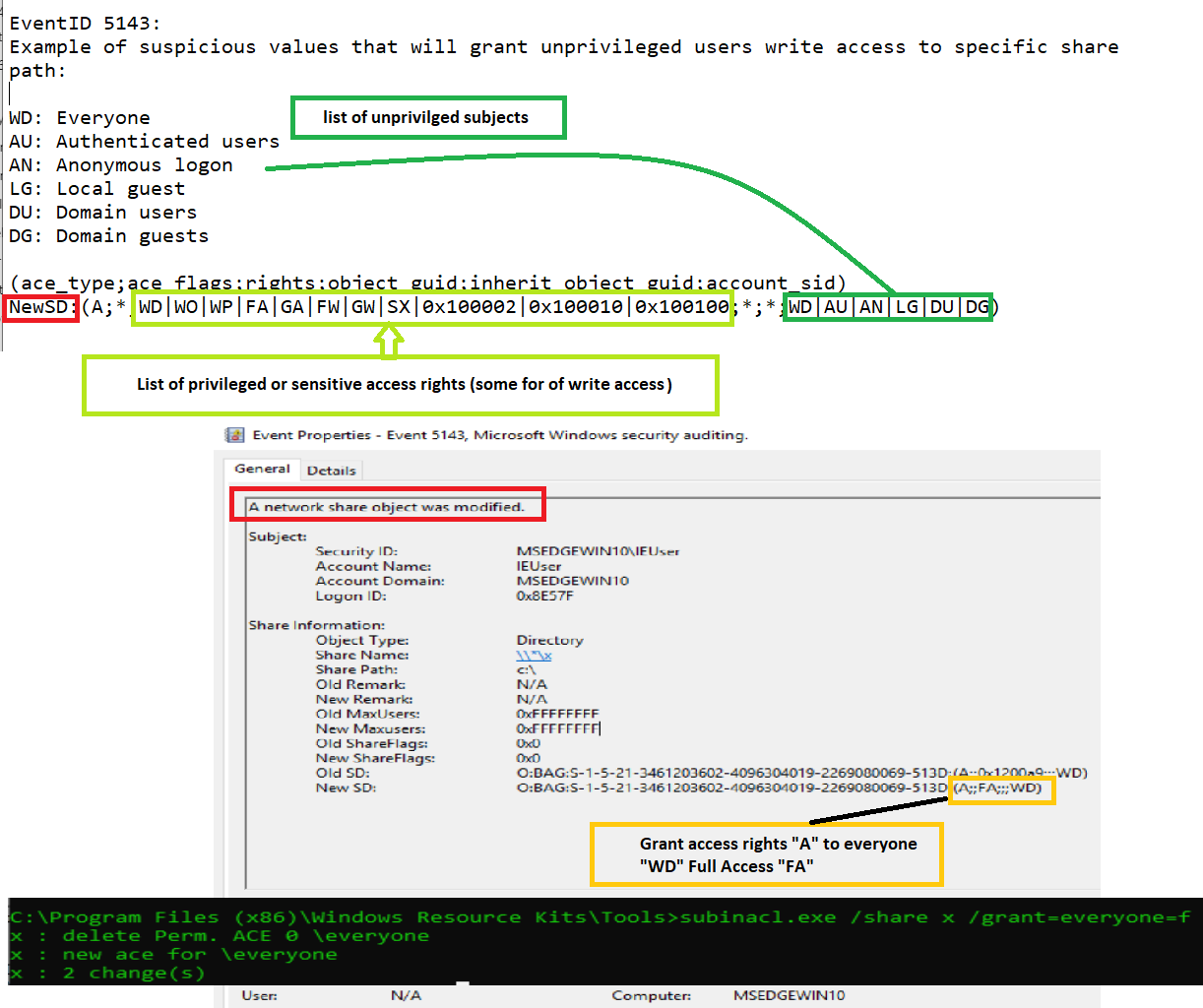
- Event ID 5143 which indicate the file permission was modified and checking the specfic share information in the logs will provide you the old SID and new SID.
- Old SID shows the user account or domain has specfic set of permission in past and New SID indicates that permissions were modified , If Event ID 5143 with New SID has the values ( A;;FA;;;WD ) means everyone access allowed ( A ) full access ( FA ) Modify Permission ( WD ) , Theses shows the attacker or insider has modified the file permission to all, Possible use cases pre-attack phase malwares changes the specfic permissions and execute it later and spread infection in network,In such cases Event ID 5145 is triggered.
- Ace type ( access control entry ) from this SID has the values ( A;;FA;;;WD ) , were “A” which is allow access.
- Event ID 5143 with suspicious file modifications can be observed using the SSDL values.
- Hunting the SDDL values (Security Descriptor Definition Language). Values next to New SID ( ( A;;FA;;;WD ) will provide the key insights of attack.
- Using the SSDL Values hunt table ,entry Type,ace_type,ace_flags,rights. Analyst can determine the suspicious files in the network and more hunting use cases can be developed.
SDDL values for Access Control Entry
| Value | Description | Value | Description |
|---|---|---|---|
| “AO” | Account operators | “PA” | Group Policy administrators |
| “RU” | Alias to allow previous Windows 2000 | “IU” | Interactively logged-on user |
| “AN” | Anonymous logon | “LA” | Local administrator |
| “AU” | Authenticated users | “LG” | Local guest |
| “BA” | Built-in administrators | “LS” | Local service account |
| “BG” | Built-in guests | “SY” | Local system |
| “BO” | Backup operators | “NU” | Network logon user |
| “BU” | Built-in users | “NO” | Network configuration operators |
| “CA” | Certificate server administrators | “NS” | Network service account |
| “CG” | Creator group | “PO” | Printer operators |
| “CO” | Creator owner | “PS” | Personal self |
| “DA” | Domain administrators | “PU” | Power users |
| “DC” | Domain computers | “RS” | RAS servers group |
| “DD” | Domain controllers | “RD” | Terminal server users |
| “DG” | Domain guests | “RE” | Replicator |
| “DU” | Domain users | “RC” | Restricted code |
| “EA” | Enterprise administrators | “SA” | Schema administrators |
| “ED” | Enterprise domain controllers | “SO” | Server operators |
| “WD” | Everyone | “SU” | Service logon user |
- G: = Primary Group.
- D: = DACL Entries ( System access control list )
- S: = SACL Entries. ( Discretionary access control list )
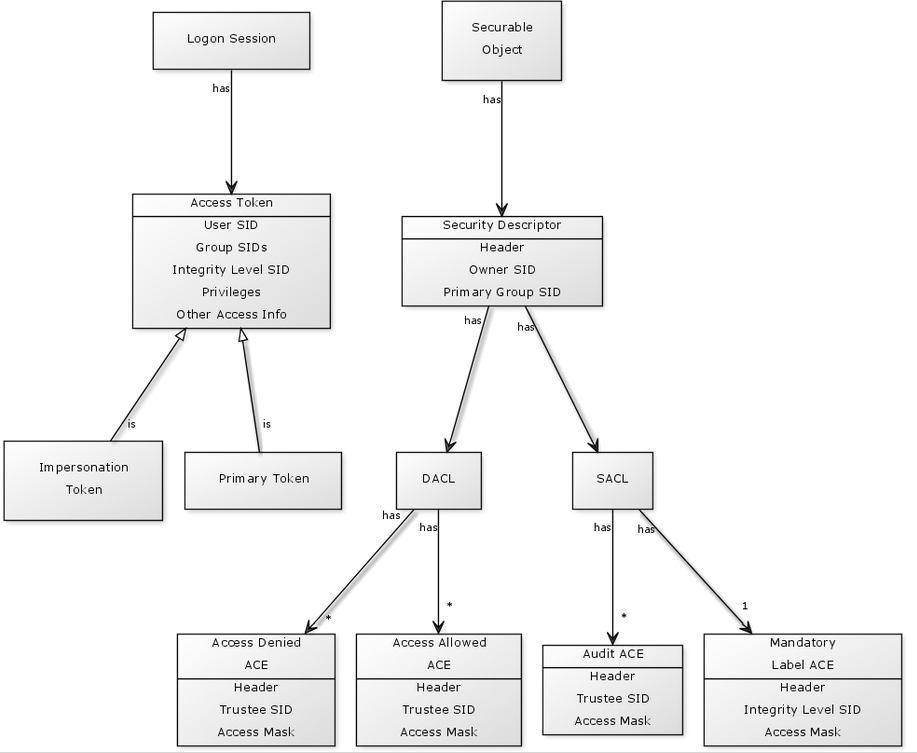
DACL/SACL entry format: entry_type:inheritance_flags(ace_type;ace_flags;rights;object_guid;inherit_object_guid;account_sid)
Example: D:(A;;FA;;;WD)
- Entry_type:
“D” – DACL
“S” – SACL
- Inheritance_flags:
“P” – SDDL_PROTECTED, Inheritance from containers that are higher in the folder hierarchy are blocked.
“AI” – SDDL_AUTO_INHERITED, Inheritance is allowed, assuming that “P” Is not also set.
“AR” – SDDL_AUTO_INHERIT_REQ, Child objects inherit permissions from this object.
- Ace_type: ( Access control entry )
“A” – ACCESS ALLOWED
“D” – ACCESS DENIED
“OA” – OBJECT ACCESS ALLOWED: only applies to a subset of the object(s).
“OD” – OBJECT ACCESS DENIED: only applies to a subset of the object(s).
“AU” – SYSTEM AUDIT
“A” – SYSTEM ALARM
“OU” – OBJECT SYSTEM AUDIT
“OL” – OBJECT SYSTEM ALARM
- Ace_flags:
“CI” – CONTAINER INHERIT: Child objects that are containers, such as directories, inherit the ACE as an explicit ACE.
“OI” – OBJECT INHERIT: Child objects that are not containers inherit the ACE as an explicit ACE.
“NP” – NO PROPAGATE: only immediate children inherit this ace.
“IO” – INHERITANCE ONLY: ace doesn’t apply to this object, but may affect children via inheritance.
“ID” – ACE IS INHERITED
“SA” – SUCCESSFUL ACCESS AUDIT
“FA” – FAILED ACCESS AUDIT
- Rights:
- A hexadecimal string which denotes the access mask or reserved value, for example: FA (File All Access), FX (File Execute), FW (File Write), etc.
| Value | Description | Value | Description |
|---|---|---|---|
| Generic access rights | Directory service access rights | ||
| “GA” | GENERIC ALL | “RC” | Read Permissions |
| “GR” | GENERIC READ | “SD” | Delete |
| “GW” | GENERIC WRITE | “WD” | Modify Permissions |
| “GX” | GENERIC EXECUTE | “WO” | Modify Owner |
| File access rights | “RP” | Read All Properties | |
| “FA” | FILE ALL ACCESS | “WP” | Write All Properties |
| “FR” | FILE GENERIC READ | “CC” | Create All Child Objects |
| “FW” | FILE GENERIC WRITE | “DC” | Delete All Child Objects |
| “FX” | FILE GENERIC EXECUTE | “LC” | List Contents |
| Registry key access rights | “SW” | All Validated Writes | |
| “KA” | “LO” | “LO” | List Object |
| “K” | KEY READ | “DT” | Delete Subtree |
| “KW” | KEY WRITE | “CR” | All Extended Rights |
| “KX” | KEY EXECUTE |
Happy Hunting!



































